Our skillful team has been quite productive, focusing on hardening the MetaDefender Sandbox analysis engine, supporting additional threat types (such as our newly added URL analysis capability), growing the community with common trends globally, and building an enterprise-grade product.
In this short blog post, we'll showcase a few admin panel/backend capabilities that most users do not interact with on a day-to-day basis, as these features are only available to administrators.
How to Access the Admin Panel
Users with administrator status can access the Admin Panel after logging into the OPSWAT Filescan web service. You can find the Admin Button by navigating to the User Profile Menu at the top right of your screen and clicking on "Admin panel".
Note: Admin status is automatically assigned to the initial user when deploying the vanilla system.

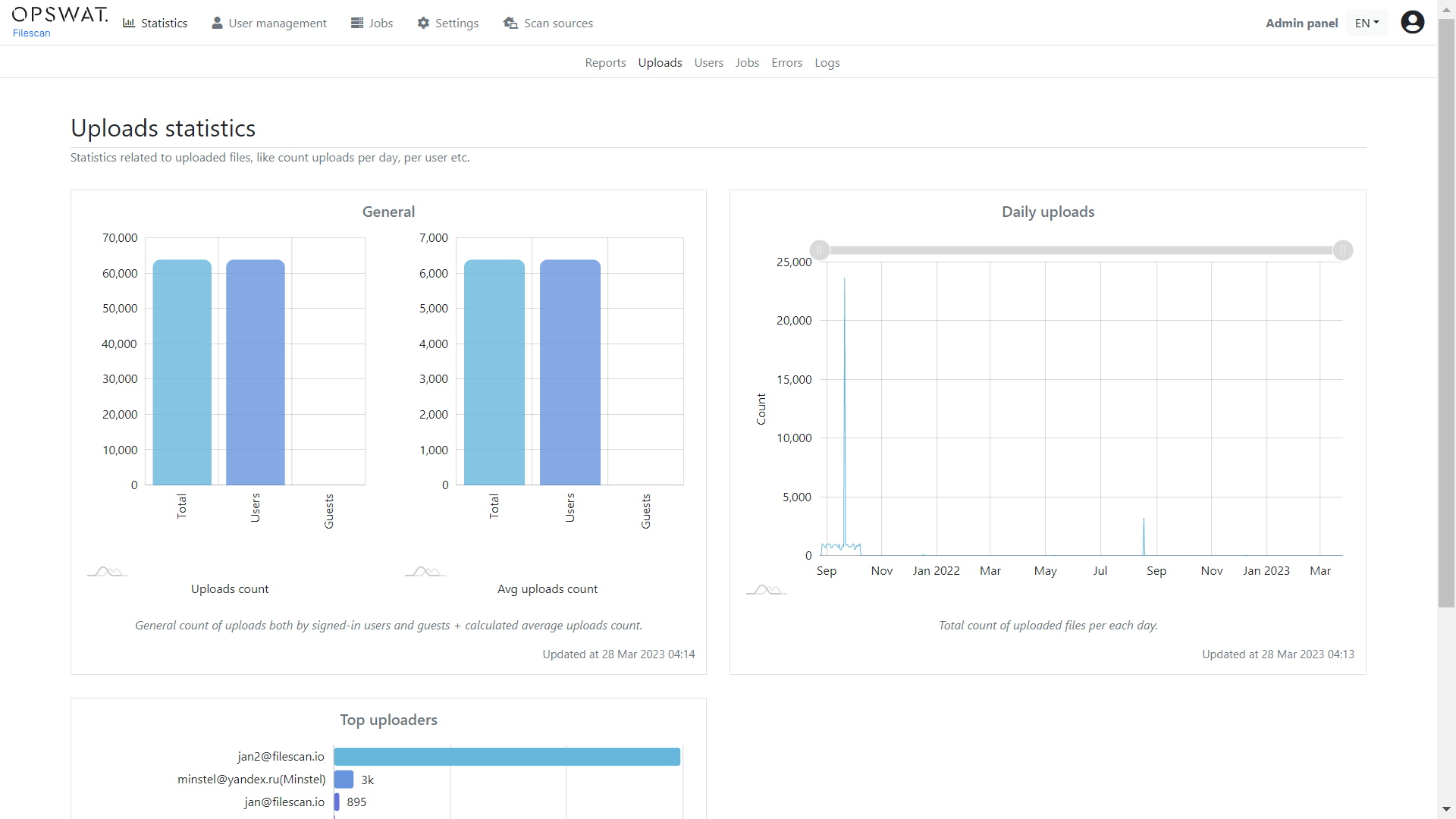
The Admin Panel contains all the Statistics subpages, which you can access using the top menu bar pictured below. In addition, regular users can access the Trends page for similar output.
