Healthcare data, including electronic health records (EHRs), financial information, and social security numbers, are a goldmine for cybercriminals. The ever-increasing reliance on digital data storage and transmission necessitates robust security measures to protect patient privacy and institutional integrity.
The Aftermath of Data Breaches in Healthcare Industry
In 2023, the healthcare sector experienced the highest average data breach costs of all industries, increasing from USD 10.10 million in 2022 to USD 10.93 million. From March 2023 until March 2024, the protected health information of 2,971,249 individuals was exposed or impermissibly disclosed.
The recent attack on Norton Healthcare in Kentucky exemplifies the devastating impact of data breaches. The attackers claimed to have gained access to network storage devices and stolen 4.7TB of data from the compromised systems. The ALPHV (BlackCat) ransomware group claimed responsibility for this attack in late May 2023. To substantiate their claims, the ransomware group posted dozens of files on their dark web leak site, including sensitive information such as Social Security numbers and bank statements of some Norton Healthcare patients.
Understanding the Challenges
Several factors contribute to the complexity of safeguarding storage data:
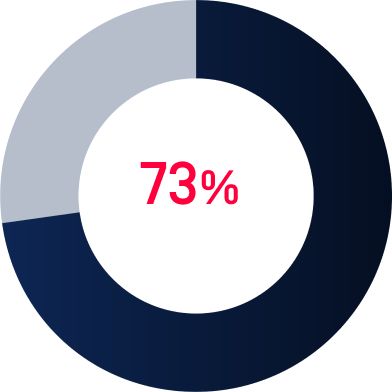
Legacy Systems
Nearly three-quarters (73%) of healthcare providers rely on outdated IT infrastructure, which presents vulnerabilities that cybercriminals can exploit. Patching and updating these systems can be complex due to legacy integrations and compatibility concerns.
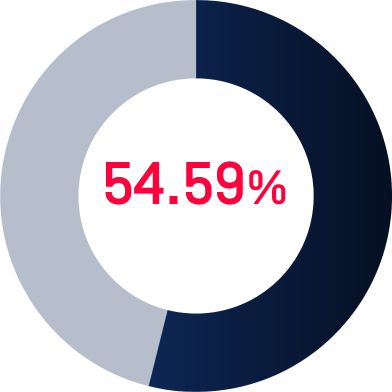
Evolving Threats
Cybercriminals are constantly refining their tactics, making it difficult for healthcare providers to stay ahead of the curve. A staggering 54.59% of healthcare organizations have experienced a significant security incident in the past year alone.

Third-Party Access
The growing trend of outsourcing data storage and processing to third-party vendors introduces additional points of vulnerability. In 2023, 35% of breaches affecting healthcare organizations originated from third-party vendors, highlighting the importance of robust security practices across the entire data ecosystem.
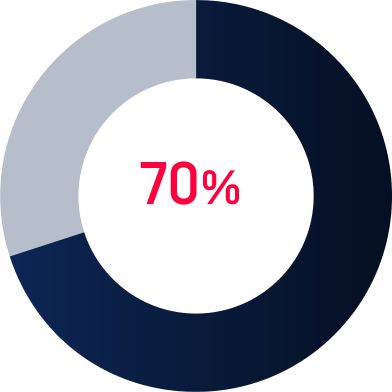
Insider Threats
Accidental data leaks from staff unaware of phishing attempts or proper data handling protocols remain a significant concern. In 2024, 70% of healthcare breaches have been caused by internal actors.
Best Practices to Protect Storage Data from File-Borne Ransomware
To combat these challenges, healthcare organizations must adopt best practices for data protection, especially against file-borne ransomware and compliance violations:
Automated File Scanning
All files should be scanned for malware. This includes on-access scans for real-time protection, periodic scheduled scans, and on-demand scans for specific files. It’s highly recommended to scan files with multiple anti-malware engines to get the highest detection rate and the shortest window of exposure to malware outbreaks.
Sensitive Data Protection
The privacy of confidential business information is essential. Sensitive and out-of-policy data in files must be removed, redacted, or watermarked before entering or leaving your network.
File Sanitization
Files such as DICOMs, Microsoft Office documents, PDFs, and image files can have embedded threats in hidden scripts and macros. To make sure that files contain no hidden threats, it is necessary to recursively sanitize files by removing any potentially malicious embedded objects before they can be exploited by attackers.
Adaptive Threat Analysis
Advanced malware can evade traditional security solutions or bypass anti-analysis tricks. Utilize next-gen sandboxing solutions that can analyze suspicious files at every layer of obfuscation to identify the Indicators of Compromise (IOC). A combination of both static and dynamic analysis is recommended to detect these evasive and sophisticated threats.
File Remediation
Establish automated remediation workflows that can take predefined actions upon detecting threats. This ensures a swift and consistent response to security incidents, minimizing potential damage.
