SVG* Files: The New Face of Malspam Payloads
Over the past several months, OPSWAT threat intelligence analysts have observed commodity malspam and credential phishing campaigns delivering weaponized SVG files to the usual mailing lists (every inbox they can reach).
One of the two critical differences between these SVG files, to what one might expect from any regular email containing embedded images, is that the sender is likely instructing recipients to open these files by indicating a sense of urgency through a crafted narrative common in malspam campaigns - such as unpaid invoices, missed voicemails, or fake instructions from upper management (lures).
The other difference is that these SVG files contain malicious JavaScript or embedded links to fake landing pages for credential harvesting or personal information theft.
For seasoned security practitioners, this file type switch should not come as a surprise. Monitoring file-based tradecraft trends over the years has shown that threat actors are adept at identifying file types that provide opportunities to evade defenses and increase delivery rates to target users.
Why JavaScript is the Real Payload
Those tracking specific actors could hypothesize with high confidence that this file tradecraft pivot was a logical next step in advancing campaigns to maintain low detection coverage against current security countermeasures.
As ‘living off the land’ techniques tend to be favored to ensure widespread effectiveness of campaign runs, a tried-and-true favorite will generally be the most common denominator: embedded JavaScript.
The ability to execute arbitrary JavaScript in a commonly observed file type grants threat actors access to their thoroughly developed arsenal of obfuscation techniques. This gives adversaries a period to spin up campaigns with low detection rates for the low cost of adapting their old tricks to a new container.
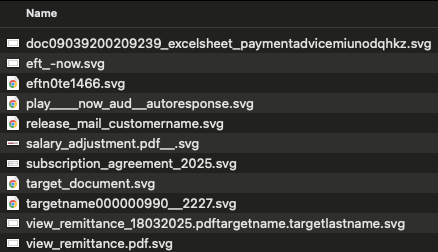
Where we’ve commonly seen the embedding of these types of JavaScript payloads is in direct HTML files, PDF files, and even plain JavaScript (.js) files. The ability to wrap the active content in a file type, typically considered less harmful (an image file), delivers threat actors inherent success rates.
Conversely, attack surface reduction that has been focused on technologies such as productivity applications like Microsoft Office and OneNote has not necessarily scaled into some of these emerging and fringe file types.
Examples below illustrate how attackers embed JavaScript in different file types, including HTML and SVG, to execute malicious functions and evade detection.
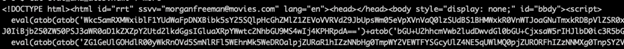
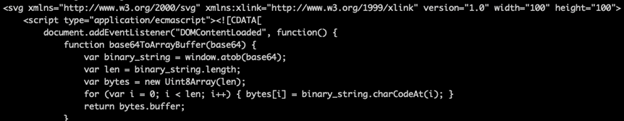
The problem inevitably leads to discussions about why JavaScript has such a large attack surface in the web space and what cost effective solutions are available to reduce exposure from malware with JavaScript in the delivery sequence. This may be a difficult proposition for certain organizations depending on operational needs.
This also falls within the problem space of tools and frameworks commonly used by vendors and developers that end up being abused by criminal elements (a discussion topic for another time). While it is debatable whether the average user needs JavaScript in widely used applications such as email, overreactions such as Steve Jobs’ open letter regarding Adobe Flash may lead to ill-conceived practices with unforeseen consequences.
Malware-as-a-Service at Scale: What SMBs Should Know
While these commoditized campaigns—often powered by malware-as-a-service and affiliate networks—lack the sophistication of nation-state operations, they make up for it with sheer volume and rapid iteration, enabling widespread impact at scale. The large number of actors in this space can be challenging for small to medium-sized organizations, which may have limited access to security tools to mitigate these threats.
Defending against this common threat then falls on the defenders tasked with weighing expected or legitimate use cases against the potentially malicious use of JavaScript within their environments.
