We are thrilled to announce our latest initiative, MetaDefender Endpoint Validation. This new layer of security brings comprehensive and advanced protection for critical endpoints, safeguarding against evolving peripheral and removable media threats.
MetaDefender Endpoint Validation
Originating from OPSWAT Media Validation Agent, MetaDefender Endpoint Validation provides organizations with multilayered removable media protection for critical endpoints. Functioning similarly to its predecessor, MetaDefender Endpoint Validation works in both air-gapped and connected environments and serves as a checkpoint, validating whether files from removable media devices were first scanned by MetaDefender Kiosk, ensuring that only validated files can be opened, copied, selected, and accessed by the endpoint. MetaDefender Endpoint Validation also detects unauthorized files and blocks unscanned files from accessing critical environments.
Alongside MetaDefender Kiosk, MetaDefender Endpoint Validation serves as an additional layer of security, protecting critical endpoints from peripheral and removable media-borne threats by enforcing scanning and sanitization policies and offering HID and BadUSB protection. MetaDefender Endpoint Validation detects and blocks USB drives that disguise themselves as HIDs (human interface devices) such as keyboards, preventing them from discreetly executing harmful commands or injecting malicious payloads into critical endpoints.
MetaDefender Endpoint Validation: New Enhancements
| MetaDefender Endpoint Validation | |
|---|---|
| Validate if files from removable media devices were scanned by MetaDefender Kiosk | |
| On-Access file validation | |
| Pop-up notifications for files validation | |
