In November 2017, we published a blog post about how OPSWAT data sanitization (CDR) blocks macro-less attacks that use Microsoft Word documents. Recently, Trustwave published an article describing another type of macro-less attack that utilizes multiple vulnerabilities in multiple stages to evade detection-based security defense systems.
In this article, we want to show how important it is to eliminate threats without relying on detection, and how effective data sanitization (CDR) technology is for this purpose.
Summary of the Macro-Less Attack
First of all, we will break down the multi-stage email word attack that Trustwave described into five stages. The process involves multiple documents and file downloads.
We will focus on stages 2, 3, and 4, which are either CVE exploits or scripting features of the files that are used for the attack.
- Stage 1: Emails with Word documents attached are an effective means to bypass email security gateways, since Word documents are a common file type and will not be blocked.
- Stage 2: In this stage, as soon as a user opens the file, it will download an RTF document, which is used for the next stage. (This stage may use an exploit similar to CVE-2017-0199.)
- Stage 3: The stage exploits CVE-2017-11882, a Microsoft Office memory corruption vulnerability that uses the old Equation Editor feature. The vulnerability allows the RTF document to download the HTA file that is used for the next stage.
- Stage 4: The HTA file has a VB script section that executes yet another file download, which is the final payload.
- Stage 5: Payload: This is malware that steals passwords, and it is executed as the final step.
Neutralizing Stage 2 of the Macro-Less Attack with CDR
The file used in stage 2 utilizes OLE object embedding, a Word feature. As you see in the screenshot below (before sanitization), the object is being downloaded from the link.
Data sanitization removes this type of object during the reconstruction process without affecting the document's structural integrity. It will remove the linked OLE object so that no file will be downloaded.
Before Sanitization

After Sanitization

Neutralizing Stages 3 and 4 of the Macro-Less Attack with CDR
The data sanitization process already blocks stage 2, but in theory an attacker could try to utilize stage 3 directly.
The stage 3 document is an RTF file that exploits the CVE-2017-11882 vulnerability targeting the Microsoft Equation Editor. (Microsoft discontinued the Equation Editor in January 2018, but it is still present in older versions of Word.) By exploiting it, an MSHTA command will be executed, and it will download and execute an HTA file.
The HTA file (stage 4) is an HTML application that contains ActiveX controls as part of its VB script, and its code is obfuscated to avoid detection. The script reveals a PowerShell script that eventually downloads and executes a final payload.
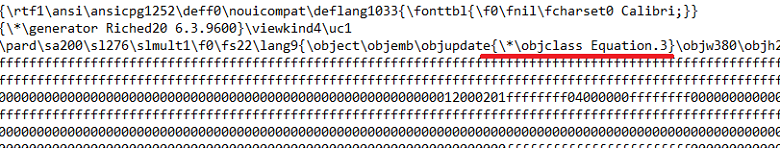
In this case, sanitizing the RTF file would remove the embedded object, as you see in the screenshot below. The exploits are removed whether or not they are detected as malicious content.
Before Sanitization
After Sanitization
Learn more about data sanitization (CDR) here.

