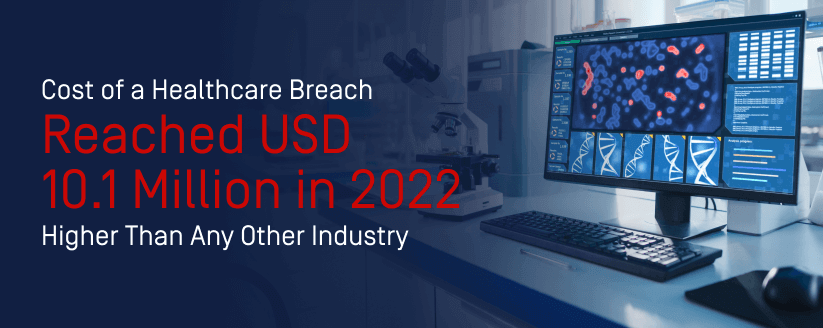
Attackers are putting considerable pressure on the healthcare sector right now, dominating the news cycle and putting ransomware and other cyberattacks top of mind. The healthcare industry poses an attractive target for cybercriminals, averaging 1,463 attacks per week (an increase of 74% compared to 2021). For the last twelve years, the cost of a healthcare breach has been higher than any other industry, reaching USD 10.1 million in 2022. And as more health systems move to digital and connected technologies, these attacks will increase even further.
Why Hit Healthcare Systems?
There are several reasons attackers focus on healthcare. The first, of course, is that when human lives are at risk, organizations targeted are more likely to pay the ransom so they can return to regular business operations — which is actually providing critical urgent care, delivering babies, and delivering ongoing care for vulnerable patients. Simply disrupting the operations in these settings can be life threatening.
In Ontario, a hospital experienced loss of utilities, including such necessities as power, water, and critical IT systems. Calling this a “Code Grey” event, the hospital worked to deliver critical hospital services but urged patients with less urgent conditions to seek alternative care options. Even after the cyberattack subsides, the hospital system will likely experience challenges in returning to normal operations.
Just days earlier, an attack on a Florida health system caused Tallahassee Memorial HealthCare (TMH) to take its IT systems offline and suspend non-emergency procedures. The impacts are wide-ranging to the private, not-for-profit healthcare system that provides acute care hospitals, psychiatric hospitals, 38 affiliated physician practices, and multiple specialty care centers in Florida and Georgia.
According to the U.S. Cybersecurity & Infrastructure Security Agency (CISA) earlier this year, North Korean ransomware operations were extorting funds and using them to support the North Korean government's national-level priorities and objectives. These attacks are targeting public health and other critical infrastructure sectors. CISA indicated that the hackers used multiple strains of file-encrypting malware to attack South Korean and U.S. healthcare systems in addition to privately-developed lockers.
In addition to nation-state actors funding government operations through ransomware attack, a hacktivist group called KillNet has been actively targeting the US healthcare sector with distributed denial-of-service (DDoS) cyberattacks, notes the Health Sector Cybersecurity Coordination Center. This group targets countries that support Ukraine, hitting them with distributed denial of service attacks that cause service outages lasting hours or days. Those delays may result in appointment delays, downtime for critical EHR systems, and ambulances being diverted to other health systems. As the war in Ukraine drags on, the US healthcare sector must be even more vigilant in their efforts to prevent cyber threats.

How Do Attackers Get In?
Health systems are incredibly complex IT ecosystems. Smaller hospital acquisitions, cloud and SaaS applications provisioned without the security team’s oversight, connected medical devices, and thousands to hundreds of thousands of digital assets all create an attack surface that can be challenging to manage. Coupled with that, there are many unknown vulnerabilities that will always exist and leveraged for zero-day attacks, making any unpatched systems an incredibly large risk.
With so many access points to insurance information and patient data, IT teams struggle to secure them all. Further complicating matters, doctors, physical therapists, physician assistants, nurses, and patients themselves are now interacting with dozens of endpoints, but these individuals are rarely sophisticated users. They may share passwords or use ones that are easy to guess, and few are likely to employ multi-factor authentication capabilities effectively. Compromised credentials and lax identity verification offer attackers a path into the networks, applications, and data of the health system.
Mitigating Attack Potential & Impact
The world is increasingly connected, and security plans and protocols need to adapt to this reality. Health systems can prepare for attacks by putting well-defined and practiced response plans in place in case an attack occurs. Conducting regular cybersecurity exercises to ensure that protocols are well-coordinated and up-to-date can help security teams prepare for the seemingly-inevitable attacks.
While budgets and staffing resources may be limited, investing in additional zero-trust technology can greatly reduce the threat surface. The healthcare industry relies heavily on emails for day-to-day communication and web application portals to share and upload files and patient data. Both of these, however, pose major risks for ransomware, data theft, compliance issues and more. Zero-trust email and file upload solutions that leverage data sanitization, proactive data loss prevention to remove sensitive data, and multiscanning with multiple anti-malware engines already help to greatly reduce the risk of malware and zero-day attacks.
Implementing zero-trust access control for these complex environments can also allow less sophisticated users to have a seamless way to perform security checks in line with the organization’s security policy before granting access to a system. Through zero-trust network access, healthcare institutions can secure cloud, remote and on-prem access, gain instant visibility into who is connected to the network, detect vulnerabilities and deploy automated patches, and enforce endpoint compliance and updates when necessary. Preventing unauthorized access to corporate data can also help organizations meet HIPAA requirements for securing and protecting sensitive patient data from attackers.
Recovering from an Attack
Preparation for an attack is the most important way an organization can recover quickly from a cyber-attack. Because each health system has specific needs and resources, it is essential to involve executives, security and IT experts, legal teams, and communication teams in creating an actionable and tested incident response process. Detecting suspicious activity early and investigating it is an important first step, as well as enduring EDR is enabled. Whether this involves an outside incident response team or internal resources, it’s essential to perform a technical analysis to identify the cause of the incident and initiate the IR plan and enable backup solutions on the endpoints. Containing the attackers while collecting forensic data for ongoing investigations is important, as is notifying local, state, and federal law enforcement agencies. The legal, IT, and communications teams must work together to ensure that regulations are being met and to limit the potential legal and reputational impact of a critical incident.
The scope of the attack impacts the recovery process and the breach notification requirements. Once the ransomware or DDoS attack has been eradicated, organizations must restore data from backups and address any security gaps. Using the lessons learned from the attack, health systems can adjust their IR plan and put in place tactics and security solutions to make it easier to detect and faster to contain future attacks.
Want to learn how OPSWAT can help?

