Industrial Automation and Control System (IACS or ICS) technologies are essential to critical infrastructure and Operational Technology (OT) environments. Such systems consist of multiple components that communicate with each other over network protocols, making them susceptible to cyberattacks. Even the air-gapped zones within IACS remain vulnerable to malware attacks via peripheral and removable media.
The ISA/IEC 62443 series of cybersecurity standards is a common framework for operators, system integrators, and component manufacturers of IACS and OT networks. The standards include sets of requirements, instructions, controls, and best practices to secure the operations, development, maintenance, and component manufacturing of IACS.
History and Evolution of ISA/IEC 62443
The ISA/IEC 62443 standards were developed in 2002 by the International Society of Automation (ISA) as ISA 99, aiming to set standards to secure U.S. critical infrastructure systems and operations against cyberattacks. Eventually, it was submitted to the International Electrotechnical Commission (IEC) for global recognition to become the ISA/IEC 62443 series of standards.
In November 2021, ISA/IEC 62443 was designated by the IEC as a horizontal standard, making it a widely recognized cybersecurity benchmark in all industries that use, maintain or develop IACS. Currently, the ISA/IEC 62443 series has extensive content with a broad scope, covering over 800 pages.
Who is ISA/IEC 62443 for?
Three main principal roles are contextually defined in ISA/IEC 62443, aiming to define the stakeholders who can benefit from them:
- Asset Owners: Organizations that own and operate IACS.
- System Integrators: Organizations or consultants offering services like system integration, maintenance, or other IACS-related services.
- Product Manufacturers: Organizations that offer products to meet security requirements, provide product components, or lifecycle support.
Components of ISA/ IEC62443
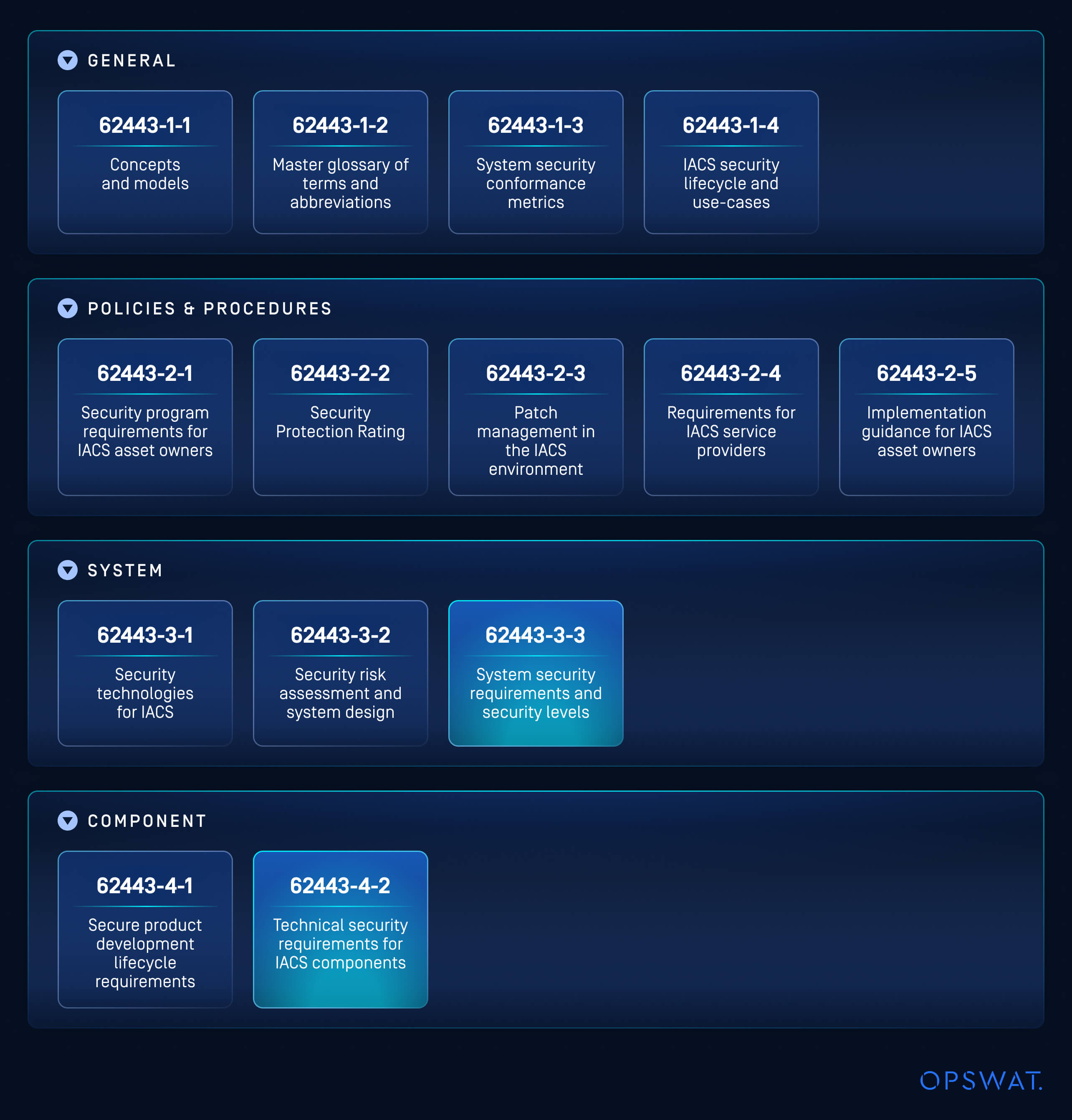
The ISA/IEC 62443 series is split into four main parts: General, Policies and Procedures, System, and Component. Each part is aimed at a different principal role and contains instructions and guidelines that cover a specific aspect or stage of ICS security.
The Four Parts of the ISA/ IEC62443 Series
General 62443-1
The first part includes a general overview and introduces the foundational concepts, requirements, terminology, and guidelines for designing and implementing cybersecurity in IACS.
It begins with section 62443-1-1, defining the foundational terminology, concepts, and reference models used throughout the standard series. Then, 62443-1-2 with a glossary of terms and abbreviations used across the series, and 62443-1-3 to discuss security metrics for evaluating and measuring the security of systems. Lastly, 62443-1-4 provides guidelines to be followed for addressing cybersecurity throughout entire systems.
