MetaDefender Sandbox 2.4.0 marks a major leap forward in threat detection, enterprise integration, and user experience. With new emulation capabilities, seamless SSO support, and enriched UI workflows, this release empowers security teams to analyze threats faster and with greater accuracy. Explore what’s new, what’s improved, and how your threat defense just got smarter.
What's New
This release brings powerful new features designed to enhance enterprise readiness, user access, and analytical depth.
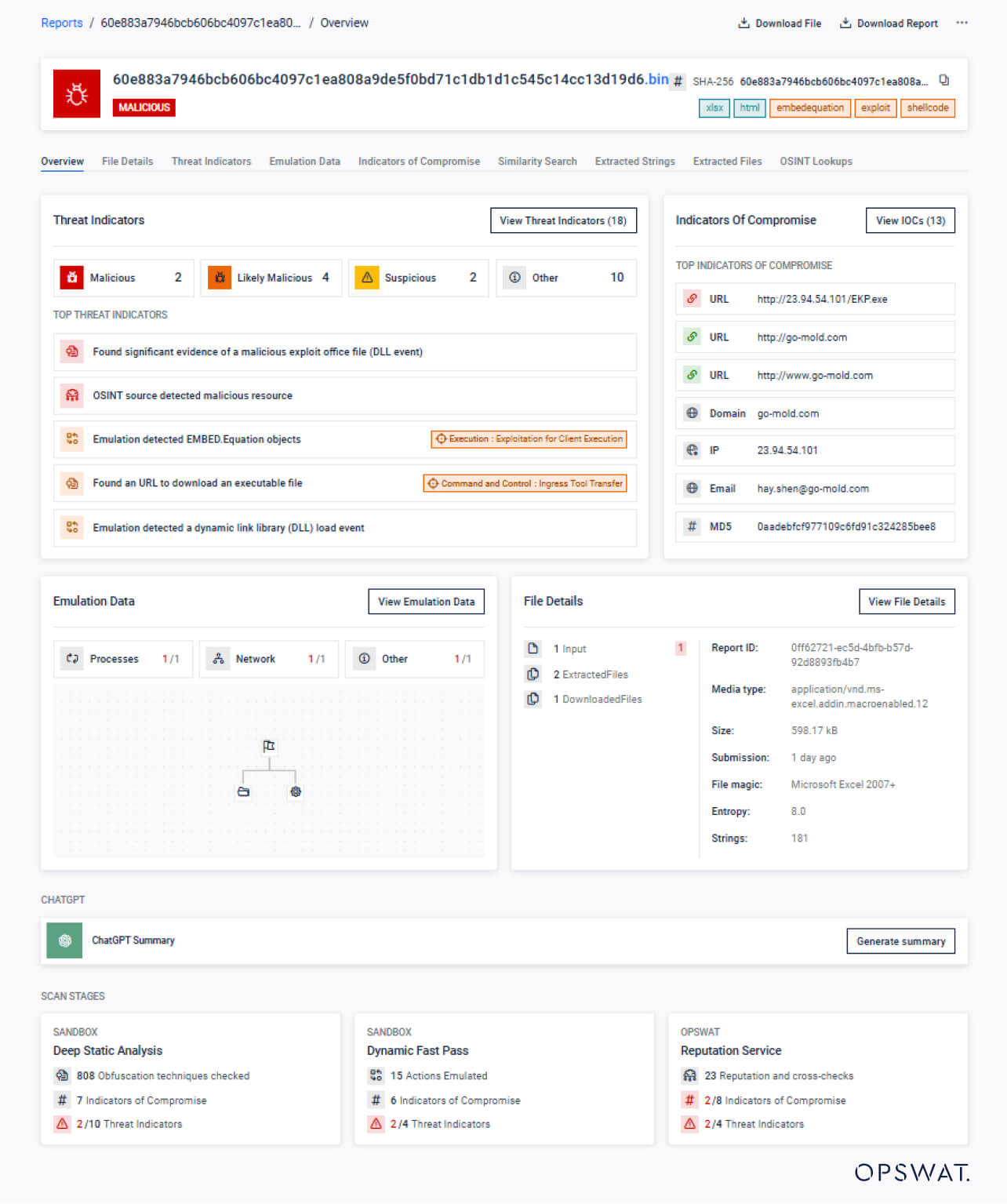
- Report Overview Redesign
Explore a fully reimagined UI designed for clarity and speed—featuring intuitive navigation, dynamic filtering, and consolidated threat insights in a single streamlined view.
