MetaDefender Sandbox now delivers threat analysis and visibility for ICS protection in Critical Infrastructure
The rate at which malware and attack techniques evolve, coupled with a rise of global geopolitical tensions, have shifted the conversation in both the public and private sector around how to protect critical infrastructure from mass cyber disruption.
Historically, IT and OT/ICS systems have been completely isolated from each other, but as digital transformation continues, these two worlds are rapidly merging.
As a result, cybercriminals are using malware to specifically infiltrate OT networks to hold hostage the systems that nations rely on – knowing that targets cannot afford the downtime that is so often seen when ransomware hits the IT side of the business.
The increasing attacks on ICS jeopardize the safety and security of the public who rely on critical infrastructure to provide basic needs. We’ve seen it happen with Iranians targeting Saudi oil infrastructure with Triton and SandWorm targeting Ukrainian electric utilities with Black Energy in 2015 and Industroyer in 2016.

Understanding Vulnerabilities
To better understand how OT malware works, it’s important to understand where the vulnerabilities reside and how they’re exploited. In most cases, it’s within the Windows controllers interfaced with these systems, and the instructions directed toward the operational systems. These include:
- Devices: Human Machine Interfaces (HMIs) clients, data historians, SCADA servers, and engineering workstations (EWS)
- Platforms (ICS software): GE Proficy, Honeywell HMIWeb, etc
- Network: direct internet access to an ICS environment through the exposure of operational protocols such as Siemens S7, Omron FINS, and EtherNet/IP, in addition to misconfigured VNC access. This can lead to lateral movement vis SMB.

So Why Focus on These Industrial Scenarios, Beyond IT?
