We are excited to introduce a series of technical analysis blogs focusing on various Common Vulnerabilities and Exposures (CVEs), identified and remediated with our advanced threat detection technologies. All research is done by the graduate students who participate in the OPSWAT Cybersecurity Fellowship program launched in September 2023.

In this blog, we will explain the Google Chrome CVE-2019-13720 and how organizations can defend against CVE-2019-13720 exploitation attacks.
What is Google Chrome and when it was founded?
Google Chrome is a cross-platform web browser developed by Google and officially released on September 2, 2008. It was developed as part of Google’s efforts to create a better, more modern browser. It offered many new features at the time, including tabbed browsing, privacy mode, and synchronization with Google services. Since its release, it has become one of the most popular web browsers worldwide. As of 2021, Google Chrome is estimated to have about 3.2 billion users.
Due to the popularity of Google Chrome, it has become a focal point for research and attacks, attracting both ethical hackers and malicious hackers. Common vulnerabilities identified in Google Chrome include Denial of Services (DoS), information leakage, and remote code execution, among others. Regarding the Remote Code Execution vulnerability, two types exist for this issue on Google Chrome: sandbox escape and non-escape.
What is CVE-2019-13720?
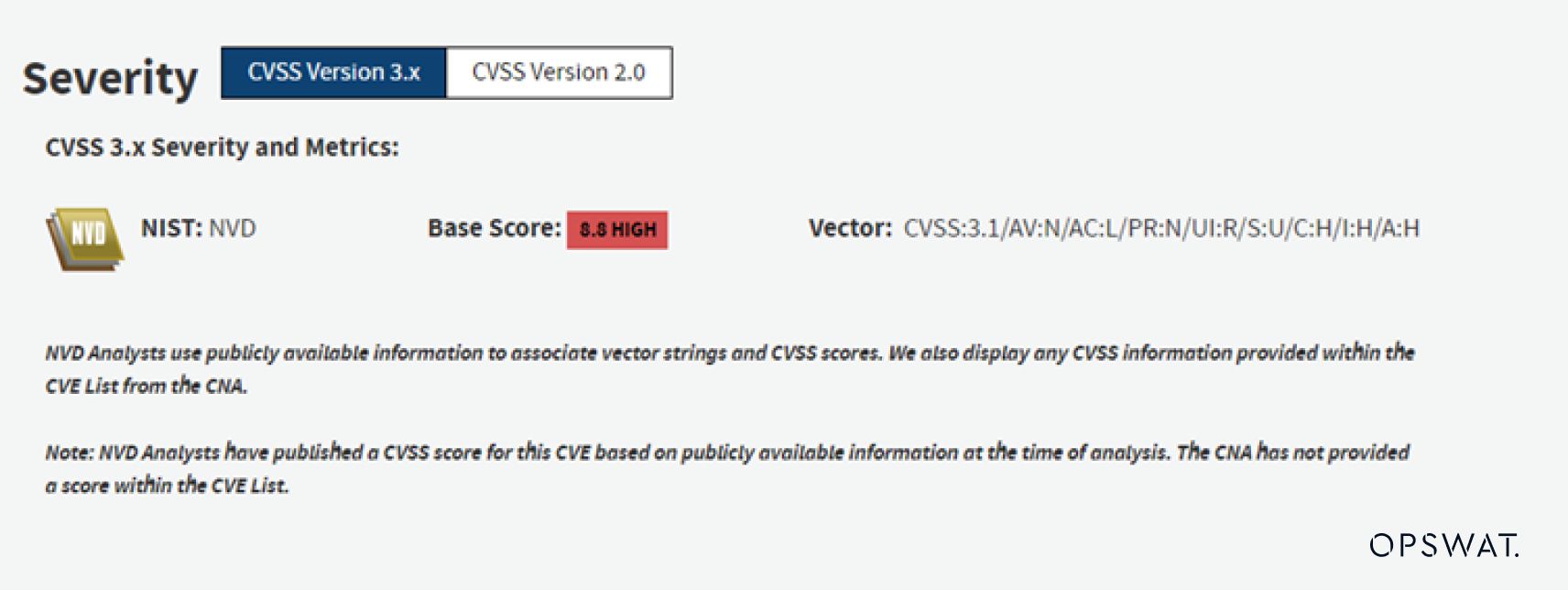
CVE-2019-13720 is a Use After Free (UAF) vulnerability of WebAudio in Google Chrome before version 78.0.3904.87 that allows a remote attacker to potentially exploit heap corruption via a crafted HTML page. When the victim accesses a malicious web page or opens a crafted HTML page on a vulnerable Google Chrome browser, the malicious code is executed on the victim's endpoint. This CVE was first reported by Anton Ivanov and Alexey Kulaev in 2019.
