The Rising Demand for Secure Access
The rise of Bring Your Own Device (BYOD) policies and cloud applications, along with the growing need for remote access to corporate data, has led to a surge in demand for secure access. This also includes oversight and compliance for unmanaged devices.
It is crucial to extend security measures beyond basic checks such as operating system level and antivirus protections. It is important to incorporate safeguards against removable media, unwanted applications, keyloggers and screen capture threats.
The questions arise: How can an organization ensure that every device complies with security policies before accessing applications or the network, regardless of the location of the user or the data? Furthermore, once a device is confirmed compliant, what measures should be in place to defend access to the network, data, and applications from tampering threats?

One Platform for All Endpoints
Addressing these challenges, OPSWAT presents a comprehensive endpoint security management platform, rooted in a zero-trust access philosophy. This platform is uniquely positioned to secure both access and endpoint devices, regardless of the user or data location, aligning with your security policies.
Implementing secure access for remote and on-premises users and ensuring endpoint compliance for managed BYODs and IoT devices, can be complex and time-consuming. It can take months to a year of work from senior network engineers, administrators, and third-party consultants. However, OPSWAT’s integrated platform streamlines this process, reducing the time and resources required.
Why We Employ Zero-Trust Endpoint Management
Cybercriminals are constantly finding new ways to gain access to your data. While the IT industry is continually strengthening its arsenal of threat intelligence, new techniques can fly under the radar, putting organizations at risk. Rather than merely looking for known threats, our zero-trust approach considers all entities untrustworthy until proven otherwise.
The Benefits of Our Endpoint Management Solutions
OPSWAT’s zero-trust endpoint management solution offers extensive advantages:
Simplified Oversight
As workforces become more distributed, oversight is key to protecting endpoints throughout your organization. A single view with all devices and their access methods keeps IT teams informed, even as the team grows. You can allow, block, or enforce rules for a device with a just a few clicks, ensuring all devices are visible and regulated.
Uninterrupted Productivity
Self-remediation capabilities provide clear actions for users to resolve noncompliance with their devices. With these straightforward solutions, end users can maintain productivity and enjoy the convenience of a Single Sign-On (SSO) login, whether on-premises or remotely.
Configurability
Set personal thresholds for access and determine when issues require notifications or blocking. Meet your organization's policies within the compliance module.
Ease
Our endpoint management software offers simple registration and can be deployed in a matter of hours or days, whether on-premises or as a cloud service.
Implement Zero-Trust Access Everywhere
With this single platform approach, ongoing implementation and management both become easier for the IT staff, with no third-party services required. At the same time, users will gain access as needed, with easy self-remediation steps if there are issues to get back in compliance. For common applications such as Omnissa and Salesforce, even stronger integration is available for maximum productivity.
Secure On-Prem Access
For an on-premises environment, OPSWAT provides detailed identification and security compliance to ensure you know exactly what is on your network, can block any unauthorized attempts and enable segmentation placing IoT devices in the proper group.