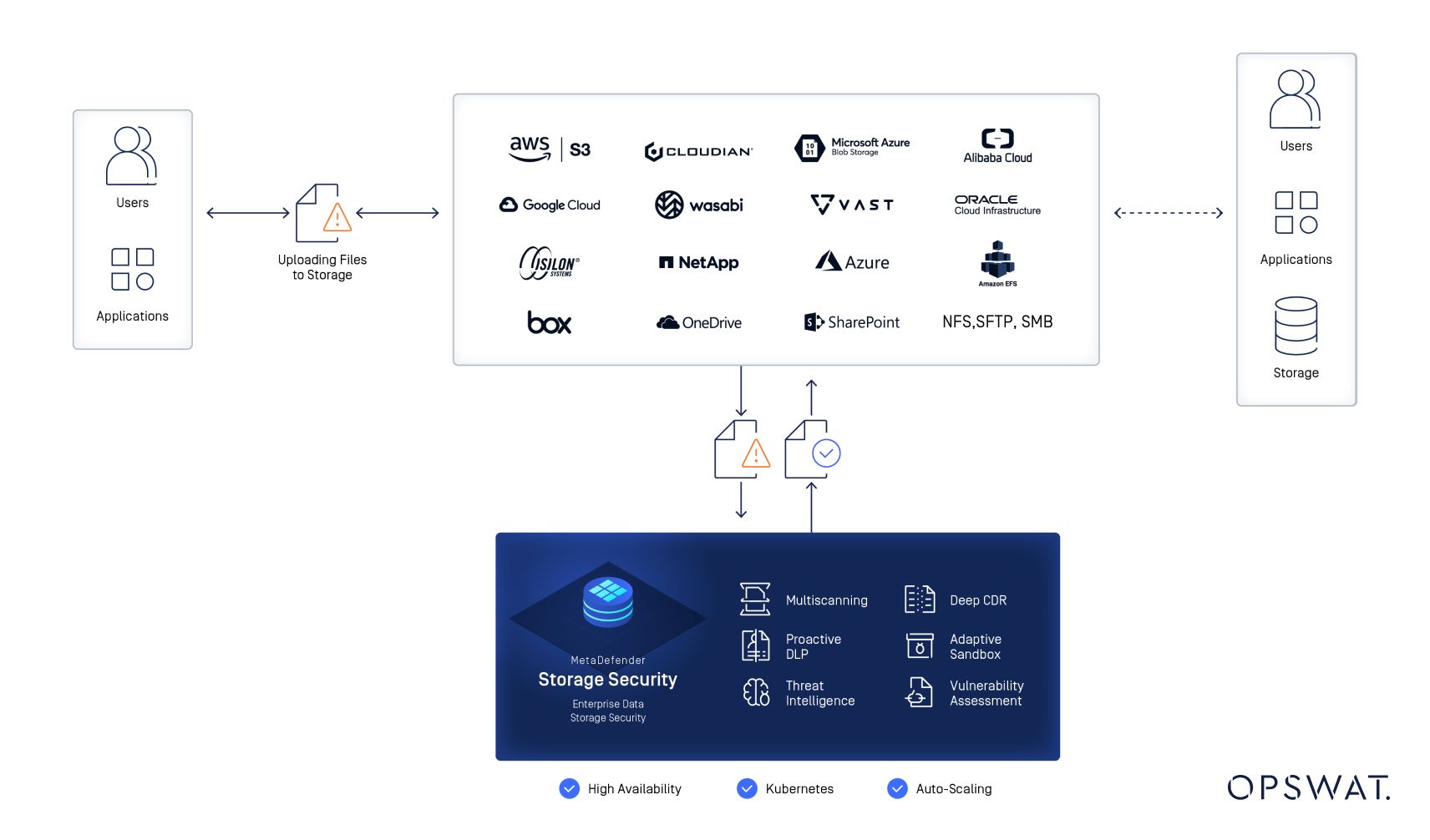
Guard Your Data with MetaDefender Storage Security
MetaDefender Storage Security is a multi-layered solution that delivers real-time threat detection and prevention that can proactively safeguard your data. It seamlessly integrates into existing workflows, offering real-time and on-demand scans across diverse storage types (cloud, on-premises) without disrupting data access.
Our solution leverage multiple advanced technologies such as Multiscanning, Deep CDR, and Proactive DLP to guard against zero-day threats and sophisticated malware and help organizations meet healthcare regulations like PCI and HIPAA.
Conclusion
Cyberthreats in the healthcare industry are constantly evolving. OPSWAT MetaDefender Storage Security proactively fortifies data security measures, enabling healthcare providers to build a robust defense against evolving cyberthreats and ensure the continued privacy and security of their patients' sensitive information. Investing in data security is not just a financial decision; it's a commitment to patient trust and the integrity of the healthcare ecosystem.
Learn more about how to protect your organization:


