What Defines a Security-First Managed File Transfer Solution in Modern Cybersecurity?
A security-first MFT (managed file transfer) solution is designed from the ground up with proactive threat prevention, continuous visibility, and compliance-by-design capabilities. It goes beyond simply encrypting files during transit by treating every file, user, workflow, and environment as a potential attack surface. Security-first MFT mitigates threats from modern adversaries who leverage file-based attacks, compromised identities, supply-chain infiltration, and unmonitored workflows to gain access to sensitive systems.
Traditional MFT, by contrast, originated as an operational tool meant to automate file delivery, not file security. Traditional MFT platforms focus on reliability, scheduling, scripting, and system-to-system connectivity. Security is typically added on later through bolt-on features such as basic encryption, optional anti-malware scanning, or external DLP integrations.
With evolving AI-based threats and increasingly complex compliance mandates, organizations can no longer depend on traditional models. They need platforms built to defend against file-borne threats and meet regulatory requirements.
Key Principles That Set Security-First MFT Apart from Traditional MFT
Security-first MFT is defined by a set of foundational principles that differentiate it from legacy approaches:
- Proactive Threat Prevention – Uses multiple anti-malware engines simultaneously (multiscanning), sandboxing, file-type verification, and content inspection before delivery.
- Zero Trust Architecture – Assumes all users, devices, and files may be compromised and validates continuously.
- Compliance-by-Design – Embeds audit controls, policy enforcement, encryption, and governance into the workflow itself.
- Automation and Security Integration – Security controls apply automatically across all workflows without manual intervention.
Traditional MFT solutions typically incorporate file security as an add-on. While traditional platforms may offer encryption or access control, these capabilities are often optional modules or require additional tooling to be effective.
How Compliance Standards Have Shaped the Shift Toward Security-First MFT
Regulatory frameworks have played a defining role in moving enterprises toward security-first solutions. Standards such as NIST, ISO 27001, GDPR, HIPAA, and PCI-DSS impose strict requirements related to:
- Encryption at rest and in transit
- Verified access controls
- Complete, immutable audit logs
- Evidence of policy enforcement
- Data residency and retention guarantees
- Timely breach reporting
- Integrity verification and risk monitoring
Traditional MFT platforms often struggle to keep pace with compliance mandates. They may struggle to satisfy data governance, audit integrity, or continuous monitoring requirements. Security-first MFT platforms address these gaps with built-in controls designed specifically for regulated industries.
Common Vulnerabilities in Traditional MFT Solutions
Legacy and traditional MFT systems frequently expose organizations to serious security risks. Common vulnerabilities include:
- Unencrypted or inconsistently encrypted transfers, especially during internal workflows
- Weak authentication mechanisms that rely solely on passwords or outdated role models
- Limited or nonexistent real-time monitoring, preventing escalation of suspicious activity
- Manual patching and updates, leaving systems exposed to zero-days or old CVEs
- Insufficient access controls, enabling excessive privileges
- No malware scanning or file sanitization, allowing file-borne threats to pass through unchecked
- Incomplete audit logs, obstructing investigations and failing compliance audits
Real-world breaches demonstrate the risks of incomplete security controls. For example, the 2023 MOVEit Transfer vulnerability (CVE-2023-34362) affected over 2,000 organizations and exposed 77 million records, according to Emsisoft's breach tracking data. These incidents illustrate how traditional MFT platforms can provide attackers silent entry into critical systems.

Comparing Security Capabilities: Security-First MFT Versus Traditional MFT Solutions
Security-first and traditional MFT platforms often appear similar on the surface. Each facilitates the transfer of files between systems, partners, or users. But beneath the surface, the architectural differences are profound.
The table below highlights how each approach handles built-in security versus optional add-ons.
Which Security Features Are Built-In Versus Add-On in MFT Platforms?
| Capability | Security-First MFT | Traditional MFT |
|---|---|---|
| Malware Scanning | Built-in multiscanning & file sanitization (CDR) | Typically add-on or absent |
| DLP Controls | Integrated, automated, policy-based | Often external or manual |
| Encryption | Mandatory and enforced | Optional or inconsistently applied |
| Zero Trust Access | Continuous verification & least privilege | Basic perimeter-based access |
| Threat Intelligence Integration | Native, real-time | Rare and external |
| Audit Logging | Immutable, granular, always-on | Partial or manually configured |
| Automated Policy Enforcement | Core design feature | Requires scripts or admin effort |
| File Validation | Deep file-type verification | Limited or nonexistent |
| Incident Response Hooks | Native SIEM/SOC integration | Optional connectors |
Traditional MFT solutions are not fundamentally security platforms; they are automation tools that require additional products to achieve baseline protection.