| User Interface (Ul] | |
| Challenge and Response feature | |
| Central management | |
| Commands can be executed with Challenge and Response feature | |
Action with allowing peripheral devices
| |
BadUSB & HID protection
| |
Manifest certificate
| |
MetaDefender Endpoint service
| |
On-Access Validation
When end users need to validate a specific file, they can incorporate that task into their natural workflow with MetaDefender Endpoint Validation by selecting a file or folder via their native application (Window Explorer, Word, Excel, etc.) to trigger the validation process, simply by opening the file. If the file is determined as allowed by the system, it will be unblocked, enabling users to continue their workflow without any disruption.
Improved File Validation Visibility
MetaDefender Endpoint Validation offers an enhanced user experience, notifying the user of the validation process status and its results. This helps users track real-time progress more efficiently.
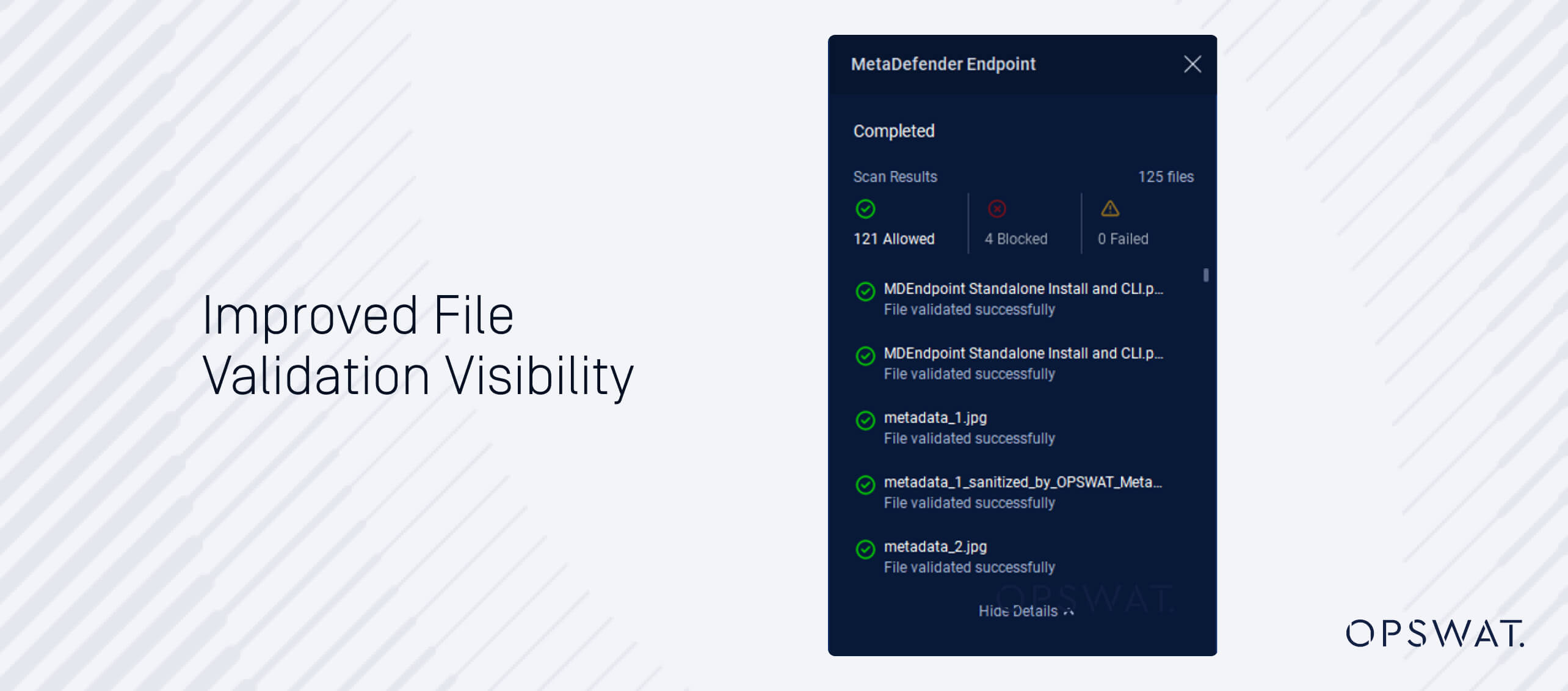
Intuitive User Interface
MetaDefender Endpoint Validation boasts an intuitive UI (user interface) that enhances experience, prioritizing key information and ease of navigation. With a clean, streamlined design, users can effortlessly navigate the product, track status, and execute commands while minimizing the learning curve.
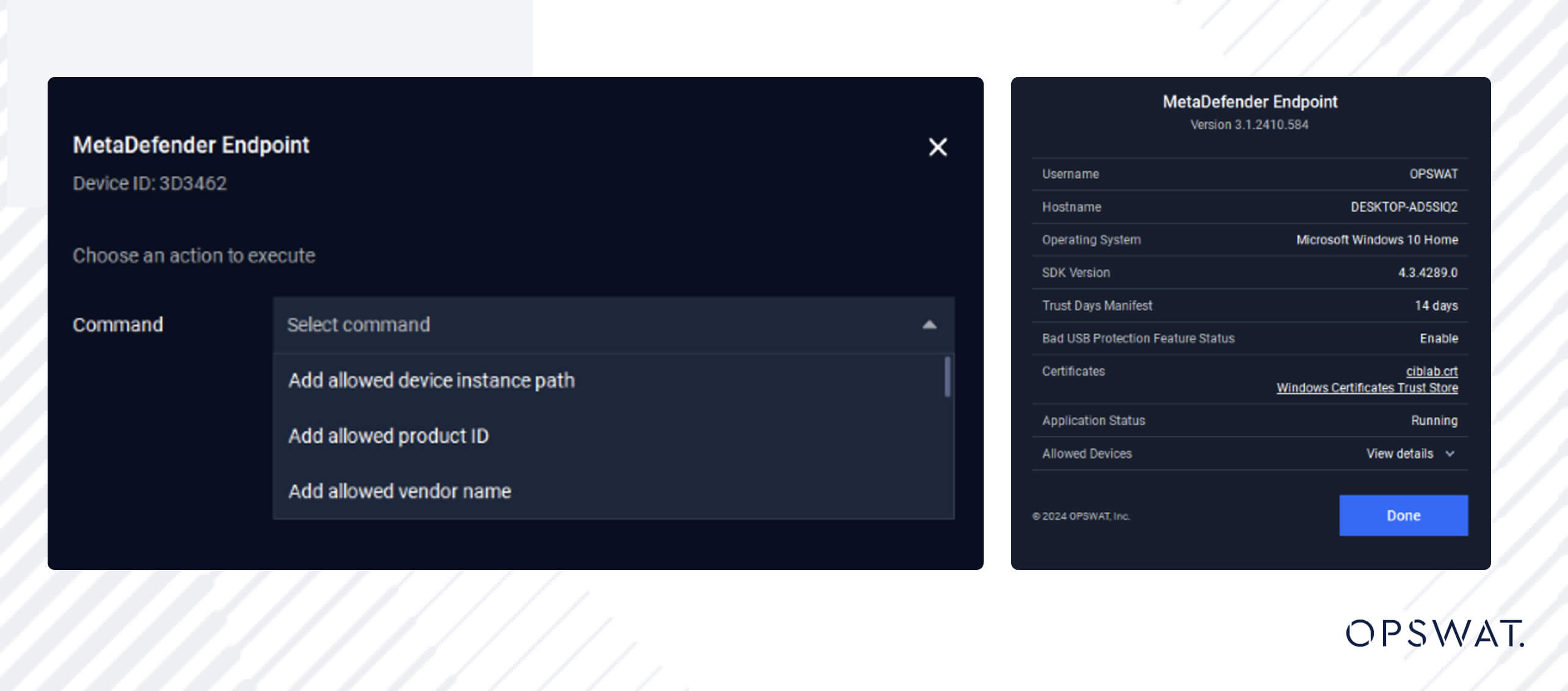
Remote Admin Exceptions
MetaDefender Endpoint Validation offers seamless air gapped, admin-endpoint control and ensures a unified experience without disrupting the workflow. It also increases security as all sensitive commands from the endpoint require a response generated by an administrator to be executed.
