OPSWAT is proud to announce that Gears clients are now available for AndroidTM and Linux operating systems! These new clients feature a streamlined registration process and IP reputation scanning options, and position Gears to provide enterprise-wide device visibility to organizations securing an increasingly mobile workforce. Read on for more information on the new clients, and a few other improvements we made along the way!
Code Name: Michigan
- Overview
- Download the New Clients
- Gears for Linux and Android -- OS Feature Comparison
- Feature Spotlight: Rooted device detection for Android
- Feature Spotlight: Revocable registration codes
- Feature Spotlight: Malware scanning on Linux
- Feature Spotlight: IP reputation scanning
- Mobile app scanning coming soon!
Overview
Gears is used around the world to monitor and manage the security state of Windows and Mac devices, no matter where they are or how they connect or which software they have installed. Gears is the single pane of glass that allows IT security professionals to unify their endpoint posture policies and seamlessly integrate into secure access solutions for enforcement. This release marks a huge step forward as we are adding support for Linux and Android devices with the same ease of use and unique features that our Gears customers love, in addition to some new unique features as well.
Gears for Android is not an MDM. It is an app freely available in the Google Play Store, requires no administrative rights on the phone, and no complicated MDM provisioning. Any Android user can download and install the app. Scanning is done on-demand when the app is opened and only takes a few seconds. By inputting your Gear's account registration code, their report results will automatically be sent to Gears servers and associated with your account, providing you with MDM-like visibility without the cost or complex deployment. This is ideal for true BYOD scenarios, ad-hoc security assessments, NAC integrations and more.
Gears for Linux is a lightweight service that runs in the background, easily installs via Yum or Apt-get, and supports auto-update for CentOS/RHEL and Ubuntu. This initial release is command-line only and will work equally well on workstations, laptops and servers -- on-premises, remote or cloud. An open source version is in progress and will be available soon as well.
Download the New Clients
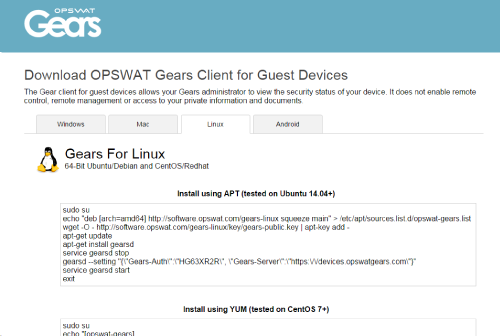
The guest device download page for Gears has been redesigned and now includes tabs for Android and Linux. The link to the download page hasn't changed so you don't have to change your existing integrations.
Click to Enlarge
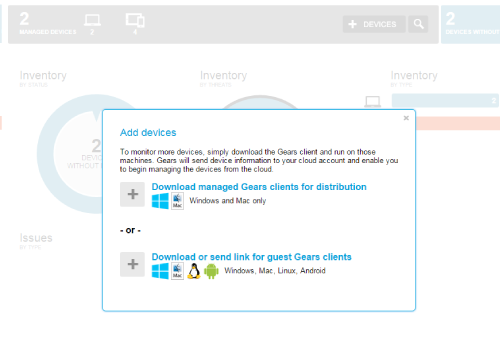
The Add Devices window has been updated with icons representing the supported operating systems.
Click to Enlarge
The guest device download page has been redesigned for easier use. It auto-detects the operating system of the client and displays the appropriate tab. For auto-configured agents like Windows and Mac the download and install is unchanged. The Linux client installation requires the user to copy and paste several lines of commands. These commands are automatically customized so the Linux device will report to your account. The instructions for Android are just as easy and will be improved even more in the next few weeks with one-click onboarding.
