Adaptive Sandbox for MetaDefender Core 2.4.0 marks a major leap forward in threat detection and enterprise integration. This release empowers security teams to analyze threats faster and with greater accuracy. Explore what’s new and how your threat defenses just got smarter.
Embedded Engine: Next-Level Threat Detection
What's New
Expand detection capabilities with smarter unpacking, deobfuscation, and variant recognition.
- Updated YARA & Malware Config Extraction Logic
Detection rules and config extraction logic have been updated to better identify Lumma Stealer (ChaCha), MetaStealer, and Snake Keylogger variants. - .NET Loader Unpacking Enhancements
Support added for unpacking Roboski and ReZer0 loaders, along with control flow deobfuscation in .NET files to improve payload extraction.
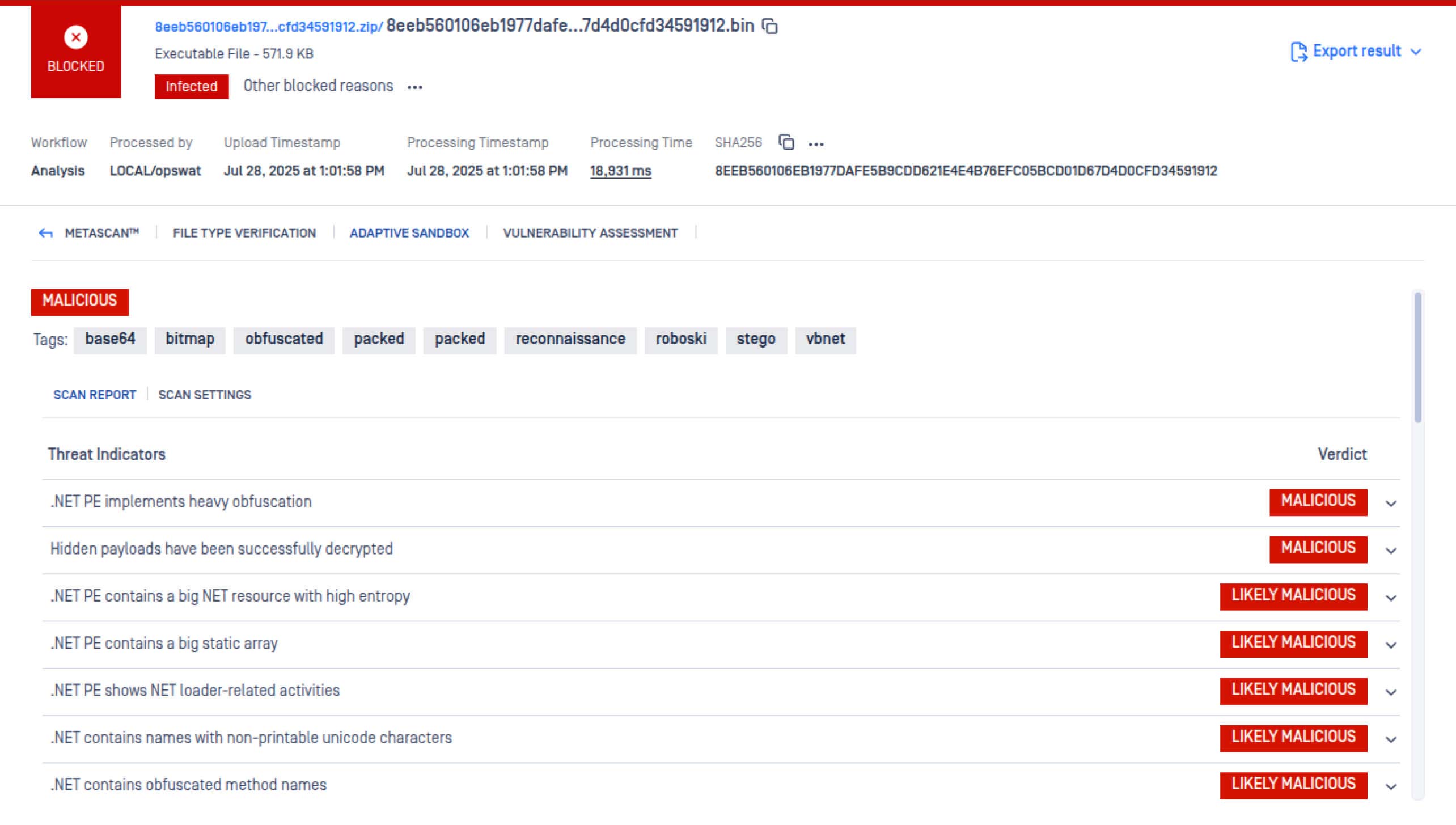
- Control Flow Deobfuscation in .NET Files
Improves unpacking efficiency and exposes hidden payloads in obfuscated .NET samples. - Early Detection for ClickFix Variants
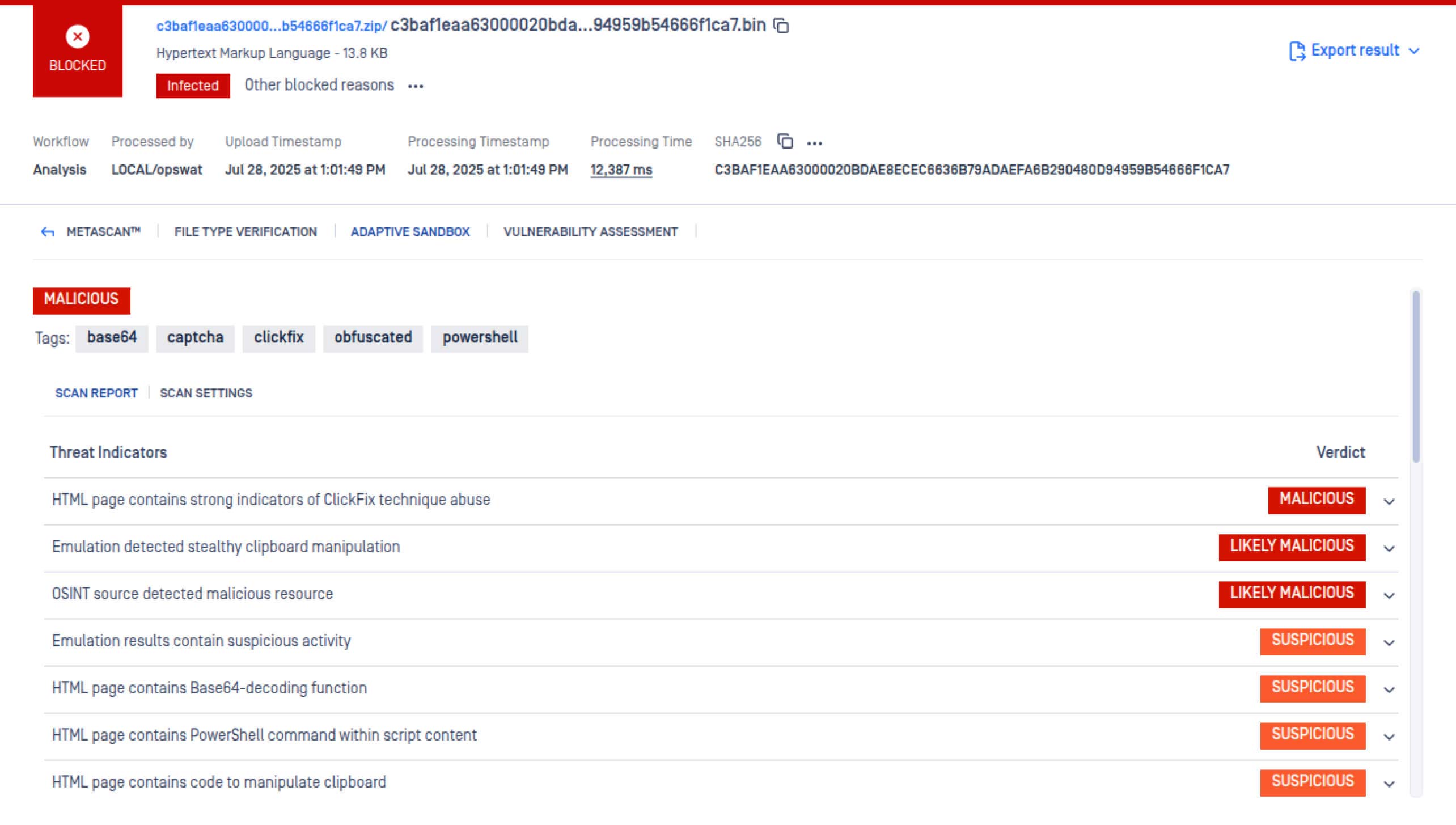
Enabled early-stage detection of ClickFix and related variants addresses a rising trend in social engineering threats.
