MetaDefender OT Security 3.4 release brings essential updates to help organizations enhance their operational security and gain better control over their OT environments. With features like integrated patch management and advanced network mapping capabilities, this release addresses key challenges in protecting critical infrastructure.
MetaDefender OT Security 3.4 Release Highlights:
- Integrated Patch Management: For Siemens, Rockwell Automation, and Schneider Electric devices.
- Advanced Network Maps: Visualize segmentation, zones and conduits
Integrated Patch Management
Managing vulnerabilities in OT environments is notoriously challenging due to legacy systems, specialized devices, and operational constraints. Additionally, dependency on third-party software to patch systems not only adds to the overall cybersecurity spends but also to the overall time taken to test and deploy a new patching solution. The integrated patch management system in MetaDefender OT Security automates this process, reducing the risk of breaches caused by unpatched systems.
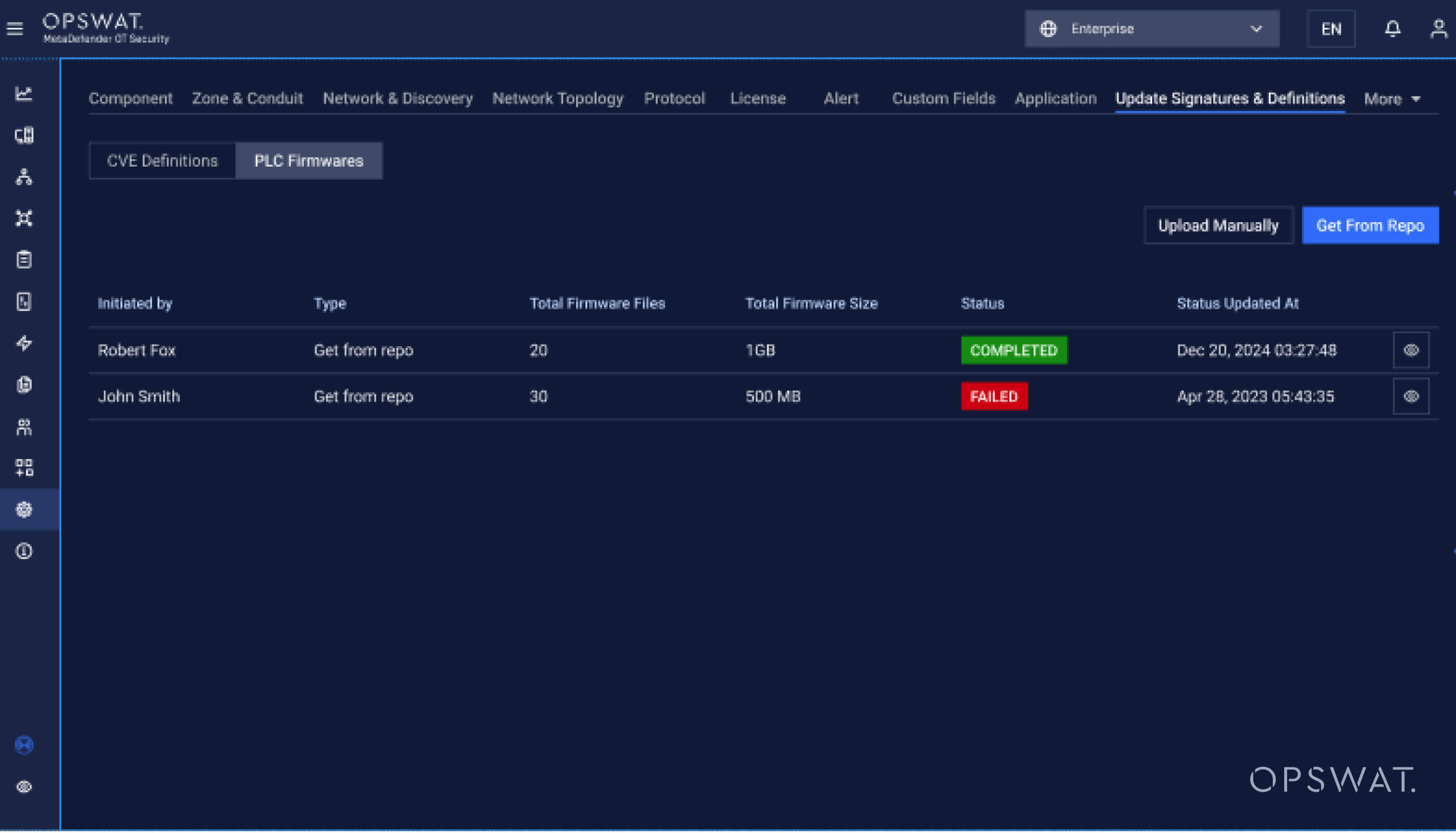
Supported Devices
The patching system supports firmware updates for devices from leading industrial automation manufacturers:
- Siemens
- Rockwell Automation
- Schneider Electric
Key Capabilities

Firmware Version Control and Recommendations
- The system provides an up-to-date list of firmware versions, highlighting recommended updates based on:
- Critical Security Fixes: Urgent updates that address known vulnerabilities.
