The USB Attack Landscape
Peripheral and removable media like USB devices have been essential tools for both individuals and organizations, mostly because they allow for easy data storage and transfer. However, their popularity has also made them a common target for cyber criminals. Throughout the years, malicious actors have taken advantage of vulnerabilities in USB devices to carry out complex cyberattacks, leading to compromised data integrity and system security. Despite the growing awareness of such risks, many users remain unaware of the potential dangers posed by seemingly harmless USB devices. In fact, these devices may appear harmless at first glance, but they can function as keyboard, mouse, or other peripherals once they gain access to a device, thereby jeopardizing its security.
In 2010, Stuxnet emerged as a landmark cyberattack that utilized USB drives, targeting Iran's nuclear facilities. The attack was executed through infected USB drives, enabling Stuxnet to infiltrate ICS (industrial control systems) and specifically target PLCs (programmable logic controllers) that were responsible for disrupting uranium enrichment processes. This occurrence emphasized the destructive repercussions of attacks facilitated by USB devices and underscored the necessity of comprehensive cybersecurity measures to protect critical infrastructure.
Types of USB-Based Attacks
In the context of USB security, previous attacks primarily focused on exploiting vulnerabilities related to USB device storage, Autoplay USB drive-related malware, and maliciously modified USB drivers, often resulting in buffer overflow attacks for privilege escalation. However, recent trends indicate a shift towards utilizing keystroke/mouse click injection attacks or reprogramming the Microcontroller. These attacks are executed through non-USB HIDs (human interface devices) disguised as keyboards or a computer mouse, with their firmware ingeniously modified. Additionally, the USB device can also be used to capture network traffic by mimicking a malicious USB as a USB Ethernet adapter. This enables the USB device to serve as a DHCP server, routing traffic through a malicious DNS or presenting the host with a malicious default gateway.
In addition to other tactics, attackers also use firmware updates and USB drivers in USB-based attacks. If a host initiates a malicious firmware update on a USB device with modified firmware, the attacker can reprogram the USB device and use it to compromise the host. In the case of a USB driver attack, the attacker might trick the host to download a malicious driver, which could enable code execution or exploit a buffer overflow vulnerability on the victim's system.
Researchers at Ben Gurion University of the Negev in Israel have grouped USB-based attacks into four primary categories, which include a comprehensive list of 29 different types of USB attacks: Programmable Microcontroller, Malicious Re-programmed Peripherals, Non-Reprogrammed Peripherals, and Electrical.

In the context of electrical-based USB attacks, the USB killer is a significant concern. When it is connected, this malicious device delivers powerful electrical shocks that can cause irreversible damage to the host's components.
USB HID Protocol
The host identifies the type of USB device connected to it by performing a process called device enumeration. During this process, the host communicates with the USB device to obtain information about its capabilities and functionality. This information includes the USB class code of the device, which identifies its type, such as a keyboard, mouse, adapter, or another HID.
The USB HID protocol acts as a standardized approach for communication between peripheral devices, like keyboards, computer mouse, and other input devices, and the host computer. By setting a series of rules and specifications, this protocol ensures a smooth data exchange between these devices and the computer, allowing users to interact with software applications in an effective manner.
Through the HID protocol, devices transmit data packets containing information about user inputs, such as key presses, mouse movements, and button clicks, which are then interpreted by the host operating system. This protocol plays a vital role in ensuring compatibility and interoperability between various input devices and computer systems, making it a fundamental component of modern computing.
Keystroke Injection Attack
A keystroke injection attack, which is a specific type of USB attack, manipulates USB devices to insert unauthorized keystrokes into the targeted system. Keystroke injection attacks leverage the HID protocol to inject malicious keystrokes to a target system, bypassing traditional security measures and multiple security layers, including GPOs, firewalls, antivirus programs, and even Windows Defender, leaving your system vulnerable to unauthorized actions. This attack achieves seamless code execution without user intervention by presenting itself as a USB HID keyboard, and then "typing" in keyboard shortcuts and commands. The keystrokes are inputted so quickly that they are invisible to the victim, happening in the blink of an eye.
