Introduction to Ruby on Rails
Ruby on Rails (Rails) is a full-stack, Model-View-Controller (MVC) web framework built with Ruby. It comes “batteries included”, offering developers everything they need out of the box: an Object-Relational Mapper (Active Record), a request/response and view layer (Action Pack/Action View), background job processing, mailers, WebSocket support, file storage and uploads (Active Storage), and much more.
Since its initial release in 2004, Ruby on Rails has grown into one of the most widely adopted web frameworks in the world. Today it powers millions of websites and applications - including high-profile platforms such as GitHub, Shopify, Airbnb, Basecamp, and Netflix. With its strong emphasis on Convention over Configuration, developer productivity, and rapid prototyping, Rails has become a go-to framework for both startups and large enterprises.
Unit 515 Research: Exposing Critical Vulnerabilities in Rails
During independent research, Thai Do, a member of OPSWAT’s Unit 515 team, identified two vulnerabilities in Ruby on Rails - one of which could lead to remote code execution (RCE). These findings were responsibly disclosed to the Rails security team, with whom OPSWAT coordinated throughout the process.
On August 13, 2025, the Rails team published public advisories and released patched versions addressing both vulnerabilities.
Affected Versions and Fixed Releases
Component | Affected Versions | Fixed Versions |
|---|---|---|
Active Storage (CVE-2025-24293) | Rails ≥ 5.2.0 and below the fixed release | 7.1.5.2, 7.2.2.2, 8.0.2.1 |
Active Record Logging (CVE-2025-55193) | Rails < 7.1.5.2, < 7.2.2.2, < 8.0.2.1 | 7.1.5.2, 7.2.2.2, 8.0.2.1 |
Security Issues Identified in Rails
CVE-2025-24293 – Active Storage Unsafe Transformation Methods
This vulnerability affects Active Storage in Rails versions ≥ 5.2.0. It occurs when unsafe image transformation methods are passed to mini_magick, which - when combined with unvalidated user input - could lead to remote code execution (RCE). While Rails notes that the flaw is not exploitable under default configuration, applications that expose transformation options to users are particularly at risk.
CVE-2025-55193 – ANSI Escape Injection in Active Record Logging
This vulnerability affects Active Record logging in all Rails versions prior to 7.1.5.2, 7.2.2.2, and 8.0.2.1. Attackers could inject specially crafted identifiers containing ANSI escape sequences into logs, potentially manipulating how queries appear in terminal output and leading to misleading or corrupted logs. Although the flaw does not directly expose data or enable code execution, it could hinder monitoring and incident response efforts. The Rails security team resolved the issue in the same patched releases.
Technical Analysis of CVE-2025-24293 – Active Storage Remote Code Execution
Overview of Active Storage
Active Storage is Rails’ built-in framework for handling file uploads. It enables developers to attach files to Active Record models and store them either locally (for development/testing) or on cloud services such as Amazon S3, Google Cloud Storage, or Microsoft Azure. Core features include performing image transformations, generating previews for non-image files like PDFs and videos, and mirroring uploads to multiple services for redundancy or migration.
How Image Transformations Work
Image transformations enable developers to deliver attachments at specific dimensions or formats. This is done by calling the variant() method on an image attachment and passing in supported operations.
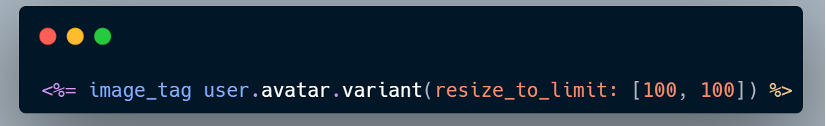
When a client requests a variant URL, Active Storage performs the transformation on demand from the original blob, stores the result on the configured service, and returns a redirect to the newly generated file.
