IT and OT—The Isolated Islands of Critical Infrastructure
For most IT (Information Technology) and OT (Operational Technology) teams, it is a common sentiment to feel like they inhabit two separate worlds. IT professionals, typically seen as the "white-collar" experts, focus on managing data and digital systems, while OT specialists—the "blue-collar" workers—are hands-on, maintaining the machinery and equipment that keep physical operations running smoothly.
This divide can lead to communication and security gaps, with each side struggling to integrate the other's processes efficiently and securely.
OT workers often perceive IT professionals as being disconnected from "real" work, believing they just sit behind computers, never getting their hands dirty. On the other hand, when IT experts venture into physical OT environments, they frequently find themselves out of their depth, encountering unfamiliar protocols and processes.
In the future, fully integrated IT-OT systems will become the standard, and secure OT environments will be a reality. Currently, however, these two domains often operate like isolated islands—gradually moving closer but still struggling to align in practice.
No matter how complex the challenges are, the need for a unified approach to IT and OT productivity and security is inevitable, and the tools to make that happen are already available.
| Information Technology (IT) | Operational Technology (OT) | |
| Components | Servers, workstations, databases, cloud, security devices, mobile devices, web applications, network devices | PLC/DCS, SCADA, data collectors, sensors, motors and other field devices, protocol converters, manufacturing controllers |
| Operation | Collaborative and interconnected apps, systems, and networks | Island-like isolated systems, independent operation |
| Security Concept | Data-centered approach | Process-centered approach |
| Personnel | “White-collar” workers: system administrators, IT and security engineers, users | “White and blue-collar” workers: operators, maintenance workers, field and automation engineers |
| Management | The operation and maintenance of IT systems are either managed by an internal team or outsourced | OT systems are usually operated and maintained by the suppliers, integrators, or manufacturers |
| Location | Centralized systems in server rooms and data centers | Decentralized, often isolated operations, remote environments |
Decentralized OT Operations
IT systems are typically managed by a single centralized team. In contrast, OT environments are often operated by multiple teams, as it is common practice for the manufacturers of OT equipment, machinery, and production lines to handle maintenance as well.
Depending on the diversity of the technological and manufacturing environment, as many as 8 to 10 different manufacturers might be involved in providing maintenance services. This means that OT management, including OT security, is often decentralized.
In many cases, OT environments operate with decentralized management, which can pose challenges for maintaining consistent security practices across the entire system.
Bridging the Gap Between IT and OT Environments
In such a diverse technological and operational landscape, can unified cybersecurity assessment criteria effectively evaluate IT and OT, especially under the NIS2 directive?
Fortunately, there is a bridge between these two environments, and a unified assessment framework does exist.

Establishes foundational security and privacy controls for IT systems, focusing on confidentiality, integrity, and availability. It categorizes systems by risk impact (low, moderate, high) and defines controls to mitigate these risks effectively, ensuring compliance across IT environments.

Extends these principles to OT environments, such as SCADA and Industrial Control Systems (ICS). Key adaptations include mandatory manual checks where automation is infeasible, and reclassification of security controls to address OT-specific risks.
These frameworks, though developed in the U.S., have gained international recognition for their comprehensive approach to cybersecurity. They align closely with modern regulatory requirements, such as the NIS2 Directive, by offering a unified strategy for securing IT and OT systems while addressing compliance with evolving global standards.
The Role of Managed File Transfer in IT-OT Convergence
In the context of IT-OT convergence, ensuring the secure transfer of data between these traditionally isolated environments is essential. MFT (Managed File Transfer) solutions offer a structured, secure, and automated approach to data transmission that addresses both the operational demands of OT systems and the cybersecurity expectations of IT environments.
MFT integrates advanced security mechanisms, including:
- End-to-end encryption to safeguard data confidentiality
- Role-based access controls to ensure only authorized personnel can access sensitive data
- Comprehensive audit trails that provide visibility and traceability of data transfers
Together, these features collectively address the unique security and operational challenges of IT-OT convergence by:
- Reducing complexity in meeting regulatory standards through automated security controls
- Providing real-time logging and monitoring, which aids in fulfilling incident reporting and risk management requirements
- Minimizing manual efforts in compliance tracking, allowing organizations to focus on strengthening overall security
Alignment of NIST Frameworks with NIS2 Directive
The principles outlined in NIST 800-53 and NIST 800-82 align with the objectives of the European NIS2 Directive, which aims to enhance cybersecurity in critical infrastructure sectors. These frameworks support robust risk management, incident reporting, and supply chain security measures, ensuring comprehensive protection across IT and OT environments.
One of NIS2’s core objectives is to establish a consistent approach to organizations with critical infrastructures, focusing on security measures such as access control, encryption, and incident reporting. This directive mandates that organizations implement systems capable of ensuring data confidentiality, integrity, and availability, while also enabling the detection and mitigation of cyberthreats.
These requirements are particularly critical in OT environments, where operational disruptions can have far-reaching consequences. To meet these regulatory demands, Managed File Transfer solutions are indispensable as they incorporate essential security measures that directly address NIS2 requirements.

