While MetaDefender Access has a deep and wide set of compliance checks out of the box, at times, organizations with network access control solutions have unique or proprietary reasons to go beyond what we offer in the box. Out-of-the-box MetaDefender Access, coupled with the MetaDefender Endpoint, can check far more than just the essential device compliance and security requirements to avoid fines and avoid endpoint-oriented attacks. With the addition of custom compliance playbooks, MetaDefender Access makes it very easy to check one-off endpoint compliance or device security requirements specific to certain organizations.
Why MetaDefender Access Adds Support for Custom Compliance Playbooks
MetaDefender Access already has a custom check capability that supports the use of either PowerShell or Bash (for macOS and Linux). However, most customers do not want to drop into a scripting language to create additional compliance or security check, as it can further complicate the processes. Based on the requests from customers to offer more flexibility and extensibility for the compliance policies in MetaDefender Access that did not depend on scripting, OPSWAT has introduced an ability to visually define compliance playbooks which can be used in MetaDefender Access policies to perform custom, conditional checks.
How to Configure Custom Compliance Playbooks
These playbooks are edited graphically (see the image below), and each playbook consists of a set of actions to perform against the device, such as the fetching the value of a registry key, a value from a file attribute or content, or information about a process. Having fetched the values from the device, actions can be taken conditionally to either move the device to a different device group or set a device status (for example, marking the device as non-compliant).
Here are some use case examples we have encountered across our customer base:
- Confirming that a particular third-party application installed on an endpoint is configured in a way that ensures encryption features are enabled.
- Checking for registry keys or other clues that indicates a device is vulnerable for a zero-day vulnerability and placing the device in a warning state so that the security team can ensure all such devices are remediated promptly.
- Taking a fallback action if one of the primary compliance checks fails. For example, if the antimalware check finds that no acceptable solution is installed and configured properly, the device could be placed in a group that leads to the MetaDefender Endpoint scanning the device with OPSWAT’s multi-scanning technology (running 20+ engines against the files on the device).
This image gives you an idea of the visual editor for the Playbooks. It shows how Custom Compliance Playbooks interact with VMware Horizon, a long-time OPSWAT partner.
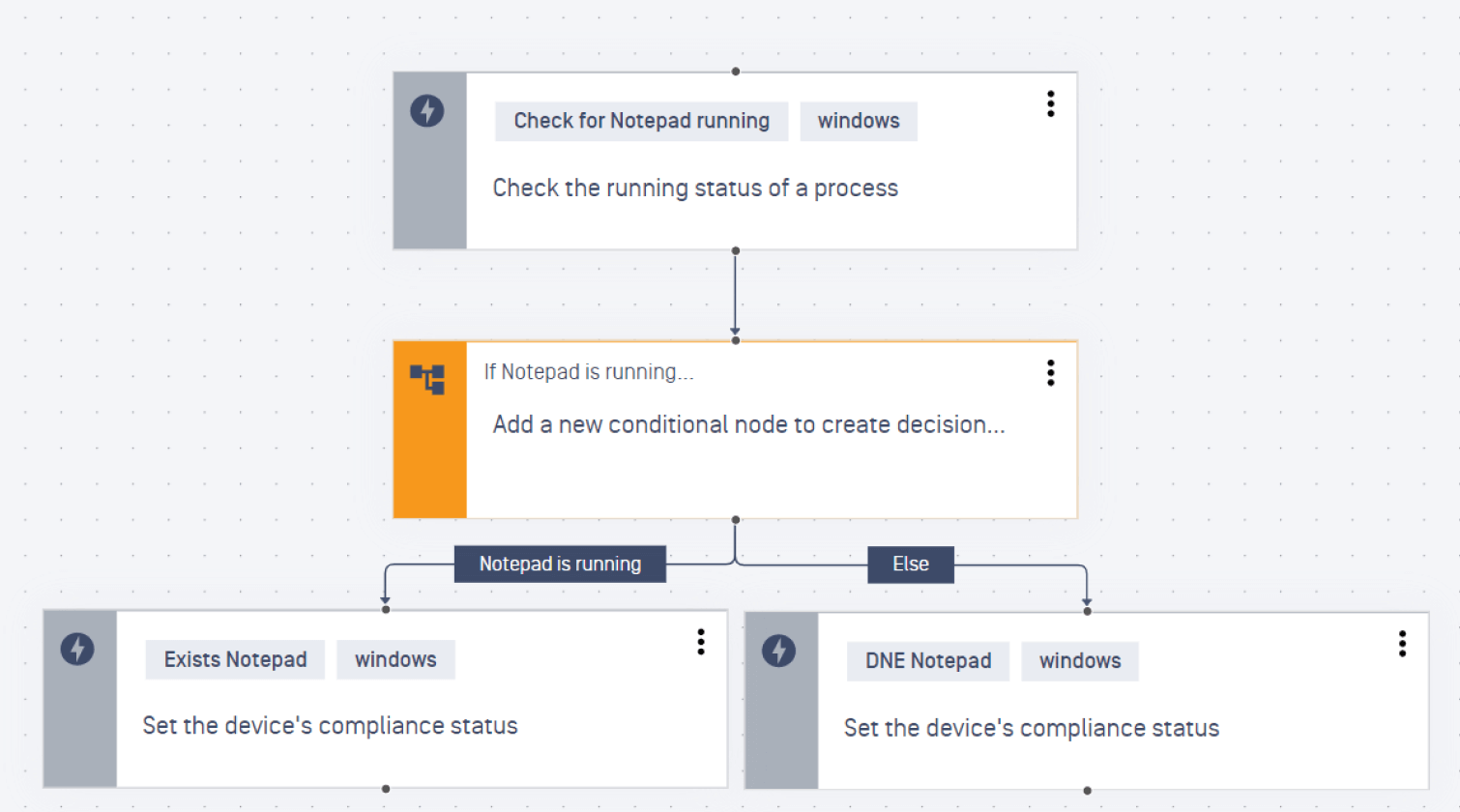
This playbook is an example of the third use case mentioned above. It is checking whether a third-party application is configured securely on the endpoint and whether it remains that way. If the user of the device manually overrides the configuration by editing a configuration file, this security check would fail, and the device would be considered non-compliant.