Policies and Procedures 62443-2
Focusing on governance and risk management, the second part provides guidance on creating, maintaining, and managing cybersecurity programs.
Section 62443-2-1 describes the process of creating, implementing, and maintaining a cybersecurity management system for IACS, while 62443-2-2 offers detailed implementation guidelines for organizations to follow when setting up IACS security programs. Then, 62443-2-3 provides best practices for managing software and firmware patches to maintain system security, and finally, 62443-2-4 lists cybersecurity requirements and best practices for service providers working in industrial environments.
System 62443-3
This part provides guidance on designing and implementing secure systems and addresses the cybersecurity requirements for IACS. It covers risk assessment, system security requirements and strategies, and system security levels.
Section 62443-3-1 reviews existing and emerging security technologies relevant to IACS. Next, 62443-3-2 introduces a methodology for assessing and managing cybersecurity risks during system design. Finally, 62443-3-3 establishes detailed system security requirements and categorizes them into four Security Levels (SL1-SL4).
Component 62443-4
The fourth and last part of the series describes the Product Development Lifecycle. It focuses on the security of individual components of IACS, such as SCADA (supervisory control and data acquisition), PLCs (programmable logic controllers), and sensors.
It includes two sections. 62443-4-1 outlines the processes of a Product Development Lifecycle, including the design, development, and maintenance of IACS components, and section 62443-4-2 specifies the technical security requirements and capabilities required for individual IACS components within the system.
Foundational Requirements
The seven Foundational Requirements (FRs) are identified in the first part of the series (IEC 62443-1-1). series. These FRs are the cornerstone of ISA/IEC62443 which every subsequent part of the series is based on, including the parts focused on security requirements for IACS systems (3-3) and components (4-2).
- Identification and authentication control
- Use control
- System integrity
- Data confidentiality
- Restricted data flow
- Timely response to events
- Resource availability
Benefits and Applications of ISA/IEC 62443
These standards have been adopted in various industries, including manufacturing, critical infrastructure, oil and gas, healthcare, and wastewater treatment. The way an organization can utilize the ISA/IEC 62443 series depends on the role of the organization within a specific industry, whether operating, maintaining, integrating, or manufacturing components for IACS.
