Phishing attacks have become a predominant method for cybercriminals targeting critical infrastructure organizations—entities that provide essential services such as energy, water, healthcare and transportation. As these attacks grow more sophisticated, the risks to these organizations escalate, encompassing operational disruptions, financial losses, and reputation damage.
Supported by key findings from the Osterman Research Report, this article explores the importance of real-time anti-phishing solutions in safeguarding critical infrastructure.
Escalating Threat of Phishing in Critical Infrastructure

Phishing poses a significant threat to critical infrastructure organizations due to the sensitive nature of the data and operations they manage. The Osterman Research report indicates that up to 80% of organizations in critical infrastructure have experienced an email security breach within the past year. Such breaches often lead to data theft, operational disruptions and regulatory consequences that can severely impact the organization’s operations, brand reputation and finances.
In fact, critical infrastructure sectors see an average of 5.7 successful phishing incidents per 1,000 employees annually, resulting in compromised accounts, data leakage and even potential ransomware attacks.
For CISOs, these incidents are more than security concerns—they’re direct business risks. A single phishing attack can result in millions in losses from downtime, data loss, and regulatory penalties. The average cost of a data breach has climbed to USD 4.88 million, with phishing-related breaches taking 261 days to contain.
Given the high stakes, critical infrastructure organizations need real-time phishing detection to proactively intercept phishing attempts before they reach end users. Traditional email security solutions are insufficient to address today’s threats, as attackers increasingly use advanced tactics, including socially engineered messages and sophisticated phishing campaigns.
Recent Phishing-Induced Cybersecurity Breaches
Phishing attacks have continued to compromise critical infrastructure organizations in recent years, leading to significant operational and financial repercussions. Notable incidents include:
- POCO RAT malware (2024) targeted Spanish-speaking mining companies, exploiting sector-specific vulnerabilities. They used phishing tactics, including email spoofing that mimics legitimate industry communications, to deceive employees and steal sensitive data.
- Australia's critical infrastructure continues to face escalating threats from phishing attacks, with 25% of recent cyber incidents targeting essential services like electricity, gas, water, education and transport.
- North Korean Cyber Espionage (2024) known as the Andariel group, executed a global campaign to steal military and nuclear secrets, as well as targeting the medical, energy and engineering sectors.
- North Korean Advanced Persistent Threat (APT) group, Kimsuky, continues to conduct sophisticated cyber espionage campaign targeting Japanese organizations using malware and phishing. They deploy malware aimed at infiltrating systems to gather sensitive information.
These breaches underscore the urgent need for organizations to implement enhanced detection to stop the advanced threats, including zero-day and emerging attacks, phishing emails sent from legitimate but compromised accounts and social engineering and technical attacks.
Business Implications of Phishing Attacks
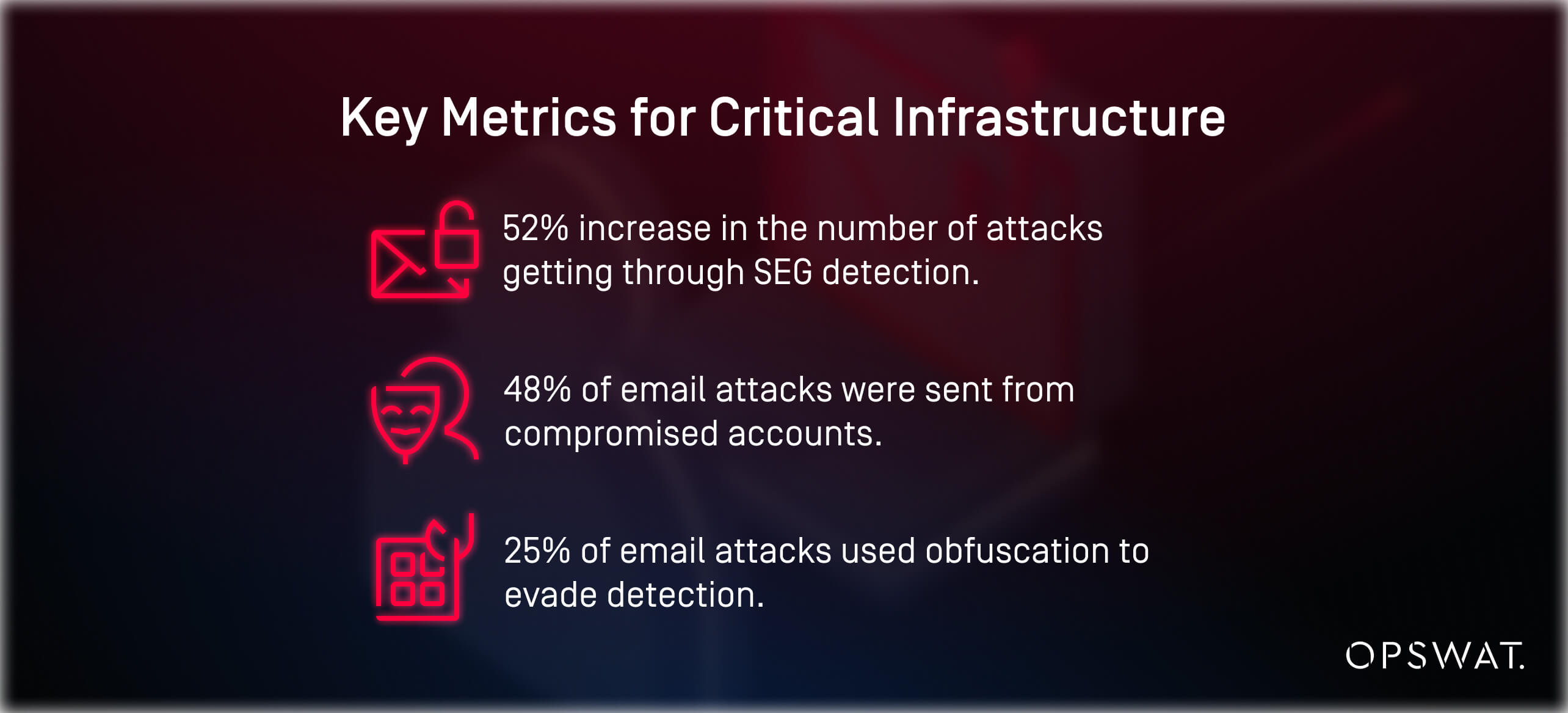
For CISOs, the consequences of phishing attacks extend beyond immediate data loss. The financial, operational and reputational risks are substantial. According to the Egress Email Security Guide 2024:
