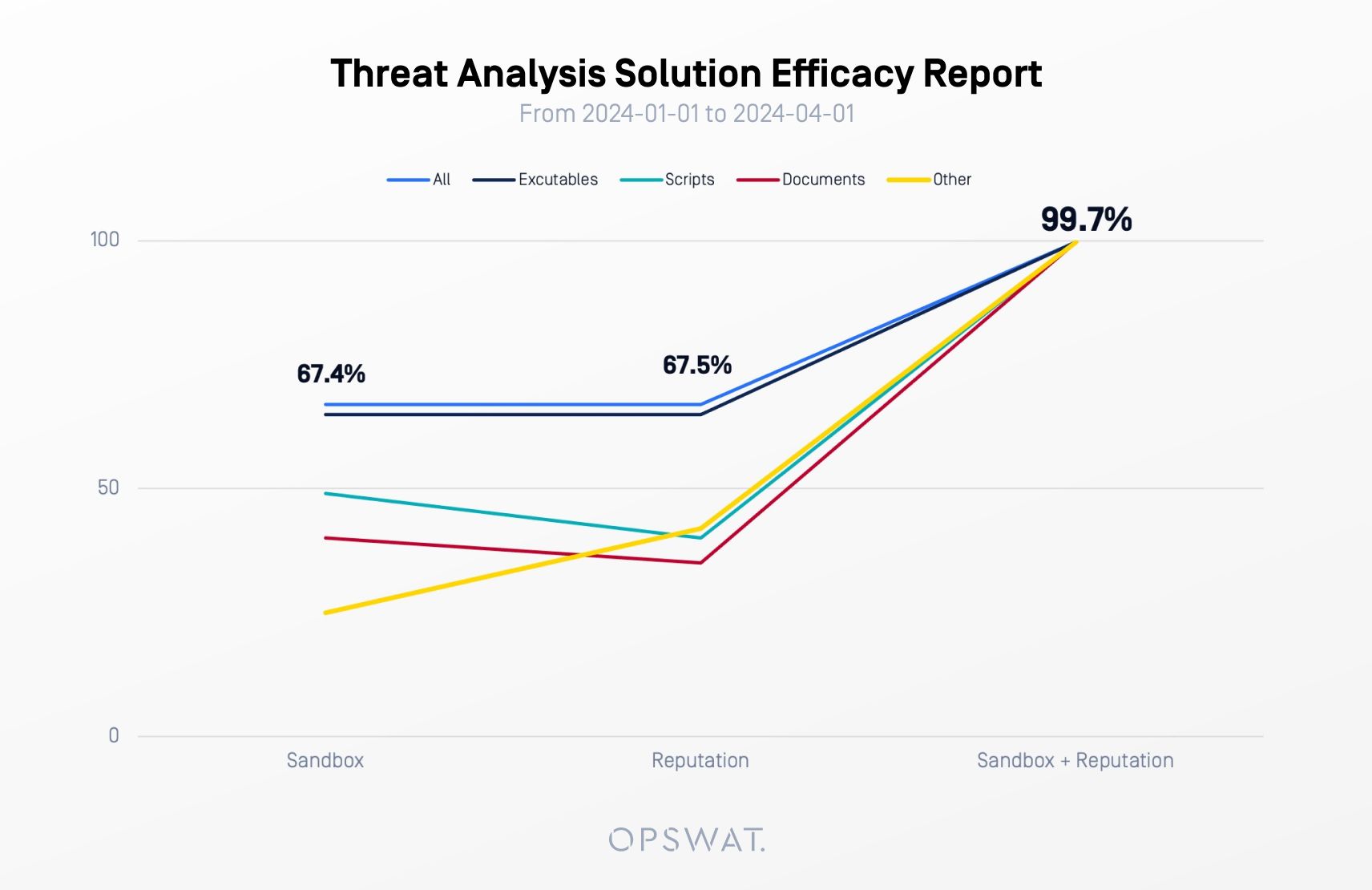
We're thrilled to introduce the latest milestone in cybersecurity resilience, MetaDefender Sandbox v2.0.0. This release brings with it not only an updated user interface, but powerful features that boost MetaDefender Sandbox’s efficacy rates to nearly 100% — up over 30% overall.
The new UX design of Filescan.io represents a significant step forward, blending aesthetic appeal with enhanced functionality. The new, more responsive UI centers around a user-first approach, along with a future-proof foundation for new features.
