A 12-year old Remote Access Trojan (RAT) that first emerged from the depths in 2008 has now scurried out of its hiding place to spread a new strain of virus in 2020.
About the Malware
During its history, various strains of this virus, known as ‘Taidoor’, have predominantly targeted government agencies, but over the years have expanded their victim-pool to think tanks, the financial sector, telecommunications and manufacturers.
The FBI issued a warning and a Malware Analysis Report (MAR) on August 3rd to alert organisations and hopefully lessen exposure to Taidoor, which it believes is a Chinese state-sponsored threat – which, in itself, is cause for concern. State-sponsored hackers are those that are sanctioned and / or employed by their governments, often targeting rival countries to gain inside knowledge of defenses, sensitive information, and intellectual property - and to cause disruption to government operations.
State-sponsored = A Force to Be Reckoned With
State-sponsored attacks can often be a much greater threat than the average virus.
- They are precisely targeted: These attacks are often delivered via spear-phishing, in which a specific individual is researched in great depth and targeted with a high-value organisation in mind as the main goal. Spear-phishing emails are cleverly crafted towards the target individual to appear genuine, to the point where even a trained eye may not spot the attack. This means it is much more likely for the individual to download malicious email attachments from a spear-phishing attack, making way for the malware that follows.
- They are good at hiding their identity: State-sponsored hackers strive to remain anonymous – often achieved by acting under the guise of another bad actor or funneling information through several different countries to obscure the origin country – so that investigators have a hard time tracing back to their origin and determining their true purpose; not knowing who or what is attacking makes it much more difficult to establish a defense.
- They are good at evading detection: A characteristic of state-sponsored cyberattacks – and one that makes them more dangerous – is to remain long-term on the target network after gaining backdoor entry. Once in, attack operators can gather and exfiltrate sensitive information at leisure and learn the patterns and habits of the organisation, all while flying under the radar of security systems in place – many of which are simply not up to detecting or preventing such sophisticated attacks.
Above all, state-sponsored attacks trump others because of the resources behind them.
Take the following two scenarios:
Scenario One: An easily recognizable ransomware virus, partially downloaded from the dark web, sent via phishing emails from a lone operator in a warehouse in Ukraine, with no particular target in mind.
Scenario Two: A RAT, created and refined over years by a well-equipped agency, with access to intelligence and unlimited resources, designed specifically for a highly researched individual of a target organization.
Defending against one is a far cry from defending against the other. This is of particular importance during the current uncertainty and unrest circulating the world amidst the Covid-19 pandemic and upcoming US election – attacks sanctioned by governments are unlikely to be dropping off in the near future.
Malware Breakdown: Dissecting the RAT
Taidoor is believed to be one such state-sponsored virus. So how does it work?
As a RAT, it seeks to gain backdoor entry to a device, where it can then give its operators remote access to copy files, execute commands and monitor the target undetected. Like others, this strain of Taidoor typically begins with an individual being prompted to open the attachment of a spear-phishing email. Once opened, a decoy document leads the individual to believe there is nothing amiss; meanwhile the malicious content gets to work on the endpoint.
According to the Malware Analysis Report published by the US Cybersecurity and Infrastructure Security Agency (CISA), four files have been identified as Taidoor: two each for 32-bit and 64-bit Windows platforms:
1. ml.dll – 32-bit loader
2. rasautoex.dll – 64-bit loader
3. and 4. svchost.dll – the Taidoor RAT files, one for each version of Windows.
For both Windows operating systems, the first of the two files is a dynamic link library (DLL). A dynamic link library comprises several small programs, procedures and code that can be used by multiple larger programs at the same time. DLL files help with conserving computer memory because information is shared between programs.
According to the CISA Malware Analysis Report, the Windows 32-bit loader, ml.dll, and the 64-bit loader, rasautoex.dll, are started as services on their respective platforms. From here they search for the second file in the running directory: svchost.dll – the Taidoor RAT.
The RAT is then read into computer memory and decrypted by the loader files, where its ‘Start’ function is executed and the trojan gets to work establishing remote access for attack operators.
Defense Line 1: OPSWAT MetaDefender Cloud
So how does one exterminate such a RAT? Or better yet: prevent the infestation in the first place. Our answer is by using a double-layered defense system!
A virus, of course, calls for an anti-virus. However, because of the sophisticated nature of Taidoor – and the likelihood of a well-equipped agency and an abundance of resources behind it, relying on a single, endpoint anti-virus solution to detect and prevent such an attack is a big risk.
Our cybersecurity experts know this; that’s why we have come up with a solution that minimizes the risk as much as possible.
