We're thrilled to introduce the latest milestone in cybersecurity resilience - MetaDefender Aether v1.9.3. This release is a testament to our commitment to empowering organizations against emerging threats.
Python Unpacking & Decompilation: Unveiling Hidden Threats
With the inclusion of Python Unpacking & Decompilation support for PyInstaller, Nuitka, and py2exe, MetaDefender Aether v1.9.3 sheds light on previously hidden malicious items. By dissecting and analyzing compiled Python files, organizations can uncover hidden threats and proactively defend against them.
Extended Malware Configuration Extraction to support Cobalt Strike malware family: Combatting Advanced Threats
The enhanced malware configuration extractor now supports the Cobalt Strike (CS) malware family. Widely utilized by threat actors, cracked versions of CS enable the deployment of an in-memory agent (known as a beacon) onto the victim host, bypassing disk interactions. CS beacon facilitates command and control (C2) communication through various protocols, offering a plethora of functionalities such as privilege escalation, credential extraction, lateral movement, and data exfiltration.
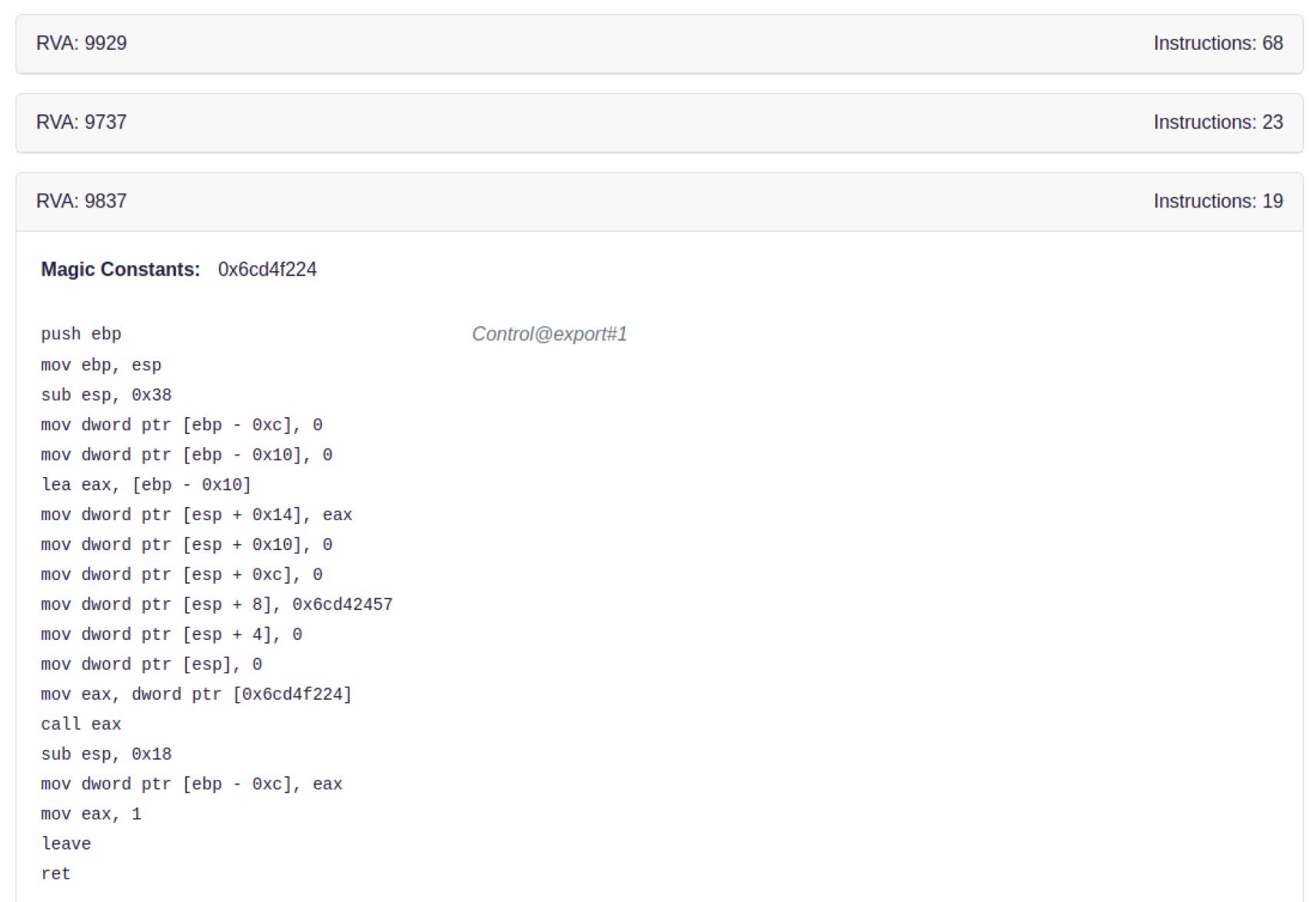
Disassembly of Exported Functions: Understanding Windows Binaries
MetaDefender Aether goes beyond surface-level analysis by displaying the binary functions to see how the file would behave in a Windows environment and what functions are executed. (e.g. when the exported function is trying to create a network and open a malicious URL). Now organizations can gain new insights into their behavior and potential risks, empowering them to make informed security decisions.