For Asset Owners
Asset Owners establishing security protocols and operating IACS can refer to section 2 of ISA/IEC 62443 to develop requirements for system integrators. These guidelines can help them determine what security features they specifically need in a product.
For System Integrators
Due to performing integration, maintenance, and similar ICS-related services, system Integrators mainly use 62443-3 standards to assess the security level of the asset owners and process their requirements. Also, the 62443-3-3 standards are used to assess the security of the components produced by Product Manufacturers and to determine if they include the features required by Asset Owners.
For Product Manufacturers
Product Manufacturers establish and maintain an SDL (security development lifecycle), offer products to meet the required security level, provide component products, and provide lifecycle support. Product Manufacturers are companies that produce IACS hardware and software components. Product manufacturers can find 62443-4 standards as a clear reference for which capabilities and security features to include with their products.
Importance of ISA/IEC 62443-3-3 for Critical Infrastructure Protection
The 62443-3-3 standards provide critical technical security requirements and security levels to be used as a reference for the security level to be achieved. This section is used by system integrators to meet the standards of the systems they develop.
Key Security Requirements
Defense- in-Depth
A technique that requires multiple layers of defense techniques to prevent or slow down a cyberattack. For instance, the layer of security can include physical checks, frequent scans, securing file transfers, and using firewalls.
Zones and Conduits
Leveraging the Purdue model, also known as Purdue Enterprise Reference Architecture (PERA), the ISA/IEC-62443 series identifies a zone as a functional or physical unit, while a conduit is a collection of communication channels between zones.
Risk Analysis
In addition to the conventional risk analysis practices, ISA/IEC-62443-3-2 brings further details about security risk assessment methodologies for an IACS.
Least Privilege
The principle of least privilege limits users’ access to specific components or applications in a system, preventing unnecessary access and minimizing the attack surface in case of a cyberattack.
Leveraging secure components
The ISA/IEC-62443-3-3 part isn’t a standalone set of requirements, it also leverages other parts of the series. It assumes that a security program has been developed according to IEC 62443‐2‐1 and assumes that secure components will be deployed according to ISA/IEC-62443-4-2 and ISA/IEC-62443-4-1 in order to guarantee compliance.
Security Levels
The defined security levels are intended to measure the strength and highlight any risk factors in OT and IACS systems. Four Security Levels are defined in 62443-3-3, starting from 1 as the minimum level and up to 4 as the maximum level.
Security Level 1
The defined security levels are intended to measure the strength and highlight any risk factors in OT and IACS systems. Four Security Levels are defined in 62443-3-3, starting from 1 as the minimum level and up to 4 as the maximum level.
Security Level 2
For protection against general cyberattacks that don’t require a specific skillset or intensive resources, such as individual hackers.
Security Level 3
Covers protection against intentional attacks using sophisticated techniques and specific skills with moderate motivation.
Security Level 4
Protects against intentional attacks that require highly sophisticated, IACS-specific skills with access to extended resources, such as attacks on highly critical systems by organized hacker groups or enemy states.
In conjunction with 62443-3-3, the 62443-4-2 standards are often taken into consideration by system integrators since they provide further guidance on securing each component of the lifecycle.
