The Mitsubishi Electric MELSEC iQ-F Series is a widely deployed PLC (programmable logic controller) designed for machine control and factory applications. Its compact design and versatility have made it a key component in modern industrial environments.
As part of our ongoing research into device and protocol security, OPSWAT Unit 515 identified multiple vulnerabilities affecting this product line. These findings were responsibly reported to Mitsubishi Electric, and the company has acknowledged the issues and provided mitigation measures along with customer guidance.
The following CVEs (common vulnerabilities and exposures) have been assigned to our discoveries: CVE-2025-5241, CVE-2025-5514, CVE-2025-7731, and CVE-2025-7405. Mitsubishi Electric has published official advisories to help customers understand the risks and apply the recommended protections.
Overview of the Discovered CVEs
Our research uncovered four distinct vulnerabilities affecting the Mitsubishi MELSEC iQ-F Series, each with significant security implications:
- CVE-2025-5241 – A flaw in the account lockout mechanism, where repeated failed login attempts can remotely trigger a denial-of-service condition, preventing valid users from accessing the system.
- CVE-2025-5514 – A denial-of-service condition in the embedded web server. Crafted HTTP requests exploiting improper request length handling can block the service and interrupt operations.
- CVE-2025-7731 – A cleartext transmission vulnerability in SLMP communication. Intercepted credentials could allow an attacker to log in, modify device values, or stop running programs.
- CVE-2025-7405 – A critical flaw in the Modbus TCP implementation, enabling unauthenticated attackers to send malicious packets over port 502/TCP, leading to unauthorized command execution or disruption.
Among these, CVE-2025-7405 demands the highest attention, as Modbus TCP is widely used and the flaw can be exploited without authentication. The following section provides a closer look at this issue.
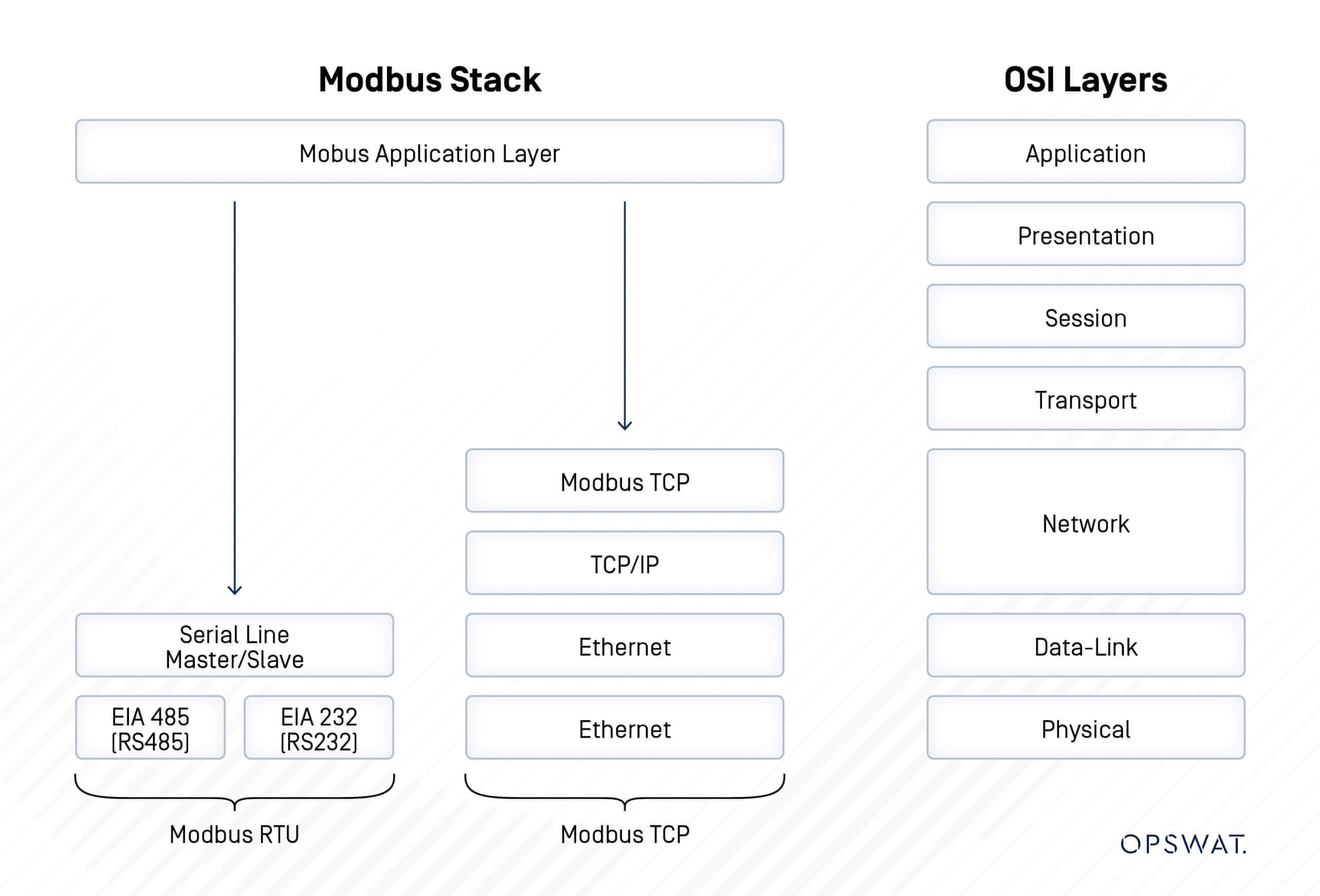
What is Modbus?