Gears for Linux and Android -- Feature Comparison
Now that clients are available for four different operating system families, we thought it might be helpful to provide a side-by-side comparison of the features available for each OS. This chart does not cover the Gears management console features, only the client-related features. Take a look at the table below, and let me know if there are features you would like to see added to the roadmap for the OS of your choice!
| Android | Linux | Windows | Mac OS X | |
| General Features | ||||
| Register to Gears Cloud | Via registration code | Via license key | ||
| Managed Devices | Roadmap | Yes | ||
| Guest Devices | Yes* | Yes* | Yes | |
| Persistent Agent | Roadmap | Yes | Yes | |
| Dissolvable/On-Demand Agent | Yes | Roadmap | Yes | |
| Supported OS | Android 4.4+ | Various | Windows XP-10, Server 2003-2012 | OS X 10.8+ |
| Supported Platforms | Phone, Tablet | Desktop, Laptop, Server, VM | ||
| Attended Installation | Via Google Play store | Yes | Yes | Yes |
| Remote/Auto Installation | No | Yes | Yes | Yes |
| Auto Update | Yes | Yes 1 | Yes (Optional) | |
| Tamper Resistence | Native | Limited | Yes | Yes |
| GUI | User and Pro Mode | Roadmap | Yes (Optional) | Yes (Optional) |
| CLI | n/a | Yes | Yes | Yes |
| GUI Rebranding/Customization | By Request | Roadmap | By Customer | By Customer |
| SDK Available | Yes | Yes | Yes | Yes |
| Detailed Features | ||||
| Infections: 40+ Engine Malware Scan | Roadmap | Report & Enforce | Report & Enforce | Report & Enforce |
| Infections: Repeated Threats | No | Roadmap | Report & Enforce | Report & Enforce |
| Infections: IP Reputation Scan | Report & Enforce | Report & Enforce | Roadmap | Roadmap |
| Detect Current User | n/a | Report Only | Report Only | Report Only |
| Detect Hostname | Yes | Report Only | Report Only | Report Only |
| Detect Network Adapters | Roadmap | Report Only | Report Only | Report Only |
| Detect MAC Address & IPs | Report Only | Report Only | Report Only | Report Only |
| Detect System Language | Report Only | Report Only | Report Only | Report Only |
| Detect System Architecture | Roadmap | Report Only | Report Only | Roadmap |
| Detect Kernel Version | Roadmap | Report Only | Roadmap | Roadmap |
| Detect Installed Software/Apps/Packages | Report Only | Report Only | Report Only | Report Only |
| Detect PUAs & Risky Software | Roadmap | Roadmap | Report & Enforce | Report & Enforce 4 |
| Detect Running Processes | Roadmap | Report Only | Roadmap | Roadmap |
| Remote (silent) application removal | n/a | Roadmap | Yes | Roadmap |
| 4-Step Lost & Found Check | Report Only 2 | n/a | n/a | n/a |
| Security Score | Report Only 2 | Roadmap | Report Only 2 | Report Only 2 |
| Device Health Score | Report Only 2 | Roadmap | Roadmap | Roadmap |
| Detect Ad Tracking Status | Report Only 2 | n/a | n/a | n/a |
| Detect Rooted Status | Report & Enforce | n/a | n/a | n/a |
| Report Disk Encryption Software | n/a | n/a | Report & Enforce | Report & Enforce |
| Report Disk Encryption State | Report & Enforce | Report & Enforce | Report & Enforce 3 | Report & Enforce |
| OS Version | Report & Enforce | Report Only | Roadmap | Roadmap |
| Antivirus Installed | Roadmap | Report & Enforce | Yes | Yes |
| AV Definition Age | Roadmap | Report & Enforce | Yes | Yes |
| Personal Firewall | Roadmap | Report & Enforce | Yes | Yes |
| Screenlock & Passcode | Report & Enforce | Roadmap | Yes | Yes |
| Detect Antiphishing Software | n/a | Roadmap | Report & Enforce | Report & Enforce |
| Detect AV Real-Time Protection State | Roadmap | Roadmap | Report & Enforce | Report & Enforce |
| Detect AV Last System Scan Time | Roadmap | Roadmap | Report & Enforce | Report & Enforce |
| Detect AV Detected Threat History | Roadmap | Roadmap | Report & Enforce | Report & Enforce |
| Detect Backup Software | Roadmap | Roadmap | Report & Enforce | Report & Enforce |
| Detect Backup State | Roadmap | Roadmap | Report & Enforce | Report & Enforce |
| Remediate personal firewall | n/a | Roadmap | Yes | Yes |
| Detect patch management software | n/a | Roadmap | Report & Enforce | Report & Enforce |
| Detect patch management agent state | n/a | Roadmap | Report & Enforce | Report & Enforce |
