MetaDefender Endpoint Security SDK™
Powerful Endpoint Security Software Development Platform
The MetaDefender Endpoint Security SDK (formerly known as OESIS) is a cross-platform, modular framework that enables developers and technology vendors to integrate advanced endpoint protection capabilities—quickly and efficiently—into their products.
Trusted by global leaders like Cisco, Palo Alto Networks, HP Aruba, IBM, and more, our patented technology has been powering secure applications for over 15 years.
Reduce Development Time
Pre-built security modules and streamlined APIs let you accelerate time-to-market without sacrificing quality or protection.
Cut Development Costs
Minimize resource investment by leveraging a ready-to-integrate SDK—reducing the need for in-house security development.
Reduce Maintenance & Support Costs
Ongoing updates, threat intelligence, and compliance-ready features lower your long-term maintenance burden and support overhead.
Secure Your Endpoints with Customizable SDK Integration
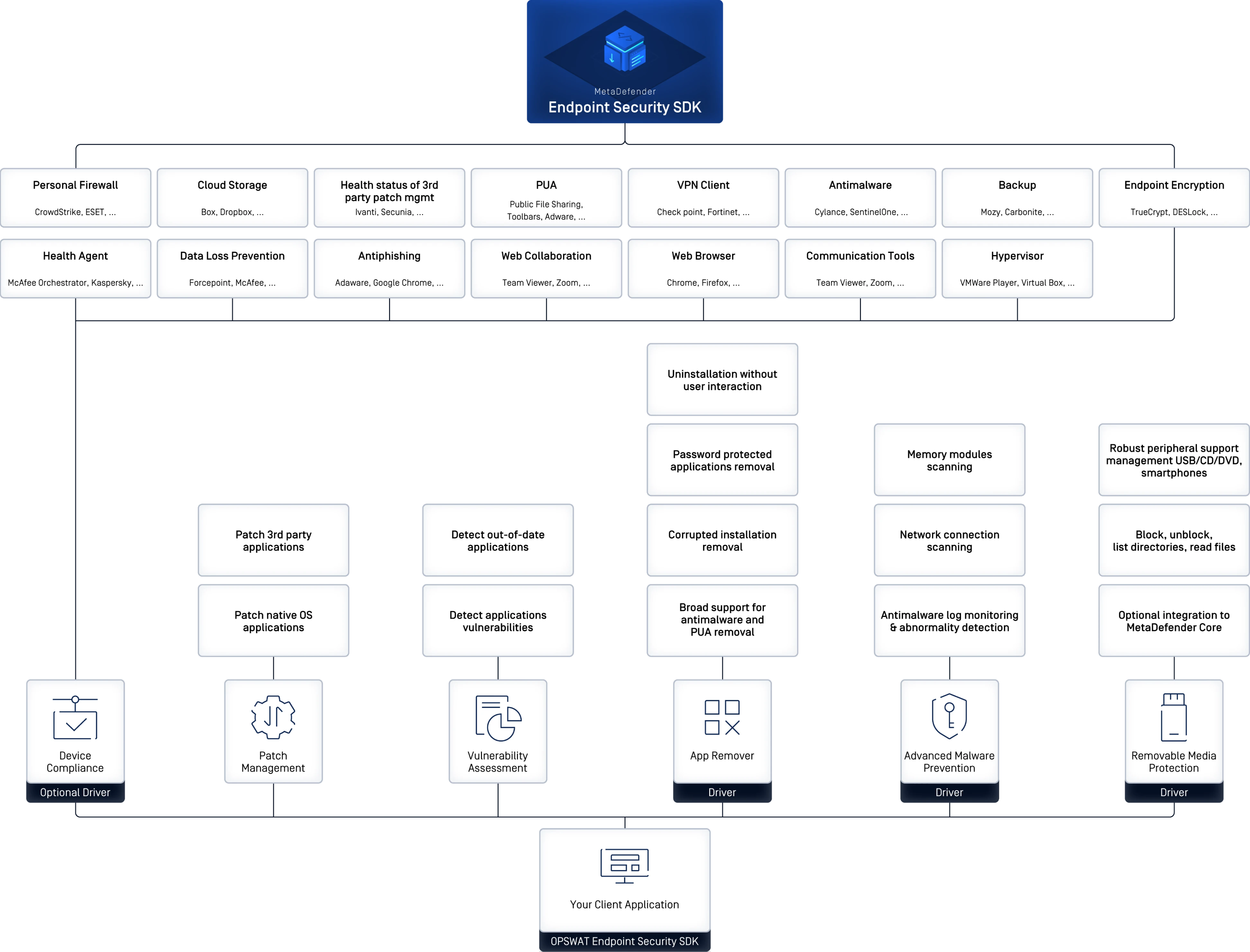
Embed powerful endpoint security features directly into your applications and enforce device trust. Our SDK offers APIs for device posture, vulnerability scanning, patch management, malware detection, and removable media protection—fully customizable, lightweight, and easy to integrate.
Device Posture
Discover, detect, and enforce policies across 5,000+ applications.
Patch Management
Automatically detect missing patches and remediate vulnerabilities for hundreds of third-party applications and operating systems.
Vulnerability Assessment
Identify, assess, and map over 47,000 unique CVEs and 100,000+ vulnerability instances.
AppRemover
Cleanly uninstall unwanted or out of compliance applications without user intervention.
Removable Media Protection
Protect against threats posed by USB drives, CDs, DVDs, and other peripheral devices.
MetaDefender Endpoint Security SDK Features
With the help of OPSWAT's OESIS framework, MetaDefender Endpoint Security SDK offers an open development design. Engineers can implement various solutions with this endpoint security software.
Supported Platforms
Platforms* | Version |
|---|
Other distributions may also be supported (**)
MetaDefender Endpoint Security SDK Integration
Sample MetaDefender Endpoint Security SDK projects are available in the following programming languages: C, C++, Python, Ruby, and Objective-C.
C++ Libraries
Our shared library is a native C++ integration, easily adaptable to other endpoint languages.
JSON
Simple JSON in, JSON out protocol for invoking the functionalities







