Email continues to be the central focal point for cyberattacks on organizations. OPSWAT, a company specializing in cyber protection for critical infrastructures, has developed a cybersecurity platform based on zero-trust technologies. Itay Glick, Vice President of Products at OPSWAT, explains how they defend organizational networks, industrial control levels, and cloud connectivity.
When examining cyberattacks over the last 20 years, a clear picture is revealed: email is the main digital channel used to attack organizations. The majority of cyberattacks stem from phishing attempts, often exploiting the fact that it is a highly accessible way into an organization. Targeting a specific individual is straight forward as you just need to know their email address, then it’s just a matter of deceiving them with well-hidden phishing links designed to steal critical login credentials.

“There are endless attack possibilities, many of which are not detected by antivirus software. Even antivirus engines based on machine learning have low accuracy. For cyber defense software developers, it’s a struggle to keep pace with over 100 million malicious programs released every year.”
"Attackers understand the challenges of maintaining effective email security and take full advantage of the situation," says Itay Glick, Vice President of Products at OPSWAT, specializing in cyber protection for critical infrastructures.
"Even when a virus is detected, threat actors quickly adapt, creating new variations by making minor code changes to generate a new, undetectable version. The antivirus engines operate based on known signatures, so a change in the code makes the specific signature irrelevant and the threat goes undetected.
In this way, infiltrating an organization becomes possible and email serves as a direct entry point to the endpoint, delivering the threat straight to a user's computer.”
An Advanced Email Security Solution