From a technical perspective, a use-after-free vulnerability can be exploited due to a race condition between the Render and Audio threads in the audio component of Qt WebEngine that allows remote attackers to execute WebAssembly shell code, leading to the victim’s device being compromised. The resolution for this issue is for all Qt WebEngine users to update to the latest version.
The Attacking Phases
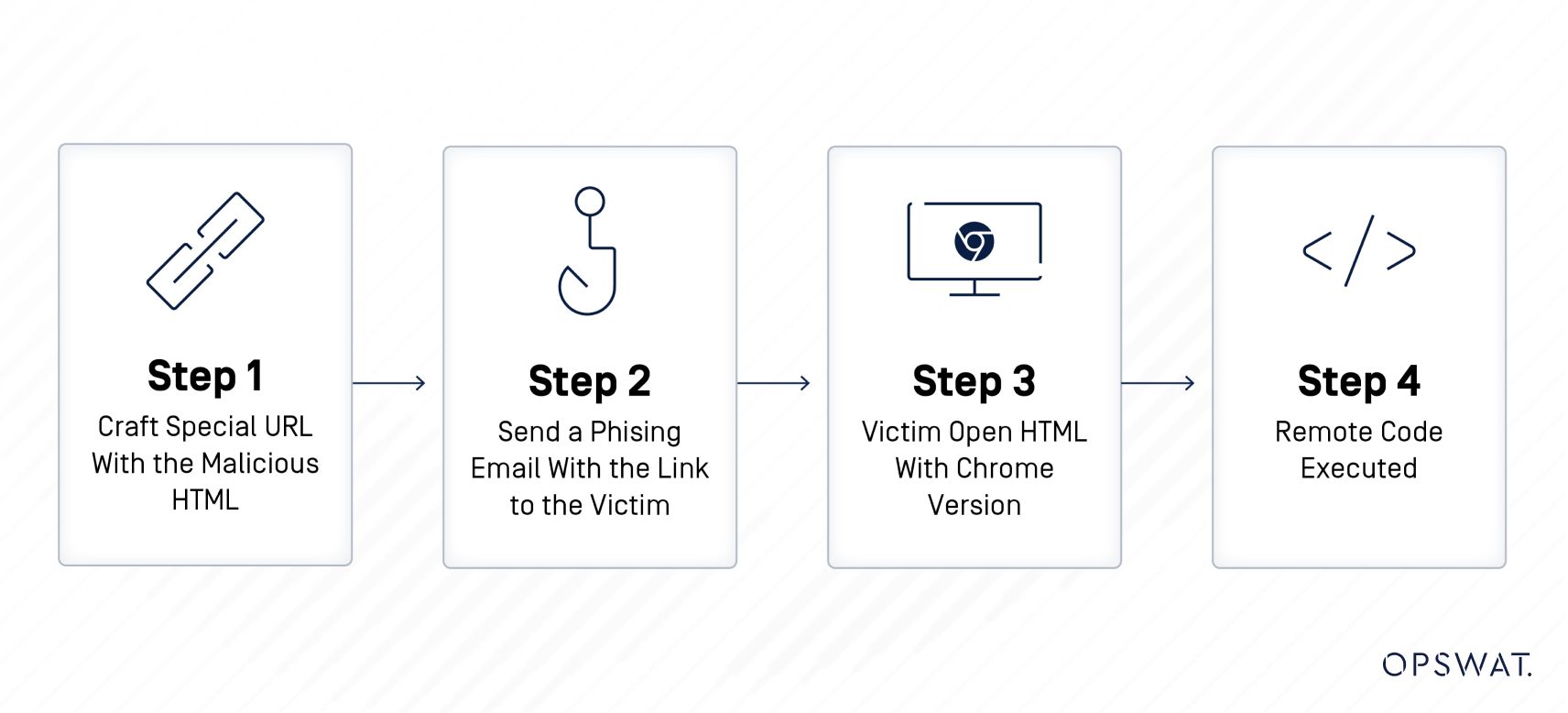
The attackers create a special URL with the malicious HTML and send a phishing email with the link to the victim. When the victim opens the email and clicks on the link, the malicious code is executed and allows the attacker to take over the affected system. Details of the remote code tactics, as they appear in an HTML document, can be referred to here.
