By the OPSWAT Data Sanitization Team
Malicious Word Documents Without Macros
Attackers have used macros in Microsoft Word documents for malware delivery for a long time, starting in the mid-to-late 1990s. To combat this, Microsoft added security features in Office 2003 to stop macros from running automatically; users are required to manually turn macros on to use them. In addition, many contemporary anti-malware programs counteract such attacks.
Though malicious macros are still widely used, more and more hackers are turning to other features of Microsoft Word.
On October 9, 2017, SensePost posted a blog describing how an unwanted program can be triggered to launch automatically when a user opens a Word document without using macros. They can do this by using the Dynamic Data Exchange (DDE) protocol.
DDE was first introduced in 1987 with the release of Windows 2.0 so that one program could communicate with another program. With a few simple steps, SensePost created a sample to demonstrate how DDE could be used maliciously.
The steps are as follows: Under the Insert tab, go to "Quick Parts," and select "Field". In the dialog box that pops up, select "= (Formula)".
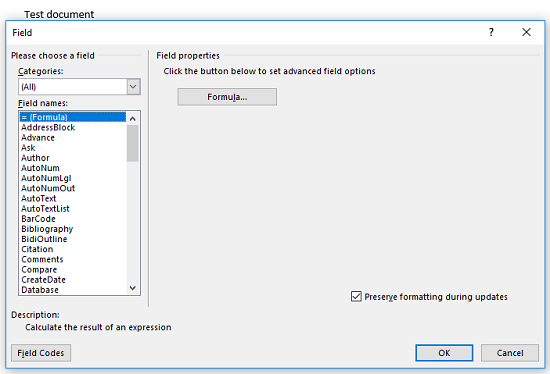
Click image to expand
A Field will appear in the document, displaying the error "!Unexpected End of Formula". Right-click the Field and select "Toggle Field Codes".
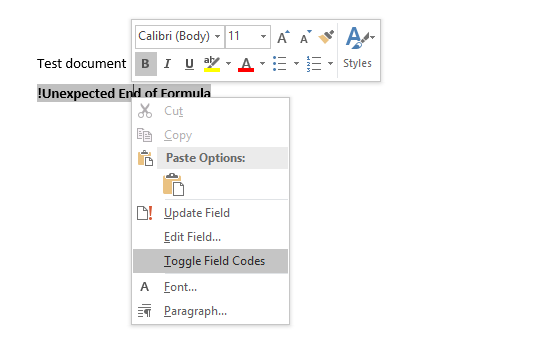
Change the Field Code to:
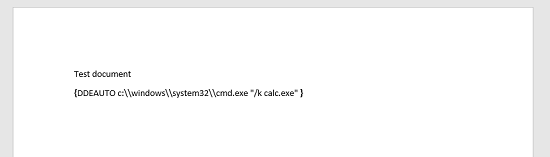
{DDEAUTO c:\windows\system32\cmd.exe "/k calc.exe" }
This particular code will access the Calculator application, but an attacker could use this to access PowerShell, or even a malicious executable.
Click image to expand
Save the document.
Now, when the file is opened, two warnings appear.
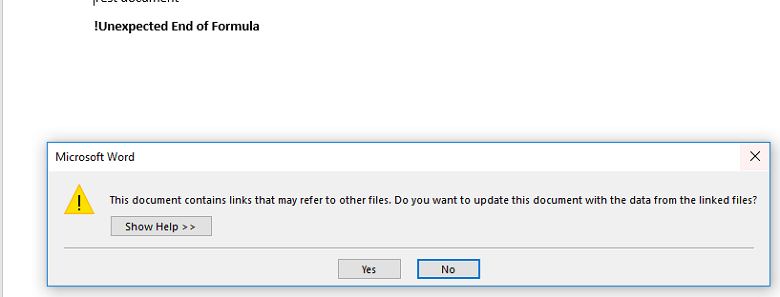
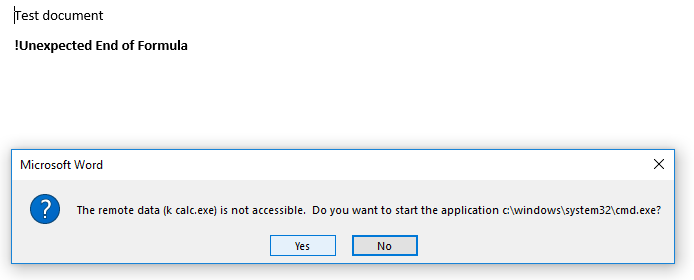
If the user clicks "Yes" to both, then the external program is accessed.