New Streamlined User Interface
1. Clean and fresh UI with a unified OPSWAT look and refreshed report design. The most interesting indicators can be filtered so users can focus on the most important information.
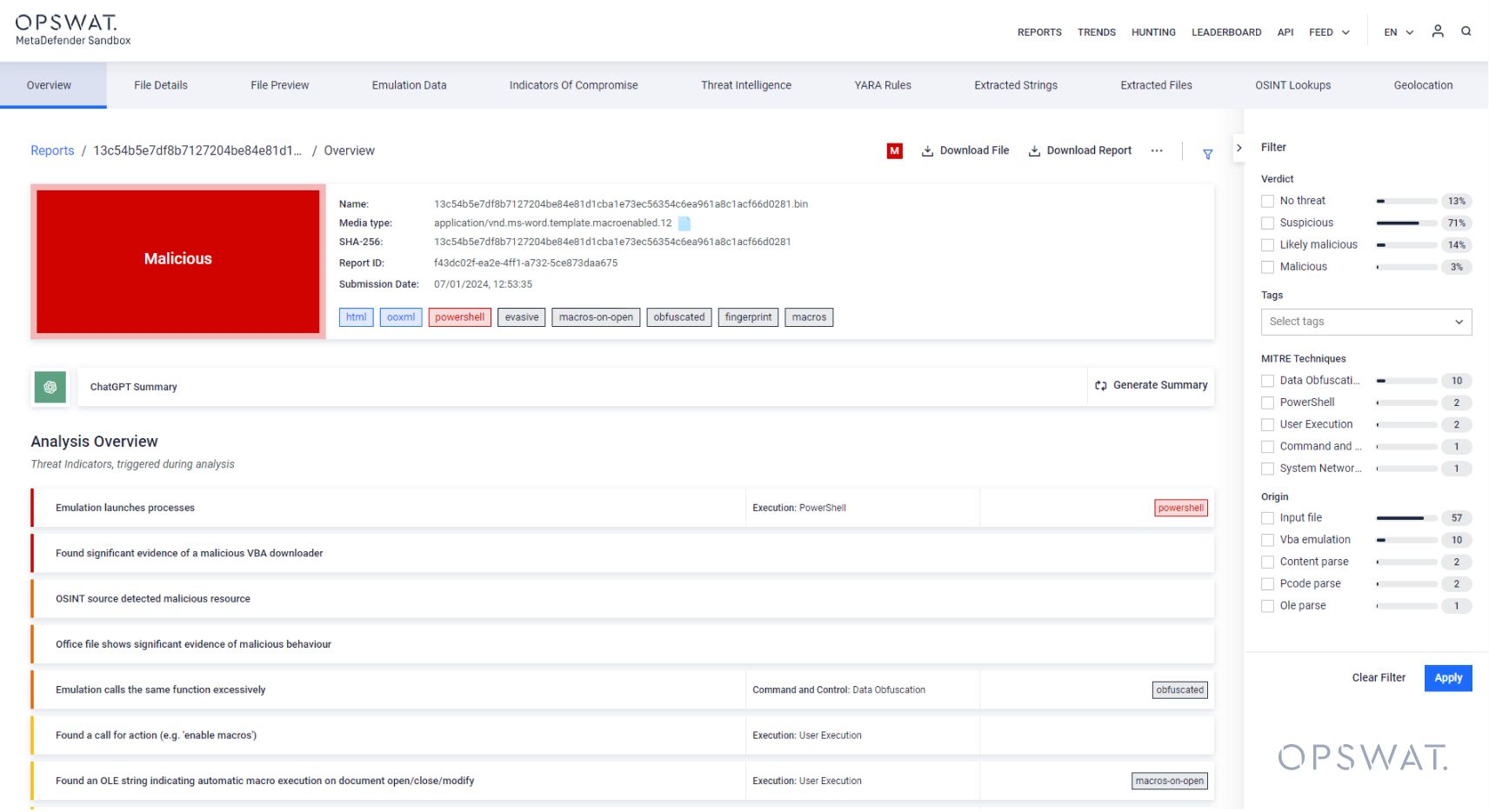
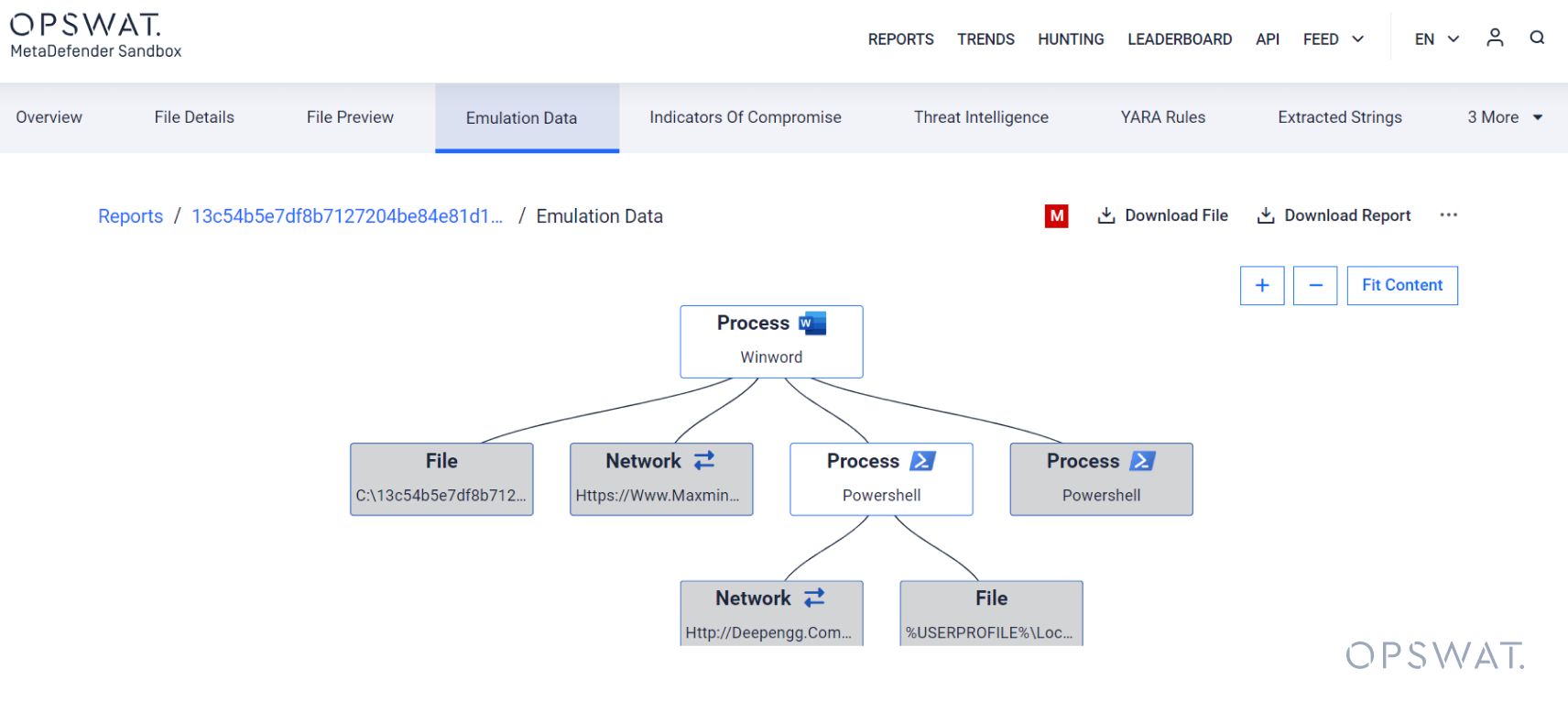