| Detect missing OS patches and service packs | Roadmap | Roadmap | Report & Enforce | Report & Enforce |
| Detect OS auto update state | n/a | Roadmap | Report & Enforce | Report & Enforce |
| Detect lock screen timeout | Roadmap | Roadmap | Report & Enforce | Report & Enforce |
| Detect available disk space | Report Only 2 | Roadmap | Report & Enforce | Report & Enforce |
| Detect battery charge and state | Report Only 2 | n/a | n/a | n/a |
| Detect location services state | Report Only 2 | n/a | n/a | n/a |
| Detect total and available RAM | Report Only 2 | Roadmap | Roadmap | Roadmap |
| Detect reboot recency | Report Only 2 | Roadmap | Roadmap | Roadmap |
| Detect hardware performance level | Report Only 2 | Roadmap | Roadmap | Roadmap |
Survey/questionnaire integration | No | No | Yes | Yes |
| Adjustable reporting interval | On-Demand | Yes | Yes | Yes |
| Integration | ||||
| NAC for SaaS: Browser Cookie | No | No | Yes | Roadmap |
| NAC for SaaS: Client Certificate | Roadmap | Roadmap | Yes | Yes |
| Local | No | No | Via Registry | Via P-List |
| REST API | Yes | Yes | Yes | Yes |
| Privacy / Personal Information Controls | Yes | Yes | Yes | Yes |
| Auto-trigger remediation page | No | Roadmap | Yes | Yes |
| Pre-tag/group devices | No | Roadmap | Managed Only | Managed Only |
| Restrict app uninstallation | No | Roadmap | Roadmap | Roadmap |
- Auto update supported on CentOS 7+ and Ubuntu 14+
- Data reported in client GUI, not in the Gears console yet
- Windows includes optional encryption algorithm and key length check
- Mac supports public file sharing and toolbar categories only
- Yes: Supported now
- No: Not supported, not planned
- n/a: Not available or not relevant
- Report Only: Data is collected by the endpoint and reported to Gears servers
- Report and Enforce: Same as report only, plus the ability to create Gears policies on that data
- Roadmap: Feature is planned
Feature Spotlight: Rooted Device Status for Android
Most of the biggest threats with mobile devices come from those that are rooted. Rooted devices are a threat to secure networks because they have disabled built-in security measures in order to utilize blocklisted or unsafe applications and alter the operating system, causing both the device and the connected network to become more vulnerable to malware infections. Rooted devices allow for applications to affect each other, as well as the operating system in uncontrolled ways. Administrators should be highly suspicious and concerned with rooted devices lingering within their network. This reporting feature is now available via Gears for Android.

Feature Spotlight: Storage Encryption Detection for Android and Linux
Storage encryption is available by default on many mobile devices as well as most Linux distros, and is an important part of many organization's security policies. Without storage encryption, the risk of leaking PII increases exponentially as more and more employees handle more information -- a single device theft or loss can be catastrophic. Gears has been a leader in disk encryption monitoring and enforcement for Windows and Mac, and now extends the same functionality to Linux and Android. You can now monitor and create policies to check the actual encryption state of Android internal storage and Linux /home and /root mount points. With these encryption options being free and built-in to the operating system you can benefit greatly simply by monitoring and enforcing its usage. Try it out on a few Android and Linux devices and let me know what you think.
Revocable Registration Codes
Adding devices to your Gears account has always been easy. The installers and executables are pre-configured to automatically connect to your Gears account. Traditionally this association is done using your Gears license key. The situation is more complex with mobile devices so we had to rethink this process -- it would be unreasonable to ask a user to type in a long license key using a mobile keyboard. So we created a revocable registration code, only 8 characters long, that is easier to share and type, without worrying about distributing your license key to the masses.