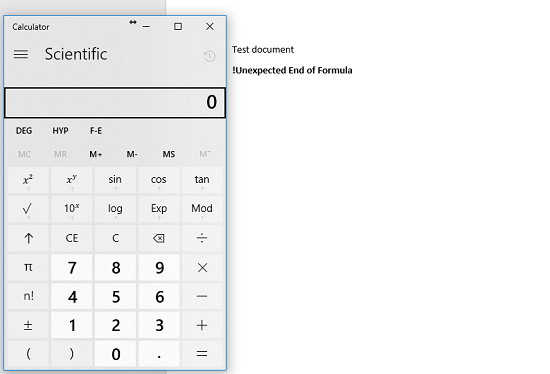
Again, though in this example the document accesses the innocuous Calculator program, attackers can use this method in a number of ways. Note that the code is executed as soon as the document is opened the only defense is the two warning boxes, which non-technical users could very easily ignore.
Additionally, at the time when SensePost described this method, no anti-malware engines detected this file as malicious.
DDE Malware Attacks in the Real World
The DDE attack method has already been used in many real-world attacks. The month of October 2017 saw multiple such attacks.
Necurs Botnet Spreads Locky Ransomware Using DDE
On October 19 Brad Duncan, writing for the ISC, described attacks that spread Locky ransomware via Word documents. Instead of using macros, the malicious files used DDE. The documents were attached to phishing emails (one example simply read "As requested" in the body of the email).
Hancitor Malware Uses DDE
On the 16th, Duncan also described malicious spam that pushed Hancitor malware and used this DDE method.
Freddie Mac Targeted with Word Document Malware
Per Iain Thomson at The Register, DDE attacks hidden in Word documents were used to target Freddie Mac employees. The malicious documents were attached to phishing emails that Thomson described as "well-crafted."
How to Prevent DDE Attacks
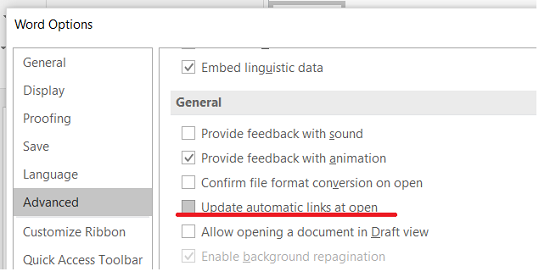
1. Disable the "Update automatic links at open" option in Office programs.
2. Be careful with warnings that may indicate another program is attempting to execute or is requesting outside resources that need unusual permissions to run.
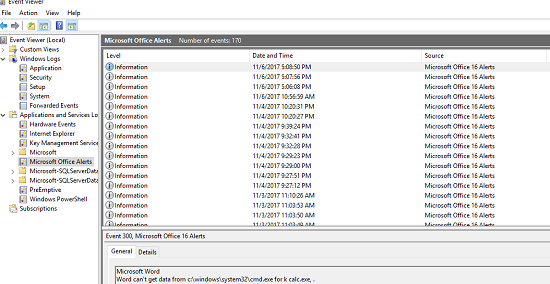
3. Check the Windows Event Log to see if Microsoft Office launched something.
Click image to expand
OPSWAT's Data Sanitization (CDR) Removes DDE
The best defense against document malware attacks is to remove potential threats altogether, eliminating the possibility of human error, social engineering, or unforeseen exploits triggering a malware outbreak. To avoid triggering a DDE attack through user error, the ultimate solution is to remove DDE threats from files via data sanitization (CDR).
OPSWAT is a leader in CDR (Content Disarm and Reconstruction), and we aim to stop document-borne malware attacks of all kinds. As soon as the DDE threat became widely used, we started developing functionality to detect and sanitize it. OPSWAT data sanitization technology now can detect DDE code in DOCX and XLSX files and remove it.
In the demo video below, we used MetaDefender Core V4 with 20 scan engines and data sanitization to process the above test file. Five out of 20 anti-malware engines detected the file as malicious, the DDE code was removed completely by data sanitization, and the sanitized file was opened safely without any security popups or any external applications launching.
As of this writing, OPSWAT's CDR is among the first to sanitize DDE.

