The tipping point came as threat groups like Scattered Spider began actively targeting the insurance sector. Known for blending social engineering with advanced file-based intrusions, these actors exploited everyday workflows to infiltrate systems and steal credentials. Several high-profile breaches across the industry served as a wake-up call: secure file transfer alone wasn’t enough. The company needed a solution that could inspect, sanitize, and control every file entering its environment before any damage occurred.
The Risks Behind Routine File Transfers
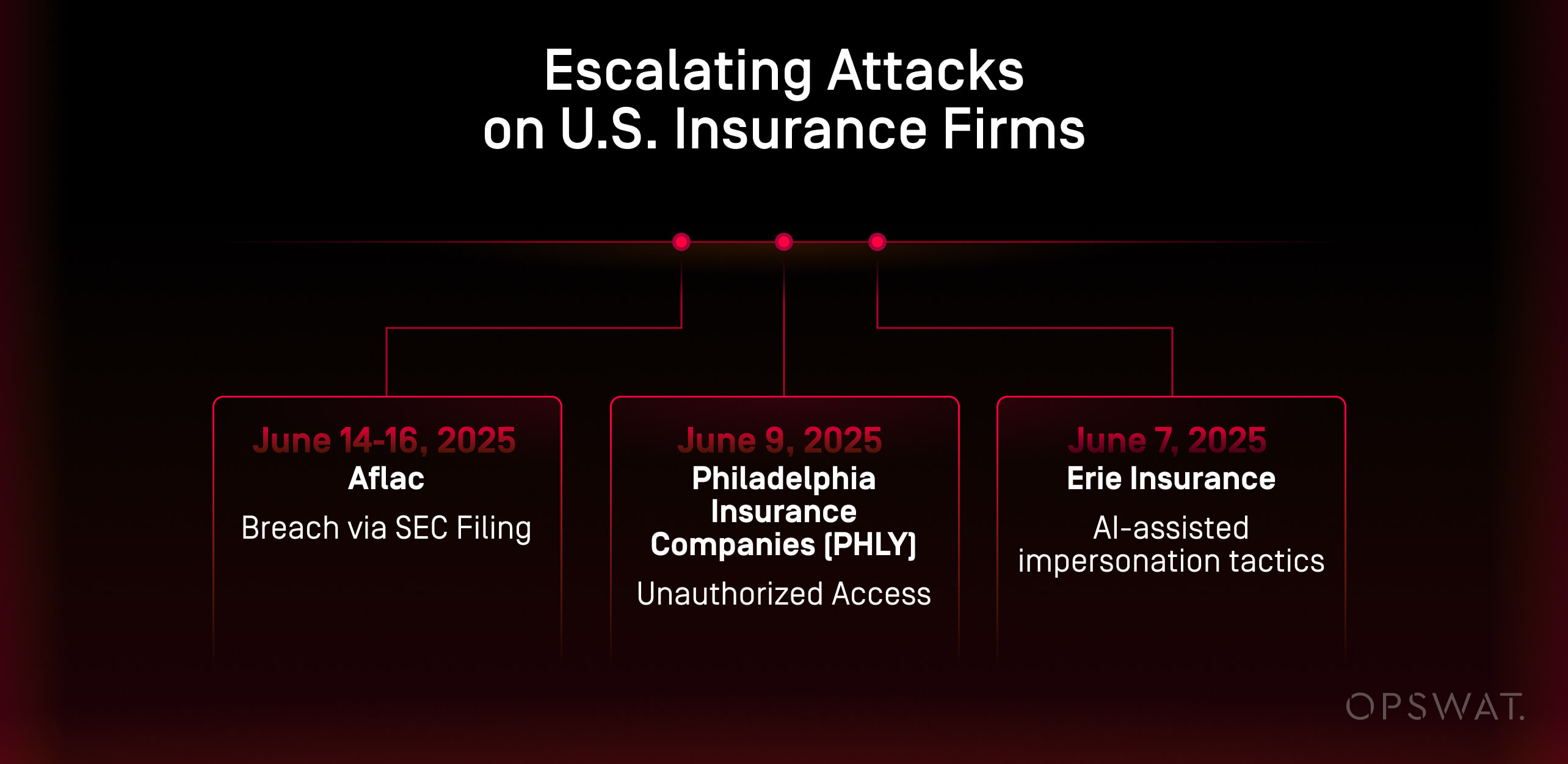
Multiple cyberattacks in the US have been identified as having all the hallmarks of Scattered Spider activity, prompting warnings that the insurance industry should be on high alert. In June 2025 alone, multiple U.S. insurance firms—including Aflac, Erie Insurance, and Philadelphia Insurance Companies—disclosed breaches tied to sophisticated social engineering and file-based tactics linked to Scattered Spider, as reported by CNN. These incidents resulted in unauthorized access, IT outages, and potential exposure of Social Security numbers, health data, and insurance claims.
