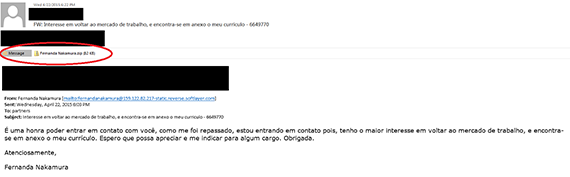
A few weeks ago, an OPSWAT employee received an unknown email with a suspicious file attachment. Following the best practices for receiving unknown emails with such attachments, we scanned the file on Metascan Online. Not to our surprise, the file was infected with malware.
Banload Threat embedded in an email attachment - Click to enlarge
The threat is a Trojan named Banload (SHA256: 55A78068A8668ED82DADE7BB79365D28AD038674F6160B199C6F8FAE7B4B807A), that steals PII and attempts to send it back to the attacker. This particular type of malware is similar to the Banker family of malware, a Trojan that steals banking credentials and other sensitive data, which is then sent back to the remote attacker. The severity level is considered Severe, meaning this threat has the potential to cause some serious damage if it were to gain control of a user's device. Banload has been around for years, just in different variants. References are mentioned below for further reading.
A few sample threat names for the Banload Trojan as detected by different anti-malware engines on Metascan Online:
- MSIL/TrojanDownloader.Banload.DD
- MSIL/Banload.COV!tr
- Troj/MSIL-COV
- Trojan-Downloader.MSIL.Banload
- Trojan.MSIL.Banload.DD
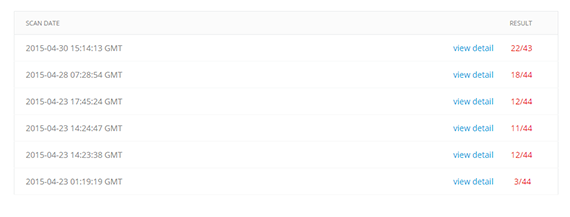
By looking at the scan results for a particular file over time, you can see how detection rates change or remain constant. If a threat is fairly new, detection may be relatively low when the initial scan is performed. As more anti-malware vendors recognize the threat, detection rates will increase. When we first ran this file through Metascan Online, only 3 anti-malware engines detected it. When the threat was rescanned less than 24 hours later, the detection jumped to 12 engines. About a week later, the detection was 22 engines.
Detection rates for Banload Trojan by date - Click to enlarge
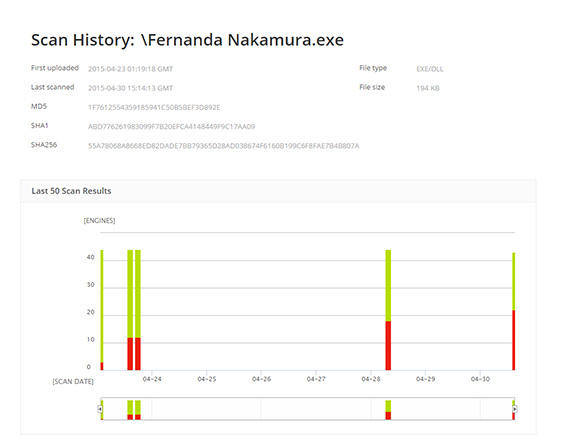
Scan History over time - Click to enlarge
When looking at a threat found in a file, it's important to develop as much context about the threat as possible. Metascan Online's Scan History feature provides that additional context by displaying the detection pattern of the threat. After taking a look at this pattern, you can start to ask yourself some important questions about the detection rate. Did detection increase in a matter of days or did it take a couple of months? Is the detection consistent at 3 engines, or at 30?
In this example, we are looking at the detection pattern of the Banload Trojan. It took a week for 22 anti-malware engines to detect this particular threat. If detection had been consistent at 3 engines over several months, it could have indicated a possible false-positive. Comparatively, If detection had increased over a couple of months it would have indicated a much slower spread of the malware. Based on the detection pattern of the Banload Trojan, we can determine that this threat was particularly widespread, as a majority of engines detected the threat within the first week. With our Scan History feature, we are able to track the detection of this threat from its initial scan.
Along with scanning files, you can also perform hash lookups or check IP addresses for threats on Metascan Online. Stay safe out there, and happy multi-scanning!
References:
http://malwaretips.com/blogs/trojan-msil-removal/
https://www.f-secure.com/v-descs/trojan-downloader_w32_banload_fvq.shtml
http://www.eset.com/us/threat-center/encyclopedia/threats/win32trojandownloader%20banloadoxp/