- Performance Enhancements: Improvements that optimize device operation.
- Regulatory Compliance: Updates aligned with industry standards.
- Recommendations are accompanied by detailed justifications, helping teams understand the significance of each update.
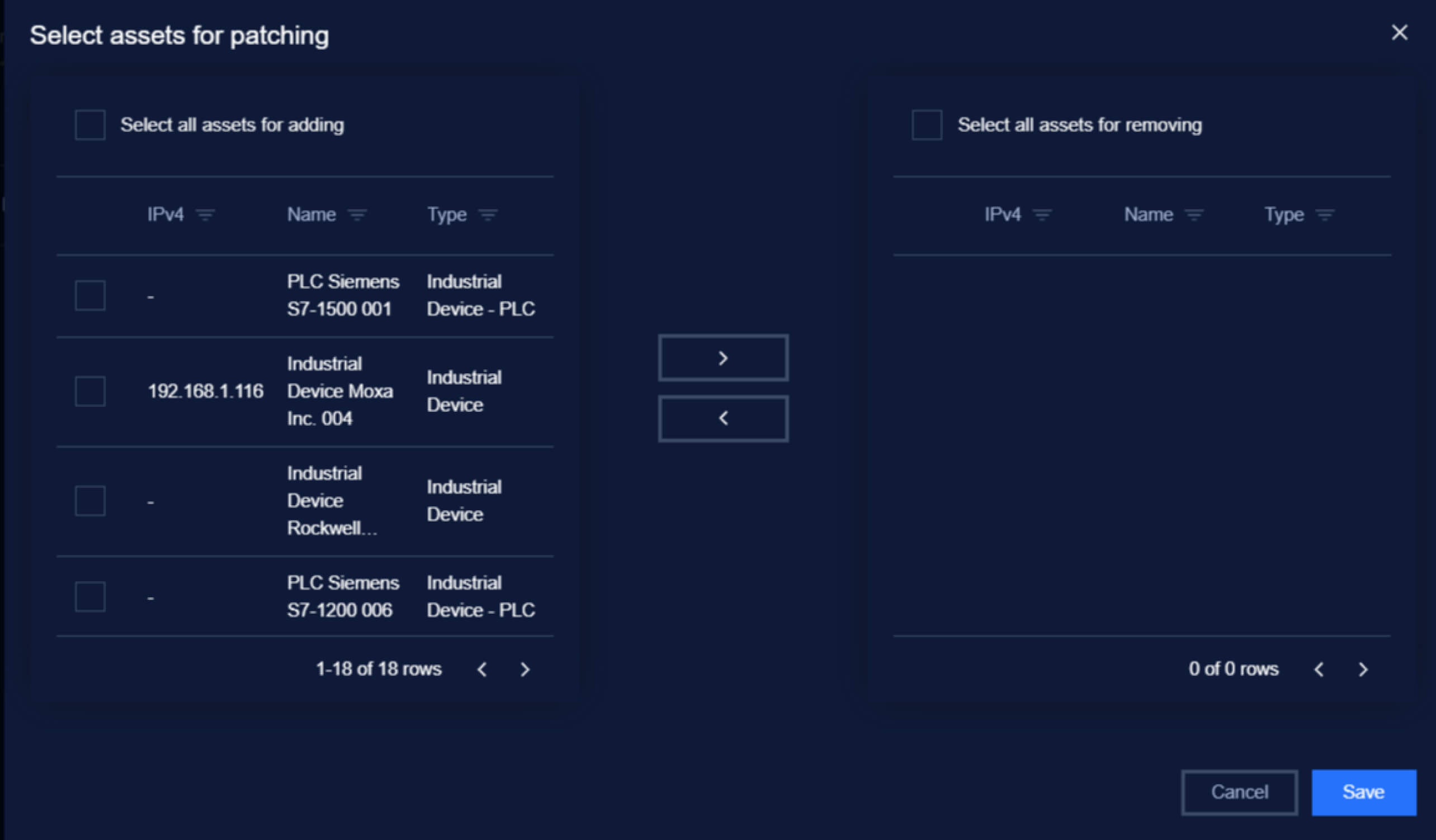