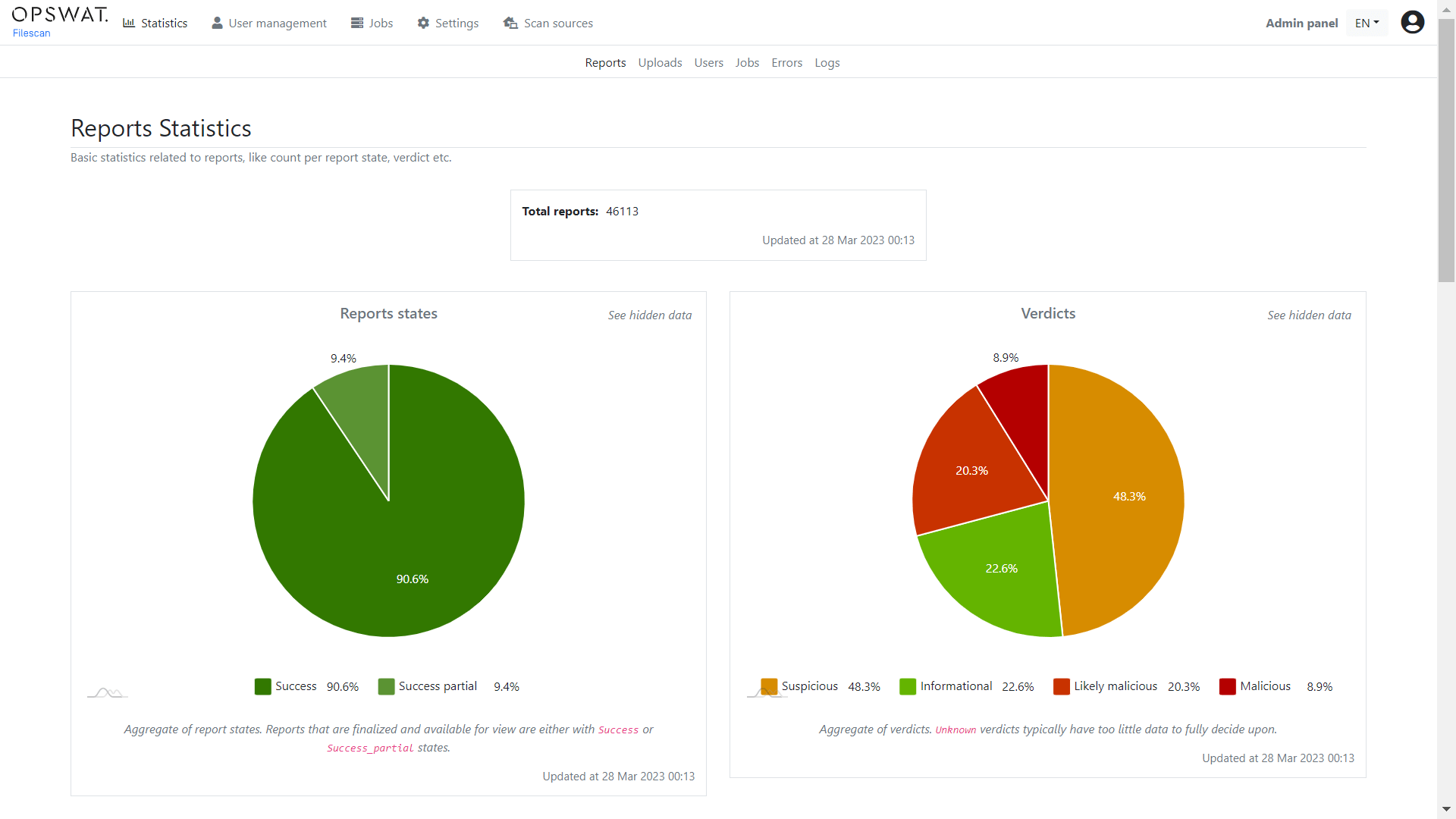
The Statistics Pages have a variety of data analytics on the file types seen, the total number of active users, top uploaders, uploader count, and more.
The Errors subpage also contains a de-duplicated list view with filtering capabilities of client errors that users may experience. It's the go-to place to find edge cases that you may have yet to consider.
Note: One of the benefits of operating a public community service is that we receive a wide range of files and URLs. We're continuously hardening our system with real-world data.
User Management
The User Management page provides a paginated list of users, including their user account status, group name, last login date, and other information. For data privacy reasons, we won't include a screenshot. However, it's worth noting that there's a highly configurable User Group capability that allows