- There was a 52% increase in the number of attacks getting through SEG detection, with 68% of these emails passing authentication checks, including DMARC (a primary detection capability used by SEGs).
- 48% of attacks were sent from compromised accounts, enabling them to more easily bypass reputation-based detection.
- Phishing hyperlinks were the most frequent payload, as these websites can be created and recreated faster than they can be blocklisted.
- 25% of email attacks featured technical obfuscation measures that enabled them to evade detection, such as hijacking legitimate hyperlinks (e.g. to file sharing sites), html smuggling, and quishing.
Given these high stakes, real-time phishing detection is critical—not only for preventing breaches but for protecting an organization’s bottom line and reputation.
How Real-Time Phishing Detection Makes a Difference
Given that human error accounts for 82% of breaches involving phishing, according to the Verizon Data Breach Investigations Report, real-time detection must happen before users are exposed to potential threats. For CISOs, this underscores the need to remove the reliance on user vigilance by implementing real-time detection that neutralizes threats before they can cause harm.
The Osterman Research report highlights that threat levels for phishing and related cyberattacks are expected to increase across all regions, with over 80% of organizations anticipating that phishing, data exfiltration and zero-day malware attacks will rise. This expected growth in threat levels reflects an urgent need for real-time anti-phishing solutions capable of adapting to evolving attack techniques.
Real-time phishing detection solutions provide organizations with advanced features such as Time-of-Click analysis that blocks malicious links as soon as they’re clicked, preventing users from landing on phishing websites. They also utilize multi-layered email content scanning and behavioral analysis to identify suspicious patterns, as well as advanced DNS filtering to block access to known phishing domains.
Some of the key components of real-time phishing detection also include:
URL Filtering & Blocking
Phishing emails often contain links to malicious sites designed to steal credentials or sensitive data. Real-time URL filtering ensures these links are blocked as soon as they are detected, reducing the likelihood of successful phishing attacks.
Email Content & Attachment Scanning
Advanced anti-phishing solutions analyze email content and attachments in real-time, flagging suspicious language patterns or malicious files before they can reach the inbox. This stops threats that exploit user trust in familiar or official-looking emails.
Deep Content Disarm & Reconstruction (CDR)
OPSWAT’s Deep CDR™ Technology addresses the risk of malicious attachments by disarming potential threats hidden within files. This technology analyzes and reconstructs over 180 file types, ensuring that even the most complex threats embedded in attachments are neutralized.
Real-Time Adaptive Sandbox
OPSWAT’s sandbox solution conducts malware analysis within seconds—ten times faster than traditional sandboxing—identifying and blocking dangerous attachments or links before they can affect the network. This technology is particularly valuable in preventing zero-day attacks that bypass standard defenses.
Ensuring Resilience Against Phishing Attacks
Phishing attacks present a persistent and growing threat to critical infrastructure organizations, with the potential for severe financial, regulatory, and reputational damage. The Osterman Research report reinforces that phishing remains a top concern, with threat levels expected to increase worldwide. For CISOs, this highlights the need to prioritize real-time phishing detection solutions that go beyond traditional defenses.