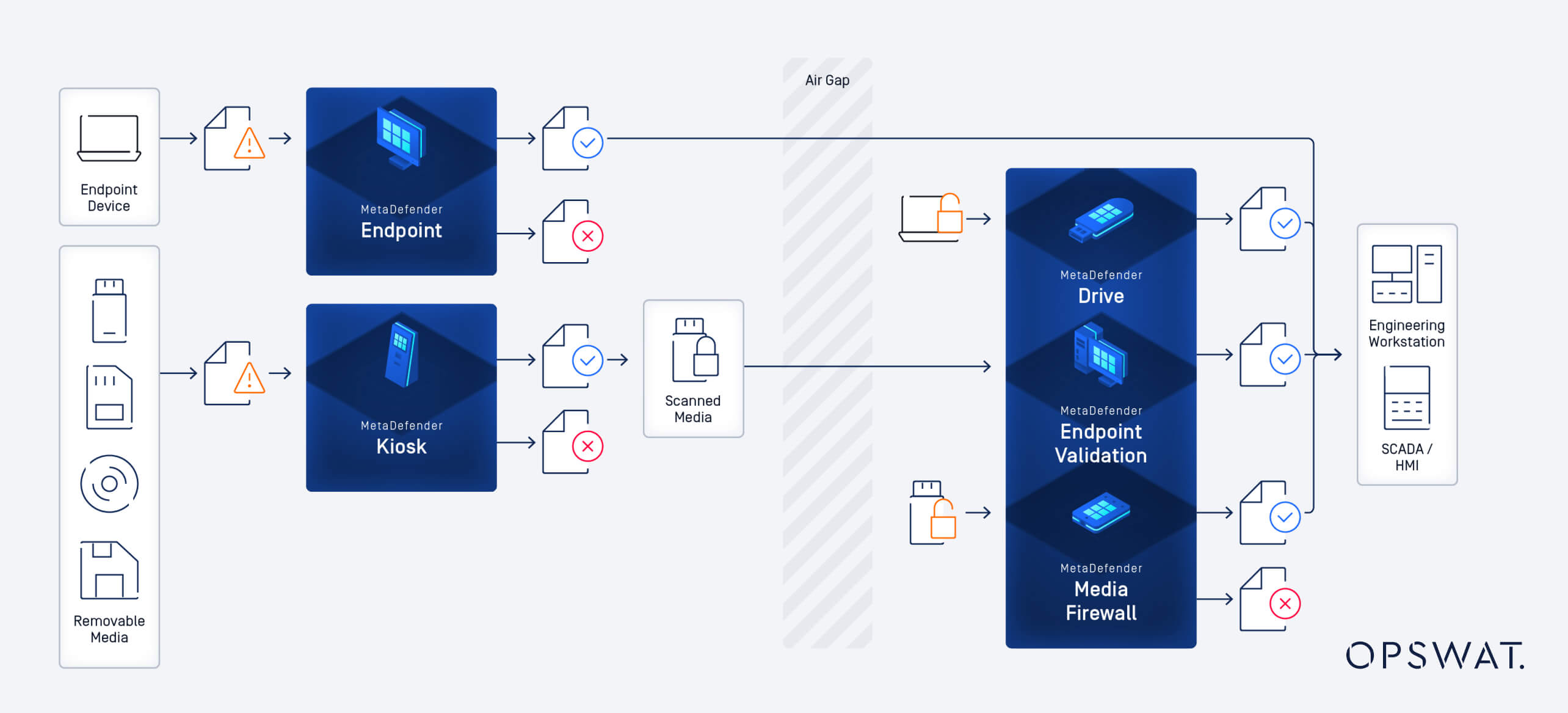
Peripheral and Removable Media Protection
Removable media, such as USB and external hard drives are often used as conduits to transfer data in IACS and OT networks, despite the significant security risks they pose. There have been prominent cyberattacks caused by removable media, such as Stuxnet that targeted Iran’s Natanz nuclear facility (2010), India’s Kudankulam Nuclear Power Plant attack (2019), and the Agent.BTZ attack that spread through the U.S. Department of Defense networks (2008).
Including peripheral and removable media protection as a part of the defense-in-depth strategy can play an essential role in mitigating such attacks, and to achieving compliance with the ISA/IEC 62443 standards, reducing the risk of data breaches and system disruptions. For instance, a physical solution, like MetaDefender Kiosk™, can scan removable media using multiple anti-malware engines to ensure its safety. Other solutions like MetaDefender Drive™, MetaDefender Media Firewall™, MetaDefender Endpoint™, and MetaDefender Managed File Transfer (MFT)™ can play a pivotal role in enhancing your security level and defense-in-depth strategy.
Conclusion
The ISA/IEC 62443 standards are considered the most comprehensive cybersecurity standards that address the cybersecurity challenges of IACS and OT environments. With the ISA/IEC 62443 series of standards, organizations can systematically recognize what is most valuable within their environment, improve visibility, and identify assets that are highly susceptible to cyberattacks.
OPSWAT offers comprehensive solutions in peripheral and removable media security to enhance the defense-in-depth protection and minimize the attack surface. To see why organizations, governments, and institutions around the world trust OPSWAT, talk to one of our experts today to learn how we can help with your peripheral and removable media security.