the admin to create any number of groups and assign permissions. Any user can be a member of a single group or multiple groups, and the final access permissions are group-aggregated similarly to how users work on UN*X (Unix-Like) systems
Individual Group Permissions are configurable by navigating to Settings > Feature Access using the top menu bar. For example, you can configure which Group is allowed to access which feature.
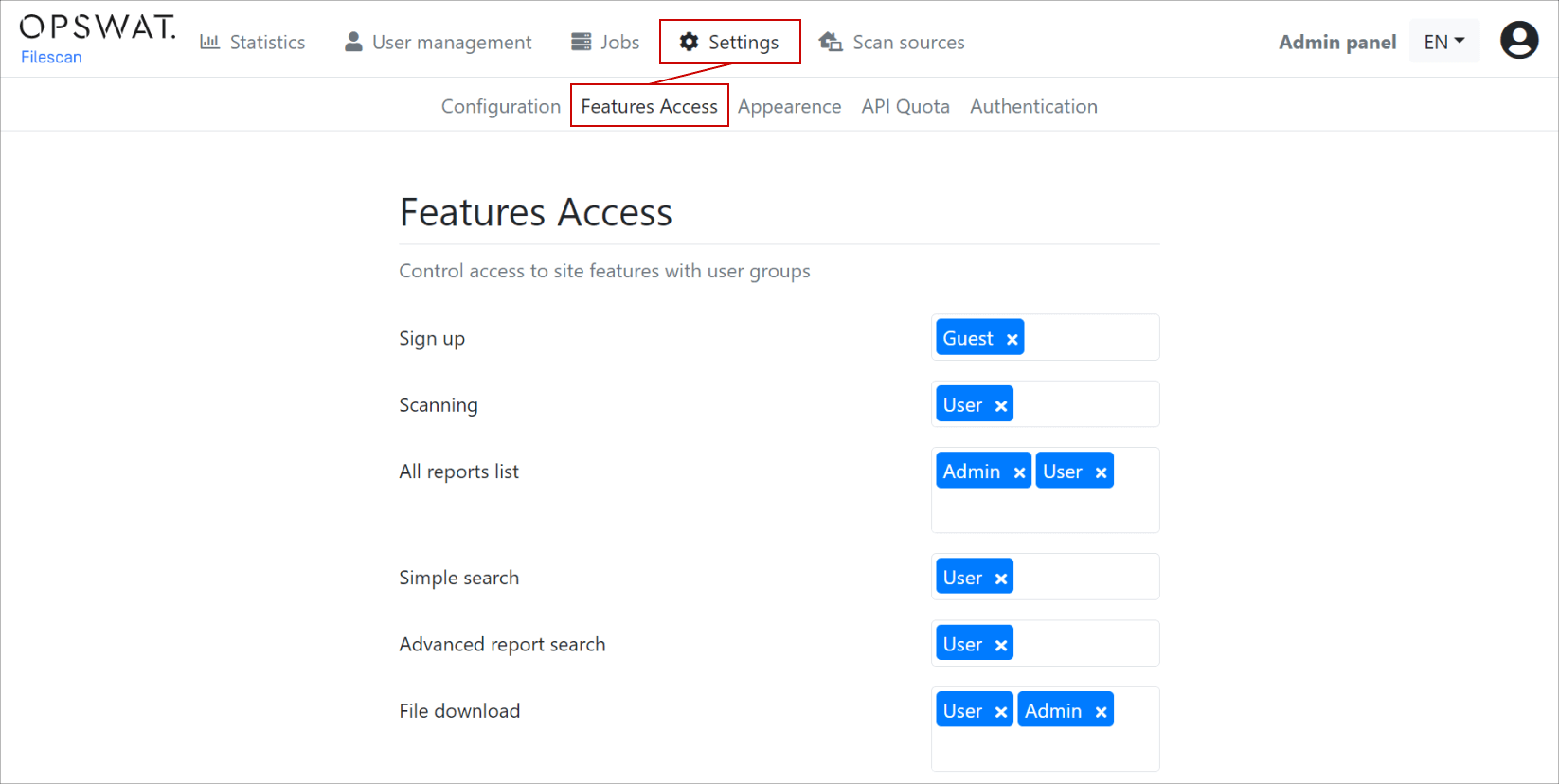
Note that by default, every user is part of the User Group. Intel users will be able to access both Basic Threat Intelligence and Advanced Intelligence features.
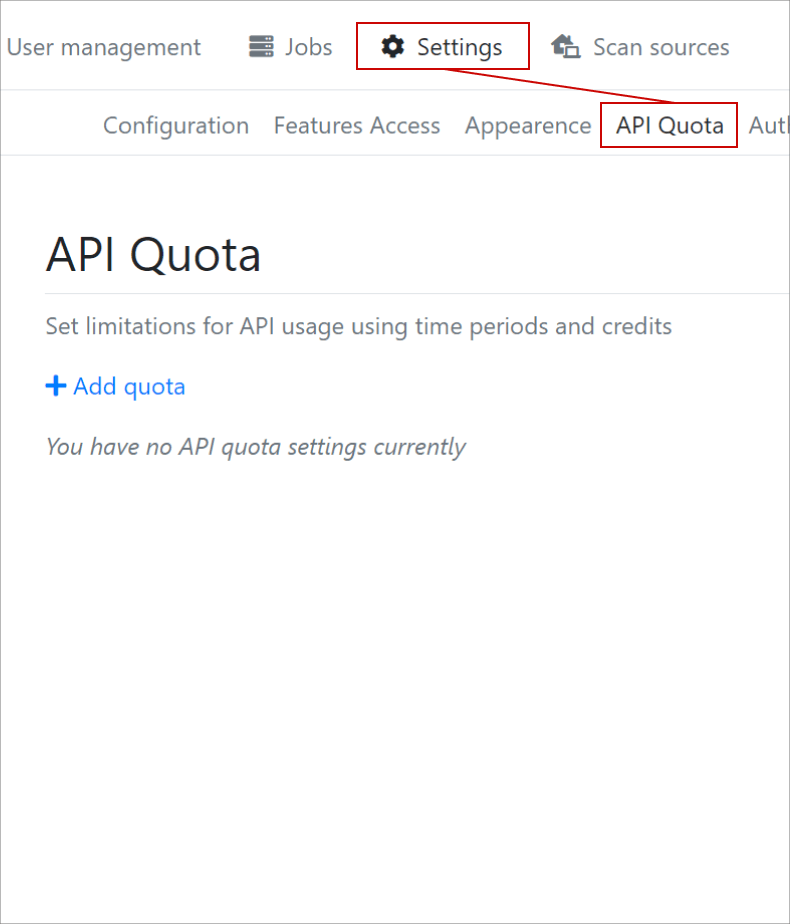
API Quotas
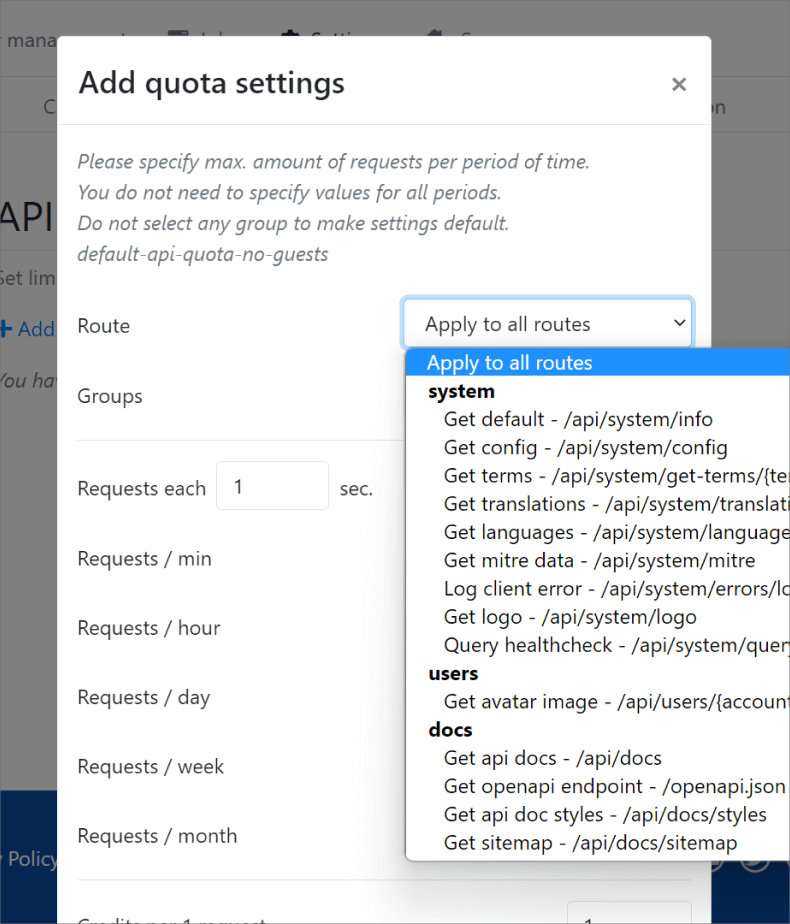
We have a very extensive API Quota Settings subpage that allows for setting an API Quota on either a Route or per Group basis with very granular configuration options.
