A vulnerability is a security flaw in an application that attackers can exploit. Vulnerabilities leave software and systems open to all sorts of cyber attacks.
Software vendors repair these vulnerabilities in the form of patches or software updates, but if those updates are not installed by the user, the system will remain vulnerable to exploits. For this reason, vulnerabilities are a major security risk for many organizations. IT administrators and security officers need to be able to quickly detect and assess vulnerabilities present on endpoints in a network.
In this blog post, we will demonstrate how outdated software can be exploited in order to install ransomware, and how to prevent this with the OPSWAT Vulnerability Engine.
Exploiting a Vulnerability to Install Ransomware
Click image to expand
Acrobat Reader 17.9 could safely and successfully open the malicious PDF like normal, without any kind of exploit taking place.
Click image to expand
However, when we opened this PDF in the second system with Acrobat Reader 8.1...
Click image to expand
...Adobe Reader crashed.
Click image to expand
Next, the malware automatically created an executable file and the file executed itself, and then...
Click image to expand
...within seconds the executable file encrypted all the files in the system.
Click image to expand
Finally, the following pop-up appeared:
Click image to expand
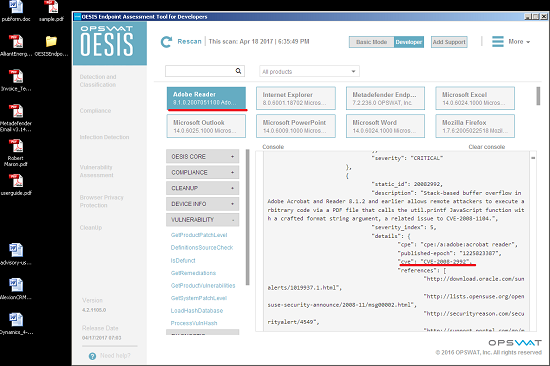
Basically, the malicious PDF exploited CVE-2008-2992 to cause buffer overflow, executed a script to download ransomware from a server, and then ran the ransomware!
Detect Vulnerabilities with the OPSWAT Vulnerability Engine
Let's try using the OESIS Endpoint Assessment Tool, which integrates with the OPSWAT Vulnerability Engine, to scan the two systems described above.
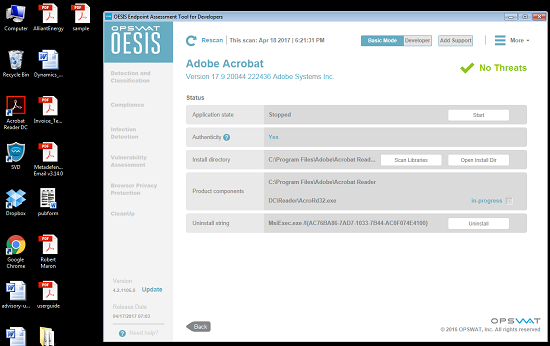
In the first system, the tool detected Adobe Reader 17.9.
Click image to expand
Taking a look at the details, we can see that no vulnerabilities were found in Acrobat Reader 17.9.
Click image to expand
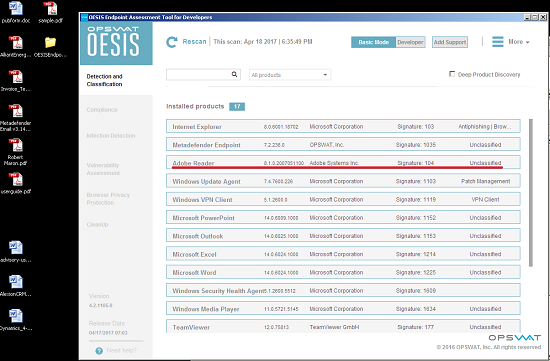
In the second system, the Vulnerability Engine detected Acrobat Reader 8.1.
Click image to expand
It detected a lot of vulnerabilities in Acrobat Reader 8.1 (identified by CVE ID), and one of them is CVE-2008-2992.
Click image to expand
Key Takeaways
If applications are not fully patched and updated, malicious software — in this example, ransomware — can infect a system in the amount of time it takes to open a document.
This is why it is so essential to gain visibility into all vulnerabilities present on a system; typically, because any given system will have a multitude of applications installed, there will be multiple vulnerabilities of varying severity.
The OPSWAT Vulnerability Engine provides a report on the vulnerabilities present on a system or network within just a few moments.
Learn more about the OPSWAT Vulnerability Engine here.