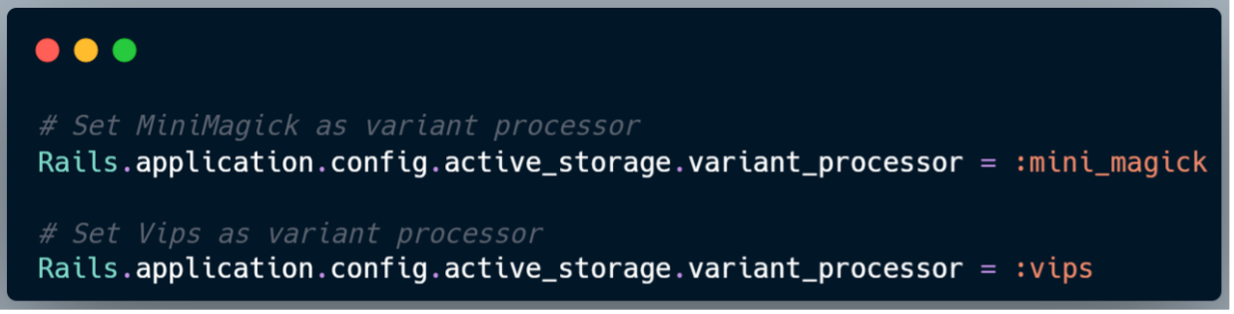
Rails supports two processors for image transformations: Vips and MiniMagick. The processor in use can be configured via config.active_storage.variant_processor.
The specific operations supported in image transformations are determined by the image_processing gem and depend on the underlying processor that is configured for the Rails application.
Incomplete Fix of CVE-2022-21831
In March 2022, the Rails team disclosed CVE-2022-21831, a critical code injection vulnerability in Active Storage’s image transformation feature. The patch introduced a default allow-list of transformation methods to mitigate the issue.
However, during a deeper review of the patch and Rails source code, Thai Do (OPSWAT Unit 515) discovered a bypass that rendered the original fix incomplete. This bypass reintroduced a path for attackers to achieve Remote Code Execution (RCE), leading to the disclosure of CVE-2025-24293.
Root Cause in the image_processing Gem
When a transformation is applied, Rails delegates the operation to the image_processing gem, which eventually calls ImageProcessing::Processor#call in lib/image_processing/processor.rb
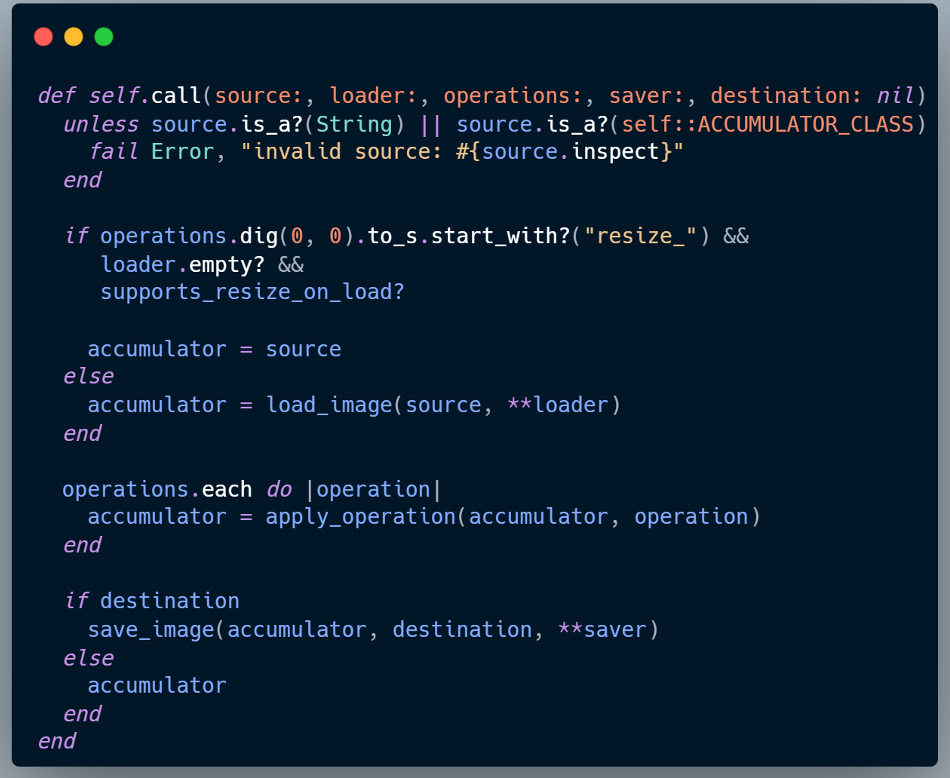
If the configured variant processor is MiniMagick, the vulnerability resides in two functions within lib/image_processing/mini_magick.rb:
• load_image – accepts unvalidated options from **loader.