Engineering Security into Your File Analysis Pipeline
Organizations with complex development pipelines will need to clearly define acceptable use policies for file types across various engineering domains to balance productivity with security.
Defenders maintaining detection based on YARA signatures likely have existing coverage for suspicious JavaScript within HTML files; adapting these rules or creating SVG specific counterparts enables detection engineers a quick avenue to covering familiar threats leveraging previously unseen file tradecraft.
Resourced detection engineers may opt to take this a step further and explore other file types that are easily user executable and support JavaScript to cover future threats.
Comprehensive File Analysis: Antidote to Malicious File Tradecraft
At OPSWAT, we believe that cautious users are a key element in defending against the onslaught of attacks. But we also know that putting all expectations on our users to recognize and avoid carefully crafted lures is not a realistic prospect.
For this reason, we’ve developed effective, highly automated means to detect malicious files at scale and within common workflows. MetaDefender Sandbox can analyze and detect SVG files that may come through connected pipelines and integrations, helping protect email and web pathways with adaptive analysis capabilities.
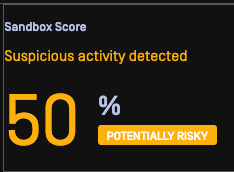
Here’s a sample SVG file illustrating Deep CDR capabilities identifying active JavaScript content in the file and identifying risk items.
Sample Hashes from Active Campaigns
Below are file hashes of observed malicious SVG samples for your threat hunting and YARA rule development.
37ec9cea8684862bf90a77750d299c402b22fd45227394f9c021271c220efde5 |
af5448f719717b02658fa6125867891c9a8398d7962c8351c52581222123812f |
e078956a4722bc5352b9f3579b0f347442e6d8bfae474989005748691c96ad61 |
c3bea88d3dd9af95a7abed667395ec7e97b9d03234e96f1deb58246eda79c480 |
0c635495ae1f7f5abb54758774e0cf3a45de833e4a625fa73b66b6fa68dba016 |
7e4196e0ea594313440db113f33e3e0cb324d48b7e7067f49692d896ced61dbd |
380228c46ad165986caf5be62c4e53104d149de19fdcd8bf1e7d0d15d9e2d734 |
20e7a72bee139660755215f2aad7695cc5b2042e3bc93d96b4da6a1ddb9d3b5c |
a559ba903d3ffe755e54bd9d74d338ce8b4a140f1495f31d380e5875ea110f77 |
d050b960f05f939598565d4ea9f54743116a5fff579de171e2380354627cf45d |
ff342515e4ab999397f9facfd3185ab251dab872a425a7a7a298971d013285ad |
ff7bb63fa228e01c0fe5f214db0b5cc60e67f0b8ba2d7984bdc6aa34bf00fd9a |
Customers using MetaDefender Sandbox benefit from rapid threat intelligence updates, including emerging file formats like SVG. Once detection logic is deployed, threats such as those discussed in this blog are automatically identified and quarantined, ensuring continuous protection even as attacker tactics evolve.
Final Thoughts: File Formats Are Fluid—So Should Your Defenses Be
Attackers constantly evolve their methods, and the use of JavaScript-laden SVG files in phishing campaigns is a prime example of this adaptive tradecraft. While the file extension may change, the core threat—execution of obfuscated scripts—remains the same.
To stay ahead, defenders must continuously refine detection techniques, adapt existing rules to new formats, and leverage automated analysis tools like MetaDefender Sandbox to uncover malicious behavior buried in unexpected places. Relying on user vigilance is not enough—scalable, intelligent defenses are now essential.
*What Are SVG Files?
SVG, or Scalable Vector Graphics, is a widely used file format for displaying vector-based images on the web. Unlike traditional image formats like JPEG or PNG, SVG files are text-based and written in XML, which allows them to include interactive elements and even embedded scripts such as JavaScript. This flexibility makes them useful for developers—but also attractive to attackers looking to hide malicious code in plain sight.