Selective Patching
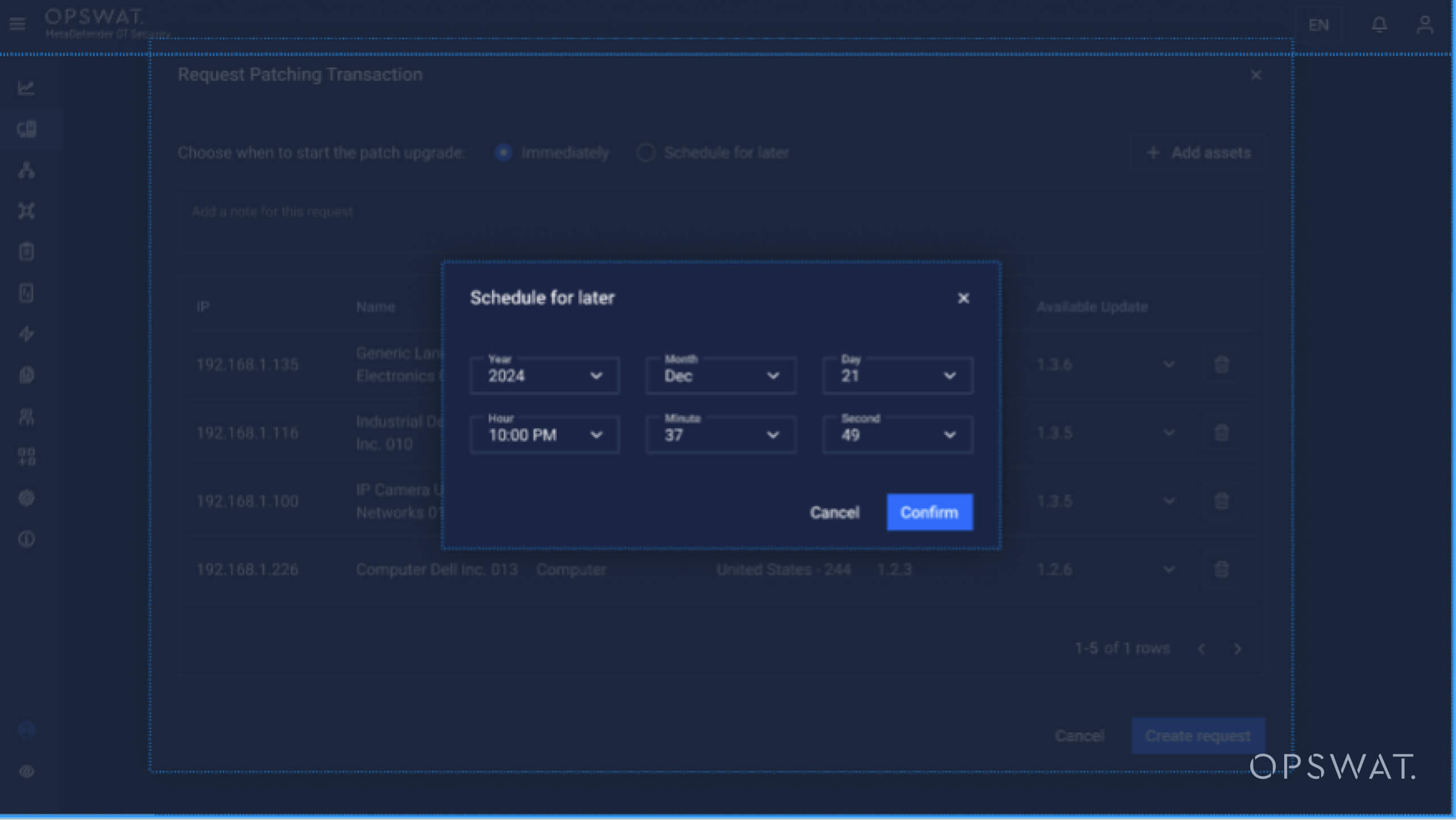
Users can choose specific devices or groups of devices for patching based on operational schedules and criticality. Patching can be executed during planned maintenance windows to minimize disruption.