What are Use After Free (UAF) and heap spray vulnerabilities?
A UAF vulnerability is a type of security flaw that occurs when a program continues to use memory after it has been freed. This can lead to various adverse consequences, including data corruption, arbitrary code execution, and system crashes.
Heap spraying is a payload delivery technique that entails writing several bytes at different locations throughout the heap. This involves injecting a crafted payload (i.e. harmful data) into the memory heap, ensuring that the execution flow jumps into sprayed memory rather than the application's original code. The purpose of this attack is typically to gain control over the EIP registry.

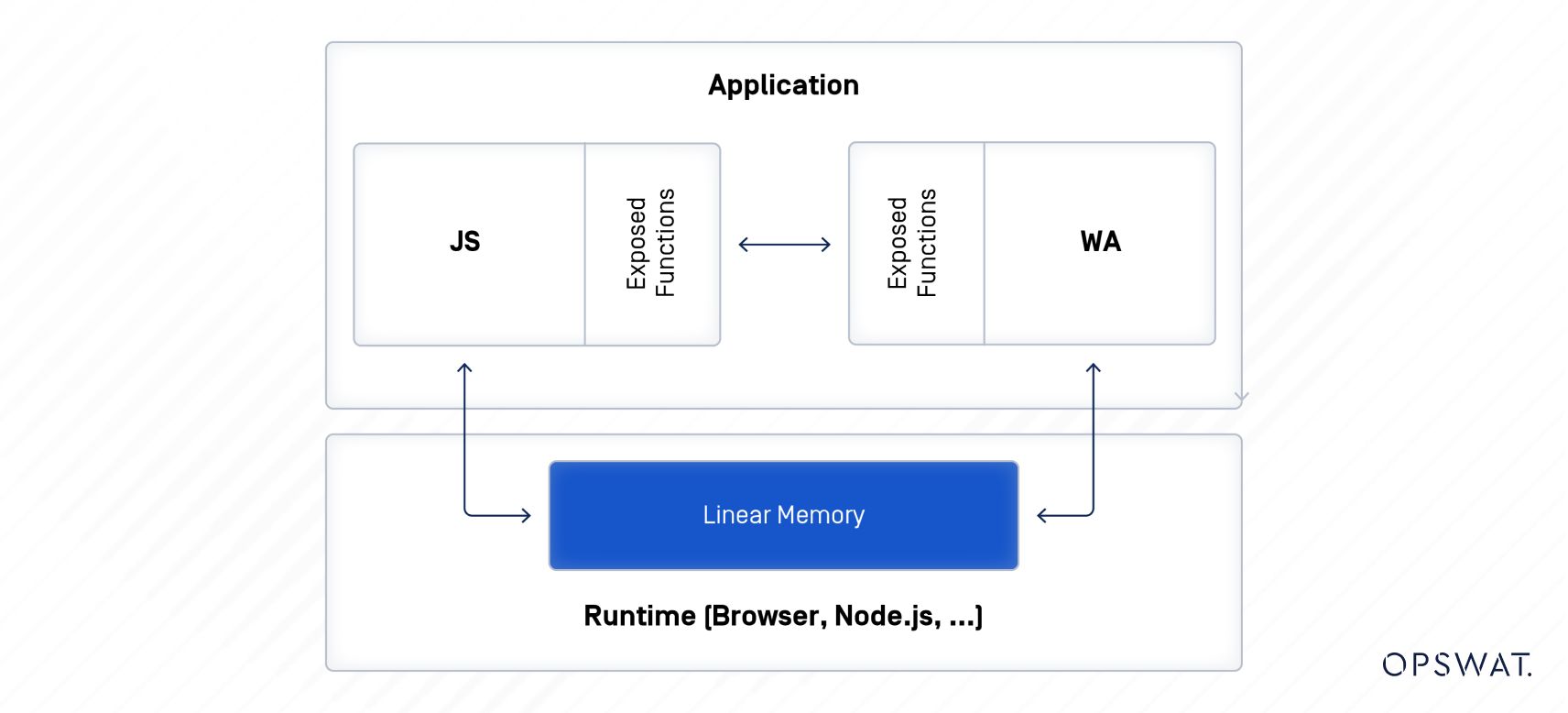
What is WebAssembly?