Secure Cloud, Remote and On-Prem Access
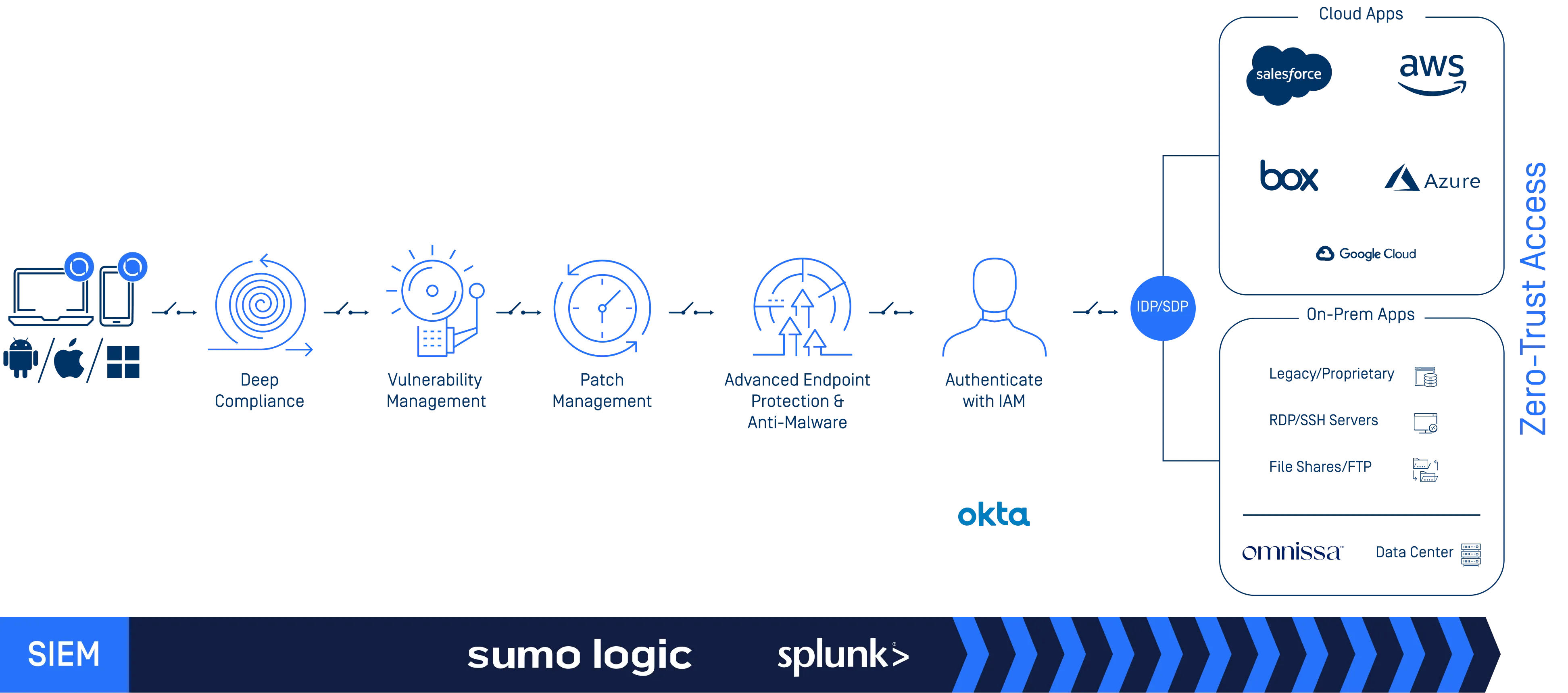
OPSWAT enables cloud integration through Security Assertion Markup Language (SAML), an open standard that allows identity providers (IdP) to pass authorization credentials to service providers (SP). OPSWAT's zero-trust endpoint management platform supersedes VPNs with better security, easier management, and a more positive user experience.
Instant Visibility
OPSWAT provides a comprehensive view of the endpoint health of the entire environment. It delivers control of every device accessing your network and cloud applications all in one interface. Administrators can conduct a detailed security review of any device and monitor specific devices that are accessing applications and at what time. A holistic dashboard illustrates risks, device activities, and current vulnerabilities across the enterprise.
In-Depth Compliance & Control
OPSWAT goes beyond standard security checks such as OS and anti-virus, offering an in-depth examination of devices. This includes risk and vulnerability evaluation, with the ability to detect and fingerprint over 5,000 third-party applications. Other checks include encryption, removable media, anti-keylogger, screen capture protection, unwanted applications, and Multiscanning to detect active and passive malware.
Up-to-Date Vulnerability and Patch Management
OPSWAT detects all known threats in the Common Vulnerability and Exposures (CVE) library. Combined with MetaDefender® IT-OT Access’ proprietary scoring system developed from protecting over 100 million endpoints, OPSWAT optimizes prioritization and patch management.
Automatic & Self-Remediation
OPSWAT offers self-remediation options out-of-the box, minimizing costly help desk calls. To maximize productivity, some remediation options can simply be automated. This includes updating the virus definitions on local anti-malware software, activating firewall software, and removing unwanted applications.