• save_image – accepts unvalidated options from **saver.
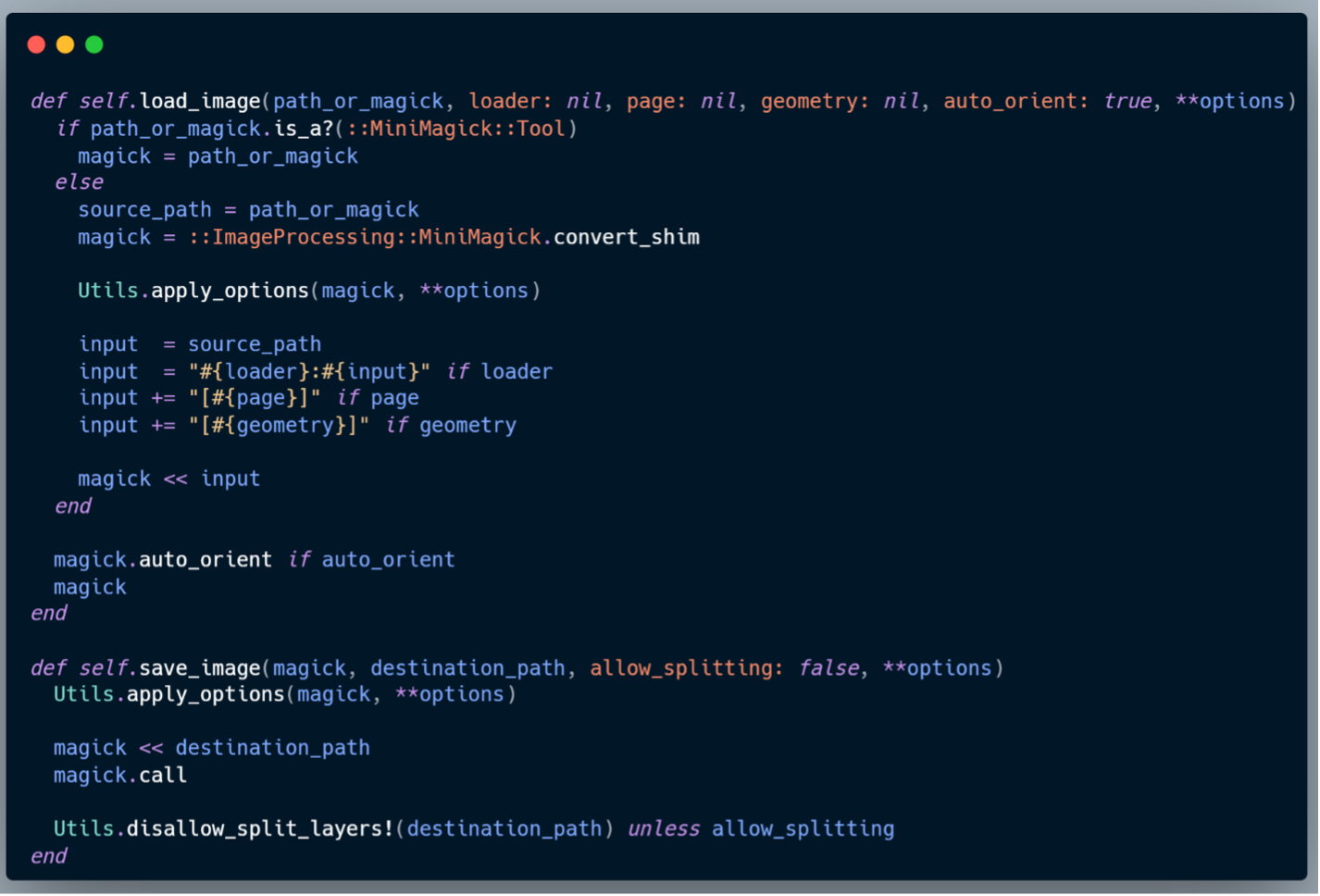
For load_image, any key-value pairs in **loader other than page, geometry, and auto_orient are preserved in **options. The same applies to save_image, where keys other than allow_splitting remain in **options. These options are later passed to Utils.apply_options(magick, **options), which applies them as MiniMagick CLI flags (e.g., -quality).