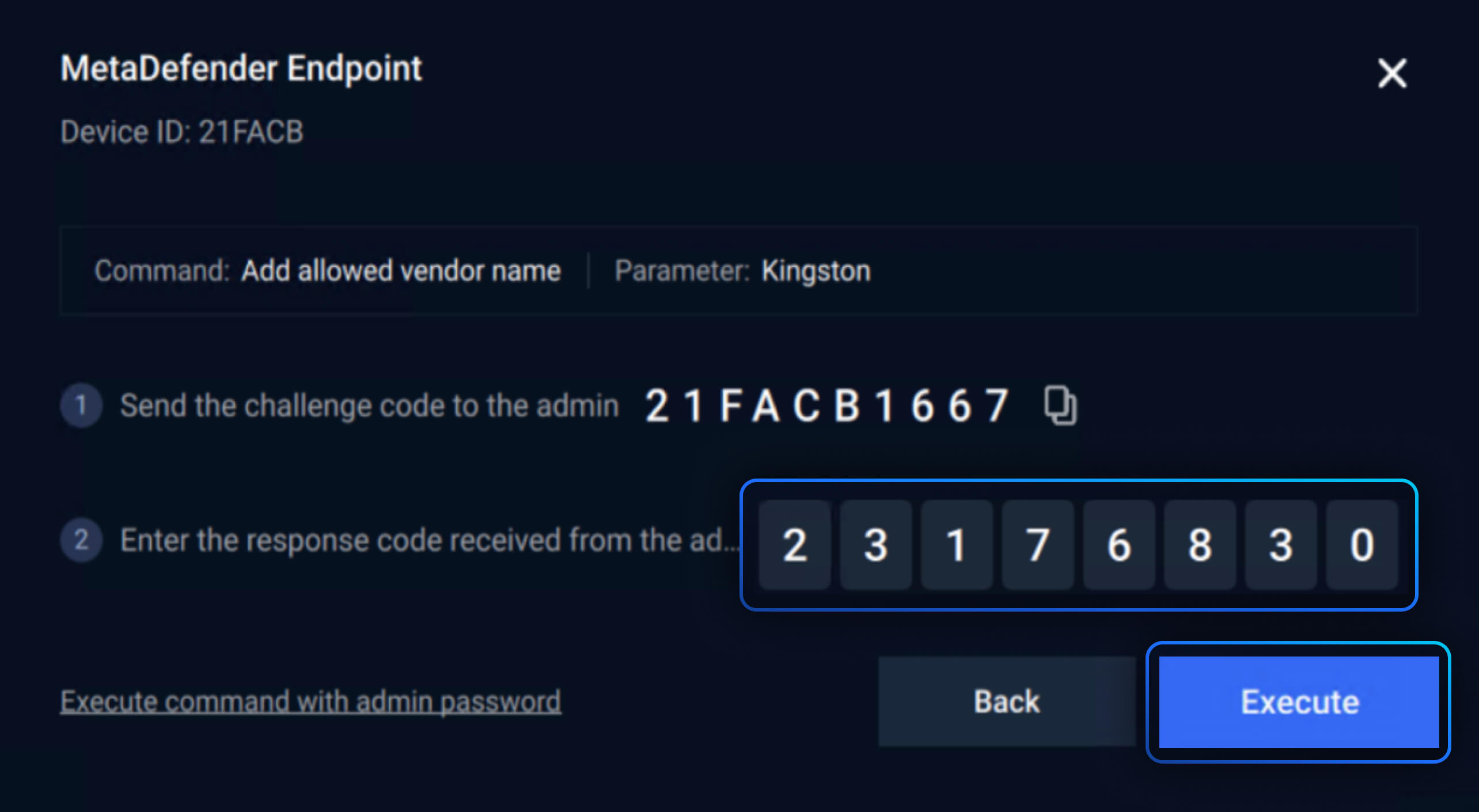
Commands that can be executed with the Challenge and Response feature include:
- Allow by instance path/product ID/vendor name
- Reset allowed list
- Enable/Disable
- Reset HID protection
- Renew manifest certificate
- Update manifest trust period
- Enable/Disable
- Disable by duration time
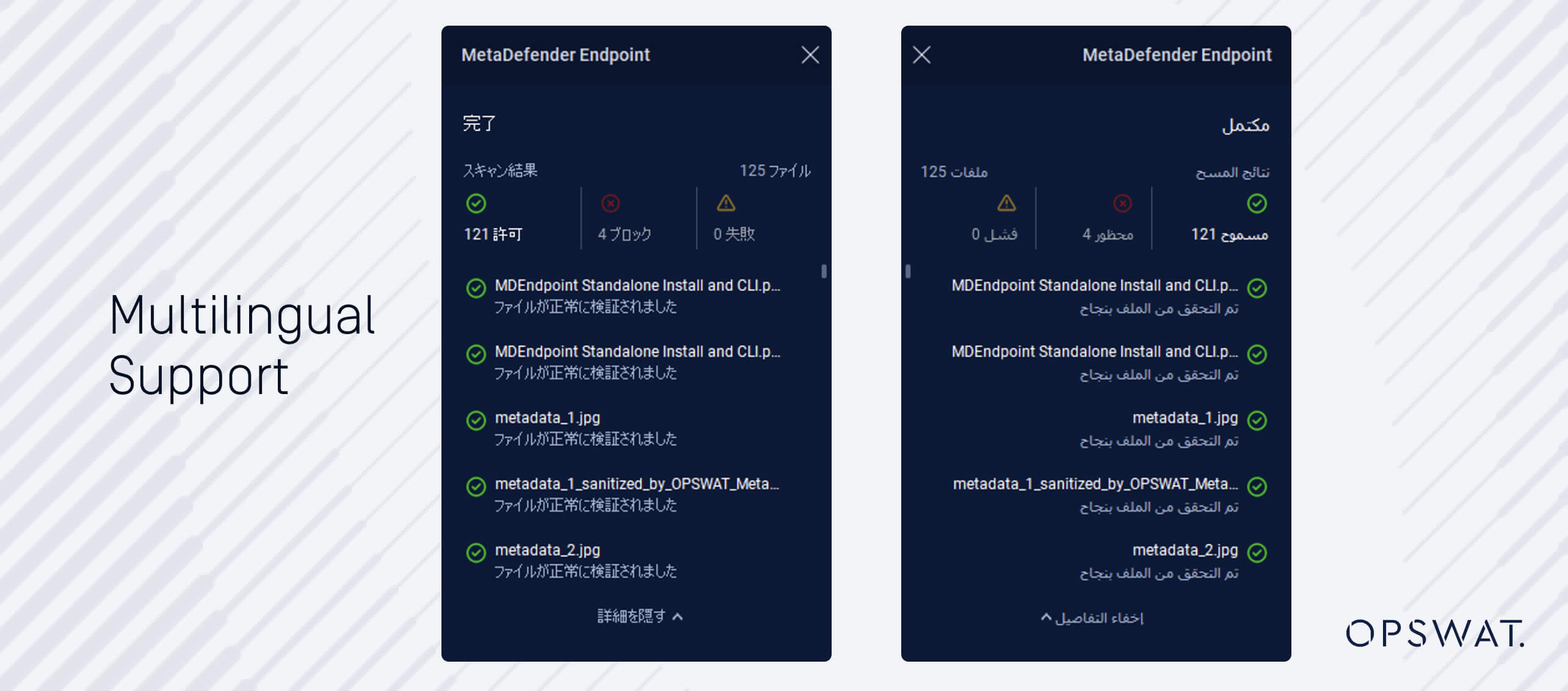
Multilingual Support
Besides English, MetaDefender Endpoint Validation also supports Arabic, Japanese and Hebrew. With this localization—and more on the way—we have minimized potential language barriers and improved overall usability, making it easier for local users in diverse regions.
In-Depth Peripheral Media Protection
Protecting critical environments requires a multilayered approach that includes comprehensive protection against peripheral and removable media threats.
That’s why our solution seamlessly integrates and is easy-to-deploy:
Next-Level Endpoint Security
Discover why worldwide organizations, institutions, and entities trust MetaDefender Endpoint Validation to protect critical endpoints. Talk to an expert today to learn more and see for yourself with a free demo.