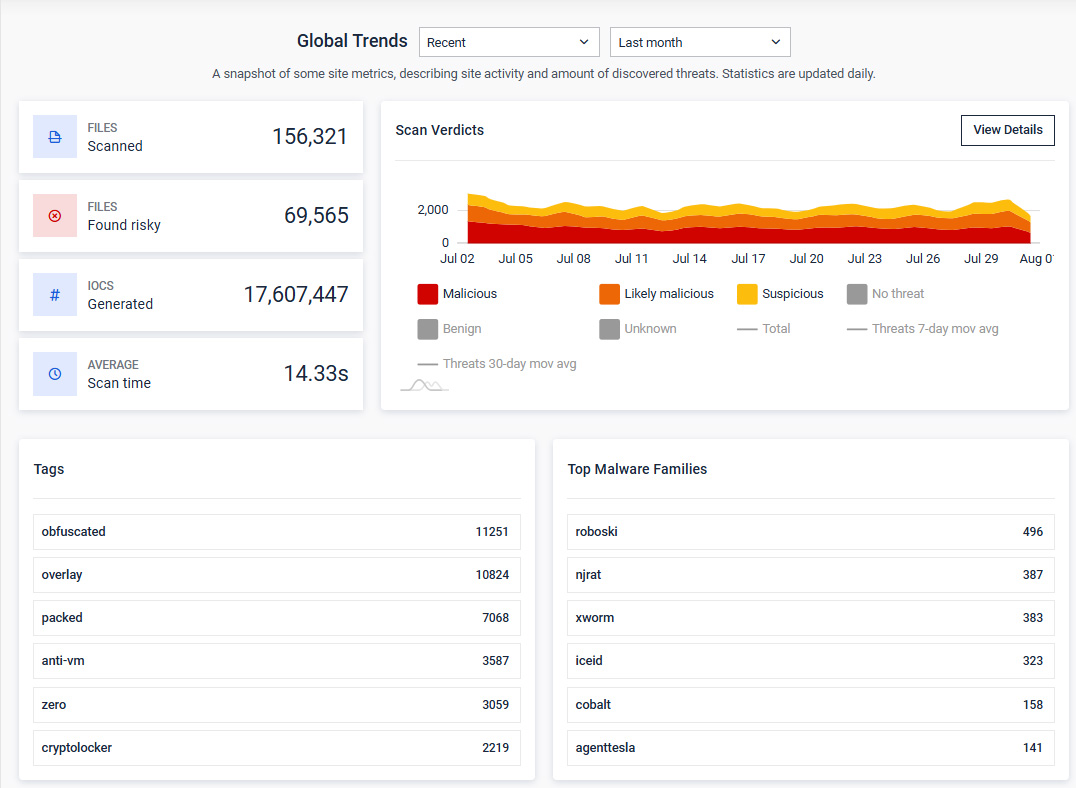
- Trends Page Redesign
Seamlessly navigate the enhanced Trends page featuring a refreshed layout, and intuitive visuals — unlocking deeper visibility with updated charts on scan verdicts, average scan time, IOC generation, and leading threat indicators.
- SAML 2.0 Identity provider (IDP) Integration
Seamlessly integrate MetaDefender Sandbox with enterprise SSO solutions like OKTA, Ping, and Active Directory Federation Services (AD FS) using full SAML 2.0 Federation—streamlining user management and reinforcing your organization’s security posture. - Red Hat Offline Installation Mode
Securely deploy Sandbox in air-gapped environments with full support for offline installation on Red Hat Enterprise Linux 9. - Advanced Windows PE Emulator (Beta)
The Advanced Windows PE Emulator Beta already delivers significant value by unpacking dynamic payloads, revealing hidden IOCs, and exposing new threat indicators—contributing directly to a real-world impact as measured on Filescan.io: a +48% increase in high‑confidence (“malicious”) verdicts per day, +224% more IOCs extracted daily, and a +159% increase in tag generation.