2. Threat hunting and analysis features available on the home page and streamlined navigation for effortless use.
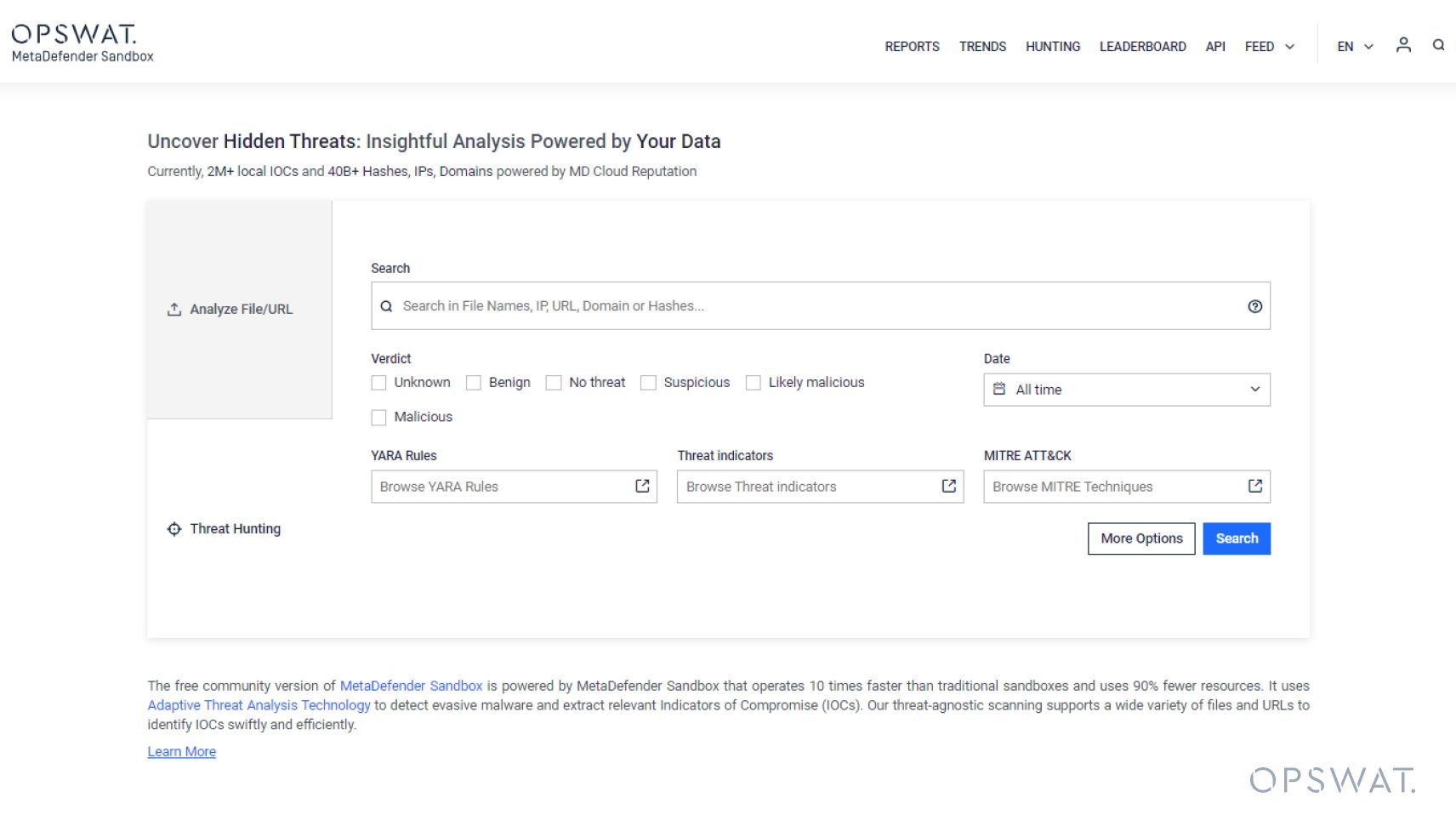
Threat hunters can easily reach a simplified version of the threat hunting page with the most common filters. This page is easy to use, with a new combined search field for names, IPs, domains, and hashes. There are multiple values allowed for many filters, a more sophisticated and precise filter for YARA rules, plus threat indicators and MITRE ATT&CK techniques and tactics.