High BYOD Adoption
BYOD users often avoid access security software because it is traditionally cumbersome and slows productivity. OPSWAT provides a lightweight and easily uninstalled application that conducts a quick, yet comprehensive assessment.
Specialized Solutions
OPSWAT offers integrated solutions for specific environments, such as Virtual Desktop Infrastructure (VDI) and Salesforce to make it even easier for both IT personnel and the end user to have secure devices and access for these situations.
Who Benefits from Zero-Trust Access?
Zero-trust endpoint management supports the world's critical infrastructure through industries like:
Seamless Secure Access for All
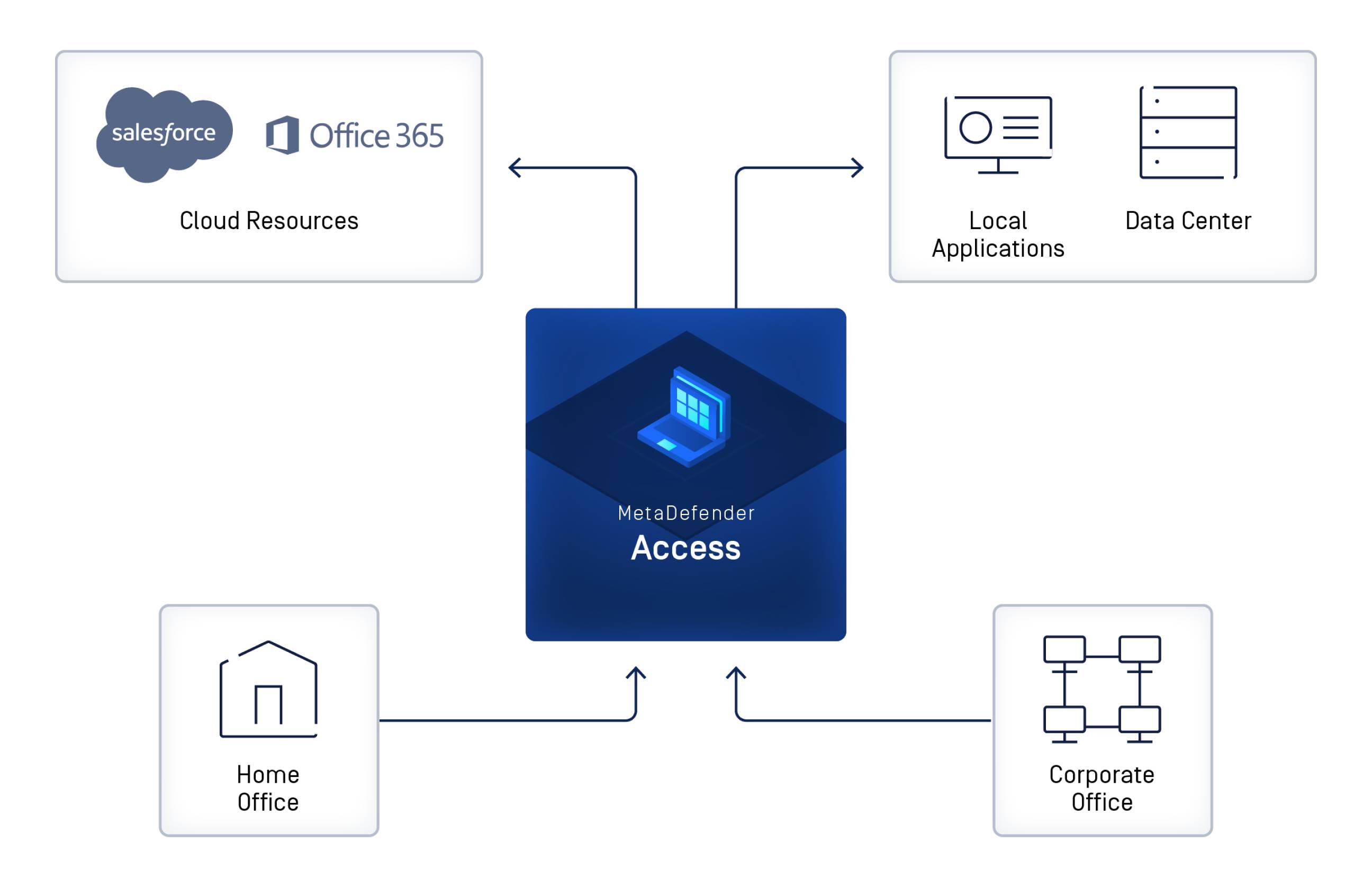
Designed with the zero-trust philosophy at its core, OPSWAT’s MetaDefender Access Solution addresses both secure access and device compliance in a single comprehensive platform. As depicted in the diagram below, MetaDefender Access performs seven in-depth security checks on various devices, including those of employees, BYOD, guest and IoT. Once the device is confirmed compliant, you can then ensure secure remote or on-premises access to only authorized network segments and applications. This platform not only addresses your security compliance but also reduces the amount of resources needed for implementation and maintenance. Moreover, it provides your users with a positive and seamless experience to access company applications and data.