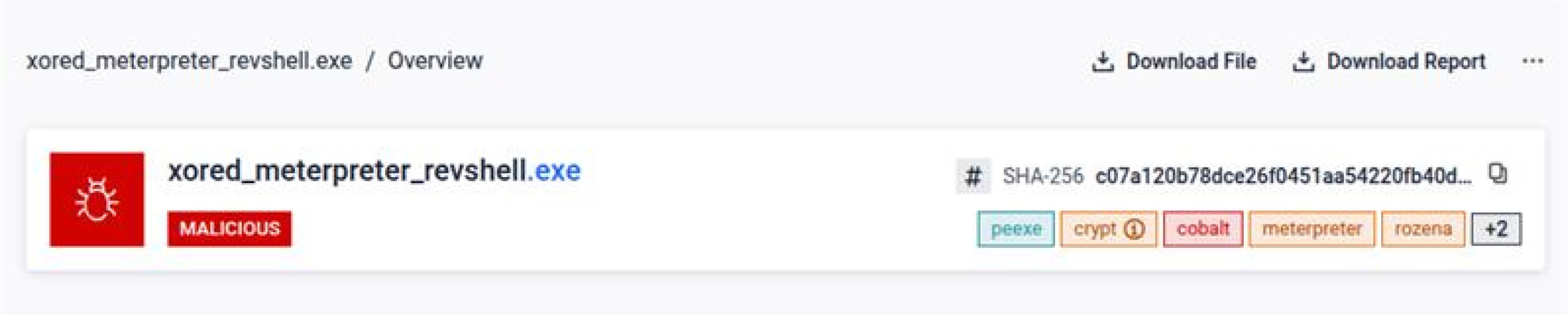
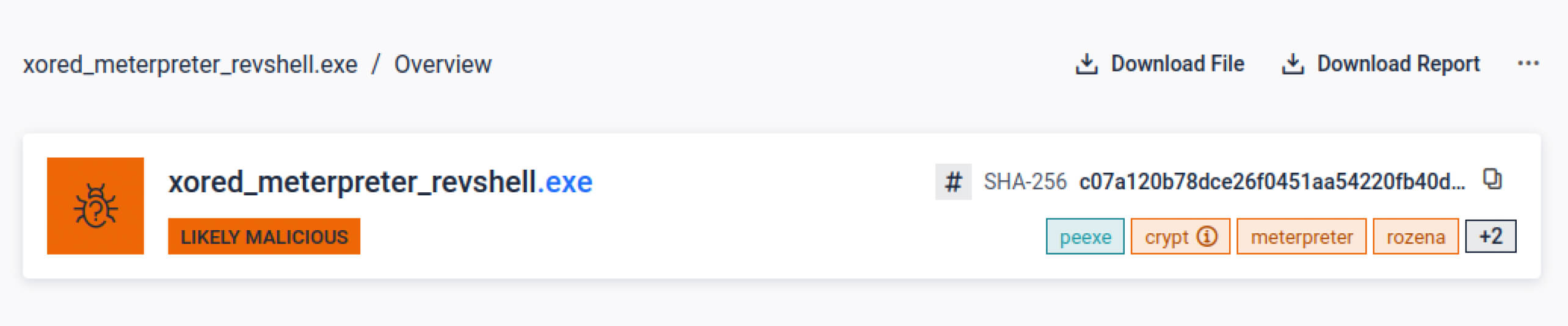
Together, these innovations make MetaDefender Sandbox more intuitive, scalable, and effective for modern security operations.
Improvements
Alongside new features, this release introduces targeted enhancements that streamline performance, resilience, and visibility.
- Threat Indicator Overview Counts
Dashboards now surface distinct threat indicators, cutting through noise to deliver clearer, more actionable risk assessments. - Input Accessibility & Form Refactor
Revamped form components ensure consistent labeling, ARIA compliance, and accessible validation - enhancing usability and aligning with accessibility best practices.
These improvements reinforce MetaDefender Sandbox's role as a foundational tool for advanced threat analysis.
