Staying ahead of emerging threats requires more than just reacting to the latest vulnerabilities. One of the key strategies for maintaining robust security is by designing detection capabilities that anticipate future trends. One of the core pieces of InQuest’s FileTAC and MailTAC offerings is a robust repository of malicious file signatures, which often prove their enduring value when older rules detect new threats. This month, we want to highlight the importance of future proofing malware detection and the critical role of proactive threat intelligence.
Future Proofing
Future proofing involves designing resilient detection methods and systems that anticipate and adapt to evolving threats. This proactive approach offers several benefits:
- Long-Term Effectiveness: Well-crafted detection rules continue to protect against new exploit and malware variations, reducing the need for constant updates.
- Resource Efficiency: By maintaining robust detection capabilities, organizations can allocate resources more effectively by focusing on new threats without constantly revisiting older rules.
- Proactive Security Posture: Future proofed detection measures contribute to a stronger overall security posture, providing consistent protection against various threats.
A well-designed system of YARA rules is a great example of this concept. YARA rules are a powerful tool for identifying and classifying malware and other types of files based on pattern matching. These rules are highly adaptable and can be tailored to detect specific threats. A number of public community YARA rule collections exist that excel in this. But one of the true strengths of a high quality detection signature lies in its ability to remain effective over time, even as new threats or new variations of existing threats emerge. When an older YARA rule detects a new cybersecurity threat, it highlights the foresight and effectiveness of well-crafted detection measures.
This is an area that InQuest has focused on in great detail, with publications around what we call detection in depth, as well as an overview of how we perform structured threat context in the form of threat sequence analysis. Using these methodologies, detection engineers can create a library of detection countermeasures that are robust, resilient, and offer forward applicability to evolutions in the threat landscape.
The Importance of Threat Intelligence Research
Robust cyber threat intelligence is the cornerstone of future proof malware detection. It involves analyzing current and emerging threat actors to understand their behaviors, techniques, and trends. It also merges insights based on experience and lessons from past threat research, helping provide a timeline that can support a broader understanding of trends and developments. This research is critical to both informed rule creation and proactive defense.
Informed Rule Creation
By understanding the latest threat landscape, cybersecurity professionals can create signatures that anticipate future attack vectors and malware variants. Our researchers at InQuest dealt with exactly this use case when developing countermeasures for CVE-2023-36884. A sample hash for this is 3a3138c5add59d2172ad33bc6761f2f82ba344f3d03a2269c623f22c1a35df97.
CVE-2023-36884 was a zero-day vulnerability that has been exploited by a threat group known as RomCom for dual-focus operations in the crimeware space as well as in service of Russian strategic interests by targeting Ukrainian and NATO aligned bodies for espionage and credential access motives. The RomCom group overlaps to various degrees with Storm-0978, Hawker, Tropical Scorpius, UAC-0132, UAC-0168, Void Rabisu and UNC4895.
The way this exploit works is similar in some ways to an older vulnerability from 2017 (CVE-2017-0199). In a Microsoft Word document, an embedded or remote OLE object can be silently loaded when the original file is opened. This capability allows Office documents to be carriers for arbitrary nested content, which attackers leverage to produce evasive multi-stage exploits. In this particular case, the malware payload can be found inside an embedded RTF document labeled “afchunk.rtf”. Inside an object in this RTF, this exploit leverages the existing technique also seen with exploits for CVE-2017-0199 to download an additional payload from a hardcoded URL. Since the URL is accessed in the form of a SMB share, it abuses the inherent trust that Windows gives remote network shares.