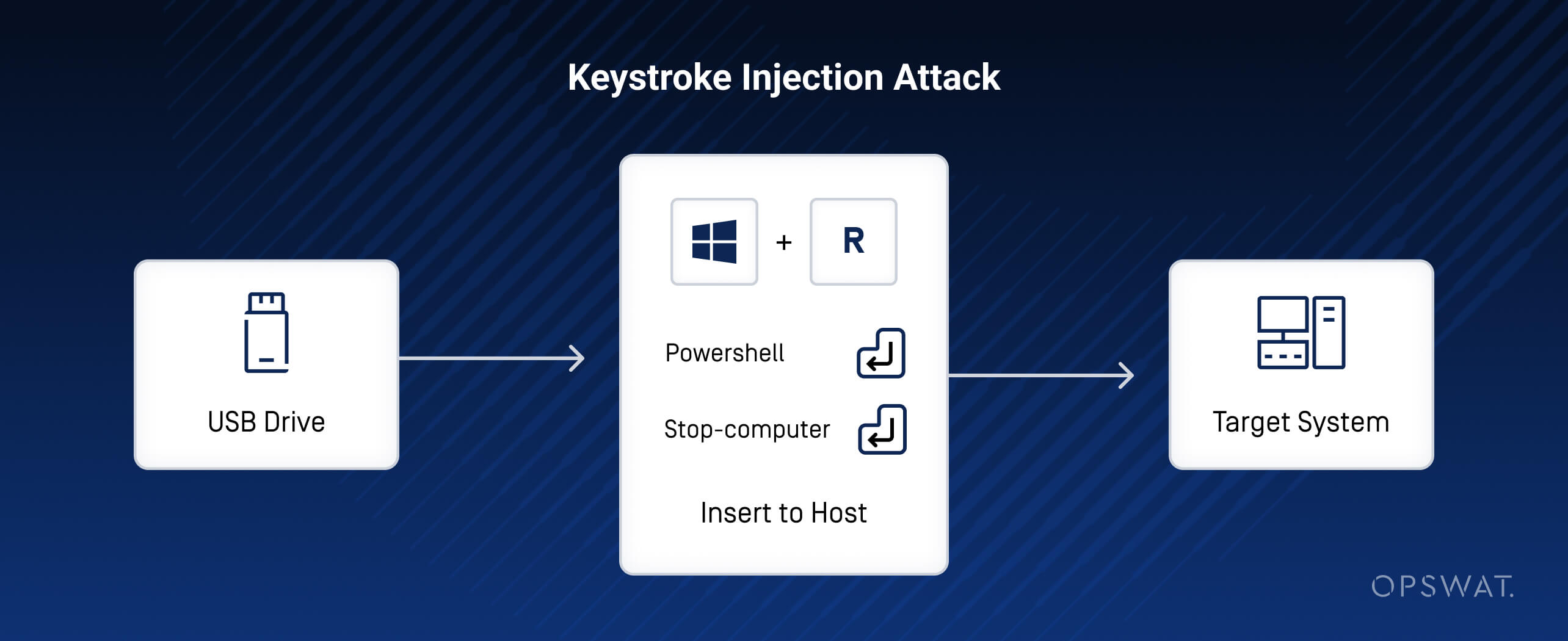
Simulate the Keystroke Injection Attack with USB Rubber Ducky
A “USB Rubber Ducky” is a formidable pen-testing tool for keystroke injection that was developed by Hak5 in 2010. It is a small USB device with a design that resembles a standard USB drive, but functions as a keyboard. Once plugged into a computer, the Rubber Ducky can instantly type out pre-programmed keystrokes at a rapid pace, enabling the execution of commands and scripts without any user intervention. This feature makes it a versatile tool for various cybersecurity uses, such as penetration testing and simulating USB-based attacks.
To use the USB Rubber Ducky, a payload needs to be designed, converted into a binary file, and then loaded onto the device. Once these steps are completed, the malicious user can execute actions on the victim's device by emulating a keyboard.