Rollback Functionality
In the event of a failed update, the system automatically restores the last stable firmware version to maintain device availability and functionality.
Real-Time Vulnerability Assessment and Reporting
With continuous monitoring, the platform provides real-time visibility into the status of OT systems, showing which vulnerabilities have been addressed and which systems remain unpatched. This helps security teams stay ahead of emerging threats and ensures comprehensive reporting.
Process for Automatic Firmware Update
- Select NIC (network interface card)
- Select IP address of the PLC (programmable logic controllers)
- Select firmware and initiate update
- Wait for connection (PLC response status)
- Restore
- Run PLC
Technical Insight
Firmware patching in OT environments follows stringent protocols to ensure safety and operational continuity. Here’s an overview of the patching workflow with MetaDefender OT Security:
Step 1
Vulnerability Discovery
- MetaDefender OT Security identifies which devices have vulnerabilities. Exposure scores and context about each asset and its role are also provided.
- Assessment by operator whether the associated risk is within the organization's tolerance. If it is determined that the assets need to be patched, we make the process very simple from there on.
Step 2
Device Identification
- Select the device (e.g., Siemens PLC or Rockwell controller) through the platform's intuitive interface.
- Validate device connectivity and ensure readiness for patching.
Step 3
Backup and Configuration
- Perform a full backup of the current firmware and configurations.
- Secure backups ensure that all operational settings can be restored if required.
Step 4
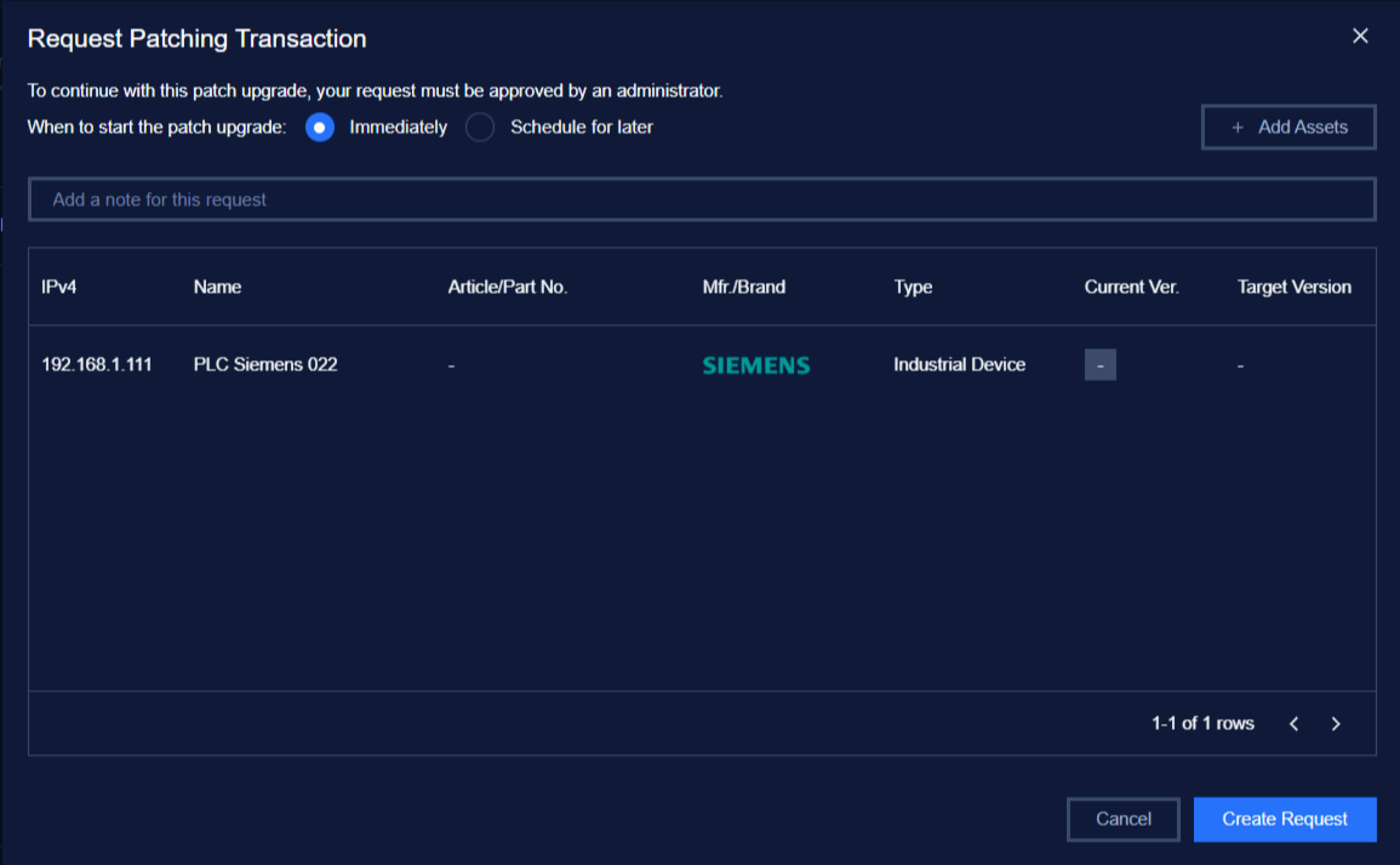
Firmware Selection
- Choose the firmware version from the available options.
- Review the recommended updates, including detailed reasons for the patch, such as addressing specific vulnerabilities or optimizing performance.
Step 5
Firmware Deployment
The patching system updates the firmware in a controlled sequence:
- Stop Operations: Pause the device to prevent interference during the update.
- Install Firmware: Upload and verify the new firmware.
- Restore Operations: Restart the device with the updated firmware.
Step 6
Validation and Testing
- Run validation tests to confirm the successful deployment and ensure that the device operates as expected.
- Save the backup for easy rollback to the previous firmware if validation and test fail.
Step 7
Reporting
- Generate detailed reports for audit and compliance purposes, including information on updated firmware versions, patch status, and rollback actions (if any).
