In a startling revelation that underscores the constant threat of cybercrime in the retail sector, Pepco Group, a prominent European discount retailer, recently fell victim to a phishing attack in its Hungarian operations. The incident, which led to a staggering loss of approximately 15 million euros ($16.3 million), has sent shockwaves through the industry, prompting businesses to reassess their cybersecurity measures.
The Attack: A Brief Overview
On February 27, 2024, Pepco Group disclosed that its Hungarian business unit had been targeted by cybercriminals employing phishing techniques. Phishing, a method where attackers disguise themselves as trustworthy entities to deceive individuals into divulging sensitive information, has become a common yet successful tactic used by threat actors.
In Pepco's case, the attackers successfully siphoned off about 15 million euros, leaving the company in a precarious situation regarding the recovery of the funds. Despite the financial setback, Pepco assured the public that no customer, supplier, or staff data had been compromised.
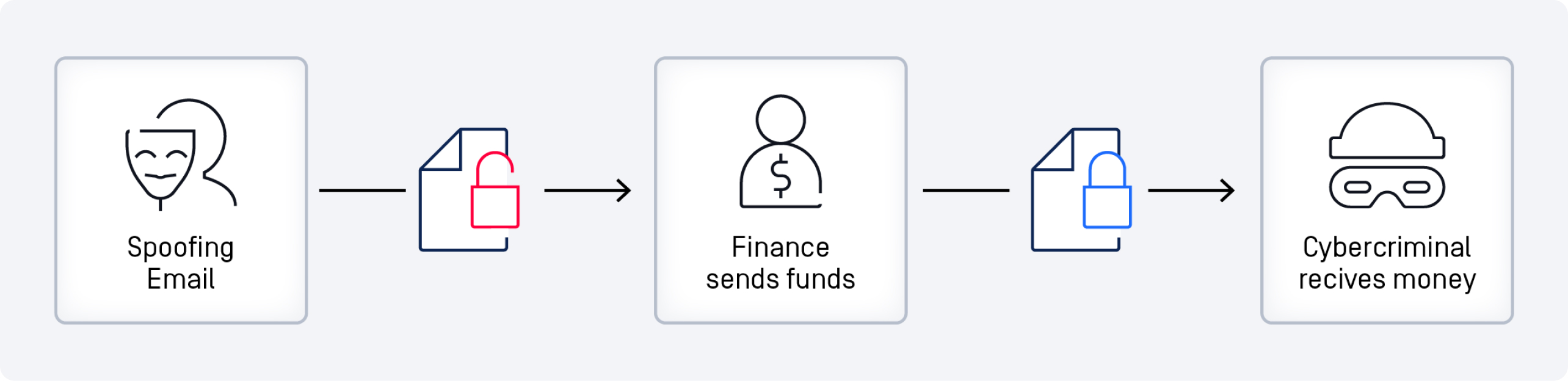
Possible Phishing Tactics Used in the Pepco Group Attack

Email Spoofing:
The attackers sent emails that appeared to come from senior executives or trusted internal sources. This involved forging the "From" address to make it look like it originated from within the organization.

Social Engineering:
The attackers used convincing scenarios and language that prompted the recipients to act quickly without verifying the authenticity.

Urgency and Authority:
Emails were crafted to convey a sense of urgency and came from figures of authority within the company, such as executives or managers.
Personalization and AI Tools:
The attackers possibly used AI tools to personalize emails, making them free of typical phishing indicators like spelling errors.
Another technique the threat actors may have used was Business Email Compromise (BEC). This attack aims to gain access to legitimate email accounts to observe internal communications and choose the optimal moment to send fraudulent emails.
An example of this would be where an attacker compromises an executive’s email account, monitors email threads about upcoming payments, and then sends a fraudulent email at a strategic moment to divert funds to an alternate account.
The Response: Strengthening Defenses
In the aftermath of the attack, Pepco embarked on a comprehensive review of its IT security and financial control systems. The objective is clear: to bolster the organization’s cybersecurity measures against future attacks. This initiative is not just about damage control but a strategic move to rebuild trust among stakeholders and ensure the integrity of its operations.
Implications for the Retail Industry
The Pepco incident serves as a stark reminder of the vulnerabilities inherent in the digital landscape of retail. Cybersecurity is no longer an IT concern but a strategic business imperative. For CISOs and IT security specialists, this event underscores the need for a proactive and dynamic approach to email security by adding advanced layers of defense to catch what traditional email security doesn’t.
Assess Your Email Security Posture with OPSWAT
This latest breach underlines the need for the retail industry to conduct regular assessments of email defenses. OPSWAT offers an Email Risk Assessment that uncovers threats bypassing traditional security solutions like those of Microsoft 365.
One of the key layers of defense used in the assessment, which possibly could have stopped the aforementioned phishing attack, is OPSWAT’s Real-Time Anti-Phishing technology. This solution processes emails through multiple detection mechanisms and content-filtering technology to ensure a 99.98% detection rate of spam and phishing attacks.
Additionally, URLs are rewritten to undergo reputation checks against social engineering at the time-of-click with over 30 sources online. QR Code scanning and rewrite features along with heuristics and machine learning further enhance protection.
Not sure if you need advanced defense layers? Discover if phishing, malware or other exploits have already bypassed your defense and are in your organizations mailbox with an OPSWAT Email Risk Assessment.
This quick assessment is non-disruptive and delivers an actionable report with insights for any CISO or IT security manager seeking to bolster their email security posture.