WebAssembly, often abbreviated as Wasm, is a new binary instruction format that serves as a portable target for the compilation of high-level languages like C/C++, allowing them to run at near-native speed in a web browser’s JavaScript engine.

However, because WebAssembly can be compiled from languages that are not memory-safe, such as C/C++, common coding vulnerabilities like buffer overflows or format string vulnerabilities can be introduced into the cross-compiled WebAssembly binaries. This potential for vulnerabilities to be included in WebAssembly modules has increased the attack surface of contemporary web applications.
What is a race condition vulnerability?
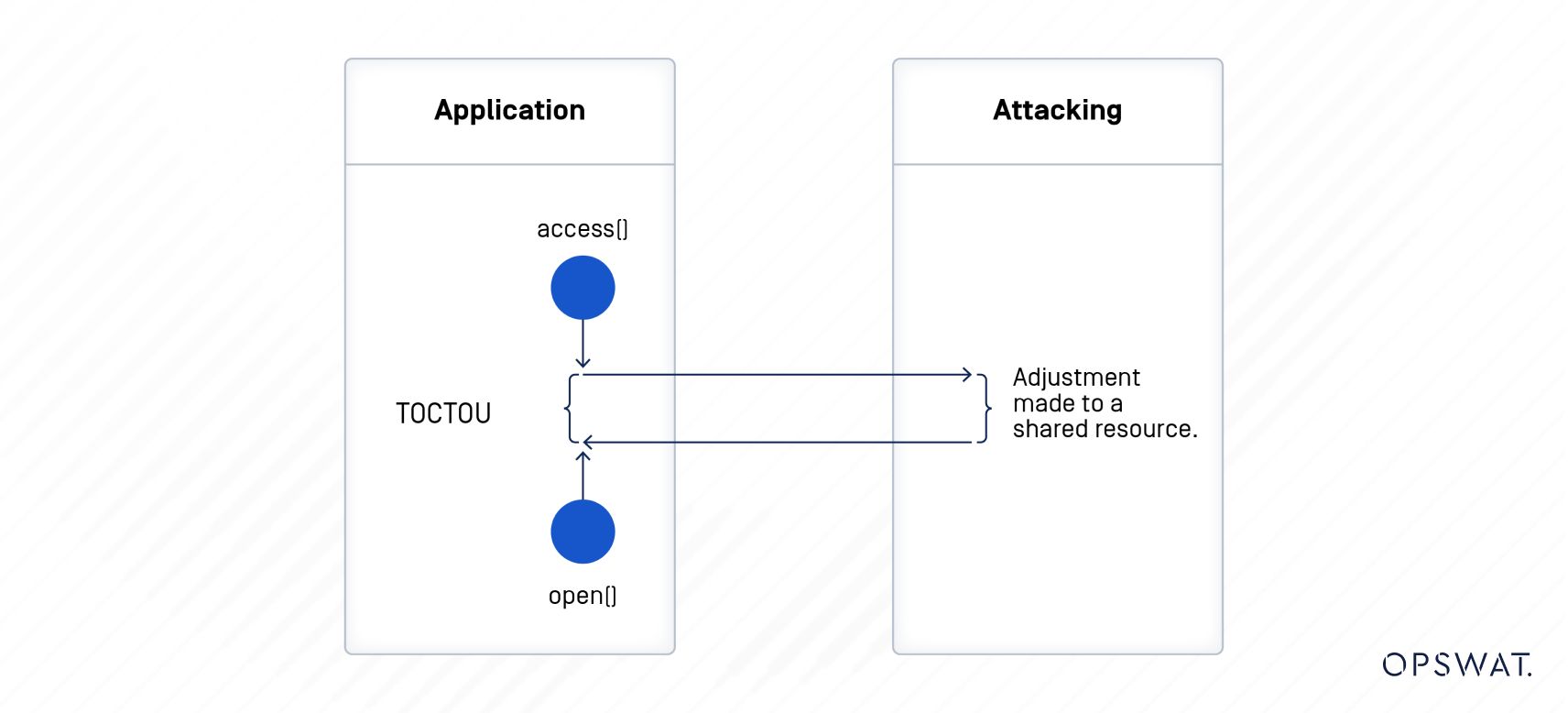
A race condition vulnerability in software arises when multiple processes or threads attempt to access a shared resource simultaneously, causing unpredictable results or operational disruptions due to the timing of the access. When a program has