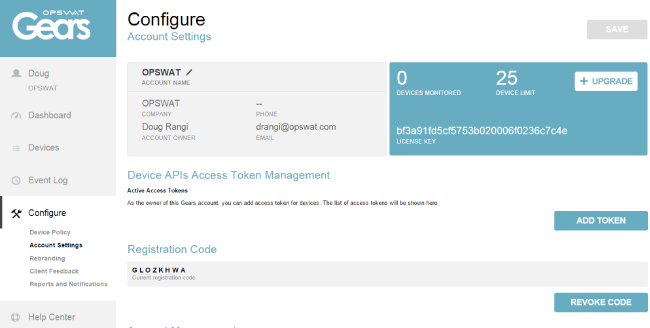
Initially, this new registration code is used for on-boarding Linux and Android devices. It will eventually be used for Windows and Mac as well. You can find your registration code on the Android and Linux tabs of the guest device download page, as well as in your account settings in the Gears console.
Click to Enlarge
Should you ever wish to reset your registration code for security reasons or convenience you can do so quite simply from the Gears account settings. Having this capability will help administrators maintain control over what devices are reporting to their account.
Metascan-powered Malware Scanning for Linux
In a recent survey we performed we found that the vast majority of Linux users do not have an antivirus product installed, and among those who did very few used real time protection or file system monitoring. The most common response from survey participants was that they run a free antivirus program occasionally, usually weekly, to perform a system scan. Many of the responses also included that they would feel better about their security if they were able to perform a quick system scan using the 40+ anti-malware engines provided by Metascan Online. Gears for Linux now makes this possible!
Once installed, the Gears for Linux daemon will perform a daily malware scan of all running processes and their linked libraries. This is the same feature we already provide for Windows and Mac devices and is responsible for detecting countless infections and potentially unwanted applications like keyloggers and rogue antivirus products. We're really excited to offer this feature to all of our Gears users immediately.
IP Reputation Scanning for Linux and Android
Not all malware and riskware can be caught with traditional antivirus products. Gears utilizes Metascan Online for malware scanning with over 40 commercial antivirus and anti-malware engines. To further increase detection rates we are introducing IP reputation scanning, also powered by Metascan Online.
Initially available for Linux and Android, Gears will analyze the reputations of all connected IP addresses using 12 large IP reputation databases in order to detect any blocklisted IP addresses. Connections to suspicious IP addresses can be an indicator of potential malicious intent, including data theft and unwanted tracking.
The IP reputation service provided by Metascan Online will classify the type of bad IP that was seen according to how it was detected -- including botnets, malware, phishing, spammers and more.
As with any multi-scanning technology, we have to be careful about false positives. For IP reputation scanning we mitigate false positives in three ways:
- We use only high quality IP reputation sources, focusing on accuracy over quantity
- IP addresses are cycled-out if not seen by the scanning sources after a period of time
- Suspicious IPs are assigned a confidence rating that combines four different weighting factors
The Android app even includes a map showing where all of the active IP connections are located! Get it from Google Play today for free.
Metascan-powered Mobile App Scanning Coming Soon!
There are millions of apps available for Android devices. Sorting through them all to find the 'good ones' while avoiding knock-offs and malware is becoming increasingly difficult. It is hard enough to stay safe if you only download apps from Google Play; if you download apps from untrusted or third-party sources your risk of infection increases dramatically.
A multi-scanning solution like Metascan Online is one of the most effective ways to detect malware and riskware. Currently provided by Gears for Windows, Mac and Linux we are excited to soon introduce the same powerful scanning and detection functionality to Android as well. Once available Gears for Android will scan all installed apps and classify any detected malware, adware, riskware and more. No single mobile antivirus solution can compare to the power and efficacy of 40+ engines running in parallel. Stay current with our OPSWAT Gears Roadmap to find out when we will be rolling out this important feature.