June 7, 2025
Incident: Erie Insurance
- Attack Type: Unusual network activity → Business disruption
- Impact: IT system outage and operations impacted
- Details: Erie reported “unusual network activity,” triggered protective measures, later disclosed a breach via SEC filing.
- Attribution: Consistent with Scattered Spider tactics
June 9, 2025
Incident: Philadelphia Insurance Companies (PHLY)
- Attack Type: Unauthorized access → System disconnection
- Impact: Ongoing service outage and customer portal down
- Details: PHLY discovered unauthorized access and took systems offline to prevent spread.
- Attribution: Techniques align with Scattered Spider’s playbook
June 14–16, 2025
Incident: Aflac
- Attack Type: Social engineering breach → Data theft
- Impact: Potential exposure of SSNs, health info, and claims data
- Details: AI-assisted impersonation tactics used to infiltrate; intrusion contained within hours
- Attribution: Strong indicators of Scattered Spider involvement
This insurance company’s existing file transfer infrastructure was not designed to defend against today’s advanced, file-based threats. Even though end-to-end encryption was implemented into the file transfer flow, the system lacked deep, proactive inspection at the file level. This blind spot left the company vulnerable to AI-generated malware, polymorphic payloads, and weaponized documents, many of which can bypass traditional antivirus tools entirely.
Every day, the company exchanged files with hospitals, independent agents, legal partners, and third-party administrators. Many of these transfer processes occurred through unmanaged channels such as email attachments, SFTP folders, or ad hoc cloud-sharing tools. These fragmented workflows made it difficult to enforce consistent policies, log activity, or trace malicious content back to its source.
At the same time, rising regulatory pressure from frameworks like HIPAA and GLBA demanded full auditability and strong data protection measures for sensitive customer information. But with no centralized oversight and minimal threat inspection, routine file transfer workflows eventually became a liability. Worse, these channels offered an ideal delivery mechanism for attackers using AI to craft evasive payloads that looked safe on the surface.
In fact, the wave of attacks continued into July. Allianz Life, a major U.S. insurer, recently disclosed that threat actors exfiltrated personal data from a majority of its 1.4 million North American customers after breaching a third-party, cloud-based CRM system. The attackers reportedly used social engineering tactics to impersonate trusted entities, tricking their way into the environment without breaching Allianz’s core infrastructure.
This incident highlights how attackers are increasingly targeting the weakest links in distributed workflows—external systems, partner platforms, and human trust—making deep file inspection and strict policy enforcement essential across the insurance ecosystem.
4 Critical File Transfer Weaknesses
Threat detection gap
Lack of real-time file inspection allows hidden threats like AI-generated malware and zero-days to slip through undetected.
Uncontrolled transfer methods
Use of unmanaged protocols and platforms such as SFTP, SMB, and unapproved cloud storage platforms prevents consistent enforcement of security policies.
Lack of visibility
Insufficient audit trails and poor oversight into file movements make it difficult to track content or detect anomalies.
