In the field of cybersecurity, threats continue to evolve, prompting the need for advanced defensive mechanisms. One such shift in attack vectors involves the use of macro-less office files, as demonstrated in the "meme4chan" incident reported by Securonix Threat Labs, which exploited the CVE-2022-30190 Follina vulnerability— instead of macros to weaponize the document and drops an obfuscated Power Shell script, and primarily targeting manufacturing, hospitality, healthcare firms and other business entities located in Germany.
Even as threats have evolved over time, Deep CDR technology still offers robust protection against these macro-less office files attacks. This blog post will illustrate how.
Understanding the Threats
Microsoft’s products now block macros by default in order to prevent macro-based attacks. However, this move has led to a tactics change where attackers turn to zero-day exploit-based techniques to execute their malicious intentions, making these disguised office files a significant risk that can infiltrate a network undetected. In the meme4chan attack, attackers first send a phishing email with a malicious Office file attachment, that exploits a vulnerability in Microsoft Office file when opened. The vulnerability allows embedded objects within the file to execute PowerShell code containing the malicious payload. This ultimately bypasses the malware scanner, disables Microsoft Defender, and finally executes a malicious worm called XWorm.
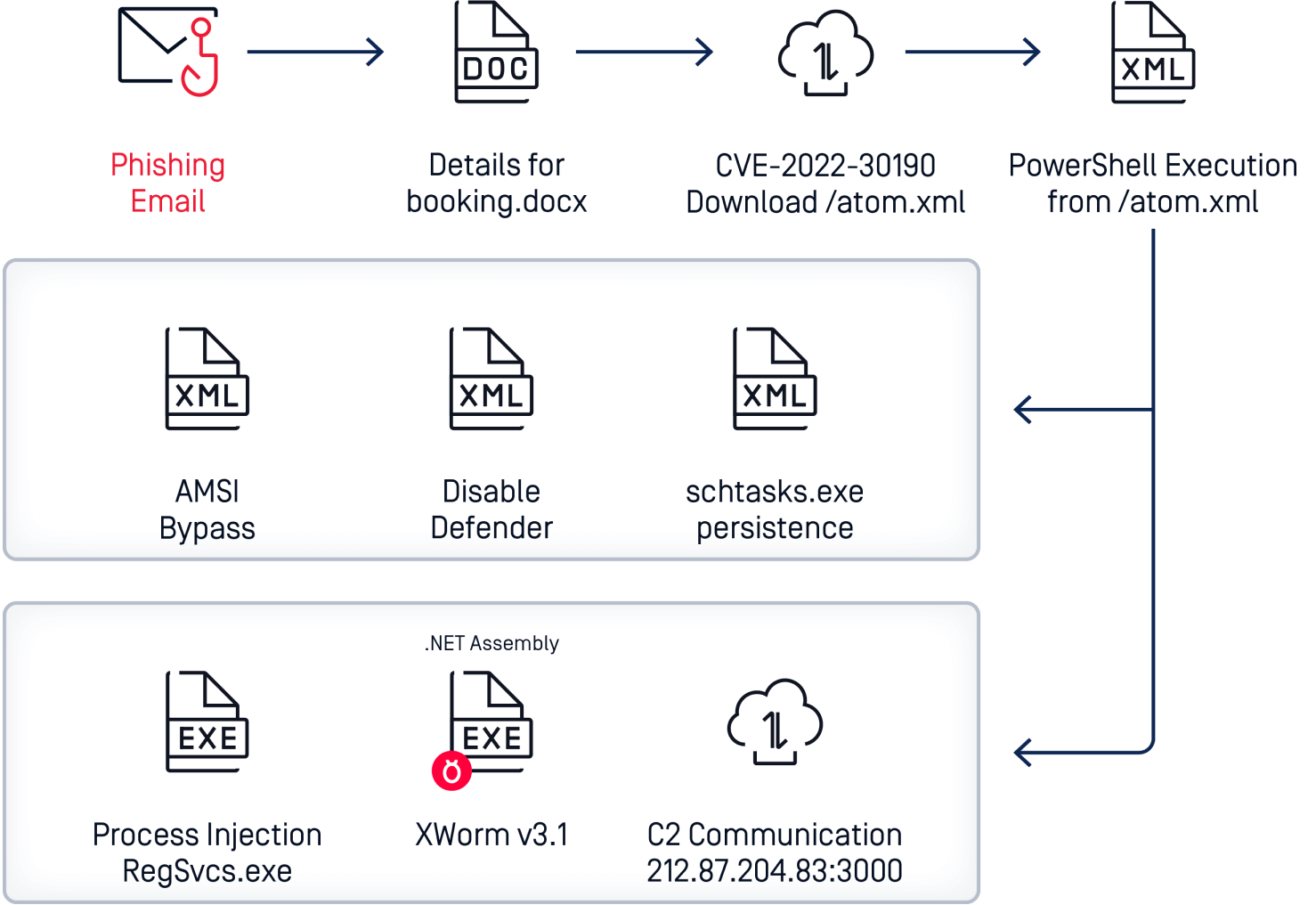
For conventional email security solutions, this attack is impossible to detect, as it does not rely on macros, a common well-known mode of attack. OPSWAT Email Security solution provides the key capabilities to address the risk and prevent similar attacks.