How Do User Access Controls and Monitoring Differ Between Security-First and Traditional MFT?
Security-first MFT employs granular, Zero Trust-aligned access controls and real-time monitoring to minimize insider risks and external threats. Users are restricted to only the permissions required, and all actions are continuously verified.
Traditional MFT platforms rely on static permissions, limited RBAC (role-based access control) models, and sporadic monitoring. They may log access but seldom detect anomalous user behavior or unauthorized access patterns.
Security-first controls include:
- Policy-driven RBAC
- MFA/identity integration
- Continuous session validation
- Behavioral analytics
- Real-time monitoring dashboards
These capabilities reduce the likelihood of compromised accounts leading to data theft or operational disruption.
How Does Security-First MFT Enable Proactive Threat Prevention?
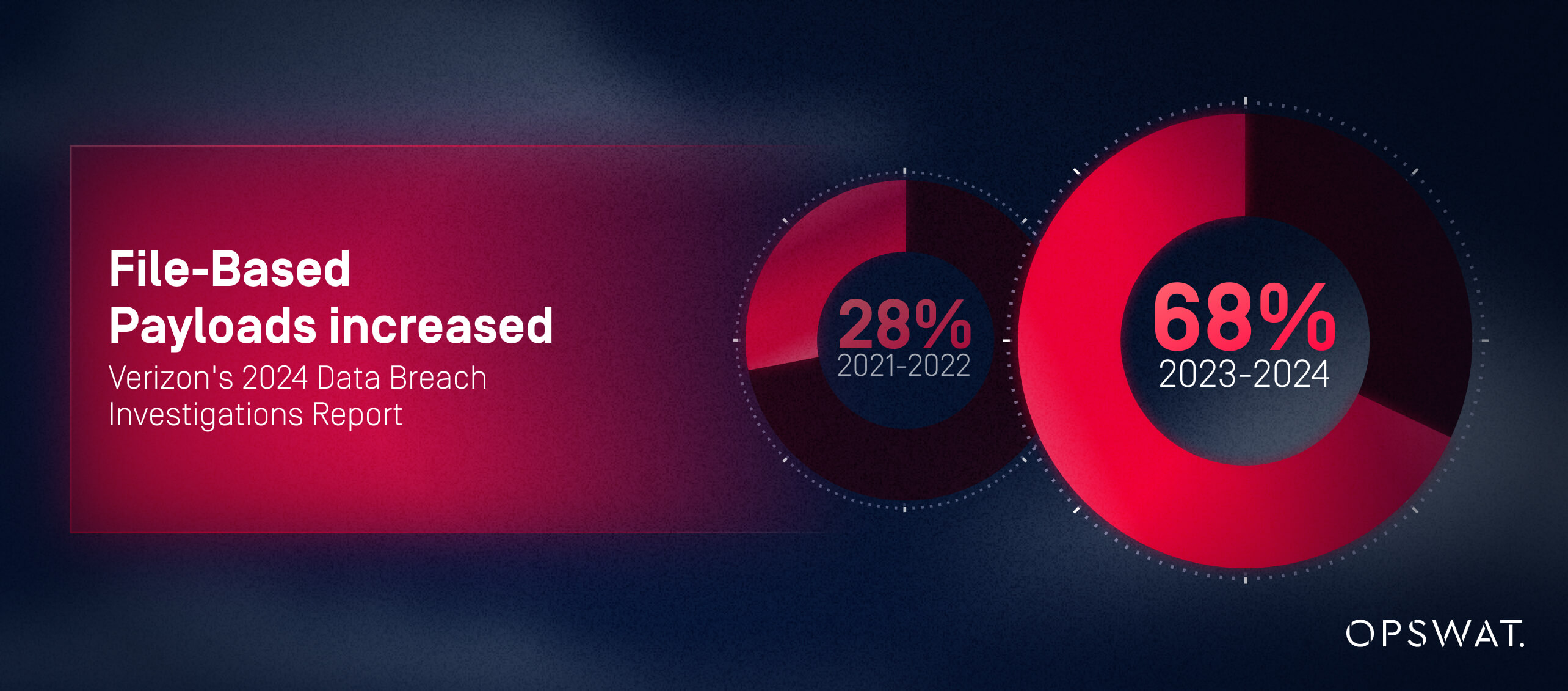
Security-first MFT prevents threats before files reach their destination. According to Verizon's 2024 Data Breach Investigations Report, 68% of attacks in 2023-2024 used file-based payloads embedded inside documents, PDFs, images, or compressed files—a 40% increase from 2020-2021. These attack vectors target file transfer systems specifically Traditional MFT systems do not inspect these files; security-first MFT does.