Non-compliant practices
Without centralized controls, file transfers often violate HIPAA, GLBA, and internal security requirements.
Traditional scanning tools, even when present, were loosely integrated and operated outside core workflows. They offered no guarantee of real-time detection or preventive protection. As a result, files were often assumed safe until proven otherwise, which is an increasingly dangerous assumption in a threat landscape shaped by automation, deception, and speed.
A Layered Defense Built for Novel File Threats
To reduce risk and regain control over its file transfer operations, the company deployed MetaDefender Managed File Transfer (MFT) with OPSWAT’s advanced threat prevention engine: MetaDefender Core. This combination gave the insurer a centralized, policy-driven platform that not only moved files securely but also actively inspected and sanitized their contents before delivery.
MetaDefender Managed File Transfer (MFT) replaced fragmented file transfer workflows, such as unmanaged SFTP, email attachments, and cloud-based file sharing, with a single, governed tool. MetaDefender Managed File Transfer (MFT) connects internal systems, partners, and remote users without relying on email attachments or unmanaged SFTP shares. Every file—regardless of source—was automatically scanned, sanitized, and logged before reaching its destination.
At the heart of the solution is OPSWAT’s multi-layered threat prevention stack of 4 Core technologies. These are reinforced by additional capabilities such as outbreak prevention, which automatically rescans previously approved files to detect zero-day threats.
4 Key Technologies

Adaptive Emulation
MetaDefender Aether™ emulates file behavior in a controlled environment to detect evasive, zero-day, and polymorphic malware.

Metascan™ Multiscanning
Analyzes each file with 30+ antivirus engines, improving detection beyond any single vendor.

Deep CDR™ Technology
Strips embedded code and rebuilds safe, functional versions of risky file types

File-Based Vulnerability Assessment
Identifies known CVEs embedded in file components before they can be exploited
Real-World Protection with Tangible Results