OAuth 2.0
A lesser-known feature is the ability to allow Authentication with the webservice using OAuth 2.0 such as Google or Azure Active Directory.
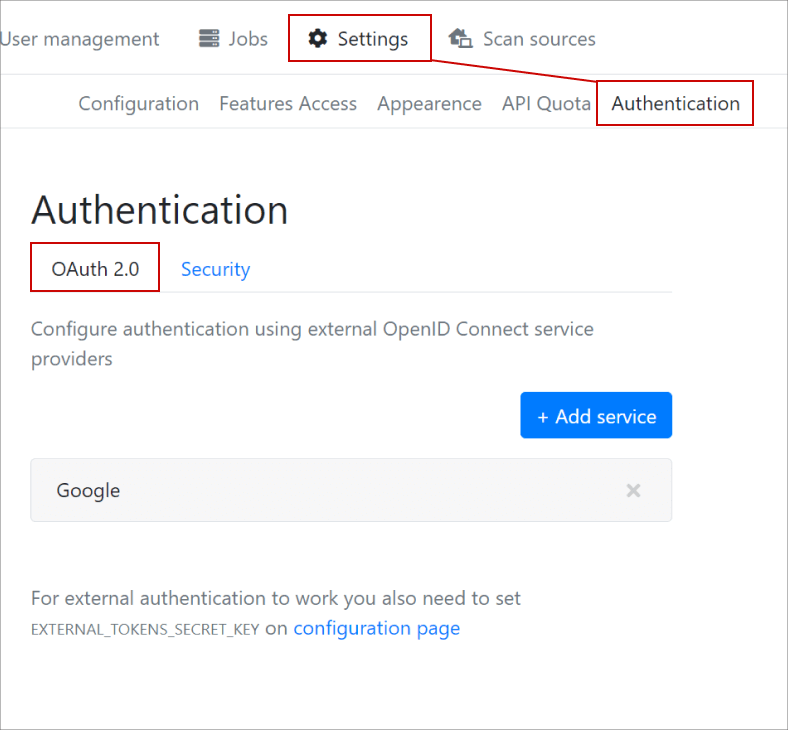
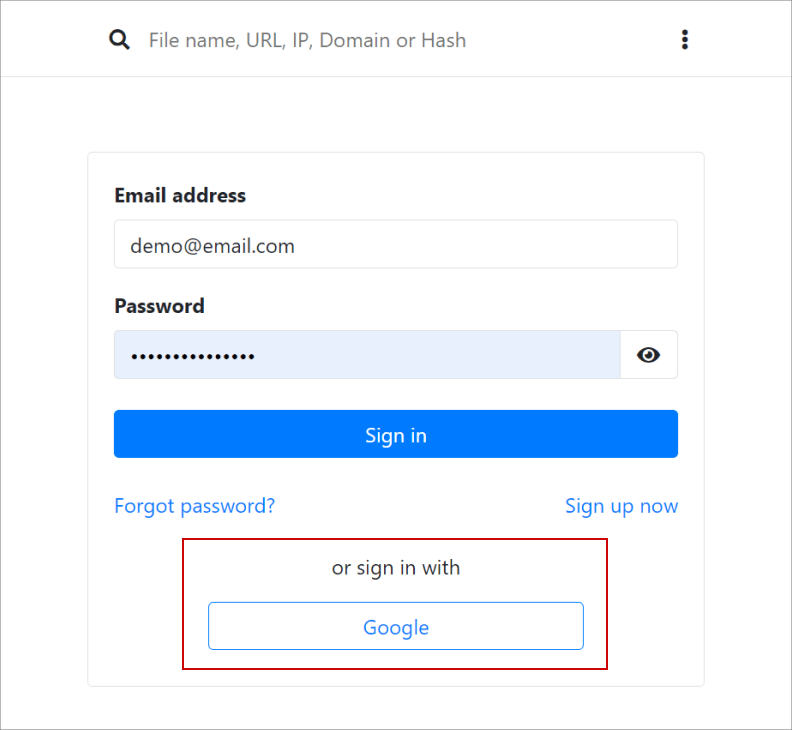
When this feature is enabled, a User will be able to login to the webservice either using the local account or the OAuth 2.0 service provider.