This situation greatly concerns the cybersecurity industry worldwide, and it is one of the reasons why OPSWAT is focusing on email security solutions in 2024. Despite the existing competition from leading email protection providers, OPSWAT holds a strategic advantage, with a 20-year successful track record of protecting critical infrastructures with innovative and award-winning technologies.
"Despite the developments of conventional email security providers, 77% of opened emails still bypass defense solutions," notes Glick. "Single or few antivirus engines cannot effectively detect ever-evolving phishing or malware attempts because either their detection rates are not high enough to be comprehensive or they lack a sensitivity to more novel attack methods."
So how does OPSWAT block such attacks?
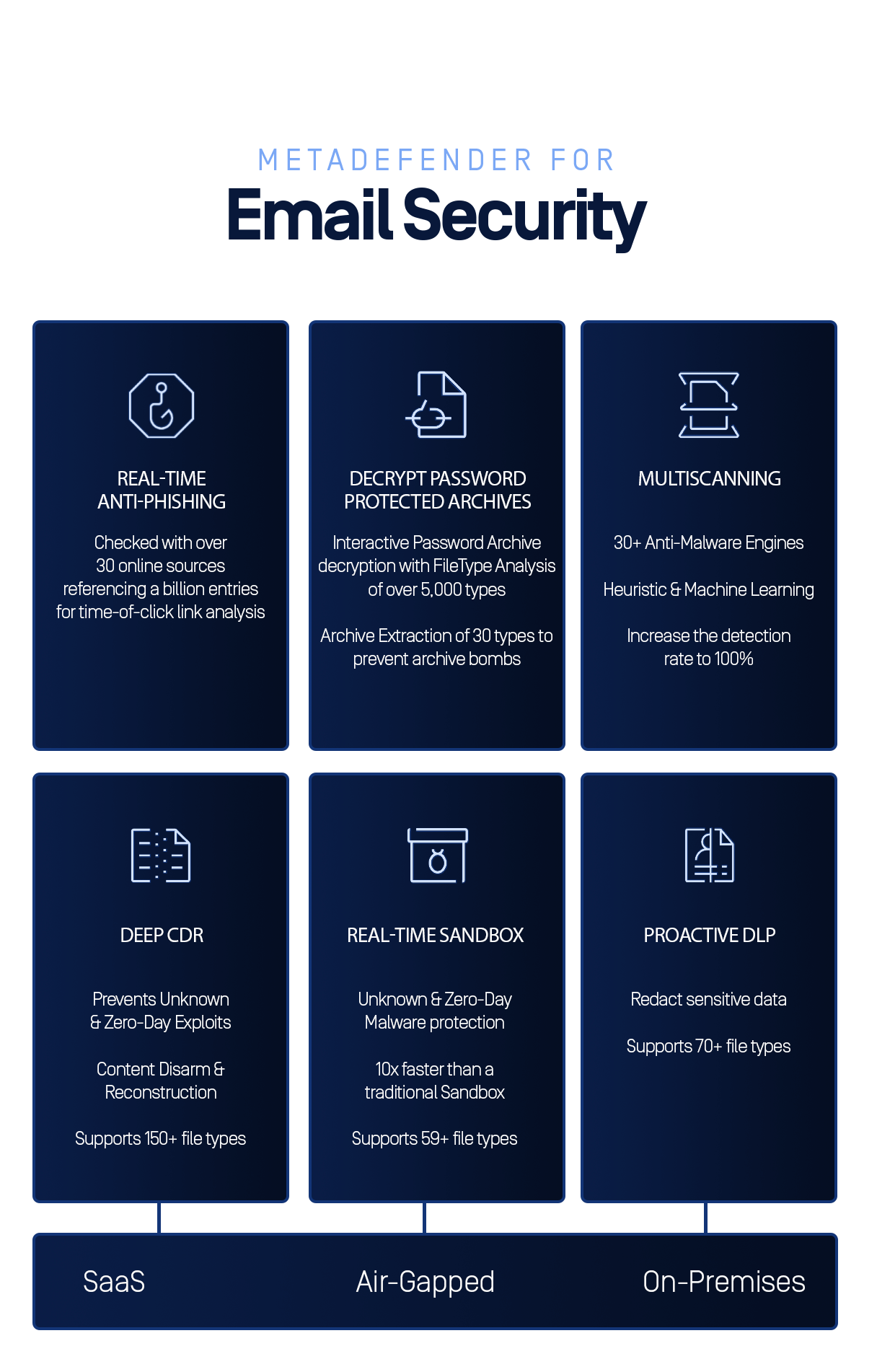
"We employ a zero-trust approach and conduct a detailed analysis of each email to detect the threat before it reaches its target. We developed a technology called, Deep CDR™ (Content Disarm and Reconstruction), which also blocks unknown email attacks. This is coupled with Multiscanning technology that uses over 30 anti-malware engines.”
Like other tools developed by the company, there are no equivalents in the industry. Many vendors develop security products, but the majority create one or two types. OPSWAT has a complete platform that can secure everything needed and meet the required compatibility through integration - a critical issue for organizations providing critical infrastructures.
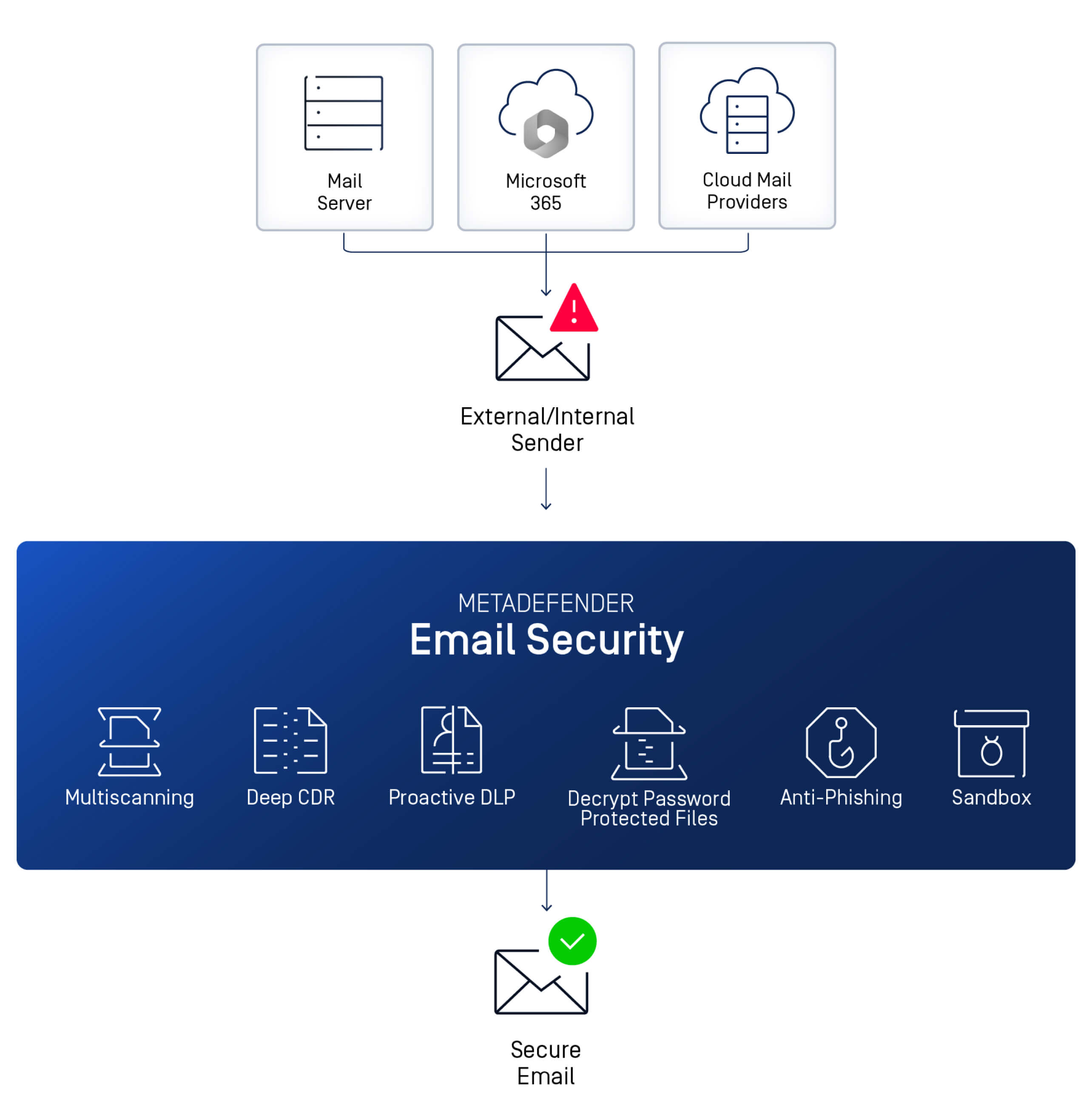
"Our system is deployed locally or in the cloud, scans incoming and outgoing emails for both internal or external environments, and performs several procedures on them: checking the URL, the sender's address, and real-time click verification if it’s a suspicious link.
