When a new feature is released in MetaDefender Access, it is always fun to think about how many ways it can be leveraged as part of vetting it. MetaDefender Access’ powerful and evolving playbook feature offers multiple customized solutions to help you with advanced endpoint security or compliance checks across all your endpoints, regardless of whether they are on-premises or remote. To that end, let’s consider a security issue that recently raised its head in a relatively new way: North Korean hackers using a technique known as Bring Your Own Vulnerable Driver (BYOVD) to exploit an endpoint. This vulnerability has also been a focus recently when it was learned that Microsoft Windows was not protecting from it as assumed.
The Attack Summarized
You can read more about this exploit here, but in summary, the hackers cleverly exploit a driver that has a known exploit that has long since been removed from most potential attack targets. The attacker installs the driver on the targeted device by baiting the victim using something like a job advertisement in an email. The email has a malicious document that, when opened, infects the device and places the driver on the machine where the exploit it contains can be used.
MetaDefender Access Playbook Feature: An Advanced and Adaptive Solution
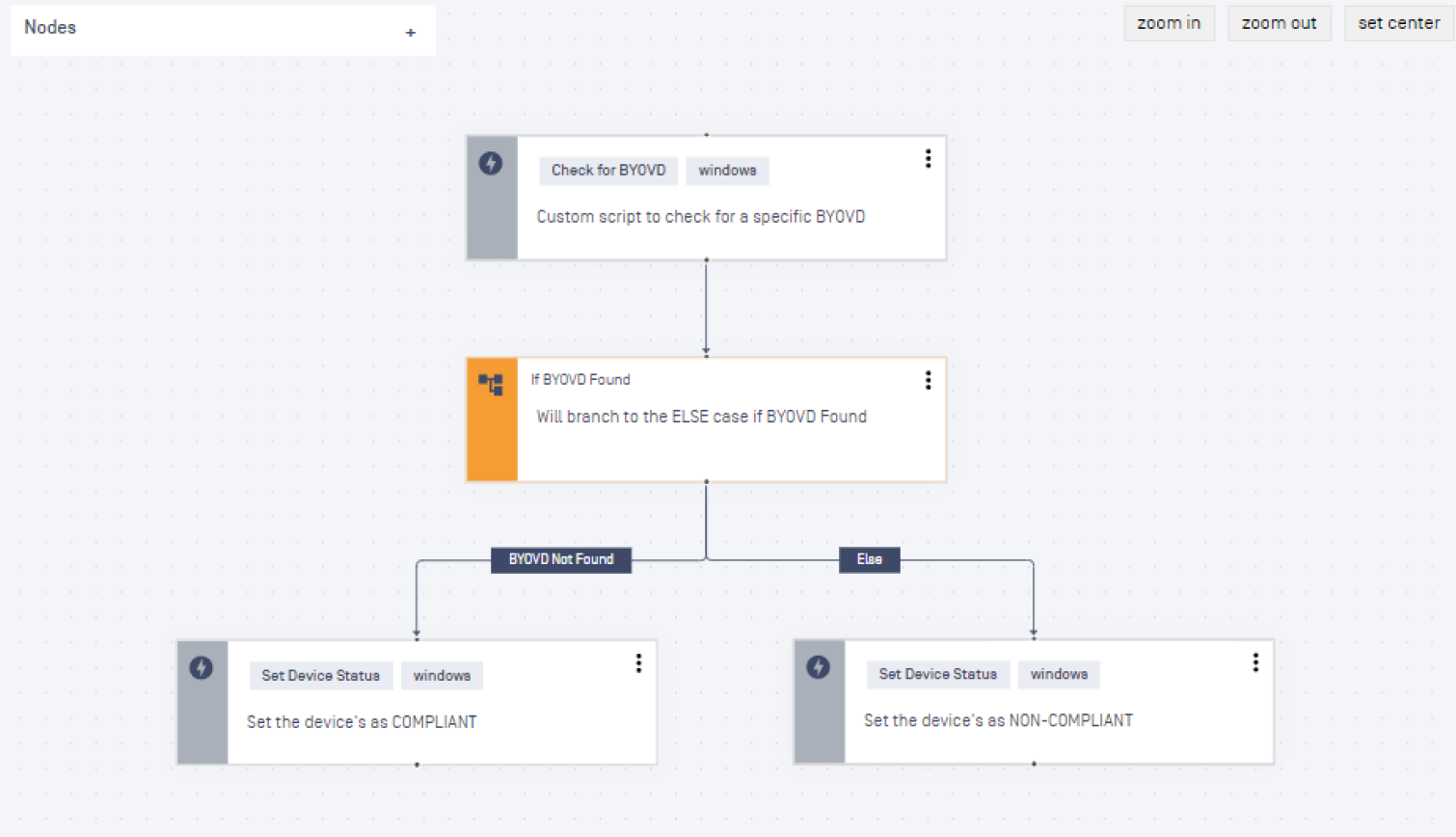
Back to seeing how to creatively use the playbook feature in MetaDefender Access. As shown below, a playbook can run a Powershell script that checks for the compromised version of the driver in the most likely folders in which the attackers would place it. If the file is found in that version, the device it is found on is flagged as non-compliant, and the user’s device can be blocked from accessing any protected resources (read here about how MetaDefender Access can protect applications from insecure devices).

The administrator and end user will then learn what the issue is. The admin will see the device listed as having a critical issue, and the end user will be given a custom message telling them why they are blocked. Then, lateral spread can be stopped by early detection of this issue.
This is just one more example of how MetaDefender Access can improve your endpoint security. For any given zero-day announcement that involves endpoints, whether it be Windows, macOS, or Linux, MetaDefender Access playbooks can give you a jump on avoiding being one of the targets of these all too clever attackers.
MetaDefender Access is a part of our suite of advanced security solutions for organizations. To find out how you can improve your cybersecurity measures, contact our experts right away for a demo.