Note: an interesting feature is that we allow specifying multiple OAuth providers and automatically detect & merge users with the same identifier.
Scan Sources
Another new webservice feature is the Scan Sources capability accessible from the Top Menu. It allows configuring the webservice to pull in files/URLs from a variety of sources.
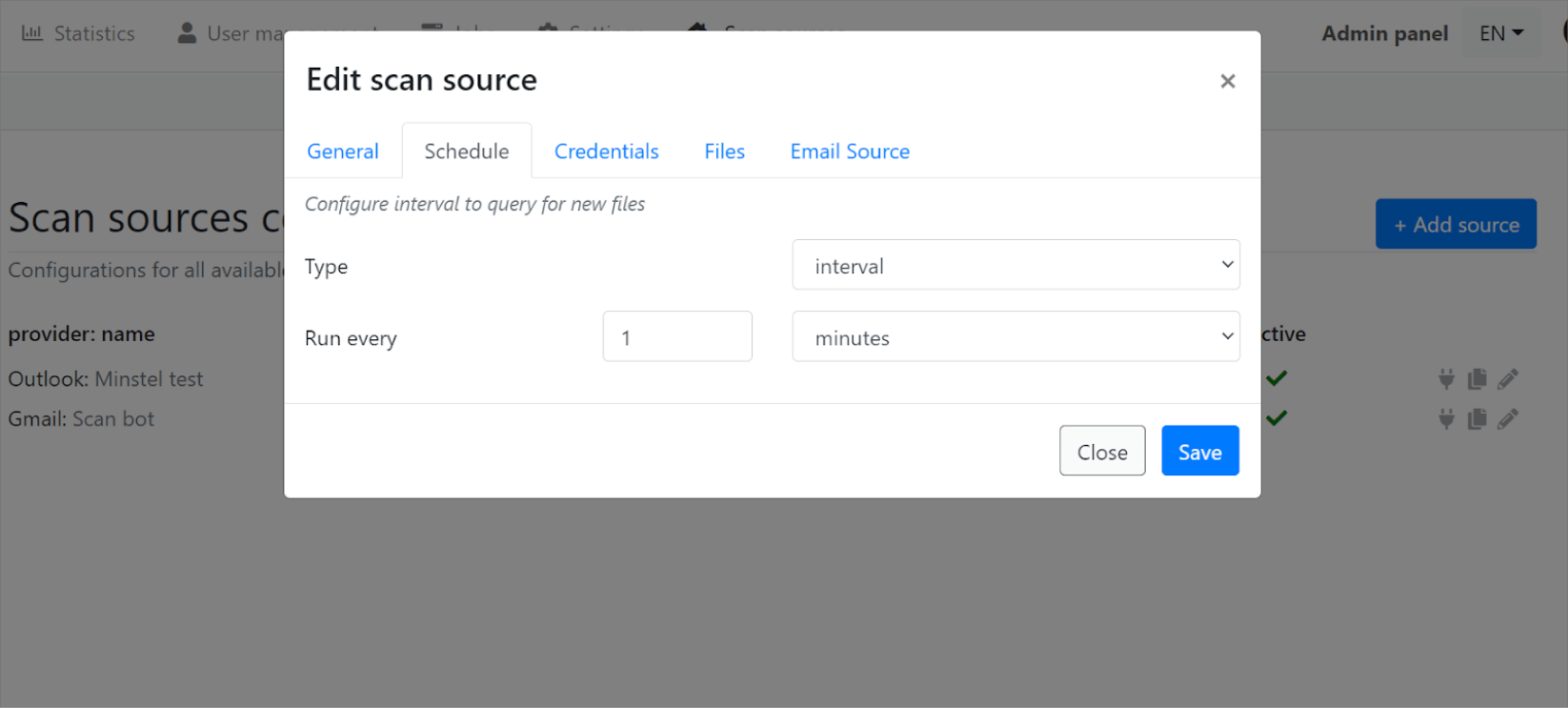
To set up an Email Scan Source navigate to Scan Sources -> Config -> Add Source.