This solution is MetaDefender Cloud, which provides threat detection and prevention by enlisting a range of advanced techniques.
Simultaneous Scanning
One of these techniques, called ‘Multiscanning’, employs the use over 30 anti-malware engines to scan for both known and unknown threats using heuristics, signature-matching and machine learning technology. Utilizing so many anti-virus engines comes with numerous benefits:
- Higher Rate of Detection: Anti-virus engines all use varying techniques and specialist in different areas when it comes to detecting malware. Statistics show that the more anti-virus engines used, the higher the detection rate. Utilizing 30+ anti-virus engines means MetaDefender Cloud can claim a detection rate of over 99%.
- Minimized Exposure Times: Anti-malware engines take different amounts of time to detect new threats; relying on a single endpoint solution could mean a longer exposure time if said solution doesn’t pick up on new threats as quickly as others. Using multiple anti-virus engines means your chances of being left out in the open when a new threat emerges are decreased to the absolute minimum.
- Limitations of using a Single Vendor are Eliminated: All anti-malware solutions have strengths and weaknesses. Using 30+ anti-malware engines means any limitations of one are covered by another. The same principle applies if one solution cannot operate due to geographical or business limitations; rest assured another of the 30+ will have this base covered.
MetaDefender Cloud vs. the Taidoor RAT
When it comes to the RAT in question, MetaDefender Cloud proves highly effective.
Take the following samples from each file used to infect a computer system with Taidoor – and see the multiscanning detection rate when each one is analysed by MetaDefender Cloud:
1. ml.dll - 32-bit loader: 4a0688baf9661d3737ee82f8992a0a665732c91704f28688f643115648c107d4

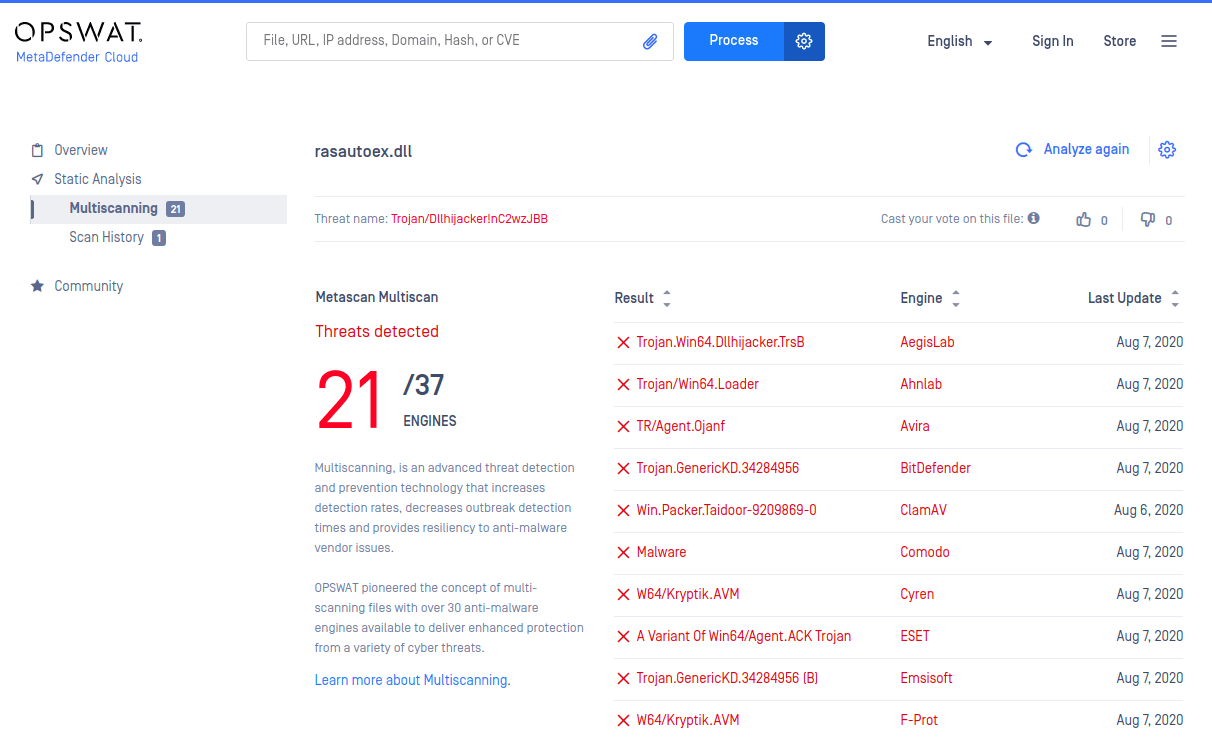
2. rasautoex.dll - 64-bit loader: 6e6d3a831c03b09d9e4a54859329fbfd428083f8f5bc5f27abbfdd9c47ec0e57
3. svchost.dll - 32-bit Taidoor RAT: 363ea096a3f6d06d56dc97ff1618607d462f366139df70c88310bbf77b9f9f90

4. svchost.dll - 64-bit Taidoor RAT: 0d0ccfe7cd476e2e2498b854cef2e6f959df817e52924b3a8bcdae7a8faaa686

Malware samples provided by CISA in the Taidoor Malware Analysis Report.