MetaDefender Access Platform

On-Premises Access
Network Access Control (NAC) allows you to maintain the same level of visibility, security and control over all devices on your network, including users’ devices in the office. NAC applies Authentication, Authorization, and Accounting (AAA) to your network to ensure that only authorized users and devices can connect. In addition to enabling pre-connection authentication checks via 802.1x, NAC also collects information about devices after they have connected. This allows it to classify and monitor them, and dynamically assign them to the proper network segment, depending on attributes such as fingerprinted device type, logged in user, and whether device posture checks follow your organizations security policies.

Remote Access
It's time for organizations to rethink the way users access valuable applications and data. OPSWAT replaces your traditional VPNs with a solution that prioritizes security and compliance verification before granting connections to applications and data resources. This zero-trust access solution encrypts communications between user devices and applications. It integrates with your existing identity access management solution, simplifying management and facilitating multi-factor authentication seamlessly.

Cloud Access
OPSWAT integrates with SAML, a protocol for cloud access, to provide comprehensive control over devices accessing the cloud. This feature ensures that each user undergoes authentication and compliance checks. If a user is found to be non-compliant, access to the cloud application is denied. Instead, the user is directed to a self-remediation page to address any issues. Once the issues are addressed, the user is granted access again.
Secure Virtual Desktop Access
Securing access to applications from devices via Virtual Desktop Infrastructure (VDI) is critical, especially with BYODs. Modern VDI clients allow many interactions with the underlying endpoint, making it essential to prevent actions like screen captures or key logging. To ensure the endpoint is secure and compliant before using a VDI client, OPSWAT integrates with VDI solutions from vendors such as Omnissa.
OPSWAT Cloud Security for Salesforce
Considering the significant reliance many companies have on Salesforce, which stores valuable data across various business aspects, it is crucial to secure access and ensure compliance before users connect. OPSWAT offers an integration with Salesforce to ensure any devices posing a risk are denied access until they undergo self-remediation.
Safeguard Against Vulnerable Devices
Every additional device connected to your network or cloud applications introduces potential vulnerabilities. Risks can arise from stolen devices, lack of password protection, outdated security software, misuse of encryption, as well as exposure to keyloggers or screen capture. OPSWAT provides comprehensive device inspection, so that you can be confident that only trusted devices can access your environment.
Meet Compliance Requirements
Regulatory compliance requirements are enforced to minimize the risk of breaches and privacy violations. Achieving compliance can be time-consuming and costly if requirements are not met. OPSWAT technologies provide extensive visibility and detailed reporting capabilities, helping to meet requirements for standards such as PCI DSS, HIPPA, FINRA, HITECH, NIST, ISO, FTC, COBIT, Sarbanes-Oxley, CIS, and SANS.
MetaDefender Access Enables Compliance and Secure Access
It’s critical to implement robust security measures for users accessing your network, data, and applications, from home or the office. MetaDefender Access is a platform designed to provide just that. It offers industry-leading compliance, security and vulnerability checks, a zero-trust VPN alternative, and on-premises network access control. This ensures secure access regardless of your location, home, office, or remote sites, and whether your data and applications are hosted - on-premises or in the cloud.