See How We Work With Vmware To Create Safer Environments For OT Professionals
Talk to an Expert
In addition to the capabilities outlined so far, the playbooks now also help those that do want to leverage custom scripts to do so more granularly, as a playbook can now have custom scripts as tasks. In this way, a MetaDefender Access policy may now apply multiple scripts, a capability that will be well received by many of you. You can select the playbook to use in a policy in the Device Compliance section of the Policy Editor menu. You can also activate custom scripts in the same section as well.
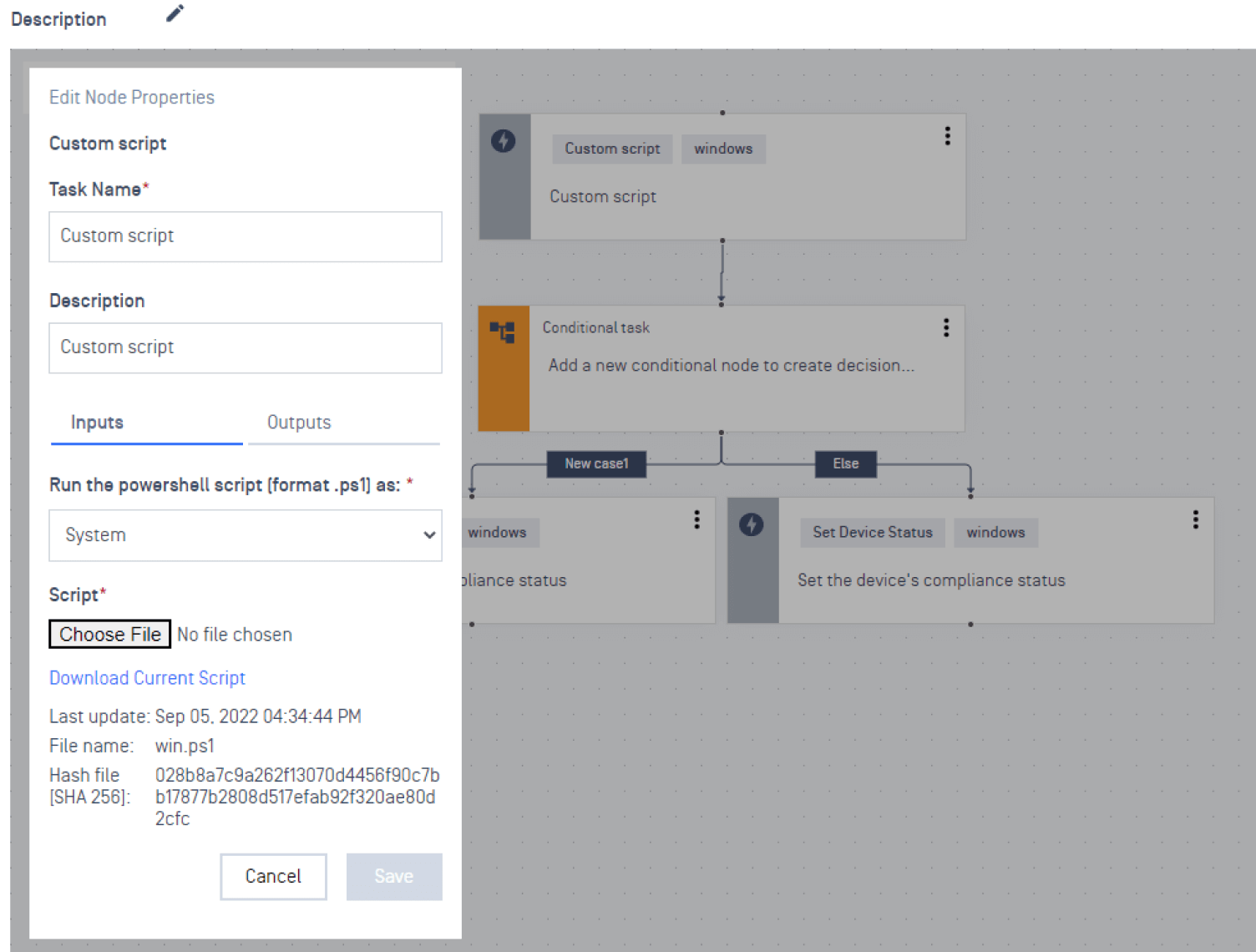
As mentioned above, deep compliance checks integrated into MetaDefender Access do more than any competitor to ensure compliance and security of endpoints across all major operating systems. However, no matter how deep or wide the options we provide are, organizations will always have a particular need that requires a certain degree of customization. Custom compliance playbooks enable organizations to easily integrate specific compliance checks into MetaDefender Access, creating a dynamic and proactive security layer against outside threats.
MetaDefender Access is designed to ensure device compliance and security without impeding productivity, and custom compliance playbooks offer even more flexibility to our customers. If you have a question regarding our security solutions, contact our security experts now to receive assistance.