Using various antivirus engines, each element in the email is examined, including the body of the text - an area less commonly suspected but still an area that can hide threats. If no threat is found, the system performs the Deep CDR process and concurrently the Real-Time Sandbox process, which runs the file and checks for anything suspicious, such as parameters of access to the disk or the network.
Everything is examined in the email message. Not just attached files and the body of the text, but over 150 different file types. Most users are not even aware that this many exist, or that they are even files. A meeting invitation, for example, is a type of file that also needs checking. These files are scanned quickly before reaching the user's inbox - they arrive only after being confirmed as sanitized."
Checking Every Email Attachment
OPSWAT was established in the United States in 2002, with the goal of creating a common language between different security solutions running on an end-user's workstation. The first cybersecurity solution they created was Multiscanning technology, which has remained an integral technology for all their products to this day. As part of its expansion, the company also established an Israeli branch, initially as a small office in Herzliya and now in a new and spacious office in Petah Tikvah.

Glick explains, the main feature of the new office is the cyber lab where you can see how OPSWAT cybersecurity solutions close security gaps for organizational networks, industrial control networks, IT Networks and to cloud connectivity, across all systems in its path.
The cyber lab is an interactive center dedicated to mapping the flow of data in operational technology (OT) and information technology (IT). The company states that it dedicates its technological solutions to modern cyber challenges.
"The lab demonstrates OPSWAT solutions, showcasing our unique ability to identify, analyze, and close security gaps against zero-day attacks, providing insights into specific responses to potential threats," explains Glick.