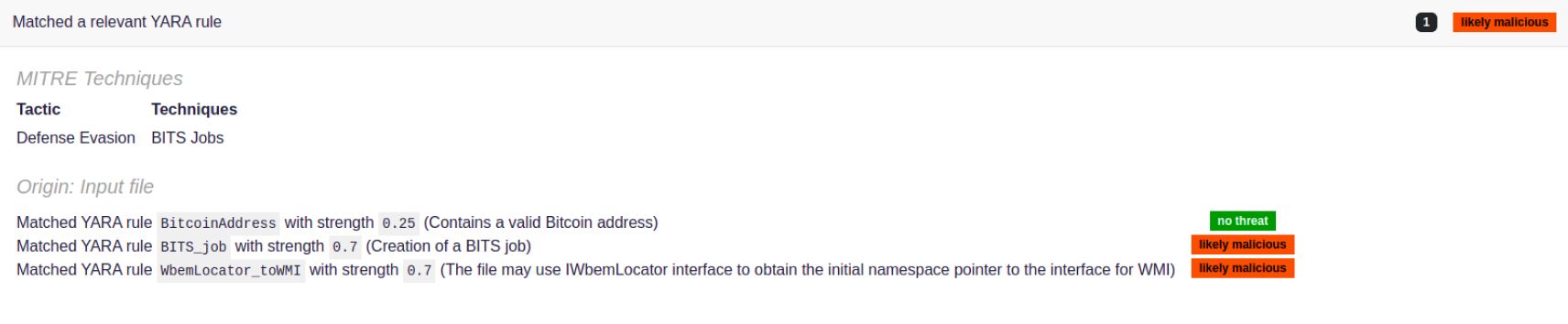
Threat Indicator Refinement: Identifying Suspicious Activity
Our new threat indicator flags executable files with two different sections bearing the same name as a preventive measure; these same section names can confuse AV engines. This measure helps organizations identify potential IOCs before they can escalate.
VBA Macro Code Extraction: Unveiling Malicious Intent in DWG Files
The release includes the extraction of VBA macro code from DWG files, providing deeper insights into potential threats hidden within AutoCAD documents. AutoCAD files can execute “Kill” functions, which might indicate malicious intent. By uncovering malicious code embedded in DWG files beyond ransomware keywords, organizations can mitigate risks associated with these often-overlooked attack vectors.