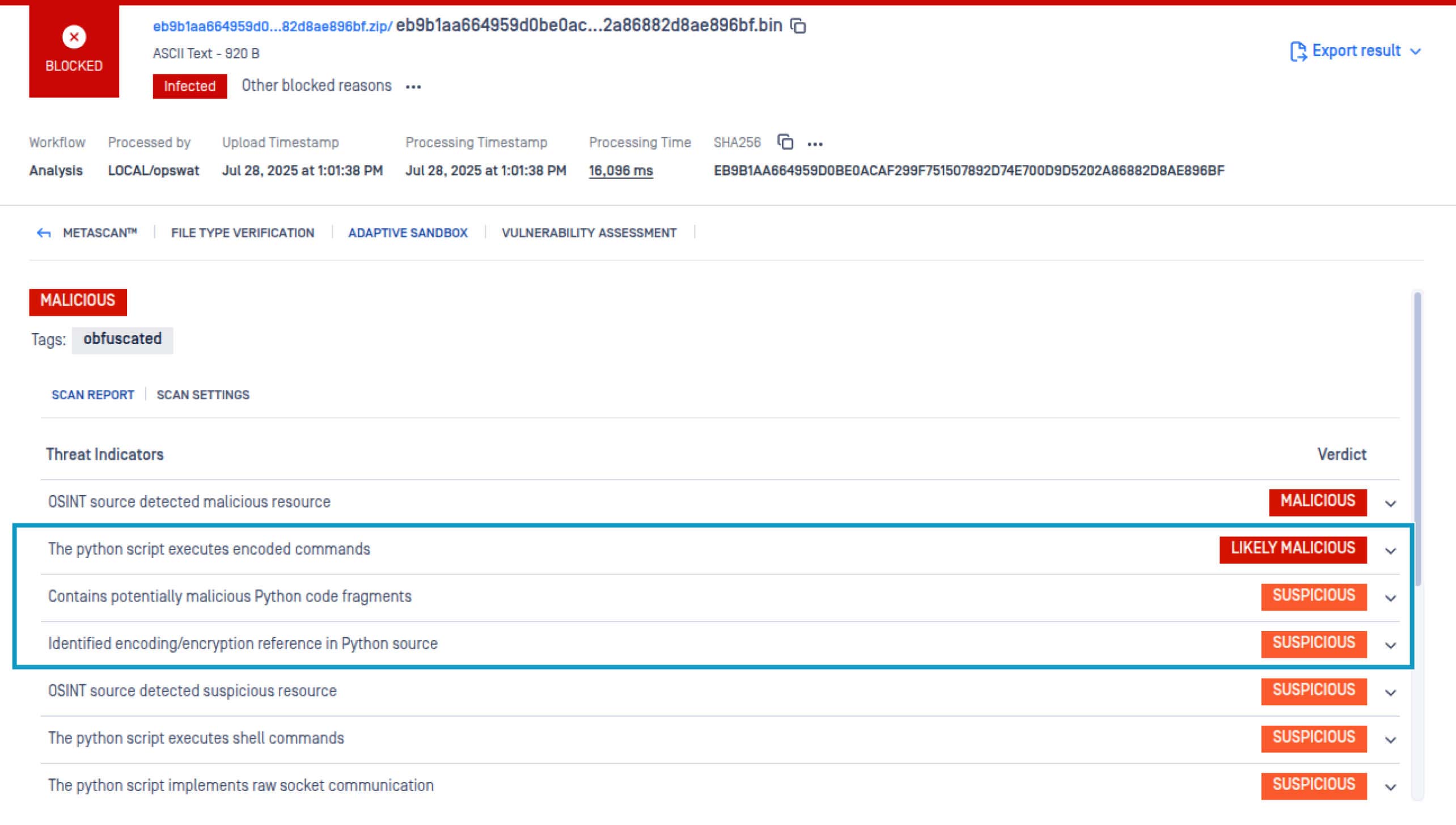
- Automated Decoding of Base64 Commands
Enabled automatic decoding of base64-encoded commands in Python and Bash scripts, revealing deeper obfuscation layers and improving detection accuracy.
- Support for ACCDE File Analysis
Support added for analyzing ACCDE files, extending coverage to Microsoft Access applications and improving visibility into embedded threats.
These additions extend the depth of behavioral insights and surface hidden threats with greater precision.
Remote Engine: Traffic distribution & high availability
What's New
- Load Balancing / Failover: Implemented Round Robin load balancing and failover to ensure even traffic distribution and high availability during node failures.
You may find the standalone release note for your Remote engine, here: Release Notes for v2.3.0 - MetaDefender Sandbox
To learn more, request a demo, or speak with an OPSWAT expert, visit: https://www.opswat.com/products/metadefender/sandbox
Stay ahead of the threat curve.