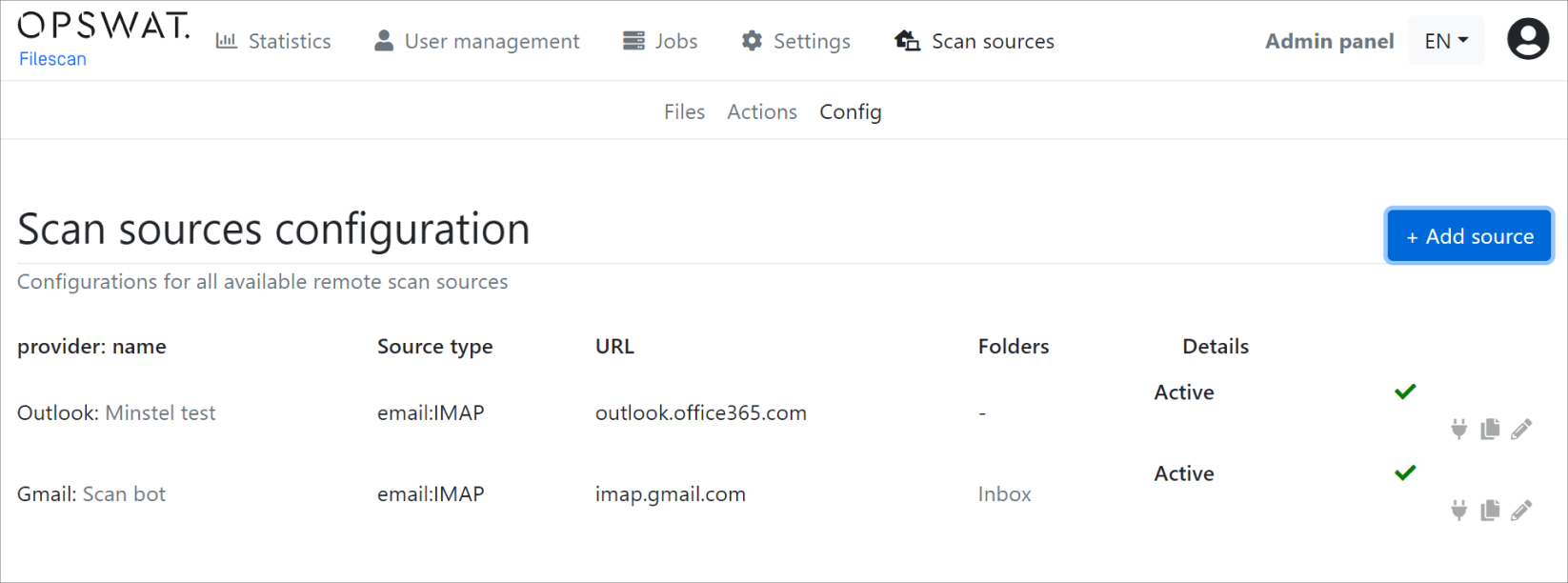
Currently, we support the configuration of IMAP accounts that are then regularly polled with a background (cron-like) job and ingested into the webservice automatically. Here are a few examples:
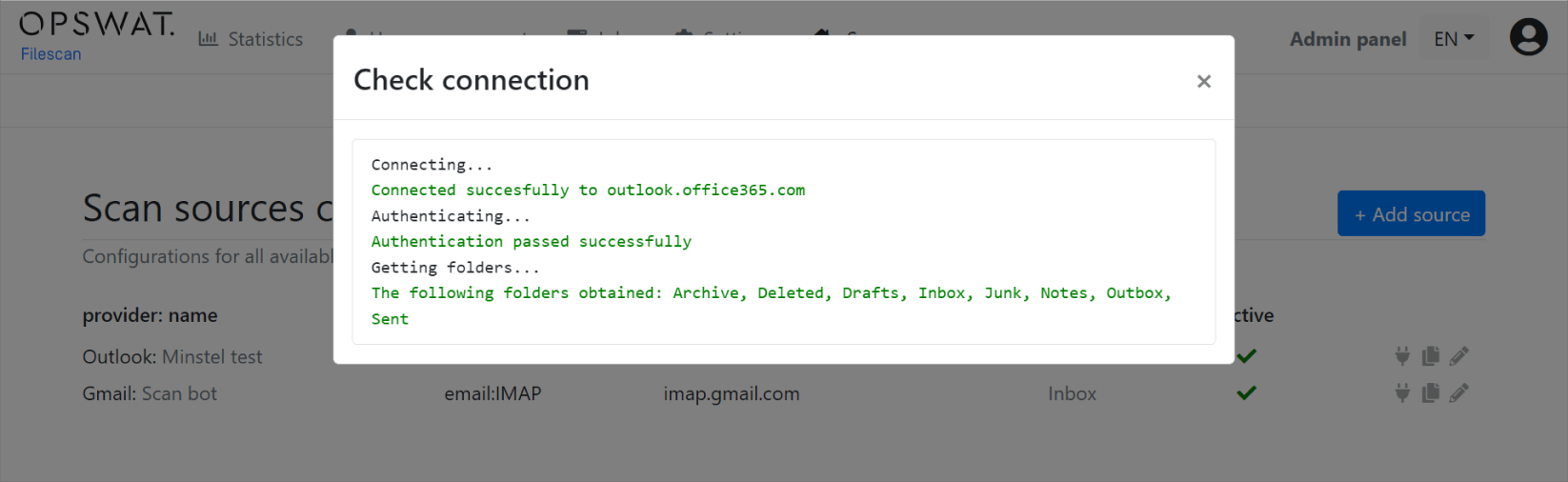
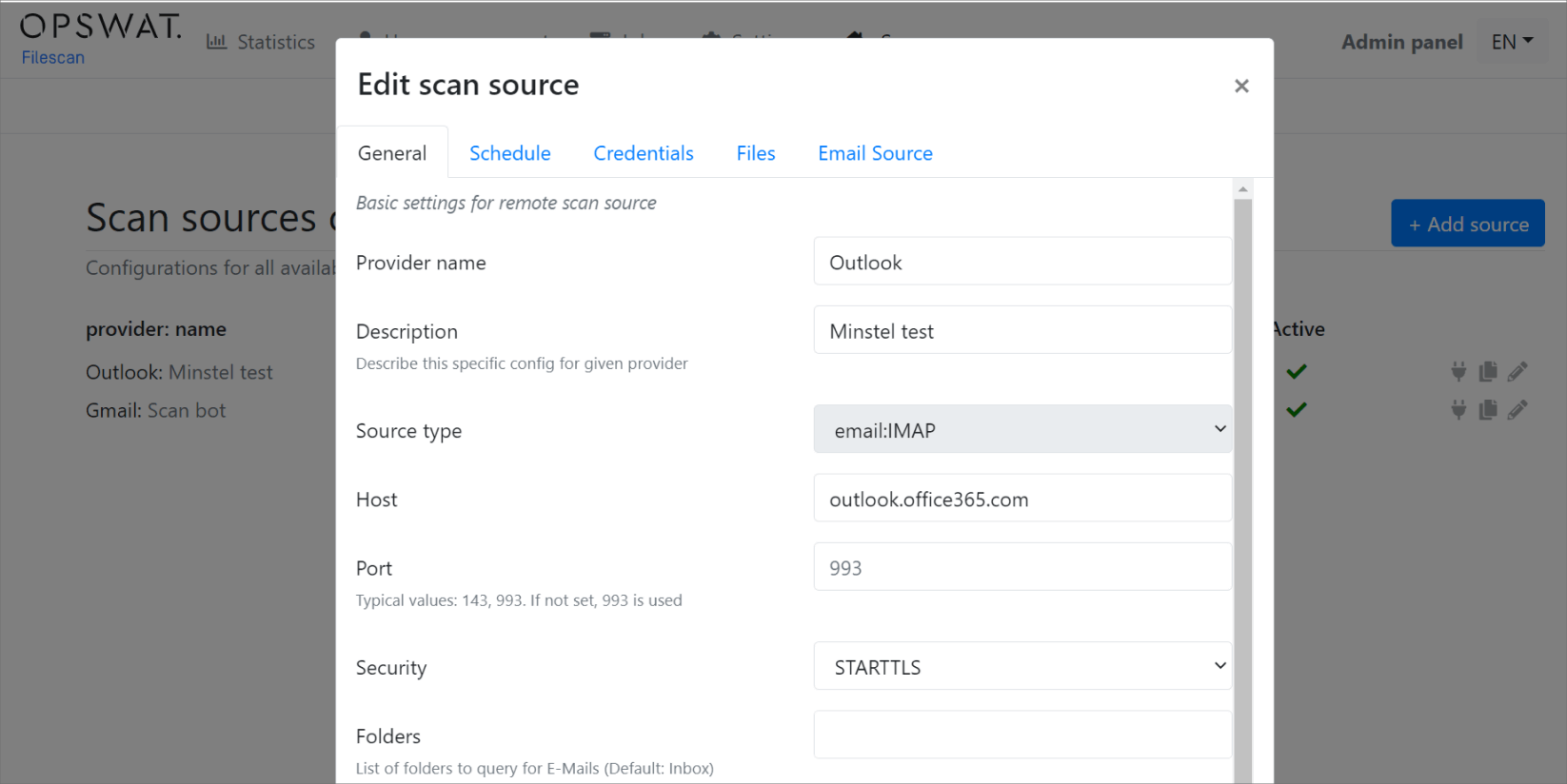
You can edit a Scan Source by navigating to Scan Source -> Config and clicking on the Pencil Icon.
Often Overlooked Features
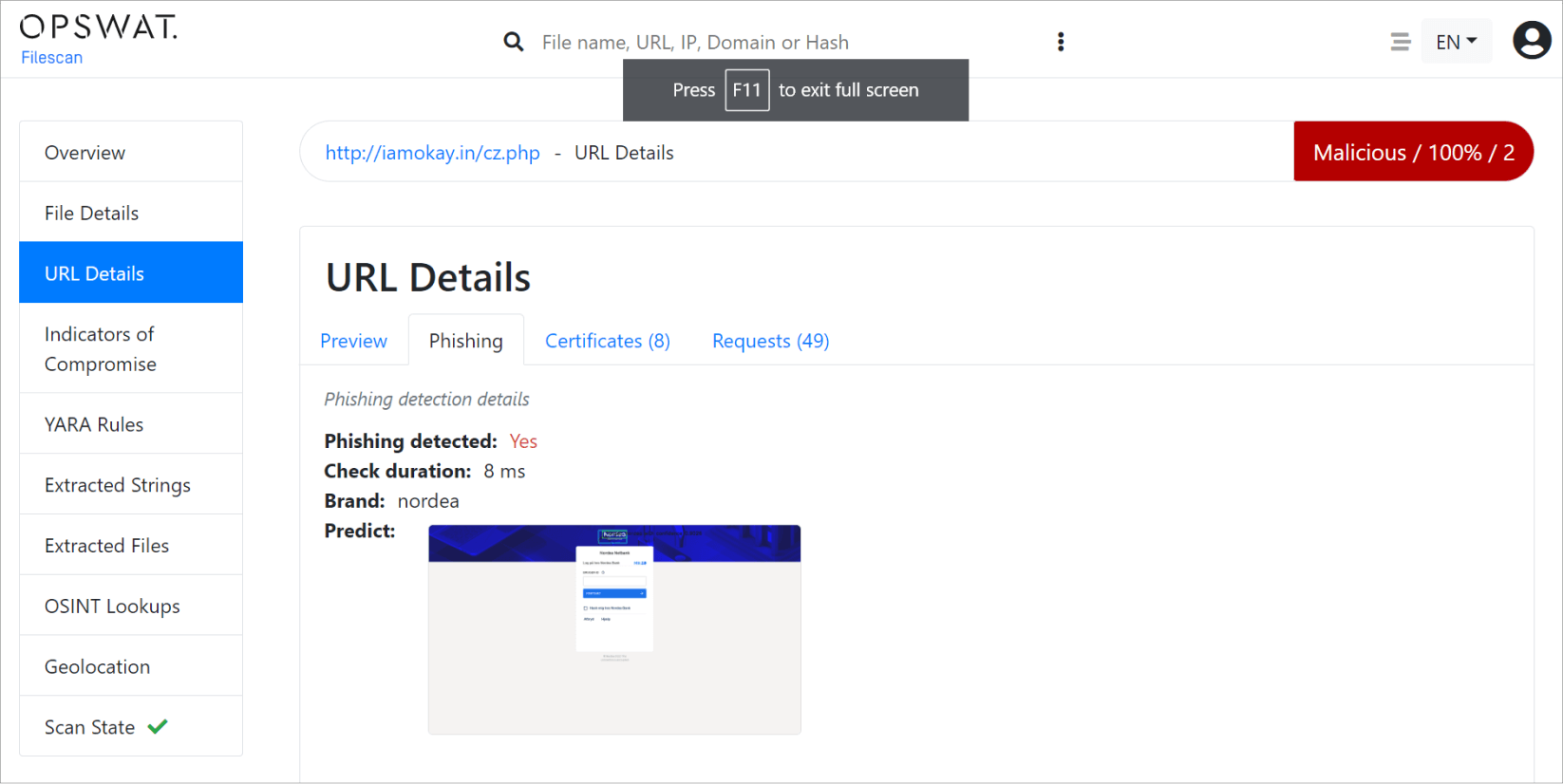
URL Phishing Detection
When submitting a URL, MetaDefender Sandbox will automatically determine if it's a "URL to a file" or a webpage. In the case of a regular webpage, a full browser emulation is performed, including machine-learning based image analysis of a phishing attack. Here's a great example of how MetaDefender Sandbox detects and alerts users of a potential phishing attack:
OpenAPI / Python CLI
An extensive API and OpenAPI (OAS3) Documentation is available from the API link at the Top Menu. You can generate your API key for authorization at the API Key Tab of your profile settings. A convenient pip package / CLI tool is available here: https://github.com/filescanio/fsio-cli.