Nation-state actors love ICS malware as it aligns with their political goals of undermining infrastructure, and broader and deeper attack services within industrial environments allow them to do so. These actors are also the ones with the resources needed to successfully execute attacks on ICS as these generally need more sophistication and planning than a ransomware attack that can be executed using “off the shelf” components and services.
Understanding the Attack Methodologies
There is a better way to understand the malware behind these attacks and help critical infrastructure organizations prevent future ones by mapping all behaviors to the MITRE ATT&CK Framework for ICS and YARA – two key resources that cybersecurity professionals should be familiar with:
- MITRE ATT&CK for ICS: Similar to the widely adopted MITRE ATT&CK framework for IT, this framework models behaviors for attacks using malware targeting Industrial Control Systems. By incorporating mapping of behavior to the MITRE ATT&CK ICS framework, tools like MetaDefender Sandbox can help defenders quickly identify how malware is trying to attack their systems, and more effectively response.
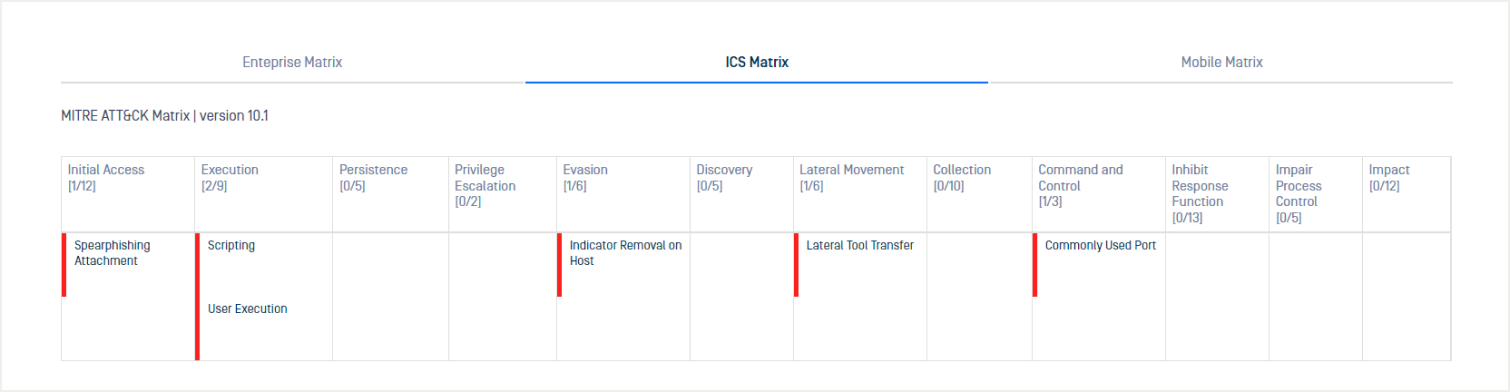
As an example of this, we analyzed Black Energy in the sandbox, and saw the mapping of ICS-specific behaviors to the framework:
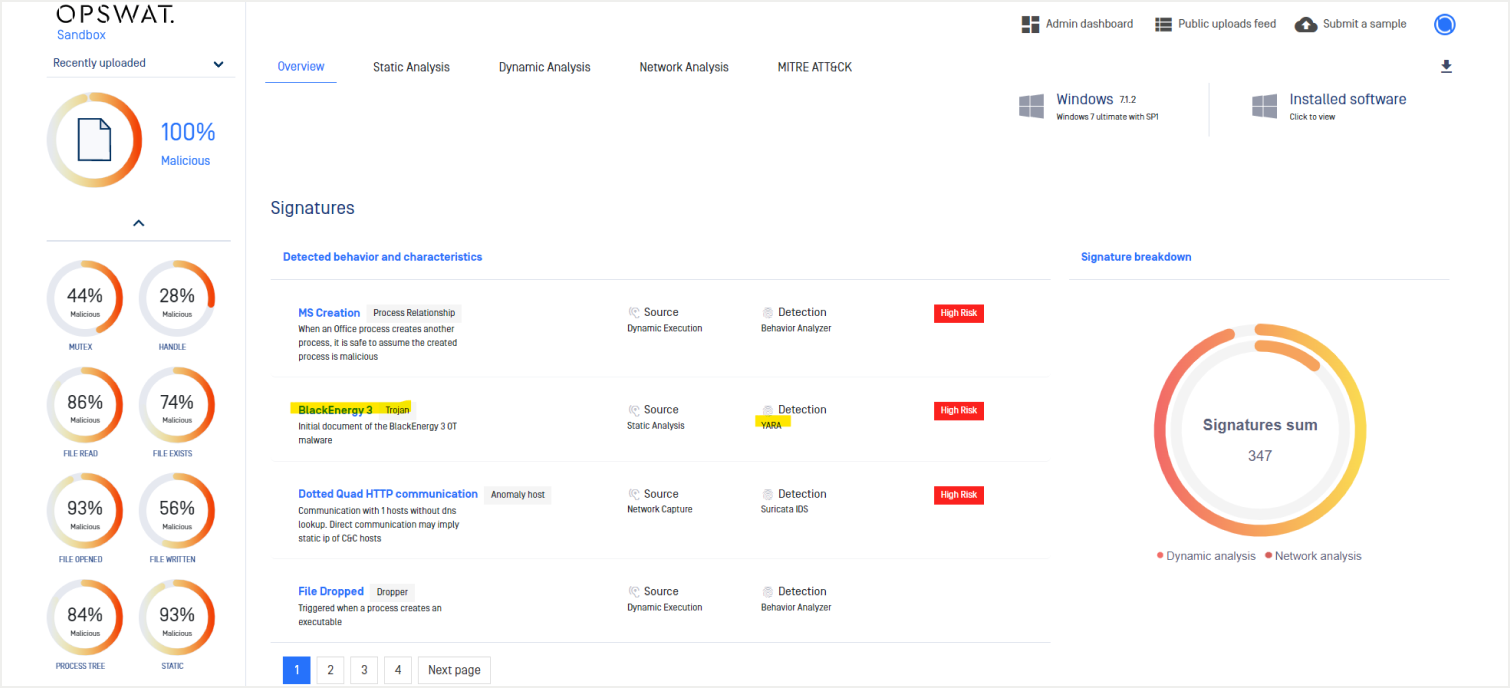
- YARA for Protection, Detection and Threat Hunting: By incorporating Yara ICS rulesets, analysis tools, including OPSWAT Sandbox, can more effectively identify attributes of malware – both static and dynamic – that match known malicious attributes for ICS malware. While malware files themselves are frequently modified by threat actors to evade detection, attackers need to leverage existing infrastructure and tools, tactics and procedures (TTPs) in order to be effective. The attacker’s infrastructure is a big sunk cost they need to reuse, and hence why TTPs are common across different variants of malware. As a result, TTPs common to more than one malware sample can identify families and aid in attribution.