a race condition vulnerability, it can lead to various issues such as application crashes, data corruption, incorrect outcomes, or inconsistencies. Attackers can exploit this vulnerability to gain unauthorized access, leak information, escalate privileges, or induce system crashes.
Categorized as a race condition vulnerability, a TOCTTOU vulnerability exploits the time gap between checking and using a resource.
How CVE-2019-13720 work?
To exploit this vulnerability, the researcher attaches JavaScript code to an HTML file. When a user launches the HTML file, the script attempts to find the leaked address by creating two threads (main thread and audio thread) that handle the same buffer data. The leaked address of the temporary_buffer_object in ReverbConvolverStage is then used to obtain the pointer of the feedforward_array in IIRFilterNode (which shares the same super page with the Convolver). Subsequently, the researcher tries to obtain the pointer of the feedforward_array in the second trigger UAF.
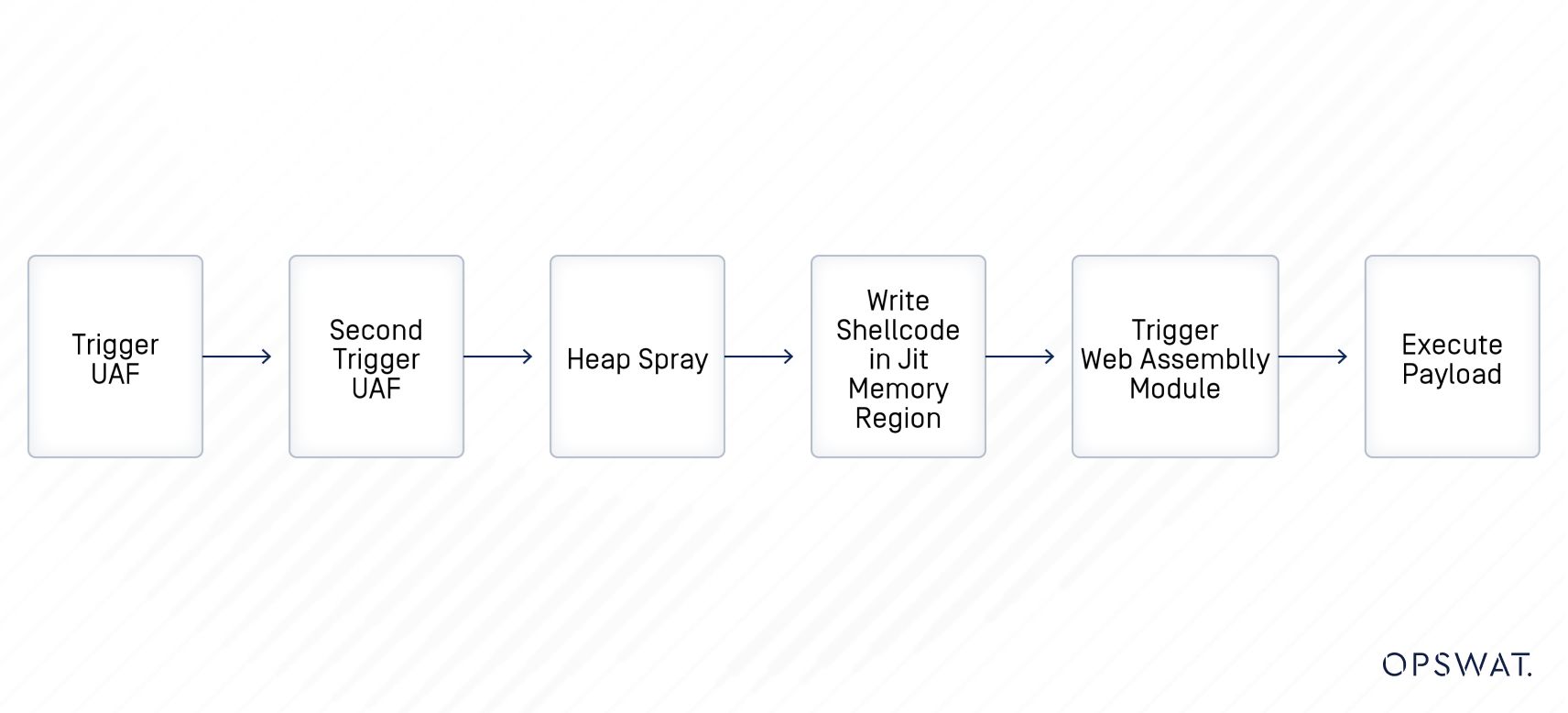
WebAssembly handles the execution of the shell code. To enable the execution of the shellcode, the researcher attempts to free the IIRFilter and writes to the GCPreventer until they gain control over where new allocations are made without the need for sprays. Finally, the researcher writes the shellcode to the Just–In Time (JIT) region in memory. Consequently, upon the addition of an error event of the file reader, the WebAssembly module will execute the shell code.
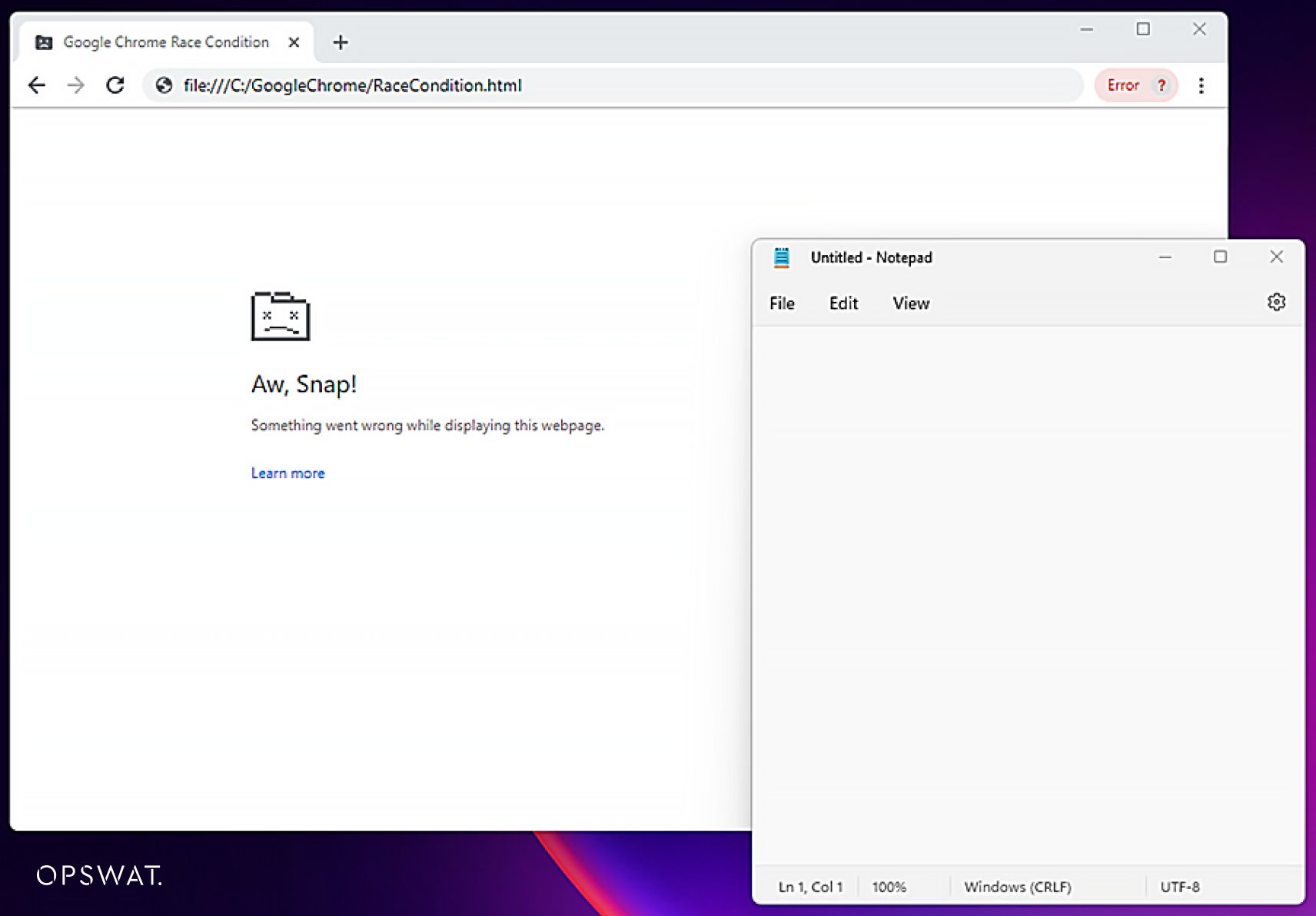
To execute the shell code associated with this vulnerability, the user must disable the sandbox in the vulnerable version of Chrome.

When the shell code is executed, it automatically opens Notepad services on the victim's device.
Remediation Method
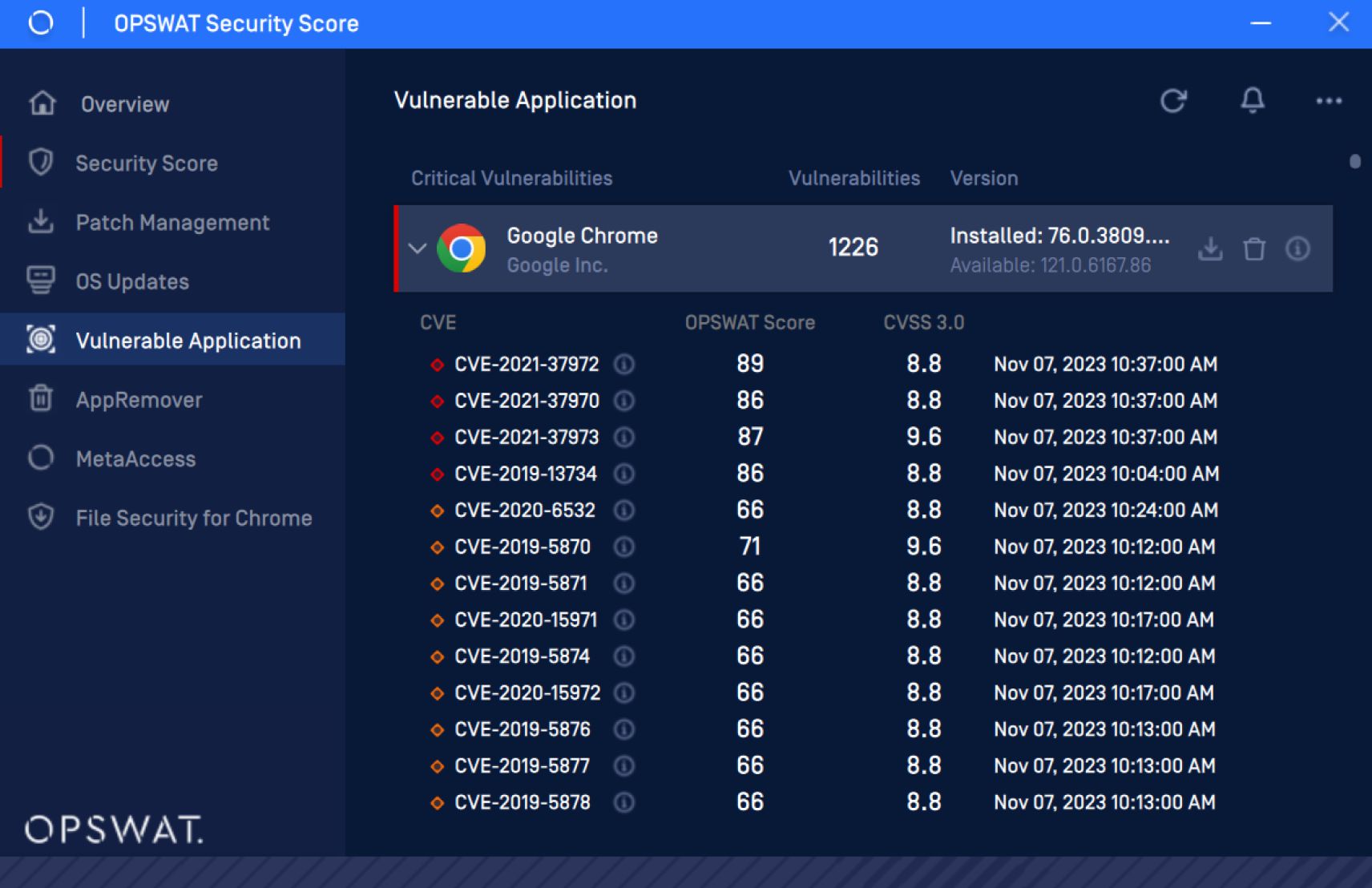