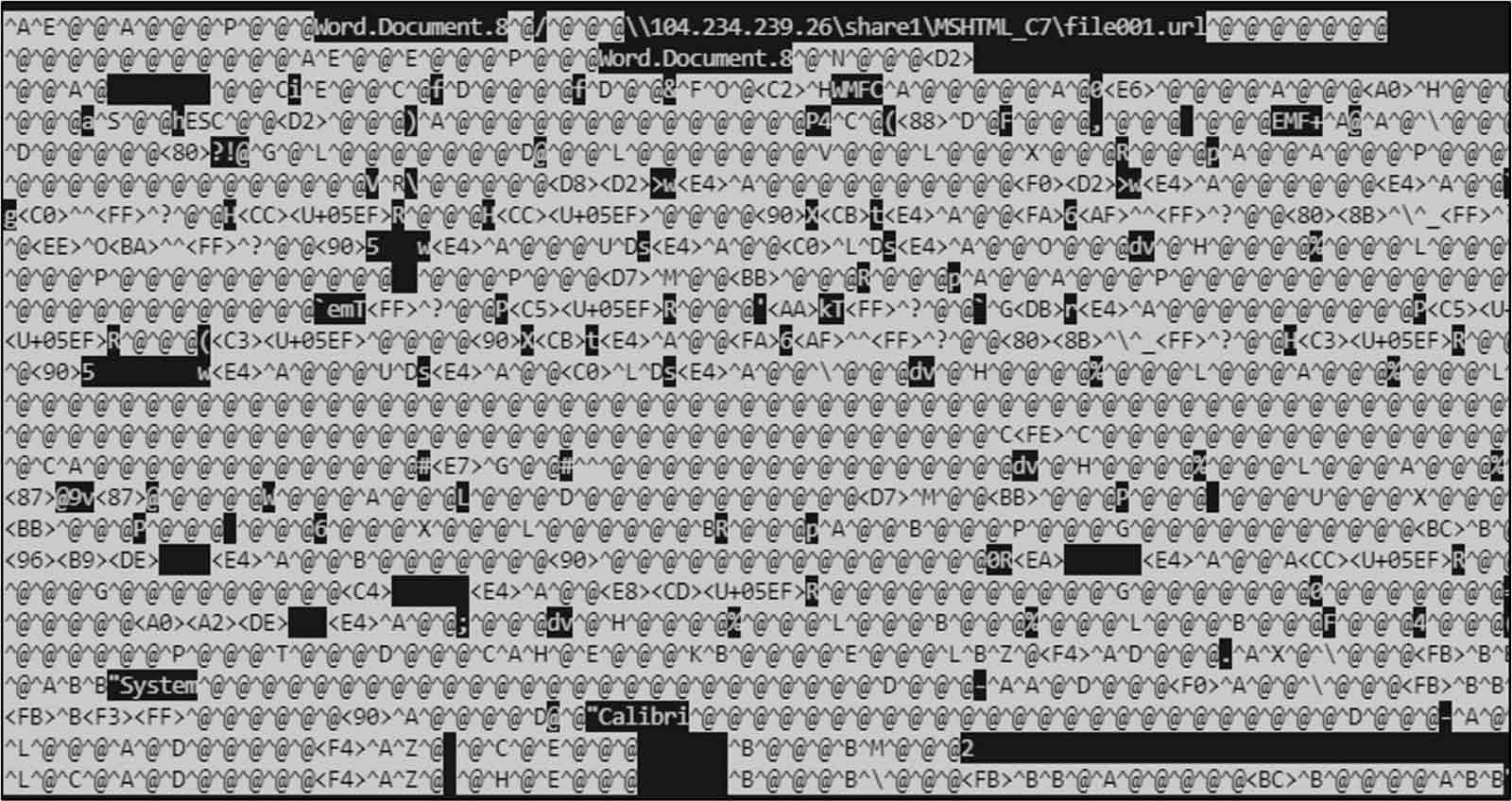
Because the underlying structure of this exploit is similar to CVE-2017-0199, our team found that this new vulnerability (CVE-2023-36884) triggered some of our older detection signatures. The overlaps we noted appeared in the structural aspects of how the exploits were crafted, even if the underlying vulnerabilities were not precisely related.
We can learn an interesting lesson from this case — some detection rules, when engineered broadly enough, can have utility over time, even detecting new zero days based on older techniques.
Proactive Defense
Continuous threat intelligence research enables a proactive defense strategy, identifying and mitigating potential threats before they can cause harm. This concept was put into action by InQuest’s threat intelligence team last month when developing signatures to detect an MHTML vulnerability in Microsoft URL files (CVE-2024-38112).
When developing this signature, our researchers recalled that the malicious URL used within a Microsoft URL file may not necessarily have to be a standard HTTP-based web link. While nothing in the available documentation demonstrated that attackers had used local file paths in this specific exploit, our analyst’s intuition suggested that variations of the attack may be possible. Based on InQuest’s previous research into internet shortcut files (URL files) as used in security feature bypass exploits, it seems clear that numerous subsystems in Windows can be affected by flaws in applying protections to files accessed over alternate media sources such as SMB, WebDAV, or potentially other protocols when using the file:// URL prefix. This seems to stem from inherent trust given in Windows to files sourced from what are typically considered more trusted zones used in internal network environments. In fact, variations of this theme are revisited once again recently in ZDI’s analysis of CVE-2024-38213, making it clear that countermeasures against these types of vulnerabilities need to consider a broader set of inputs than may be immediately obvious. As a result, the detection signature we created for this exploit was designed to anticipate this kind of variation in the future.

Concluding Thoughts
Both of these cases highlight a central theme: threat intelligence is the cornerstone of robust, future proof detection capabilities. Hand-crafted detection rules exemplify this capability, often detecting new threats with older, well-thought-out signatures. Detection signatures crafted with detection in depth and robust threat sequencing analysis in mind tend to be more resilient in the face of evolutions in the threat landscape. This effectiveness over time underscores the importance of foresight in rule creation and the critical role of threat intelligence research.
By focusing on future proof measures and investing in threat intelligence, organizations can maintain a more resilient security posture as the threat landscape continues to evolve.
InQuest was recently acquired by OPSWAT. Read the announcement here: OPSWAT Acquires Inquest Strengthening Federal Go-to-Market Strategy, Network Detection, and Threat Detection Capabilities
Author: Darren Spruell, Hunter Headapohl