By deploying MetaDefender Managed File Transfer (MFT), the insurer closed a critical gap in its cybersecurity strategy: the uncontrolled movement of potentially dangerous files. The new platform gave security teams confidence that every file—whether incoming or outgoing—was fully inspected, sanitized, and traceable.
With policy-based controls and automated workflows in place, the organization streamlined how files moved between departments, partners, and customers. This reduced manual effort and eliminated the need for risky workarounds like unsecured SFTP or cloud-based sharing tools.
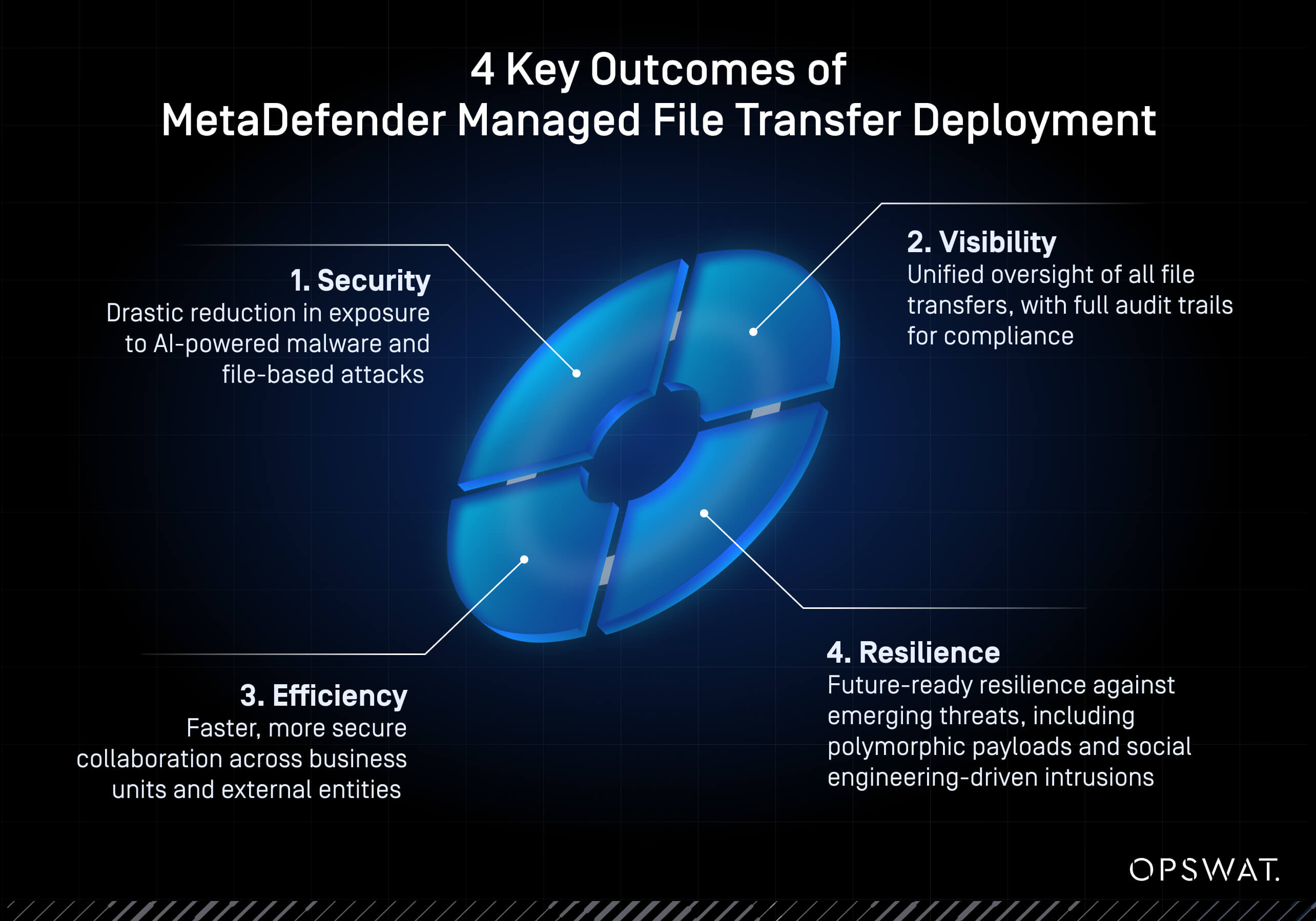
4 Key Outcomes
- Security: Drastic reduction in exposure to AI-powered malware and file-based attacks
- Visibility: Unified oversight of all file transfers, with full audit trails for compliance
- Efficiency: Faster, more secure collaboration across business units and external entities
- Resilience: Future-ready resilience against emerging threats, including polymorphic payloads and social engineering-driven intrusions
For a company under constant pressure to protect sensitive data, meet regulatory requirements, and maintain operational continuity, MetaDefender Managed File Transfer (MFT) offered more than just secure delivery: it delivered protection, visibility, and control.
Staying Ahead of the Threat Curve
As cyberthreats continue to evolve, fueled by AI, automation, and increasingly coordinated adversaries, the insurance company is now better positioned to adapt. With MetaDefender Managed File Transfer (MFT) as part of its long-term strategy, the company plans to expand policy-based controls across more business units, integrate deeper with cloud and regulatory reporting tools, and extend protections to additional data-sharing workflows. The goal is not just to stay ahead of threats, but to continuously harden the organization’s resilience against whatever comes next.
Turn Routine Transfers into Reliable Defenses
For this leading insurance provider, securing file transfers was only the beginning. By embedding multilayered threat prevention into the fabric of its operations, the company transformed routine file transfers into verifiable, compliant, and secure processes.
Learn how OPSWAT's leading MFT solution, MetaDefender Managed File Transfer (MFT), can help your organization safeguard critical data, reduce complexity, and prepare for the next generation of cyberthreats. Visit our product page and talk to an OPSWAT expert today.