"The goal is to demonstrate our products in an interactive way that simulates a live attack scenario at all levels. This allows critical infrastructure organizations to easily view all our solutions in action via an integrated and user-friendly cyber defense platform. There are 16 categories defined as critical infrastructure, including transportation, banking, government institutions, and security agencies."
How common is the implementation of a zero-trust approach to cyber security today?
"The entire information security world is now moving towards a zero-trust model, and organizational norms are also adopting it, even for endpoints. Lately, this approach has been recognized by the email security world, and there is a growing understanding that every file that arrives should be checked and not trusted.
Every element in the email message, from the text body to attached files, needs to be thoroughly examined – going through a series of required processes – and only then, if everything is clean, is it passed on to the end user. Adopting a zero-trust approach can significantly enhance an organization’s security posture.
For example, encrypted files were traditionally not scanned. Nowadays, they too are not trusted but scanned. After this, it is reasonable to assume that emails leaving an organization are clean. But what if they contain unnecessary personal information? Or if the user accidentally sends a virus? So, even in this case, there is now a zero-trust approach.
Beyond the complexity of attacks, the variety of attacks are also increasing, and many of them can hide in different sophisticated forms to prevent detection by traditional security mechanisms. Lately, there have been many attacks using QR codes. If a user scans one with their phone, they could easily enter a phishing site. The user may be asked to enter their password which will then reach the attacker.
There are well-known malicious programs that can easily be identified and run on the endpoints, but there are also dormant programs. They sit on the endpoint without causing harm, perhaps collecting information, and cannot be detected through running processes. They hide themselves well and wait for the right moment to be activated.
For example, if attackers spread a high number of these threats within the organization, all set for activation on a specific date - they will not be identified until that date, and when it arrives, they will operate simultaneously and can disrupt the targeted organization."
Maximizing internal email security
Cyber challenges like these causes organizations to change their approach to security, each according to its perception of what is a more secure approach and solution. Many organizations transfer much of their activity to the cloud, where applications are protected by the provider's security.
85% of organizations currently use Microsoft 365 email security packages – E1/E3/E5. Other organizations opt for local protection, thinking that in this way they can protect against email-borne attacks better. "Organizations concerned by email security challenges, or by regulations requiring them to follow a specific conduct, tend to choose local email security," explains Glick.
"They want a separate network with comprehensive email security measures. This is the advantage of OPSWAT, as many of our anti-malware engines operate in the cloud and determine if the attached file in the email is malicious or not. Therefore, we built a solution that can function disconnected from the cloud and provide a set of options to create internal email security that includes all defense protocols, without compromises.
Even organizations that are more security-conscious can migrate email or move to Microsoft 365 in the cloud, and we can easily change the protection from local to cloud."
How do you address dormant malware that remains a threat in mailboxes?
"The ideal way to identify and neutralize such malware is to use Deep CDR solution. If, for example, the attack is embedded in a Word document, the solution creates a secure copy for opening the document without additional components. It only takes the text and images from the document and essentially rebuilds it from scratch.
In the second stage, the file enters the Adaptive Sandbox and is checked more deeply for malicious behavior according to the broadest range of malware types. When we compare our Sandbox capabilities to other players in the email security market, we see that we are the leaders.
OPSWAT currently has thousands of customers, most of them large corporations and institutions dealing with critical areas such as energy, security, and government."
Uncover Security Gaps with an Email Risk Assessment
It's vital to have a comprehensive view of your organization's existing email security posture by revealing phishing, malware or exploits that bypassed your defenses.
OPSWAT provides an actionable Email Risk Assessment designed to identify security gaps in your email security framework. Obtain valuable insights with cutting-edge email security technology that will:
- Find phishing attempts with Real-Time Anti-Phishing with a detection rate of 99.98%.
- Identify malware with Multiscanning, using over 30 anti-malware engines for a detection rate of 99.20%.
- Reveal unknown malware with a Real-Time Sandbox, 10X faster than a conventional sandbox.
- Detect file-based exploits using Deep CDR, which supports more than 150 file types.
By assessing your current email security measures against modern threats, you'll be empowered to take effective actions to strengthen your security posture.