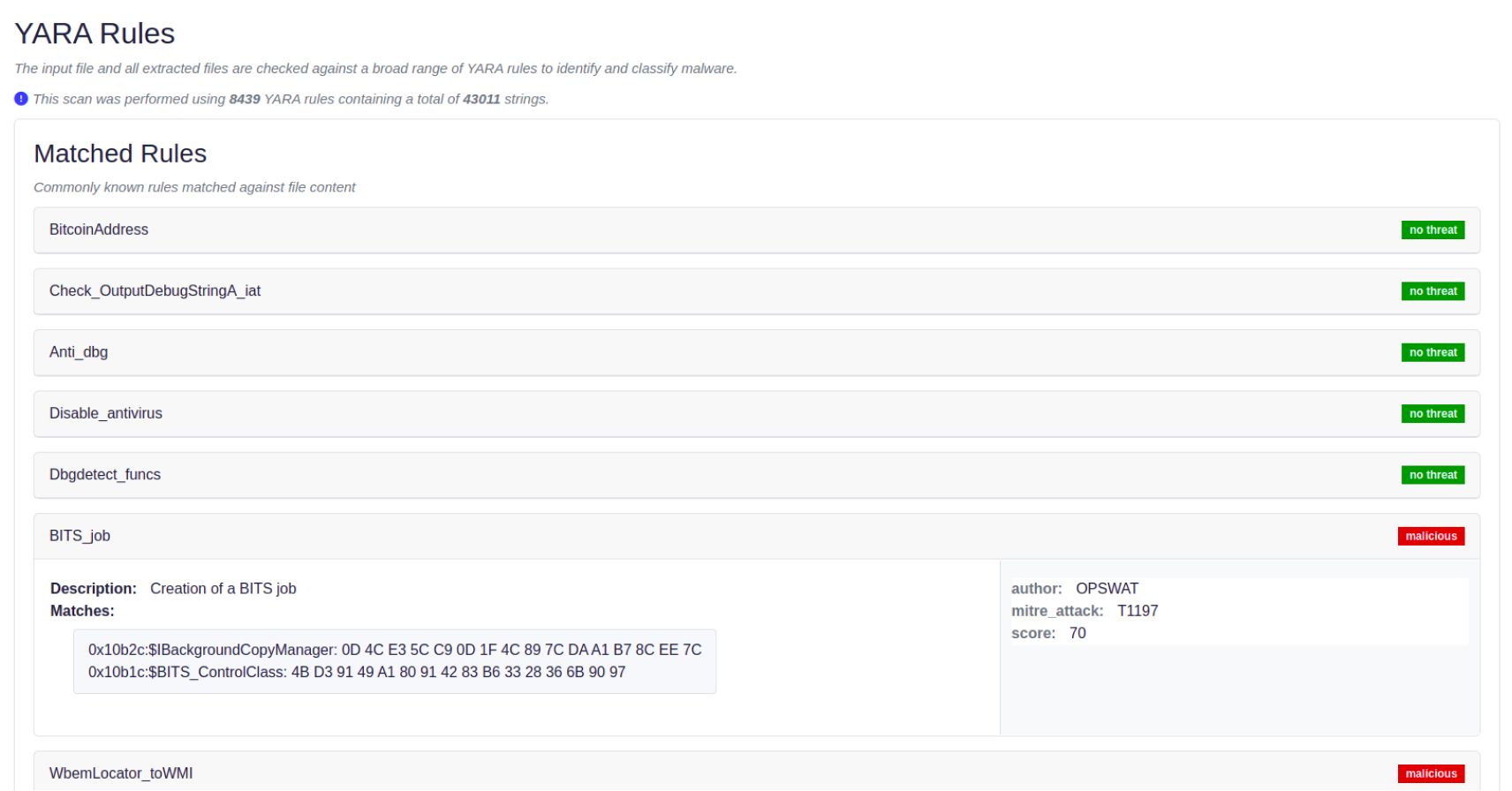
MITRE Att&ck Technique Mapping: Aligning with Industry Standards
MetaDefender Aether now supports mapping of MITRE Att&ck techniques from YARA rule metadata. By aligning with industry standards, organizations can enhance their threat intelligence capabilities.