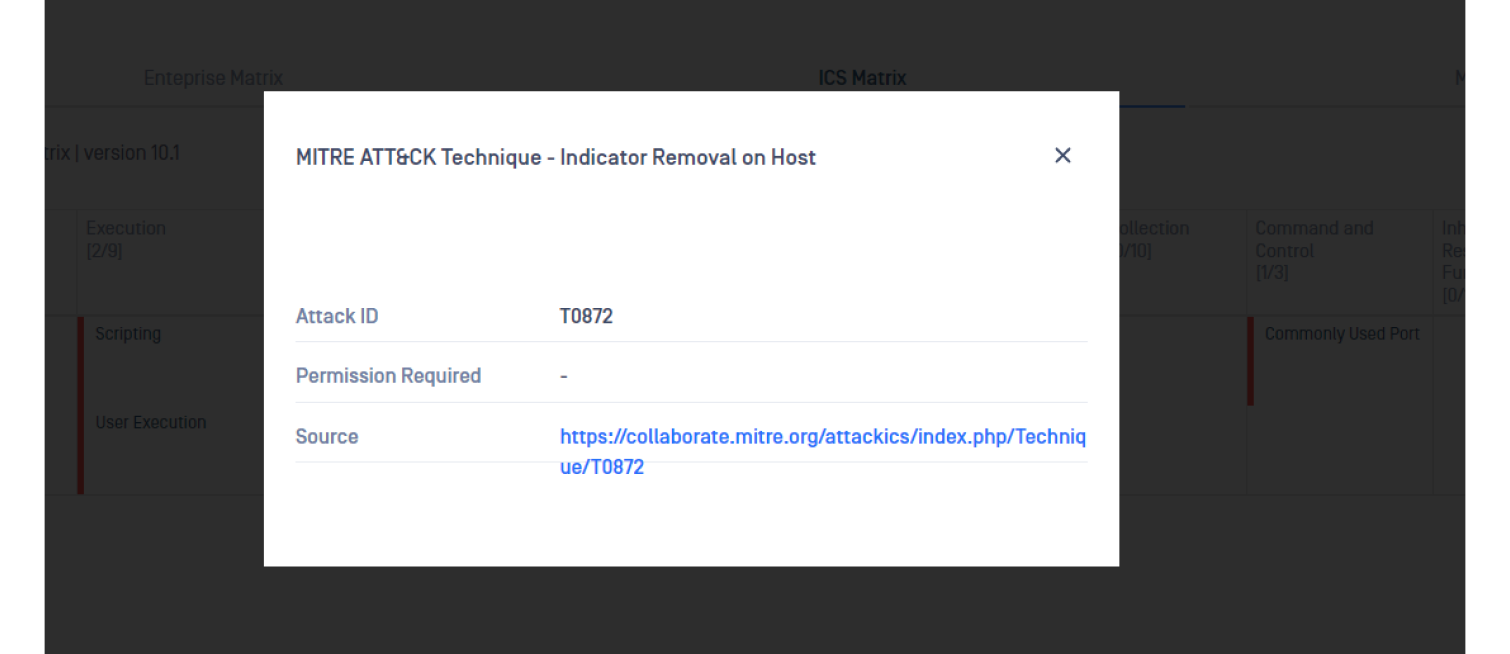
The latest MITRE ATT&CK for ICS provides the TTP framework specific to attacks targeting operational technologies, such as inhibiting response functions.