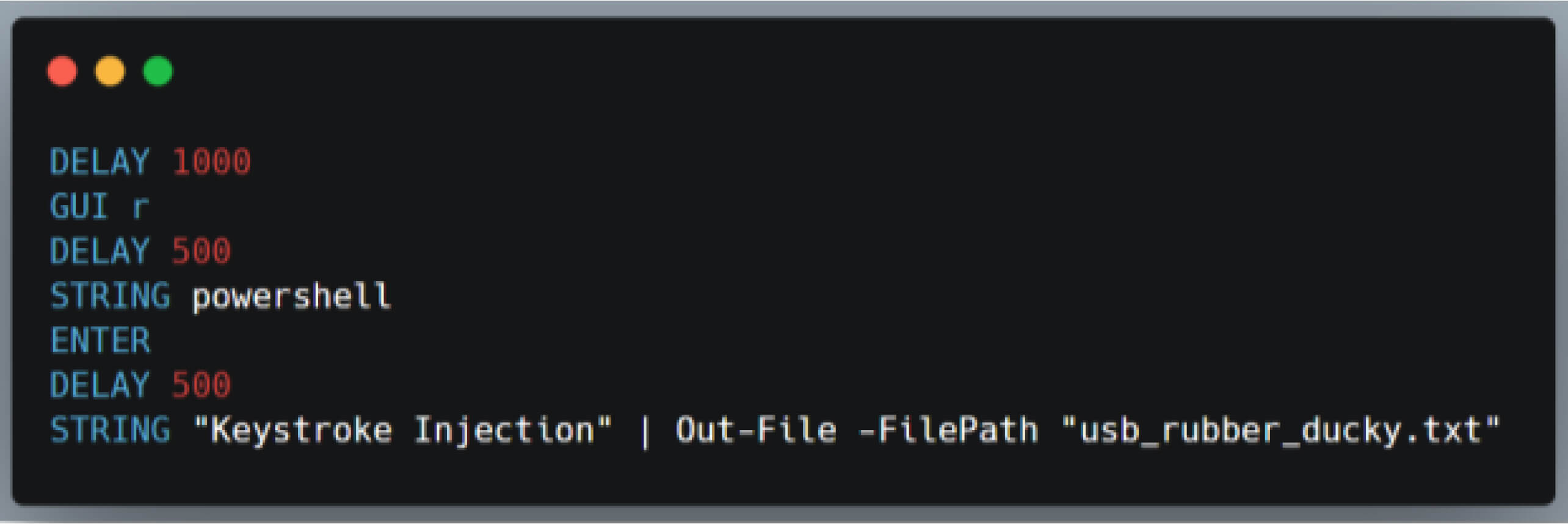
The USB Rubber Ducky uses DuckyScript as its programming language, and the payload will be written using this syntax. Below is a DuckyScript payload that allows a file named "usb_rubber_ducky.txt" containing the text "Keystroke injection" to be written to the victim's device when the malicious USB device is inserted.
Imagine the innocent act of plugging in a USB drive into your laptop, without knowing that it could set off a keystroke injection attack that operates without your awareness. This covert attack can secretly open numerous services and subsequently take over your device, putting your device's security at risk and jeopardizing your sensitive data. It's truly disturbing to acknowledge the potential danger stemming from a seemingly harmless USB device. Let's examine the video below to comprehend the severity of this threat.
Mitigation
At OPSWAT, we adhere to a "Trust no file. Trust no device.™" philosophy, which focuses on deploying zero-trust solutions and patented, market-leading technologies across every level of our customers' critical infrastructure. We secure networks, data, and devices by solving their challenges from the plant floor to the cloud, worldwide. We understand the cybersecurity risks posed by peripheral devices and removable media to essential systems. To address this, we have developed MetaDefender Kiosk, an advanced peripheral and removable media sanitization station, which helps prevent many attacks from USB devices.