Next-Level Threat Detection
What's New
MetaDefender Sandbox 2.4.0 expands detection capabilities with smarter unpacking, deobfuscation, and variant recognition.
- Updated YARA & Malware Config Extraction Logic
Detection rules and config extraction logic have been updated to better identify Lumma Stealer (ChaCha), MetaStealer, and Snake Keylogger variants. - .NET Loader Unpacking Enhancements
Added support for unpacking Roboski and ReZer0 loaders, along with control flow deobfuscation in .NET files to improve payload extraction.
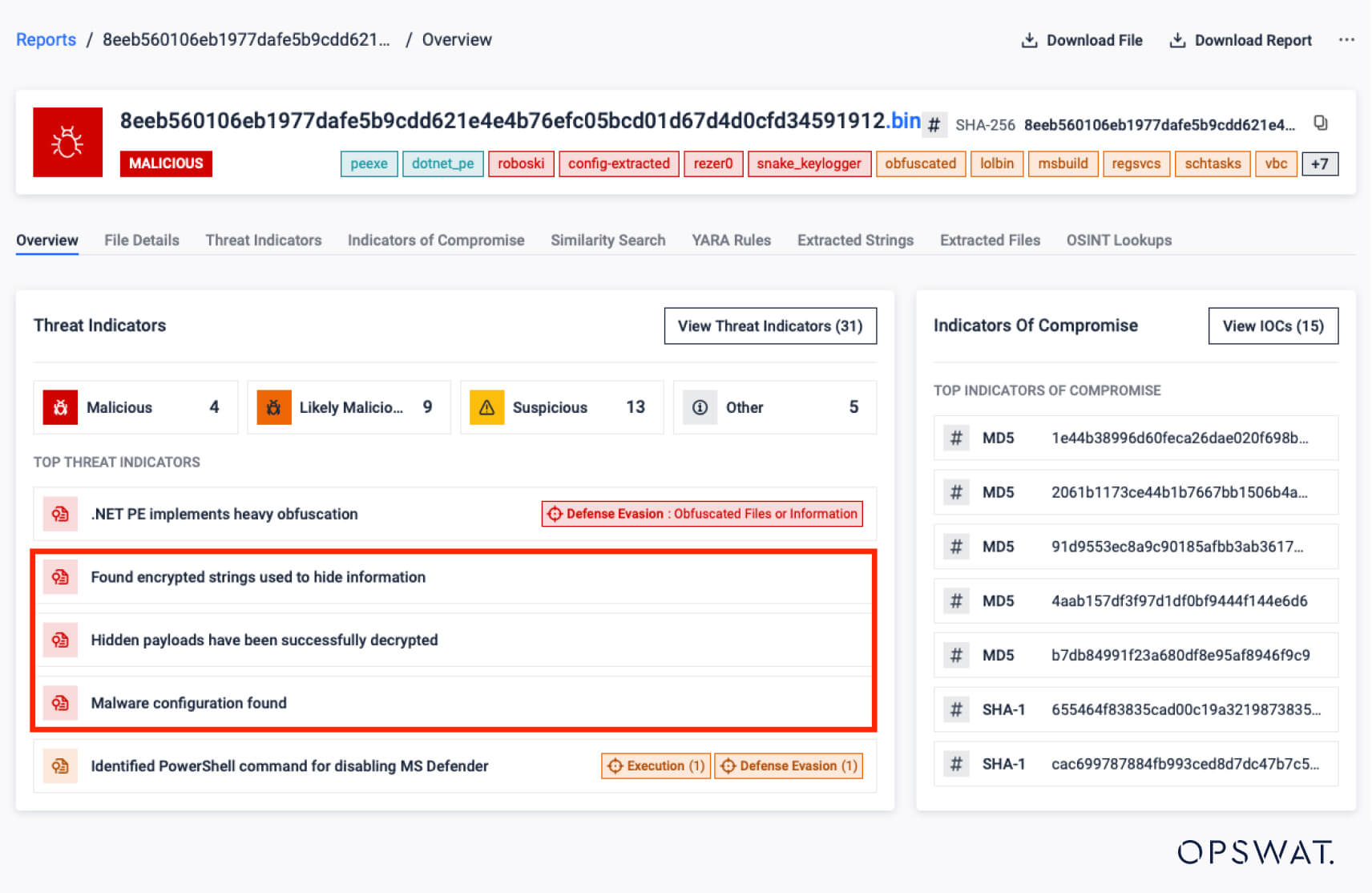
- Control Flow Deobfuscation in .NET Files
Implemented control flow deobfuscation to improve unpacking efficiency and expose hidden payloads in obfuscated .NET samples. - Early Detection for ClickFix Variants
Enabled early-stage detection of ClickFix and related variants—addressing a rising trend in social engineering threats.