Modbus is a client/server data communications protocol in the application layer. Originally developed by Modicon in 1979 for use with its PLCs, it has since become a de facto standard in the industrial sector. Its simplicity, open-source nature, and reliability have made it one of the most common and enduring protocols for connecting industrial electronic devices.
Security Limitations of Modbus TCP
Modbus TCP was originally designed for use in trusted, isolated industrial networks, long before modern cybersecurity principles became essential. As a result, the protocol has no built-in security features. It operates on the assumption that any device on the network can be trusted, an approach that creates serious vulnerabilities in today’s interconnected environments.
The absence of authentication, encryption, and access control makes systems that rely solely on Modbus TCP highly susceptible to unauthorized access and command manipulation. Over the years, multiple vendors have faced security incidents linked to these inherent design limitations.
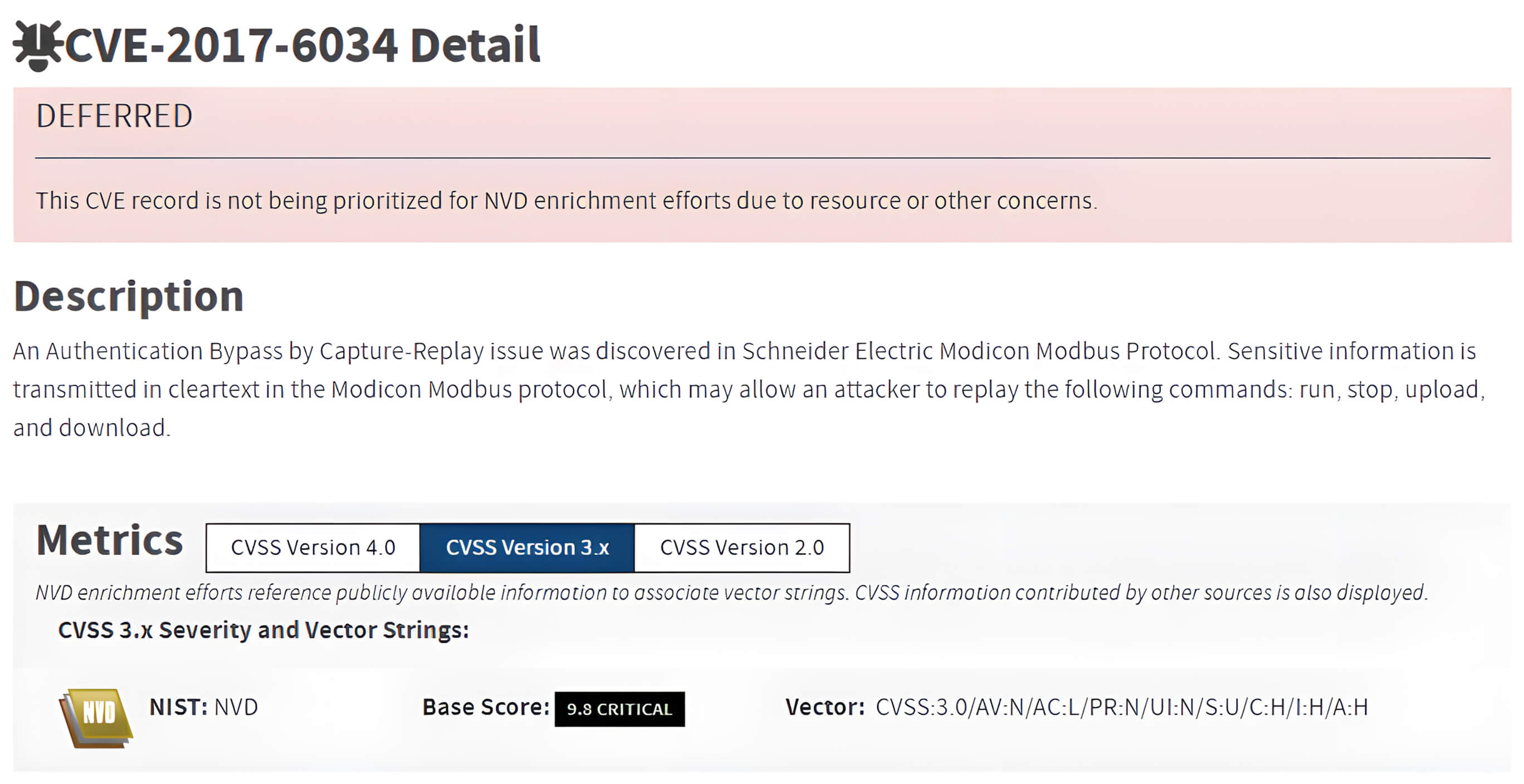
Even Schneider Electric, the original developer of the Modbus protocol, has experienced this risk. For example, CVE-2017-6034 demonstrated how the lack of encryption in Modbus TCP communications could expose sensitive data in transit. Attackers able to capture and replay legitimate commands (such as start, stop, or configuration instructions) could compromise the integrity and control of affected PLCs.