MetaDefender Endpoint, an endpoint security solution engineered by OPSWAT, enables users to detect and defend their systems from these attacks. After the user disables the Privacy Sandbox feature (--no-sandbox), MetaDefender Endpoint can detect CVEs and apply the latest Google Chrome patches. After that, the user can update Google Chrome to the latest version manually or activate the “auto-update” feature under the Patch Management tab to let OPSWAT MetaDefender Endpoint automatically update the browser as soon as new patches become available.
To prevent exposure to malicious code, users should use email filter tools to detect phishing attacks and avoid clicking unknown URLs in emails.
MetaDefender Endpoint Key Product Features and Benefits
- Review and remediate at-risk applications. Vulnerable or out-of-date applications can be viewed within the MetaDefender Endpoint UI.
- Check that anti-malware protection is properly configured on the OS.
- Ensure compliance with organization security standards.
- Hard disk encryption assurance.
- Operating system patch verification.
- Multiple options for malware scanning and making malware-free announcements on endpoints.
MetaDefender Endpoint for Endpoint Vulnerability and Application Patching can be downloaded here.
Reference
- https://nvd.nist.gov/vuln/detail/CVE-2019-13720
- https://bugs.chromium.org/p/chromium/issues/detail?id=1019226
- https://www.w3.org/TR/webaudio/
- https://security.gentoo.org/glsa/202004-04
- https://www.cve.org/CVERecord?id=CVE-2019-13720
- https://packetstormsecurity.com/files/167066/Google-Chrome-78.0.3904.70-Remote-Code-Execution.html
- https://devopedia.org/race-condition-software
- https://webassembly.org/
- https://www.researchgate.net/figure/WebAssembly-high-level-architecture_fig1_360232889
- https://www.researchgate.net/publication/331990070_Native_Web_Audio_API_Plugins
- https://whitehat.vn/threads/gioi-thieu-ky-thuat-khai-thac-exploit-heap-spray.5056/
- https://www.opswat.com/