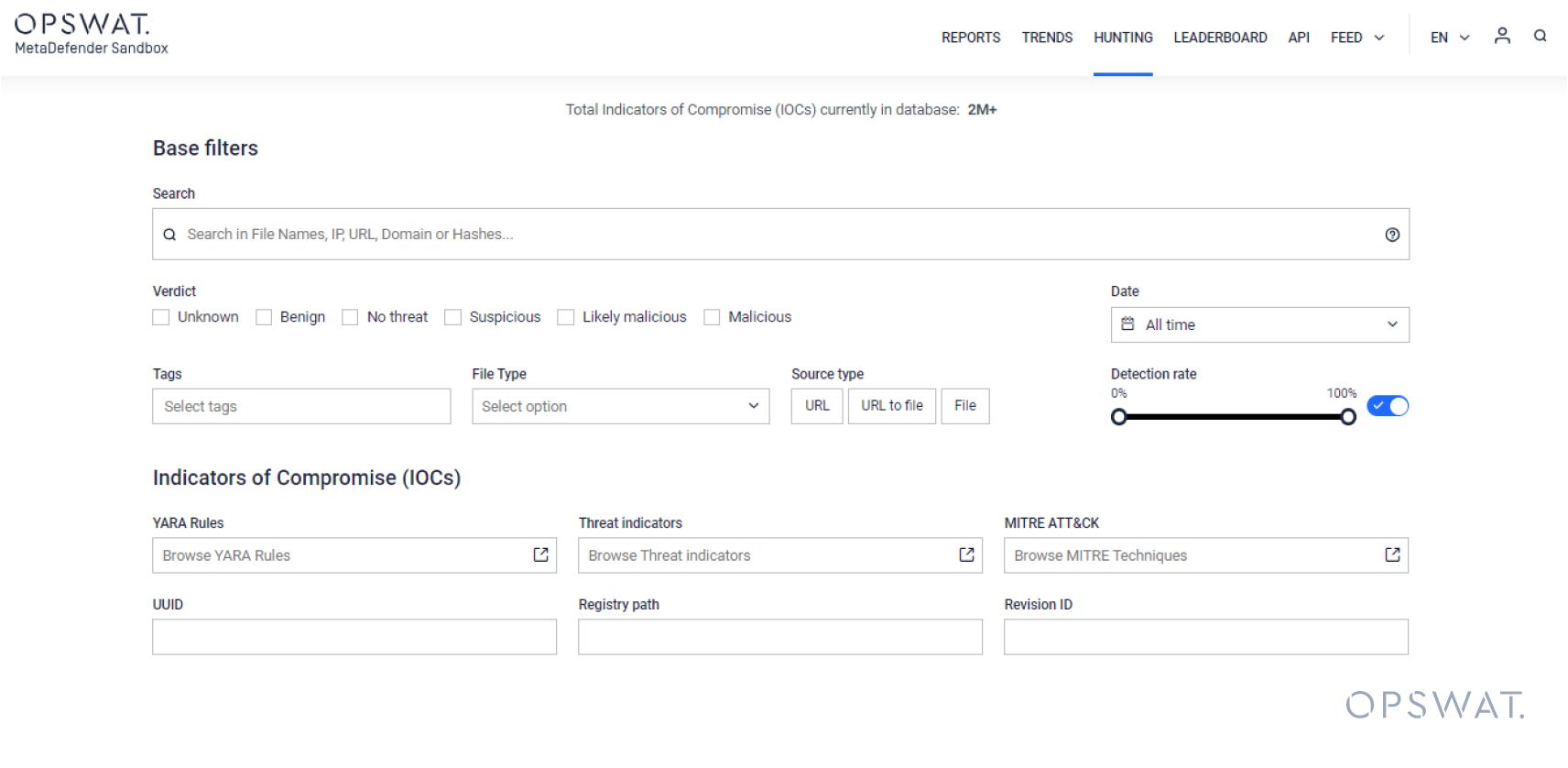
Support for Sandbox Installation on Offline Systems
Previously, Sandbox installation required an Internet connection, but it is now possible to run the installation process on offline systems using a prebuilt installation package*.
Features and Benefits of an Offline Installer for Sandbox
Who Benefits from Sandbox v.2.0.0?
Enhanced Metadata and Behavioral Information Extraction for MSI, LNK, AutoIT and ODF Files
As malware authors continuously innovate, distributing malicious code through more complex methods like MSI installers and LNK shortcuts has become more common. Traditional sandbox environments might not be equipped to extract all the information and fully handle these file types, leading to gaps in threat detection and analysis.

Malware Detection
Many malware variants are distributed as MSI installers or through LNK shortcuts. Additionally, scripting malware can be compiled into executable files, hiding its plaintext code. The ability to analyze these file types in a sandbox helps identify and mitigate these threats more effectively.

Behavioral Insights
Understanding how an MSI installer modifies the system or how an LNK file redirects or executes can provide valuable insights into potential vulnerabilities or malicious behaviors. Furthermore, MetaDefender Sandbox now extracts macro code ODF files, which have their own language to implement additional behavior.