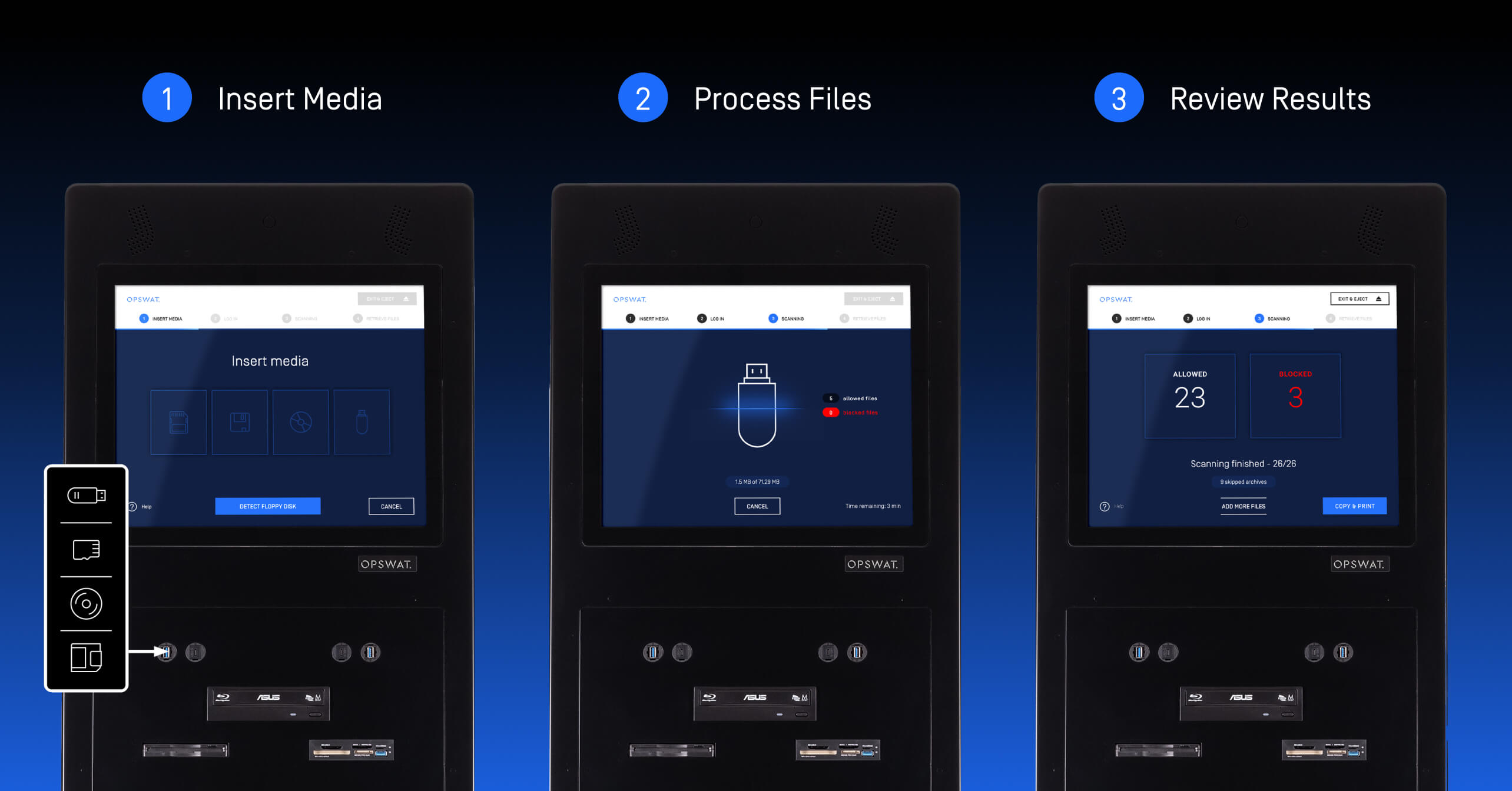
MetaDefender Kiosk helps protect your assets by enabling control over the flow of data into and out of your organization. It can be used as a media scanning station on your own hardware or on OPSWAT's Kiosks. Media such as USB devices, DVDs, SD cards, flash drives, or floppy disks are processed by Kiosk. After the scan is complete, Kiosk generates a detailed report.
With the built-in MetaDefender Kiosk hardening measures, Kiosk significantly enhances its immunity against USB attacks.
The below video demonstrates the effectiveness of the MetaDefender Kiosk in safeguarding against USB-based attacks, particularly those employing the USB Rubber Ducky.
Talk to one of our experts today and discover why the MetaDefender Kiosk is the critical advantage in preventing peripheral and removable media-borne threats.
Loc Nguyen is a Senior Penetration Tester at OPSWAT. He proactively enhances the security of OPSWAT’s products and safeguards them from potential cyberthreats before they reach customers. Additionally, he actively shares his cybersecurity expertise with colleagues and students in the OPSWAT fellowship program.