With these risks in mind, Unit 515 conducted a comprehensive security assessment of Mitsubishi Electric’s MELSEC iQ-F Series. The objective was to determine whether similar security weaknesses in Modbus TCP could be exploited in Mitsubishi devices, and to evaluate the potential impact on industrial environments where these controllers are deployed.
CVE-2025-7405: Unauthenticated Read/Write Operations via Modbus TCP in MELSEC Series PLCs
As outlined in the previous section, Modbus TCP’s lack of authentication and encryption creates a significant security gap in modern connected environments. During our security assessment of Mitsubishi Electric’s MELSEC FX5UJ series PLCs, Unit 515 detected that this weakness directly affects the product line.
By default, the controllers expose Modbus TCP on port 502, where insufficient access controls allow unauthenticated read and write operations to internal memory areas. An attacker with network access could exploit this condition to extract device data, alter device values, or disrupt ongoing operations.
The vulnerability was reported to Mitsubishi Electric under our responsible disclosure process. It has been assigned CVE-2025-7405, and Mitsubishi Electric has released advisories with mitigation guidance to help customers secure their deployments.

To help prevent potential cyberattacks, OPSWAT has not published detailed exploitation techniques, giving customers time to apply vendor mitigations before adversaries attempt to weaponize the issue. The video below provides a proof-of-concept demonstration of the critical impact this vulnerability can have on affected devices:
Remediation
We strongly recommend that organizations utilizing Mitsubishi Electric MELSEC iQ-F Series devices follow the official guidance provided by Mitsubishi Electric to remediate these vulnerabilities.
To effectively mitigate these vulnerabilities, organizations should adopt a comprehensive defense-in-depth strategy, which includes:
- Vulnerability detection via continuous CVE scanning and remediation: Regularly scanning networks for vulnerabilities, and apply remediation (best with firmware patching if possible)
- Monitoring for anomalous behaviors: Flagging unusual increases in frequency in communication to the Mitsubishi Electric MELSEC iQ-F Series devices, which could suggest an ongoing unauthorized data exfiltration attempt.
- Identifying unauthorized device connections: the system should detect when a rogue/ unauthorized device connects to the PLC.
- Network segmentation: Isolating affected devices can help prevent the lateral spread of attacks, thus minimizing impact.
- Intrusion Prevention: immediately identifying and blocking malicious/ unapproved commands to the PLC, then effectively protect normal operations of the PLC
OPSWAT’s MetaDefender OT Security addresses these needs by detecting CVEs, continuously monitoring the network for unusual behaviors and identifying unauthorized connections. Using AI and machine learning, it learns normal traffic patterns, establishes baseline behavior, and implements policies to alert anomalies. This allows instant, informed responses to potential threats. In addition, MetaDefender OT Security allows remediation of vulnerability with its unique capability of centralized and integrated firmware upgrade for the controllers.
In the case of an attack exploiting these CVEs, MetaDefender OT Security integrates with the MetaDefender Industrial Firewall to detect, alert and block suspicious communications based on set rules. MetaDefender Industrial Firewall uses AI to learn regular traffic patterns and enforce policies to prevent unauthorized connections.
Beyond prevention, OPSWAT’s MetaDefender OT Security also empowers organizations to monitor signs of exploitation in real time through continuous asset visibility and vulnerability assessment. By leveraging advanced asset inventory discovery and tracking, vulnerability assessment and patching capabilities, our platform provides proactive threat detection and facilitates rapid, effective remediation actions.
Connect with an expert today to learn more about how OPSWAT can help your organization mitigate CVEs and shrink your overall attack surface.