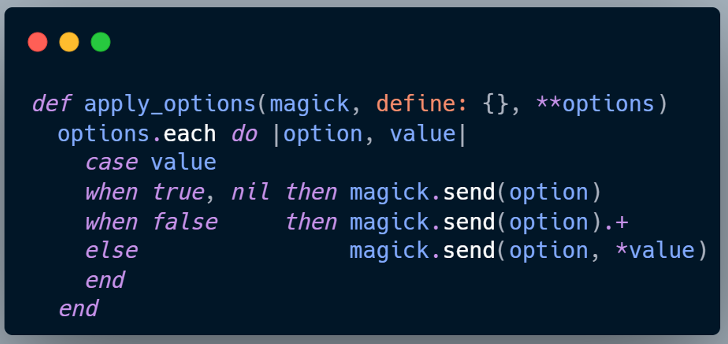
Although loader and saver are included in the default allow-list and therefore considered safe, this trust is misplaced. With carefully crafted input, an attacker can exploit these options to bypass the checks and ultimately cause Rails to execute arbitrary system commands on the host machine.
Exploitation Scenario in Rails Applications
If an application passes unvalidated user input directly into transformation methods, for example:
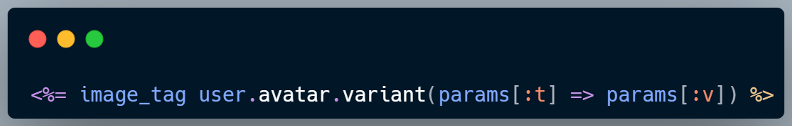
An attacker could craft malicious input to manipulate the loader or saver options. This would bypass the allow-list and execute arbitrary commands on the server, resulting in Remote Code Execution (RCE).
Proof of Concept: Remote Code Execution
In Rails applications running vulnerable versions (prior to 8.0.2.1, 7.2.2.2, and 7.1.5.2), OPSWAT Unit 515 successfully demonstrated an exploit chain where unvalidated transformation input resulted in shell command execution.
This video PoC demonstrates the exploitability of CVE-2025-24293 and highlights the real-world impact on Rails applications:
Mitigation and Professional Penetration Testing Services
Organizations should address CVE-2025-24293 and CVE-2025-55193 by upgrading Ruby on Rails to the latest security releases (7.1.5.2, 7.2.2.2, or 8.0.2.1). If immediate patching is not possible, temporary safeguards include restricting image transformations to predefined presets, validating and sanitizing user input, hardening ImageMagick policies, and ensuring logs cannot interpret ANSI escape sequences.
However, applying patches does not eliminate all risks in modern web environments. Custom business logic, third-party integrations, and complex deployment pipelines often create exploitable paths that extend beyond vendor advisories. This is why web application penetration testing is essential.
At OPSWAT, Unit 515 delivers specialized web application penetration testing services that go far beyond automated scanners or checklist audits. Our team consists of seasoned offensive security experts who bring years of experience in testing large-scale applications across diverse industries. Using a systematic, adversarial methodology, we uncover vulnerabilities in authentication flows, input validation, access control, and data handling - issues that can persist even in fully patched frameworks such as Ruby on Rails.
Each engagement combines deep technical expertise with enterprise-ready reporting, providing clear, actionable insights that enable development teams to remediate flaws effectively. By engaging Unit 515, organizations gain the assurance that their critical applications are tested by experts who not only simulate real-world attack techniques but also validate that fixes truly close the gaps. This expertise strengthens remediation efforts, reduces residual risk, and elevates overall application resilience against evolving threats.