Examples of proactive threat prevention include:
- Automated malware multiscanning
- CDR (Content Disarm and Reconstruction) – removing malicious active content
- Sandboxing unknown files
- Threat intelligence–driven risk scoring
- Policy-based quarantining or blocking
How Security-First MFT Streamlines Regulatory Compliance and Audit Readiness
Compliance complexity is one of the biggest challenges for modern enterprises. Security-first MFT simplifies compliance by embedding governance, validation, and auditable controls directly into transfer workflows.
Traditional MFT places responsibility for compliance on administrators, often through manual configuration, patching, scripting, and piecemeal documentation.
Meeting GDPR, HIPAA, PCI-DSS, and Industry Standards with Security-First MFT
A security-first MFT solution meets key regulatory requirements by design:
- Encryption in transit and at rest (GDPR Article 32, HIPAA §164.312(a)(2)(iv), PCI-DSS Requirement 4)
- Immutable audit trails for monitoring access and data movement (GDPR Article 30, HIPAA §164.312(b), SOX Section 404)
- Data residency enforcement (GDPR Article 44-50, various national data protection laws)
- Access controls aligned to least privilege (NIST SP 800-53 AC-6, ISO 27001 A.9.2.3)
- Real-time alerting for potential breaches (GDPR Article 33 - 72-hour notification requirement)
- Secure file validation to maintain data integrity (HIPAA §164.312(c)(1), PCI-DSS Requirement 11.5)
These built-in controls reduce compliance gaps and provide verifiable evidence required by regulators.
Reducing Audit Burden and Streamlining Evidence Collection
Traditional MFT audits can take weeks due to poor logging, inconsistent controls, or missing data. Security-first MFT solutions eliminate this burden by providing:
- Automatically generated audit reports
- Centralized logs with full transfer visibility
- Preconfigured compliance mappings and templates
- Event-level metadata for forensic reconstruction
This reduces audit fatigue, accelerates evidence collection, and improves regulatory trust.
How Security-First MFT Supports Continuous Compliance Amid Evolving Regulations
Security-first MFT solutions adapt to evolving regulatory standards quickly through policy-driven controls, automated updates, and configurable governance frameworks. These capabilities future-proof compliance efforts and allow organizations to demonstrate continuous adherence, which traditional MFT struggles to maintain.
Risk Mitigation and Incident Response: Why Security-First MFT Reduces Breach Exposure
Modern security programs measure success by their ability to mitigate breaches quickly and effectively. Security-first MFT dramatically improves both detection and response, reducing breach impact and strengthening forensic outcomes.
Traditional MFT often lacks the visibility, intelligence, and automation required for rapid response.
How Security-First MFT Improves Brach Detection and Threat Response
Security-first platforms enable:
- Real-time alerting for suspicious file activity
- Automated triggers that quarantine or block malicious files
- Integration with SIEM and SOC workflows for rapid escalation
- Anomaly detection based on user and file behavior
Traditional MFT relies on manual monitoring with average detection delays of 24-72 hours, according to Ponemon Institute's 2024 Cost of Insider Threats Report. This increases breach exposure time by 300% compared to security-first solutions that detect threats in real time (under 5 minutes). Extended detection windows allow lateral movement and data exfiltration to progress unchecked.
Supporting Forensic Investigations with Advanced Audit Trails
Incident response depends on high-fidelity visibility. Security-first MFT provides:
- Immutable, timestamped logs
- File integrity validation
- Full user activity histories
- Transfer-level metadata (source, destination, policies applied)
These capabilities support rapid root-cause analysis and defensible regulatory reporting.
Addressing the Most Common Security Gaps in Legacy MFT
Legacy MFT exposes organizations to:
- Outdated or unpatched cryptographic libraries
Weak identity or access models
- Blind spots in partner or third-party integrations
- Uninspected file movement across networks
Security-first MFT addresses all these deficiencies with integrated threat prevention, continuous monitoring, and built-in governance frameworks.
Operational and Resource Considerations When Migrating to Security-First Managed File Transfer
Moving from traditional to security-first MFT requires thoughtful planning but pays dividends in reduced operational overhead, lower breach risk, and improved compliance efficiency.
What Are the Key Steps for Transitioning from Traditional to Security-First MFT?
A structured migration roadmap includes:
- Assessment – Inventory workflows, partners, encryption dependencies, and compliance gaps.
- Design – Define Zero Trust policies, security controls, and architecture requirements.
- Pilot – Validate workflows in a controlled rollout.
- Phased Deployment – Expand across departments and high-value workloads.
- Governance Alignment – Update policies, roles, and compliance documentation.