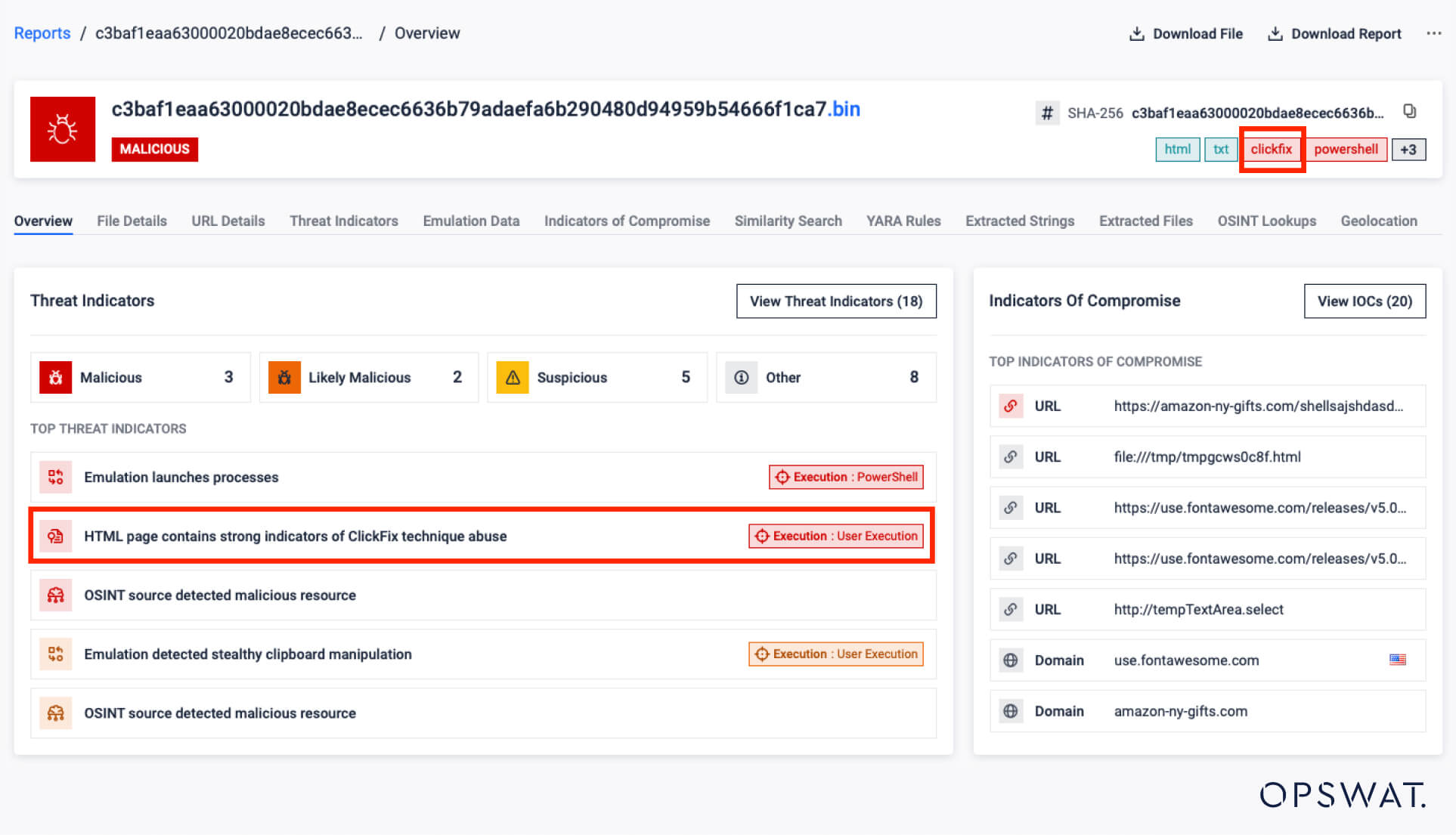
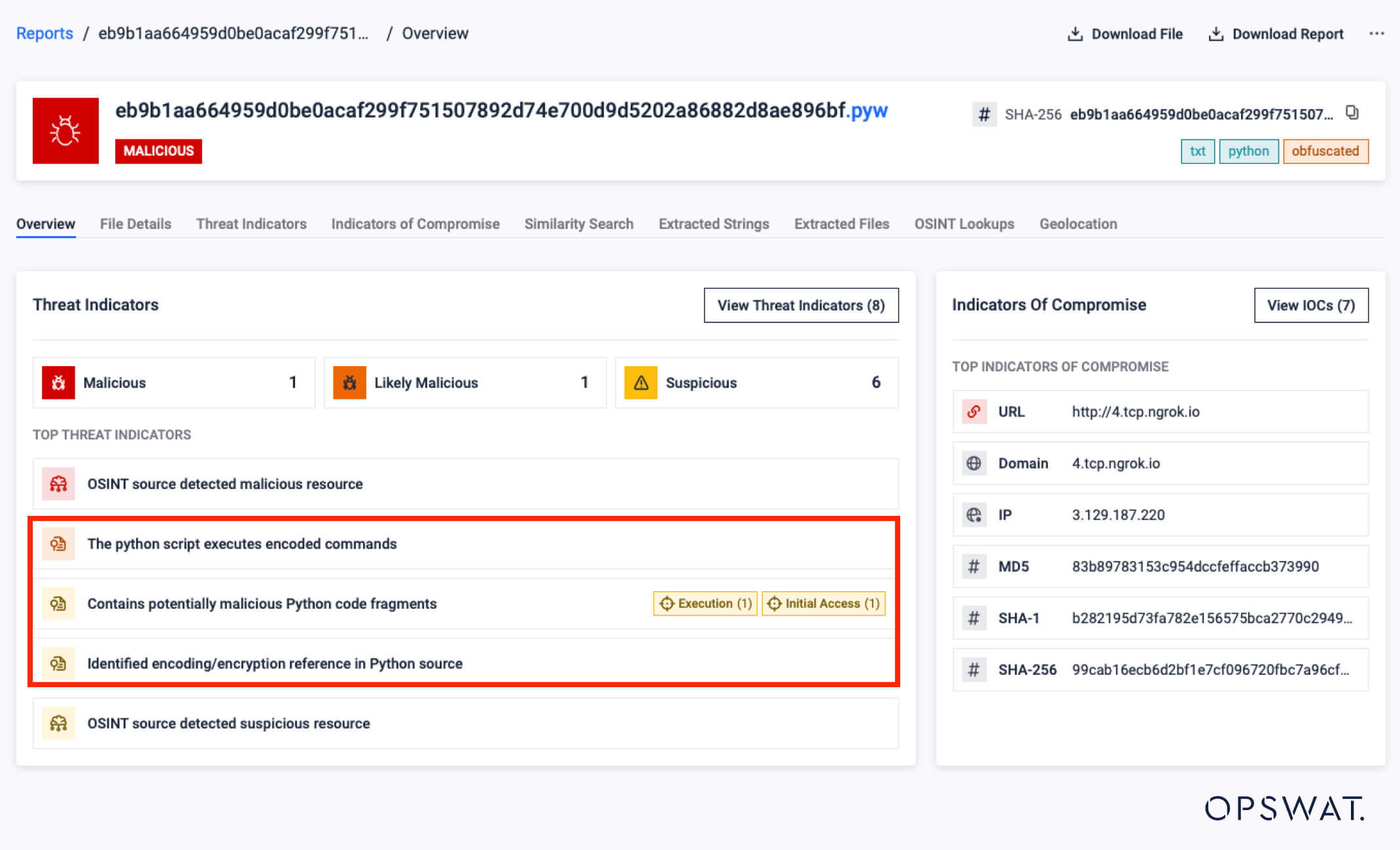
- Automated Decoding of Base64 Commands
Enabled automatic decoding of base64-encoded commands in Python and Bash scripts, revealing deeper obfuscation layers and improving detection accuracy.