MetaDefender Cloud Multiscan detects malware in all four samples used in Taidoor attacks, with multiple engines flagging the samples as malicious each time.
These detections offer a real-life example of what would happen if a user attempted to download the Taidoor RAT from a spear-phishing attack: files would be detected and flagged by MetaDefender, and blocked from the host device, thus preventing infection.
Defence Line 2: Admin By Request
The second line of defence comes in the form of Privileged Access Management (PAM) software. PAM refers to the practice of restricting, controlling and monitoring higher-level access to computer systems using the Principle of Least Privilege (POLP): allowing only the minimum access necessary for undertaking activities; and Just-in-Time elevation (JIT): allowing elevated access only where and when absolutely necessary.
Our partners, Admin By Request provide one such PAM solution, delivered in an easy to deploy, use, manage and maintain package. Essentially, Admin By Request quickly and cleanly revokes admin rights.
Within the user portal, groups can be created and settings can be customized to cover all levels of user, depending on their access needs.
The Requests page displays any requests users have made to run applications with administrator privileges, or to have a timed session in which they have elevated access to their machine – with the option to approve or deny these request in the web-based user portal, or the mobile application.
The Auditlog logs activity that takes place when users run an application as the administrator or have an administrator session, allowing all elevated access to be monitored.
In the Inventory, all the necessary data for each user’s device is collected and displayed, along with the elevated applications and administrator sessions used by that user.
All of these features ultimately allow Admin By Request to protect the end point by stopping users from having access and being able to make changes to critical parts of their machines.
Admin By Request vs. the Taidoor RAT
So how does Admin By Request’s PAM solution stack up against the Taidoor RAT?
Considering how the virus must operate in order to infect a system, the answer is: very well.
From our malware breakdown, we know that the loader files (ml.dll and rasautoex.dll) begin the infection process by starting as Windows services on their respective platforms.
- Admin By Request disrupts this first step when it revokes local admin rights: Due to the fact that regular users are unable to start, stop or restart Windows services, it is impossible for the Taidoor loader files to start running as services on any device where Admin By Request is installed, without the user first gaining admin access.
Another early step in Taidoor’s infection process is the loader files reading the RAT file (svchost.dll) into computer memory.
Again, Admin By Request prevents this from happening by restricting elevated access:
- User accounts that don’t have administrative privileges cannot access memory on the host device without first gaining elevated access, meaning Taidoor loader files are not able to read / write to the memory of an endpoint that has Admin By Request installed.
If a user did attempt to download and run malicious code from a spear-phishing email on a device with Admin By Request installed, the malware would simply not have the access it needs to commence infection.
An Alliance: MetaDefender Cloud and Admin By Request
A comprehensive anti-virus or a PAM solution on their own are both viable security options for a safer IT system – but a single solution that combines the two provides the necessary layered defense system against advanced, state-sponsored attacks.
Admin By Request’s PAM software integrates the MetaDefender Cloud API to form that layered defense.
As well as users having their local admin rights revoked, any files that are run with administrator privileges are first scanned in real-time by MetaDefender Cloud’s 30+ anti-malware engines.
Protection is two-fold: Admin By Request blocks malware from gaining much-needed local admin rights, while MetaDefender blocks the user from running the file as administrator if it detects malware – Taidoor and similar malware are successfully prevented from doing any damage.
Summary
State-sponsored, backdoor malware like the Taidoor RAT needs to be taken very seriously, with targeted, spear-phishing emails often fooling regular users and experts alike.
Detecting and preventing such attacks if you’re targeted is possible – but only with a comprehensive defense system that ensures all gaps and endpoints are covered: 30+ times over.
Cover all bases with the layered approach provided by OPSWAT MetaDefender Cloud and Admin By Request’s PAM solution.
For more malware analysis news, subscribe to our newsletter below.