The Future: Full Convergence
The convergence of IT and OT systems is no longer a distant vision—it is an immediate necessity. As organizations adopt integrated architectures, the potential to secure OT environments is achievable today with advanced solutions tailored to their unique challenges.
- Encryption: OT components are increasingly equipped with encryption capabilities, and solutions like Managed File Transfer support secure data exchanges across systems while enabling data exchange even in mixed technology environments.
- Audit Logs: Enhanced logging capabilities ensure OT systems can generate detailed, actionable logs, enabling comprehensive visibility and compliance.
Achieving secure OT systems today requires the expertise of IT professionals adapting to OT-specific cybersecurity needs and OT specialists embracing IT-driven approaches. Solutions like MetaDefender Managed File Transfer (MFT) bridge this gap by providing seamless, secure, and traceable data transfers, ensuring compliance with evolving regulations such as NIS2.
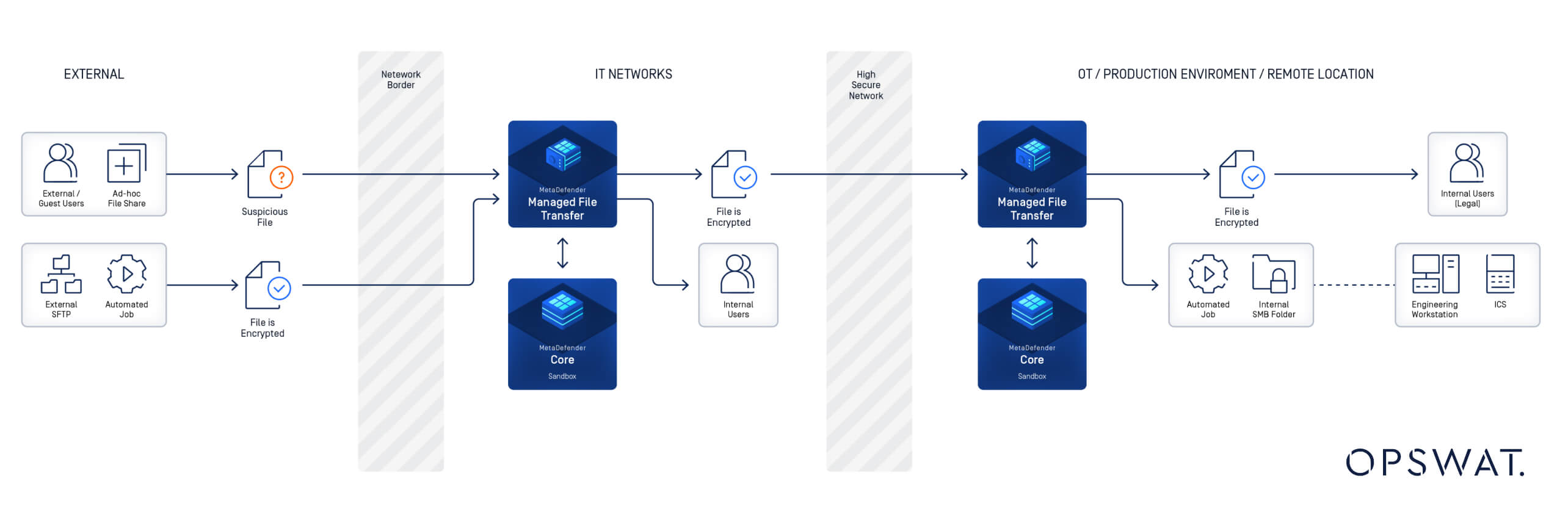
OPSWAT’s industry-leading managed file transfer solution, MetaDefender Managed File Transfer (MFT), is at the forefront of IT-OT convergence, providing advanced security measures designed specifically for critical infrastructure environments:
- End-to-End Encryption: TLS 1.3 and AES-256 encryption secure data both in transit and at rest.
- File Integrity Verification: OPSWAT's checksum algorithm ensures file integrity, maintaining trust and security throughout data transfers.
- Granular Access Control: role-based and granular permissions ensure secure, controlled access to files and workflows while preventing unauthorized data breaches and system downtimes.
- Advanced Security: The MetaDefender Core cybersecurity engines—Multiscanning, Outbreak Prevention, Sandbox, and File-Based Vulnerability Assessment—mitigate sophisticated file-based attacks and facilitate compliance.
- Specialized Deployments for Regulated Environments: MFT-to-MFT and MFT-to-multiple MFT deployments address the compliance needs of highly regulated industries.
Organizations no longer need to wait for the future to achieve IT-OT integration and secure operations; the tools to safeguard critical systems are available now.
To learn more about how MetaDefender Managed File Transfer (MFT) can support your IT-OT convergence and ensure regulatory compliance, visit our product page.