Deep Content Disarm and Reconstruction (Deep CDR)
Deep CDR stands as a powerful countermeasure. This is a proactive, preventive technology that essentially "disarms" all harmful active objects in a file by breaking it down into components and removing or sanitizing potentially malicious elements such as embedded objects, scripts, and macros, whether they are known threats or not. This ensures that any malicious content inside the document will be neutralized before it can be activated, preventing threats.
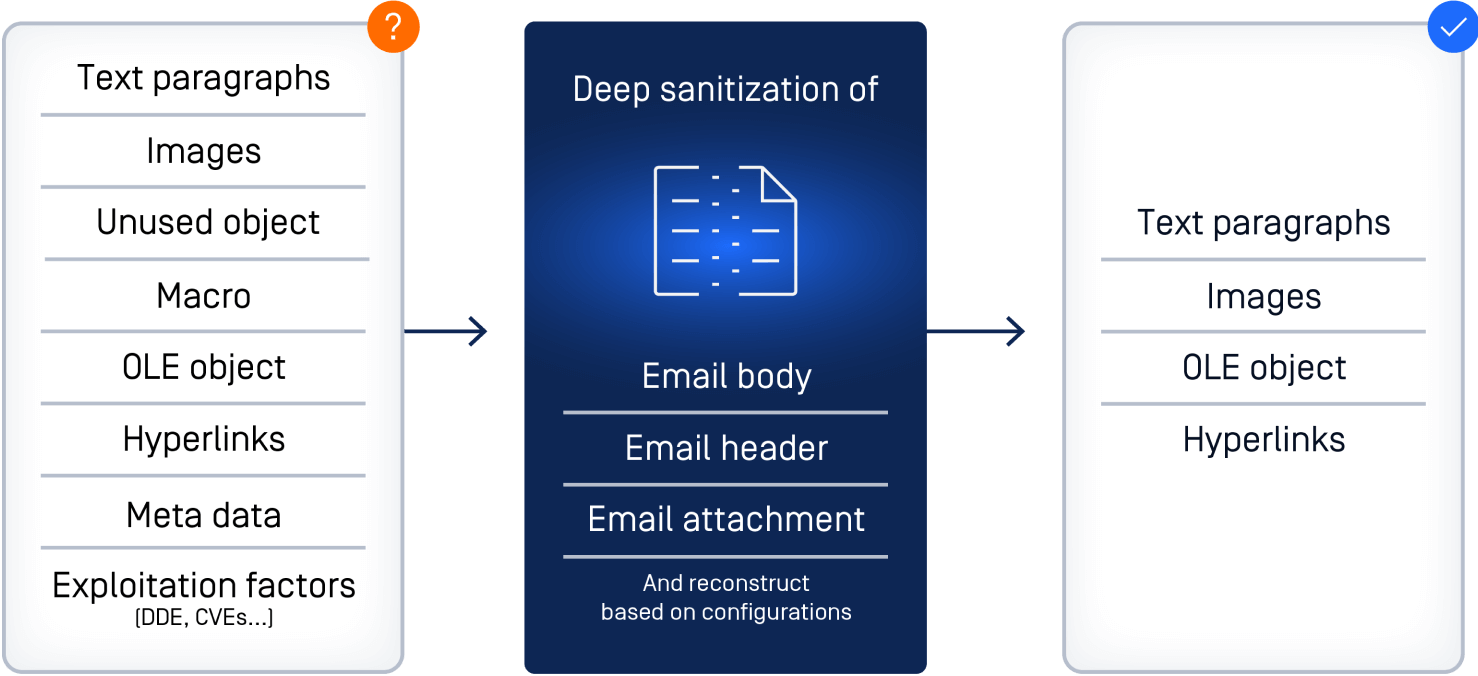
Once the active content is removed, Deep CDR reconstructs the file to its original format, maintaining its usability while ensuring its security status. By sanitizing every file, Deep CDR ensures business operations continue seamlessly without compromising security.
The Advantages of Applying Deep CDR in MetaDefender Email Security Solution
The effectiveness of Deep CDR in combating malicious macro-less office files results from:
- Proactive Protection: Instead of relying on known threat signatures or patterns, Deep CDR disarms all active content, neutralizing potential threats before they can cause harm.
- Preserved Usability: Deep CDR fully reconstructs the files with their functionality after sanitizing them, ensuring that business continuity is not disrupted.
- Comprehensive Coverage: Deep CDR sanitizes a wide range of file types including password-protected archives – which is another common delivery method for malicious payload.
In conclusion, the rise of macro-less office files attacks like meme4chan underscores the need for advanced, proactive email security measures. Deep Content Disarm and Reconstruction (Deep CDR) is an advanced threat prevention technology in OPSWAT's MetaDefender Email Security solution that protects organizations against attackers using unknown and Zero-Day exploits by sanitizing more than 120 file types and emails from malicious active content. Deep CDR ensures that your organization's email security is prepared to combat the ever-evolving cyber threat landscape.