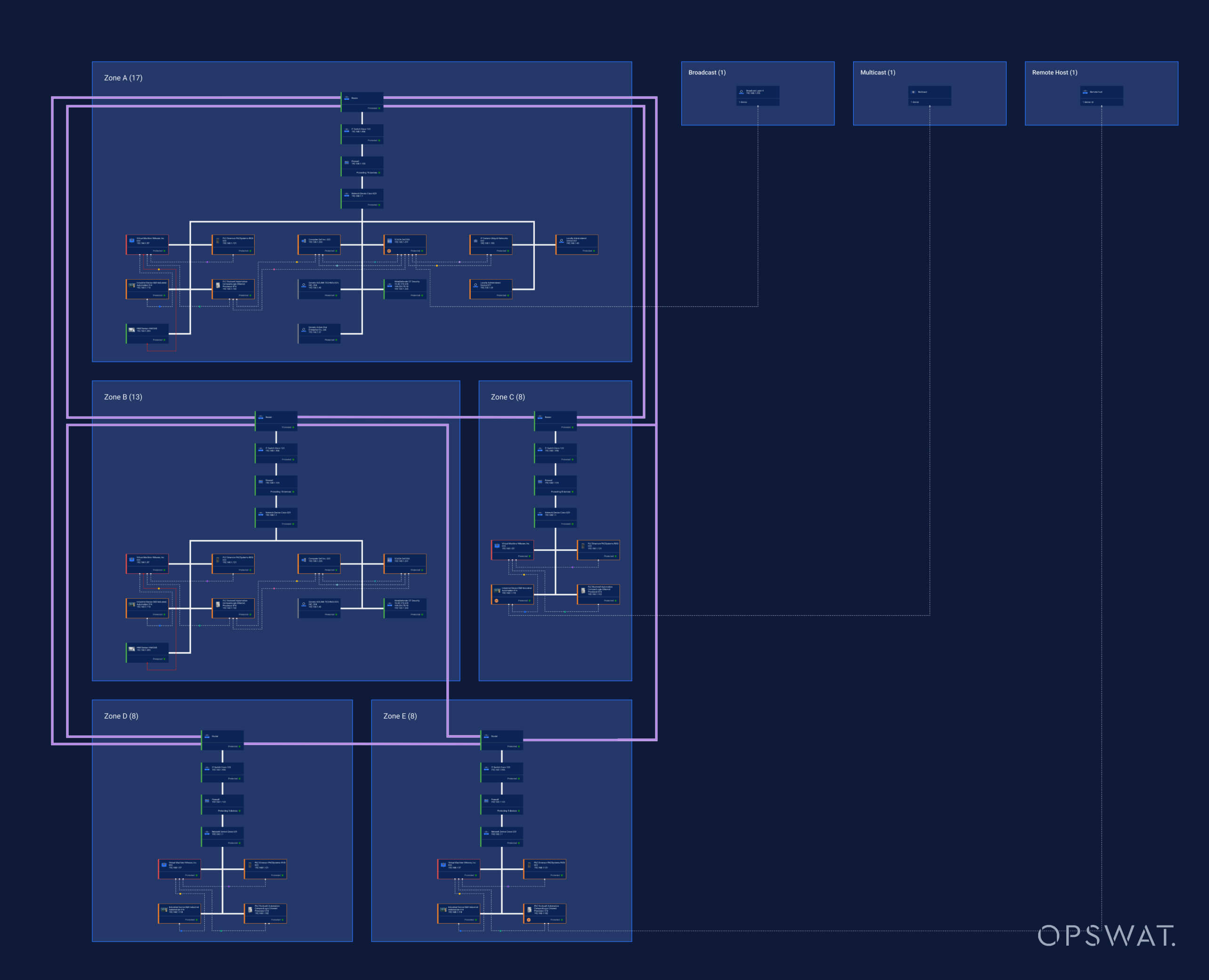
Improved Network Maps
Understanding the layout and behavior of your network is essential for robust security. Properly defining zones and conduits is crucial in OT security. This segmentation of the network into distinct areas with specific security requirements effectively limits the spread of cyberattacks. By controlling communication pathways between these zones through designated conduits, you can actively minimize potential damage and protect critical assets within the network.
Advanced Network Visibility Solution
- Detailed Segmentations: Clear visualization of data flow and device relationships.
- Zones and Conduits: Logical groupings of devices (Zones) and secure communication pathways (Conduits) for better management and compliance.
Why MetaDefender OT Security 3.4 Stands Out
The latest updates focus on addressing the core challenges of OT environments:
- Safe and Controlled Firmware Patching: A structured approach to keeping critical devices secure without compromising operational stability.
- Enhanced Visibility: Tools that provide actionable insights into network behavior and device relationships.
- Proactive Threat Identification: Detect and address traffic anomalies before they impact operations.
MetaDefender OT Security 3.4 empowers organizations to secure their OT environments with confidence, ensuring operational excellence while safeguarding critical infrastructure.