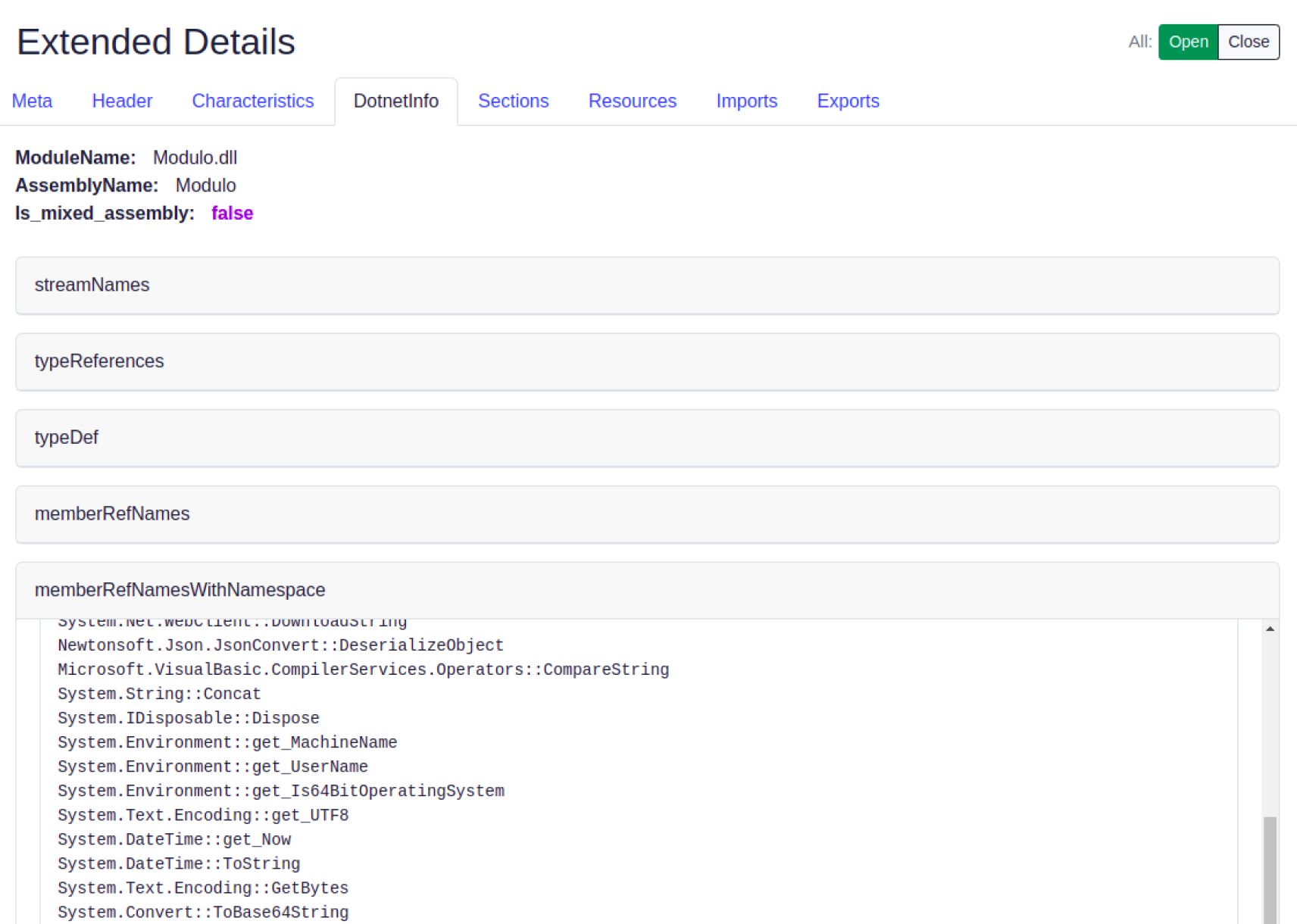
New DotnetInfo Tab in the File Details Section for .NET Executables
The new DotInfo tab caters directly to Dotnet specifics, facilitating disassembly and providing invaluable insights into functionalities. Our Sandbox boasts its own array of indicators, from decisive actions like "Killing" and subtle maneuvers like "Sleep" for processes, to strategic evasions like "Load" to avoid static detection.
Administrative Enhancements: Streamlining Operations
In addition to advanced threat detection capabilities, MetaDefender Aether v1.9.3 introduces administrative enhancements aimed at streamlining operations and improving efficiency. From improved proxy handling to enhanced queue management, these features ensure smooth and seamless operation of the sandbox environment.
MISP Integration
This integration introduces significant enhancements in the structured sharing of threat intelligence, empowering organizations to proactively manage their prevention measures.
Furthermore, in response to increasing demand, we’ve created a new Auditor role that addresses the necessity for a "read-only" administrative role, providing more flexible permissions and visibility across the platform.
For more information about these changes and updates, check out the release notes for MetaDefender Aether v1.9.3.