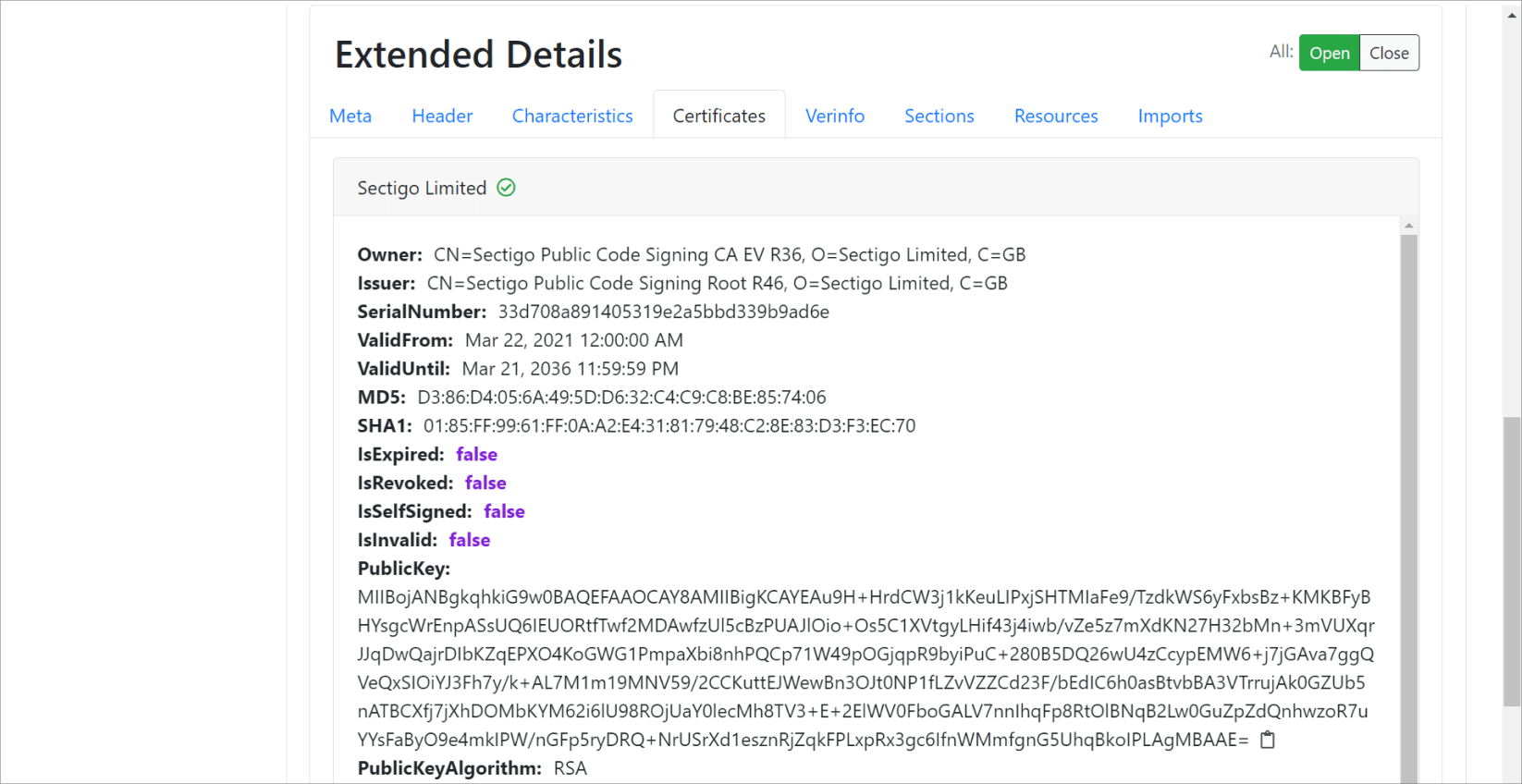
Certificate Whitelisting and Validation
MetaDefender Sandbox.io extracts certificates not only from PE files but also productivity files such as PDF or VBA macros. All extracted certificates are checked to determine whether they are expired, revoked, or self-signed. When a trusted software vendor issues a certificate, the verdict for that binary artifact is set to benign automatically.
Final Words
In this blog post, a few key areas of the Admin Panel and backend features have been showcased, outlining the maturity of the overall product and its flexibility in terms of ACL and customization.
If you are interested in learning more about www.filescan.io or in this blog post and are interested in a live technical demo, data sheets, and/or a quote, please get in touch with sales via our company contact.