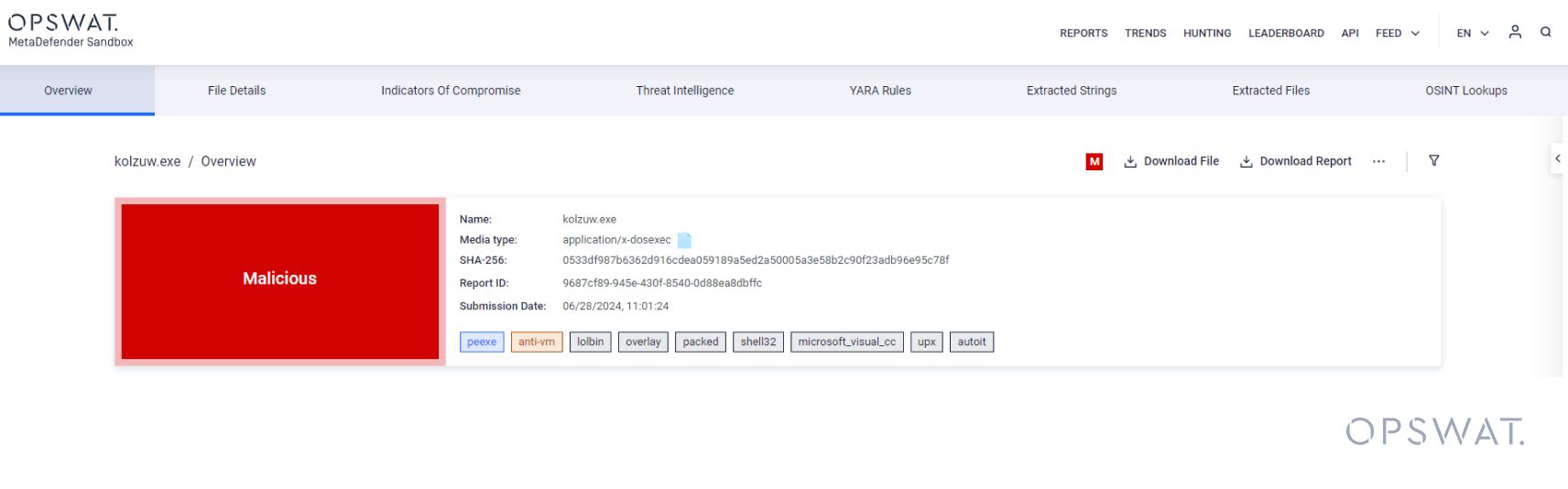
This example demonstrates how we now apply the corresponding AutoIT tag for the root input file:
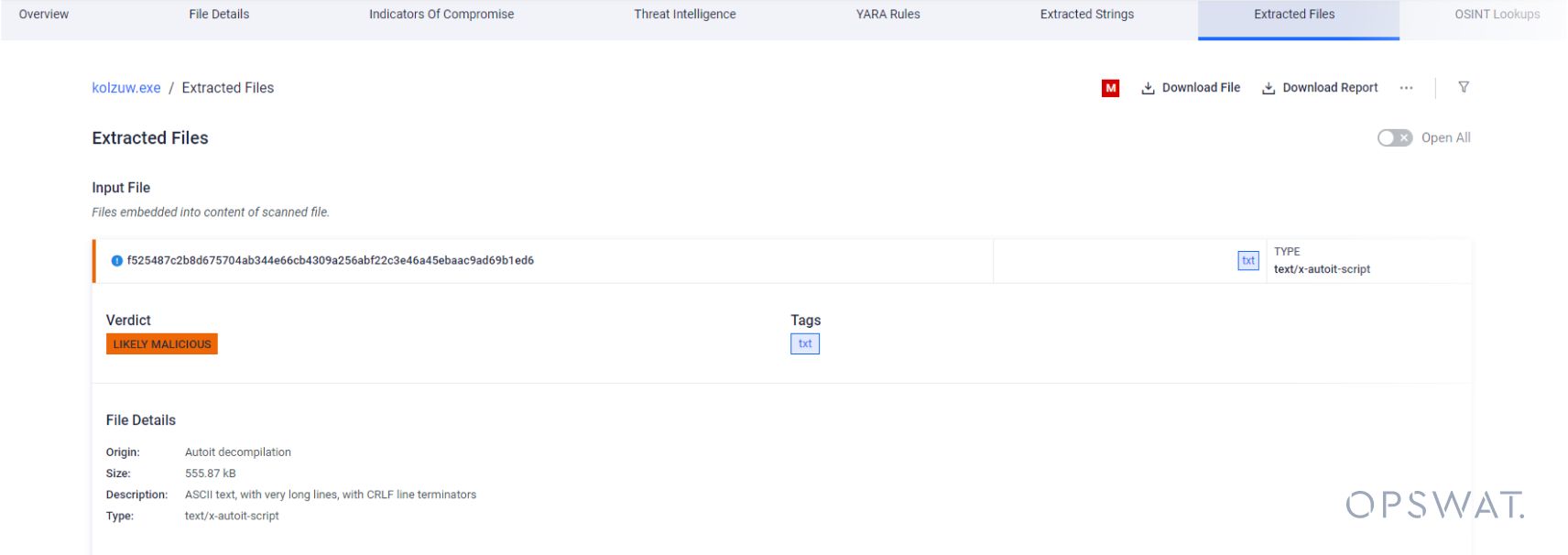
Then, we can see that the AutoIT script is extracted and decompiled to plain text from the same PEEXE input file:
Improved indicators and detections for already supported file types
Among the many new indicators, we’ve included similarity matches between Office document icons and PEEXE icons. It is common to try to masquerade executable file types by using icons and file extensions used for documents. Now MetaDefender Sandbox flags such icons used in executables based on Dhash, a similarity hash implemented for images.