Detecting particularly evasive malware within critical infrastructures requires analysis capabilities that should include comprehensive static and dynamic analysis, with the ability to flag TTPs specific to ICS attacks, as shown with the analysis of Black Energy below.
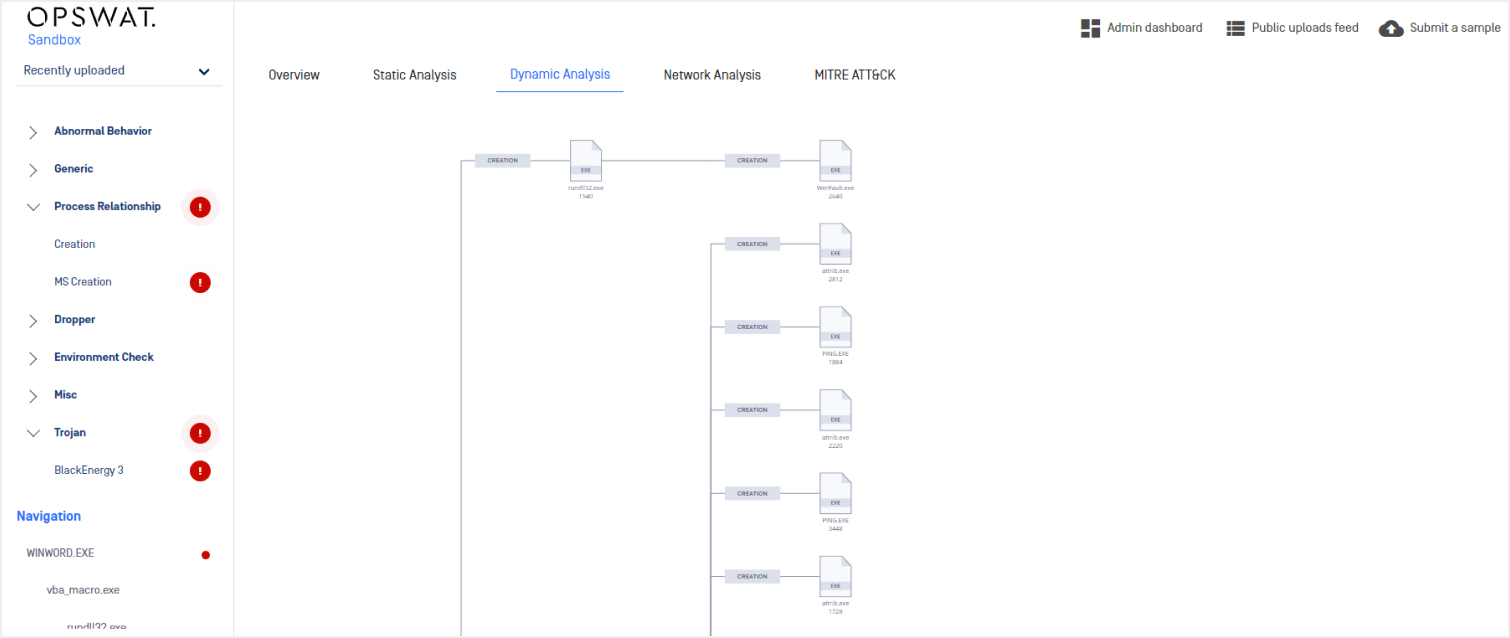
The recent release of OPSWAT Sandbox v1.1.7 includes Mapping IOCs to ICS TTPs, and with available YARA rules and a MISP repository native to OPSWAT MetaDefender Core, organizations can better protect themselves from malware threats through OPSWAT’s comprehensive threat intelligence solution.