- Support for ACCDE File Analysis
Added support for analyzing ACCDE files, extending coverage to Microsoft Access applications and improving visibility into embedded threats.
These additions extend the depth of behavioral insights and surface hidden threats with greater precision.
Improvements
The enhancements in this section sharpen detection accuracy and contextual analysis across a broader threat surface.
- Improved Detection of Suspicious .NET Binaries
Enhanced detection by analyzing low-level anomalies—such as oversized static arrays, high-entropy resources, and irregular call patterns—for earlier identification of obfuscated .NET threats. - Enhanced HTML Threat Analysis
Upgraded HTML parser and expanded detection indicators increase accuracy against evasive or malformed web-based threats. - Expanded IOC & MITRE ATT&CK Coverage
Deeper LNK file parsing, smarter indicator enrichment, and flexible YARA-based tagging sharpen threat correlation and contextual analysis across reports.
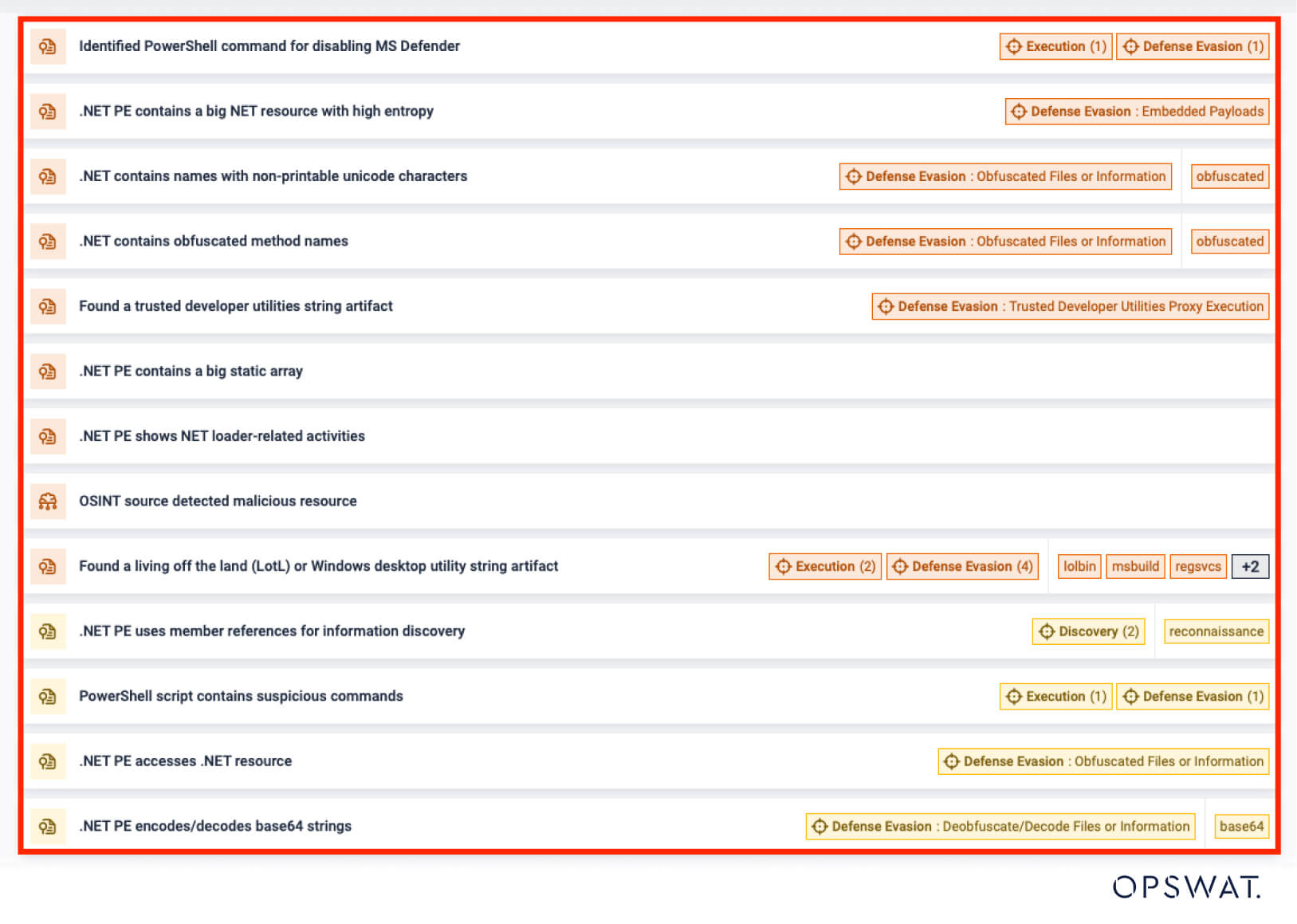
- DIE (Detect It Easy) Database Update
Improved file type and packed binary identification boost classification accuracy across diverse and complex sample sets. - OSINT Lookup Optimization
Disabled lookups for heuristically extracted domains to reduce false positives and improve overall verdict precision.