Integrating Security-First MFT with Existing IT Infrastructure
Security-first MFT integrates seamlessly when:
- Identity governance (IAM/MFA) is centralized
- SIEM platforms consume MFT telemetry
- DLP tools enforce content governance
- Cloud and on-prem file repositories sync securely
- APIs and automation frameworks support workflow orchestration
Common challenges, such as siloed systems or legacy dependencies, can be mitigated through phased rollout and connector-based integrations.
Evaluating the Total Cost of Ownership and ROI of Security-First MFT
While security-first MFT may involve higher initial investment, its ROI is driven by:
- Reduction in breach likelihood and associated costs
- Decreased audit workload
- Lower operational overhead from automation
- Fewer manual security layers
- Improved uptime and workflow stability
For regulated industries, these savings can be substantial, often surpassing the initial investment within the first year.
Decision Framework: When and Why to Upgrade to a Security-First MFT Solution
Enterprises often recognize the need for an upgrade after experiencing audit failures, operational complexity, or increased threat activity. A decision framework helps leaders determine timing and strategic justification.
Key Triggers That Signal the Need for Security-First MFT
Common triggers include:
- Failing security or compliance audits
- Increasing ransomware and file-borne malware attempts
- Lack of visibility into file movement
- Overreliance on manual or script-based processes
- Data residency or cross-border compliance challenges
- Digital transformation initiatives requiring modernization
If multiple triggers apply, the organization is a strong candidate for security-first MFT.
Best Practices for Evaluating and Selecting a Security-First MFT Platform
A comprehensive evaluation should include:
- Requirements Gathering – Compliance, threat prevention, workflow complexity
- Vendor Comparison – Built-in security, integrations, reporting, and Zero Trust capabilities
- Proof of Concept – Validate performance, ease of use, and scalability
- Security Assessment – Review architecture, APIs, and vulnerability management
- Governance Review – Ensure alignment with enterprise policies
Questions to ask vendors:
- Are security controls native or add-ons?
- How are threats detected and neutralized?
- Can you demonstrate compliance mapping?
- How do you support Zero Trust enforcement?
Red flags include reliance on external anti-malware scanning, incomplete logs, outdated architectures, or limited integration capabilities.

Why OPSWAT Leads in Security-First Managed File Transfer
OPSWAT sets the benchmark for security-first MFT with:
- Integrated multiscanning, CDR, sandboxing, and file-type verification
- Zero Trust architecture with least privilege and continuous validation
- Compliance-by-design controls
- Immutable audit logs and SIEM-ready telemetry
- High-performance, hybrid-ready deployment models
- Proven outcomes in critical infrastructure and regulated industries
These capabilities directly address shortcomings in traditional MFT and empower organizations to modernize securely.
Next Steps: How to Engage with OPSWAT for a Security Assessment or Demo
CISOs and IT leaders can take the next step by:
- Requesting a tailored security assessment
- Downloading compliance checklists
- Scheduling a MetaDefender MFT demo
- Engaging OPSWAT’s experts to evaluate migration readiness
Security-first MFT is a strategic transformation. OPSWAT provides the architectural depth and proven security needed to execute it.
FAQs
What security features differentiate security-first MFT from traditional MFT?
Security-first MFT differs from traditional MFT through four core architectural features: built-in threat prevention (multiscanning, sandboxing, CDR), granular access controls with continuous verification, Zero Trust design principles, and complete immutable audit logs. Traditional MFT typically offers these as optional add-ons rather than core capabilities.
How does security-first MFT mitigate threats more effectively?
Through integrated multiscanning, sandboxing, CDR, and real-time monitoring.
What challenges arise when migrating from traditional to security-first MFT?
Legacy dependencies, workflow mapping, IAM integration, and policy alignment.
How does automated threat intelligence reduce breach risk?
By continuously updating policies and detecting new threat patterns instantly.
What are the ROI differences?
Security-first MFT reduces operational overhead, compliance risk, and incident costs.
How does a security-first MFT support incident response?
With immutable logs, granular metadata, and automated alerts for rapid investigation.
Is Your Organization Protected with Security-First MFT?
As cyber threats evolve and regulatory expectations intensify, the gap between traditional and security-first MFT grows wider. Legacy systems cannot protect against modern file-borne threats, insider risks, and compliance complexity. Security-first MFT delivers a fundamentally stronger model—one designed to prevent breaches, accelerate compliance, and provide deep operational visibility.
Modern enterprises can no longer afford reactive or partial protections. By adopting a security-first approach, organizations reduce risk, strengthen trust, and ensure secure, compliant, resilient file movement across their entire ecosystem.