Audit Logging Framework for Admin Settings and User Authentication
The new audit logging feature captures events happening in the system. These events include setting changes, logins and logouts, and registers whether operations succeed or fail. The audit logger captures the event, the user responsible for it, an error message in case of an error, and the before and after states where applicable
Types of Audit Logs
There are multiple types of audit logs, each logging events for a specific component of the system.
Admin Settings
The Admin Audit Logger logs any event happening on the Admin Panel including changing settings; creating, modifying or deleting users or groups; etc.
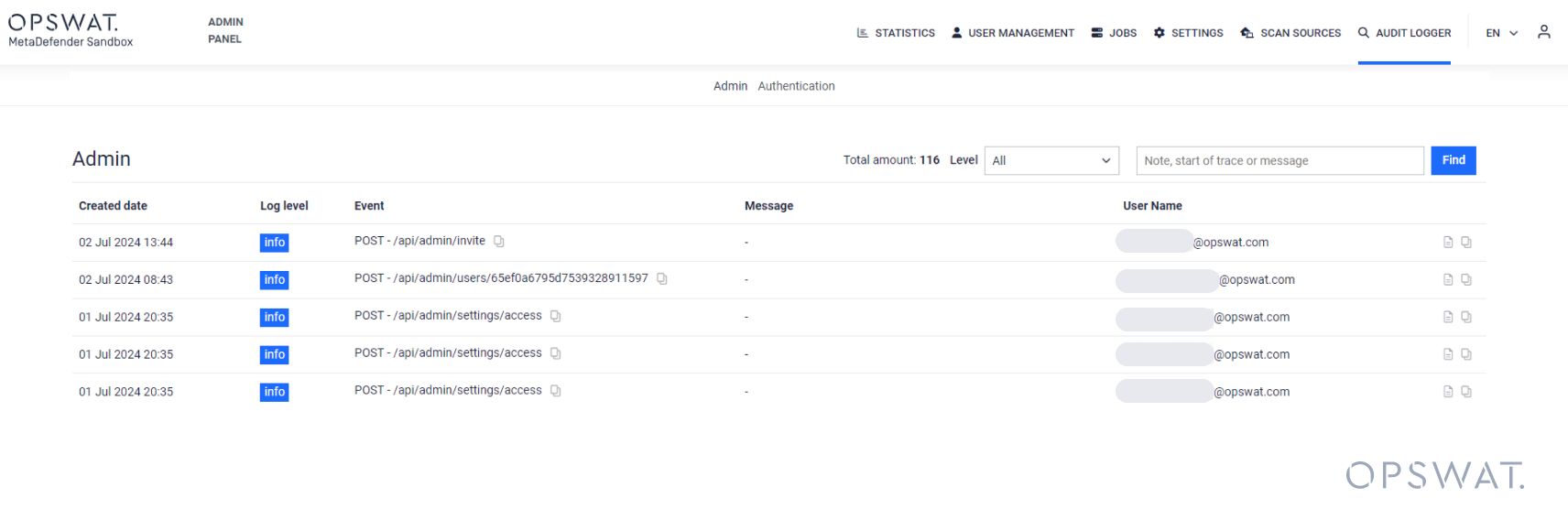
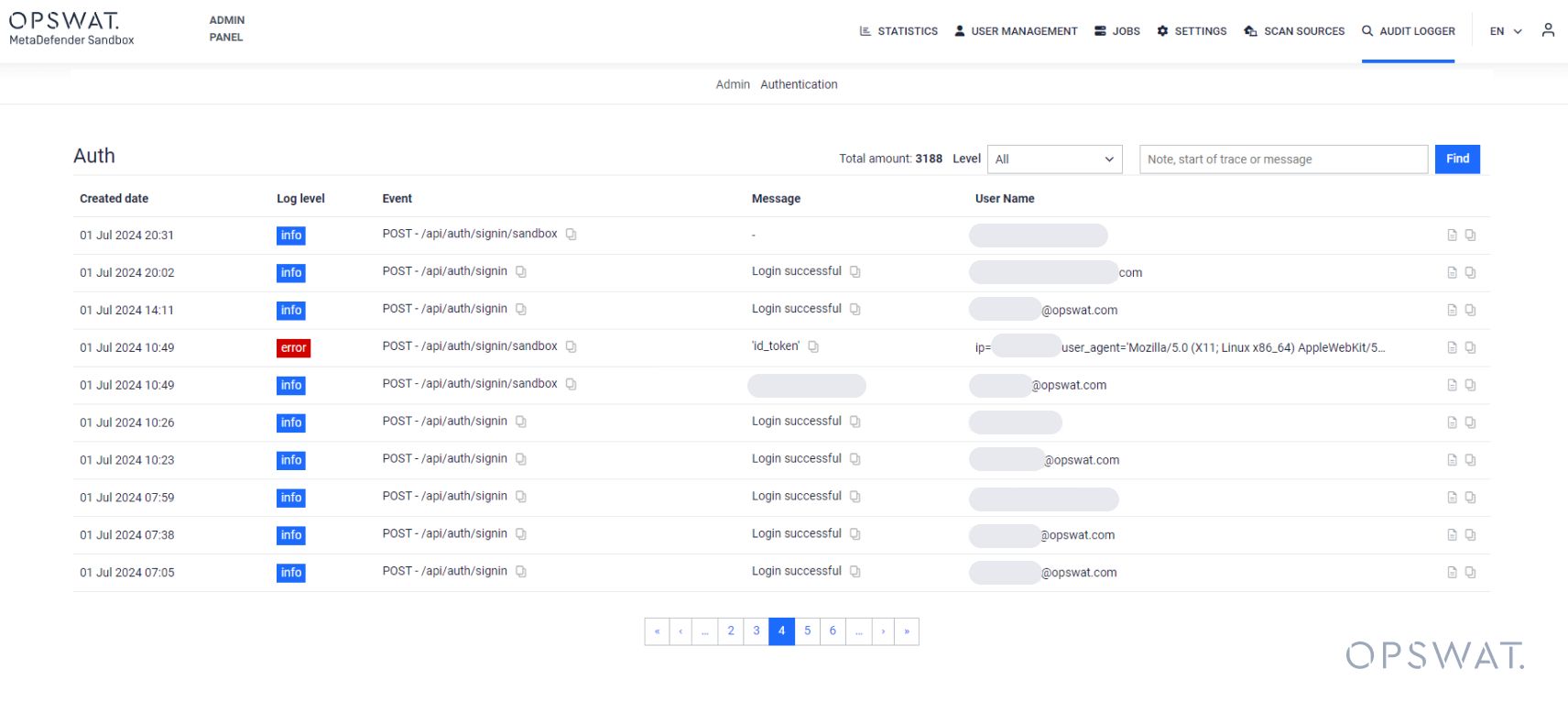
User Authentication
The Authentication Audit Logger logs any login and logout events.
A complete list of features and enhancements in the release can be found in the Release Notes for MetaDefender Sandbox v2.0.0.
* Due to legal reasons, this installation package cannot be downloaded directly from my.opswat.com. To prepare the assets for the offline installation, an online computer or virtual machine running Ubuntu 22.04 is required. After the preparation step is completed, the offline installation can be performed on multiple offline systems using the same prebuilt assets.