From static heuristics to dynamic enrichment, these improvements further arm analysts against today’s evasive threats.
Engine Release Notes
Enhancements
The Advanced PE Emulator (Beta) sees major upgrades in this release, unlocking deeper behavioral insights and uncovering threats that evade traditional analysis.
- Shellcode Execution
Added support for standalone shellcode and forwarder binding, enabling deeper analysis of low-level payloads. - Event Tracking
Captures suspicious activity including memory and disk writes, protection changes, DNS resolution, HTTP requests, and more. - Relevant Dumps
Automatically extracts memory dumps from key execution points—such as PE files—for deeper threat inspection. - Integration with Disassembly
Routes meaningful memory dumps directly into the disassembler pipeline for enhanced in-depth analysis. - Overview and Trace
Introduces summary stats, versioning, and configurable API log enhancements for richer execution trace visibility. - New Threat Indicators
Adds PE-specific behavioral indicators to provide more targeted and meaningful analysis insights. - Additional IOC Extraction
Leverages emulation to uncover IOCs not visible through static analysis, boosting detection completeness. - Defeating Evasion
Implements advanced simulated fingerprinting to detect and bypass evasive malware behaviors.
These enhancements establish the emulator as a critical asset for detecting complex, multi-stage malware and extracting actionable IOCs with unmatched precision.
What's New
This engine update introduces expanded emulation, advanced indicator logic, and modern script analysis.
- .lnk Batch Drop Detection
Detects Windows shortcut files that generate and execute batch scripts—closing a critical gap exploited by “living-off-the-land” techniques. - Clipboard API Emulation
Web emulation now captures modern clipboard operations like write() and writeText(), exposing techniques used in phishing kits and droppers. - ECMAScript 6 Support in Anesidora
JavaScript emulation now supports ES6 syntax, significantly expanding coverage of advanced and modern malicious scripts.
Each new capability contributes to earlier threat detection and more confident verdicts, especially in complex environments.
Improvements
Performance, fidelity, and automation take a step forward in the engine’s latest refinement cycle.
- Automated Button/Link Clicks in HTML Emulation
Improved emulation triggers UI-driven scripts, increasing detection of drive-by downloads hidden behind interactive elements. - Event Handler Execution on onclick
Inline onclick event handlers are now executed, enhancing detection of exploits embedded in HTML/JavaScript. - document.body.append() & Self-Read / Stage-Spawn Support
Introduced high-fidelity DOM simulation and support for self-referential behaviors to better analyze multi-stage threats. - HtmlUnit Upgrades
Upgraded
Java-based browser emulation brings JavaScript engine fixes, improved CSS rendering, and greater overall stability.
These backend improvements enhance scalability and precision across large volumes and advanced payloads.
Get Started with MetaDefender Sandbox 2.4.0
To learn more, request a demo, or speak with an OPSWAT expert, visit: https://www.opswat.com/products/metadefender/sandbox
Stay ahead of the threat curve.

