The nuclear industry is a critical sector where a security breach can lead to catastrophic events. Section 73.54 of NRC 10 CFR (1), the Code of Federal Regulations established by the Nuclear Regulatory Commission, requires nuclear plants to have cybersecurity programs in place. This requirement falls under the physical security program of nuclear power plants and calls for measures to isolate critical digital assets (via airgaps or other isolation methods), controlling and securing the use of mobile devices such as laptops, and continuous monitoring through both active and passive malware analysis.
Besides NRC’s regulatory requirements, NEI 18-08(2], a guideline developed by the Nuclear Energy Institute, states that nuclear plants are required to implement protective measures against cybersecurity threats introduced by mobile devices such as laptops from third-party vendors, and organizations that implement BYOD (bring your own device).
With this growing need for robust security solutions, critical infrastructure supply chains can’t rely on traditional methods such as single antivirus scanners.
Challenges to Securing Nuclear Supply Chains
Between 2022 and 2023, the National Institute of Science and Technology recorded a hike of nearly 2,000 system vulnerabilities with an increase of nearly 60 additional threats per day, according to a recent analysis from POLITICO[3]. Given these alarming numbers, rigorous cybersecurity measures are essential not only to meet regulatory requirements, but to ensure uninterrupted service. However, nuclear facilities and other critical infrastructure providers face numerous challenges when implementing these cybersecurity measures:
Risks Posed by Mobile Devices
- Compliance requirements adherence: OT air-gapped networks require strict adherence to compliance mandates, such as the previously mentioned NRC 10 CFR and NEI 18-08 requirements. Ensuring that third-party vendor devices are compliant with the latest regulations is challenging, as out-of-policy devices can lead to severe penalties and network disruption.
- Sensitive data leakage: third-party devices that enter secure zones can accidentally or maliciously transfer confidential data through air-gapped layers.
- Device specification complexity: mobile devices often come with installed applications that might outpace an outdated antivirus scanning capabilities, creating new challenges in the way of securing these devices against emerging cyberattacks.
Limitations of Traditional Antivirus Software
- Compatibility issues: integrating OT devices with security tools often fails due to compatibility issues. Many of these devices operate on legacy systems that are not designed to work with modern security technology. This incompatibility makes your systems more prone to modern cybersecurity attacks due to the need to rely on outdated antivirus software.
- Limited detection capability: most scanning systems rely on a single antivirus engine that uses a signature database, which may not be the optimal solution to secure critical infrastructure networks against newly discovered vulnerabilities.
- Time efficiency: a full-system scan using antivirus software typically takes hours, even days, to run and produce results.
Enhancing Nuclear Supply Chain Security with MetaDefender Drive
MetaDefender Drive is designed to protect your supply chain— from the manufacturer to your air-gapped zone — to ensure all external and internal devices are safe for use. As a standalone physical device, powered by MetaDefender core, it boots without requiring any installed software.
MetaDefender Drive ensures critical infrastructure supply chain security by performing a bare metal multiscan, from the kernel to the user space, on third-party devices. It has been trusted as the main solution to secure numerous critical infrastructure facilities all over the world, such as the Dounreay Nuclear Facility.
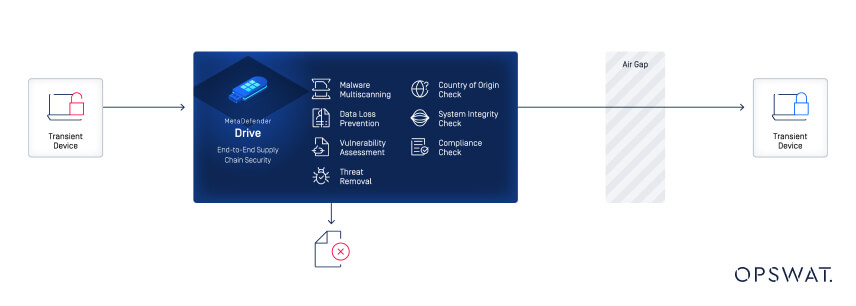
MetaDefender Drive enforces a Zero Trust policy to enhance your defense-in-depth strategy:
Compatibility with OT firmware
MetaDefender supports UEFI, GPT, and legacy BIOS firmware. For full compatibility details, please refer to the MetaDefender Drive datasheet.
Non-Intrusive Scanning
MetaDefender does not rely on device resources or interact with the device’s operating system.
Encrypted disk scans
Antivirus engines face difficulty scanning as they rely on the running OS to decrypt disk file systems.
Multiscanning
Using Metascan® technology, increase detection rates to 82.9% with multiple antivirus engines.
Compliance with critical OT mandates, including
- ISO/IEC 27001
- NEI 18-08
- US Executive Order 14028
- NIST SP 800-53 and 800-82
- NIST FIPS 140-2
- CIP-003-7 and CIP-010-4
- ANSSI
Country of Origin Detection
Determines the origin of the hardware, software, and firmware.
Data loss prevention
Detects sensitive data with support for 70+ file types.
File-based vulnerability assessment
30,000 associated CVEs with severity information, and 3 million datapoints.
OPSWAT Solutions
OPSWAT offers advanced cybersecurity solutions that covers a wide range of use cases, enhancing the security of air-gapped networks and maintaining compliance.
MetaDefender Drive is designed to overcome critical infrastructure challenges to maintain compliance; however, its effectiveness falls short when it comes to portable media. To ensure compliance with the NEI 18-08 guidelines, you can also utilize MetaDefender Kiosk as your solution of choice to protect critical infrastructure from portable media attacks.
MetaDefender Kiosk is designed to be installed at the physical entry point of secure facilities. The Kiosk acts as a digital security guard— inspecting all media for malware, vulnerabilities, and sensitive data.
To discover how OPSWAT solutions can help secure critical infrastructure supply chains, talk to one of our experts today.

