Earlier in September 2023, OPSWAT launched the Graduate Fellowship Program, offering graduate students a unique opportunity to study and address real-world cybersecurity vulnerabilities affecting critical infrastructure systems.
To highlight the outcomes of The OPSWAT Graduate Fellowship Program, we are excited to introduce a series of technical analysis blogs focusing on various Common Vulnerabilities and Exposures (CVEs), identified and mitigated with our advanced threat detection technologies.

In this blog, we will explain the RARLAB WinRAR CVE-2023-38831 and how organizations can defend against CVE-2023-38831 exploitation attacks.
Background on CVE-2023-38831
- WinRAR, a widely adopted file compression and archive utility supporting various formats, boasts a user base exceeding 500 million worldwide.
- RARLAB WinRAR versions preceding v6.23 were recently identified as zero-day vulnerability by Group-IB, actively exploited by cybercriminals since at least April 2023 in campaigns targeting financial traders.
- NVD Analysts assigned a CVSS score of 7.8 HIGH to CVE-2023-38831, officially designated by MITRE Corporation on August 15, 2023.
WinRAR Exploitation Timeline

WinRAR Vulnerability Explained
OPSWAT Graduate Fellows conducted a thorough analysis of the exploitation of the CVE-2023-38831 vulnerability, which impacts WinRAR versions preceding 6.23. The malicious content encompasses various file types and is contained within the ZIP file.
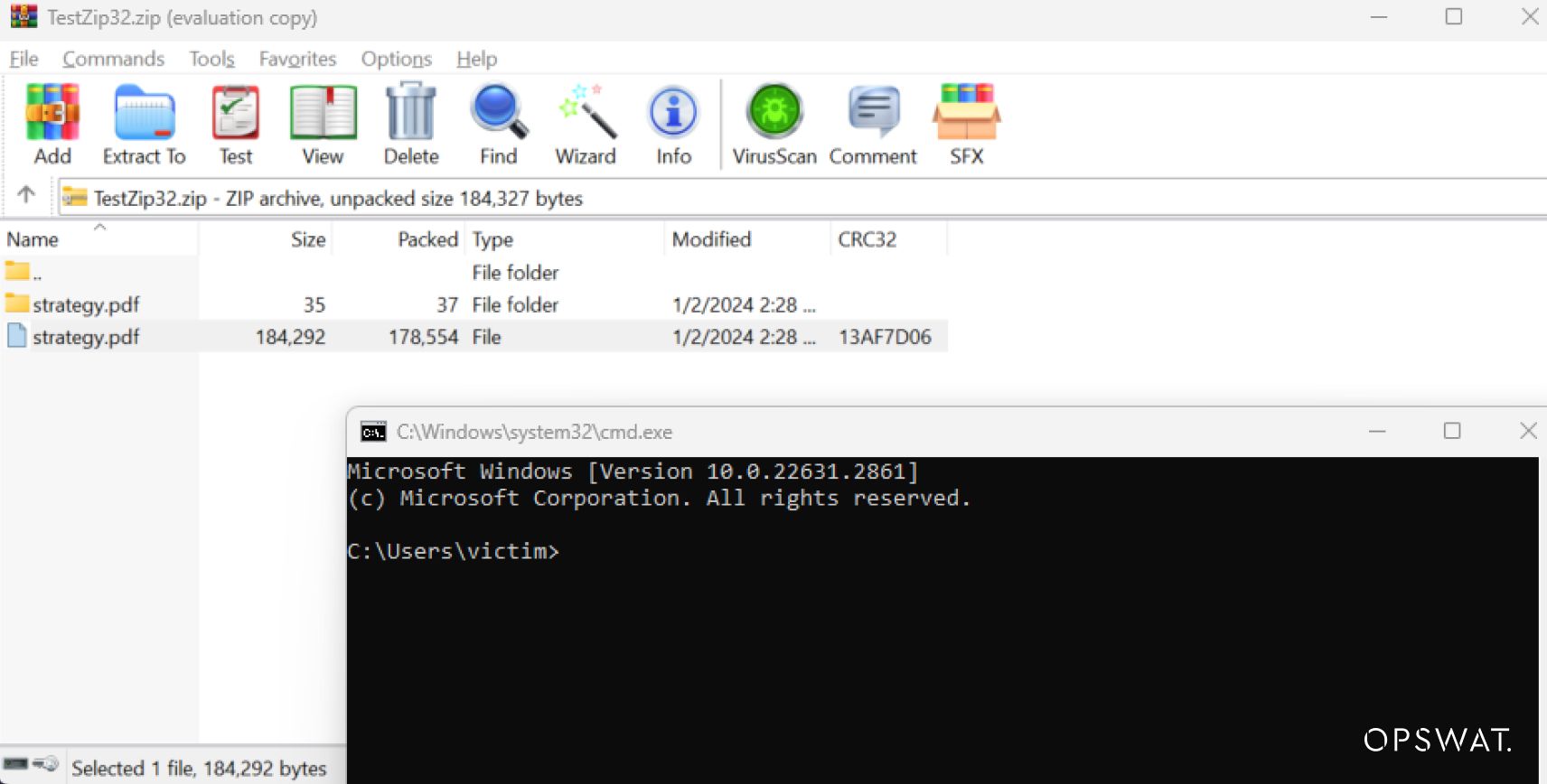
To exploit CVE-2023-38831, threat actors create a malicious zip file containing harmful files within a folder that mimics the name of a harmless file.

Both the harmless file and the folder have a space as their last character. The malicious file will be placed in a folder whose name closely resembles the harmless file.
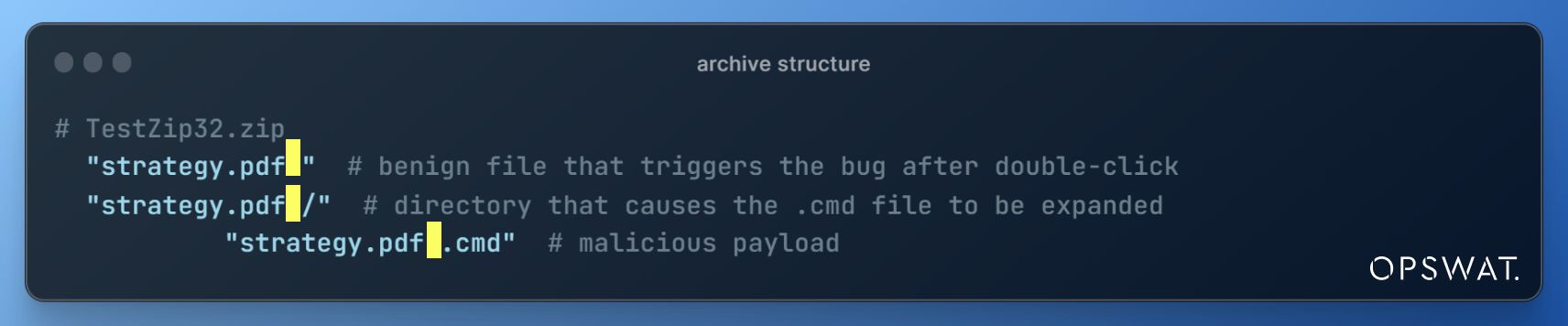
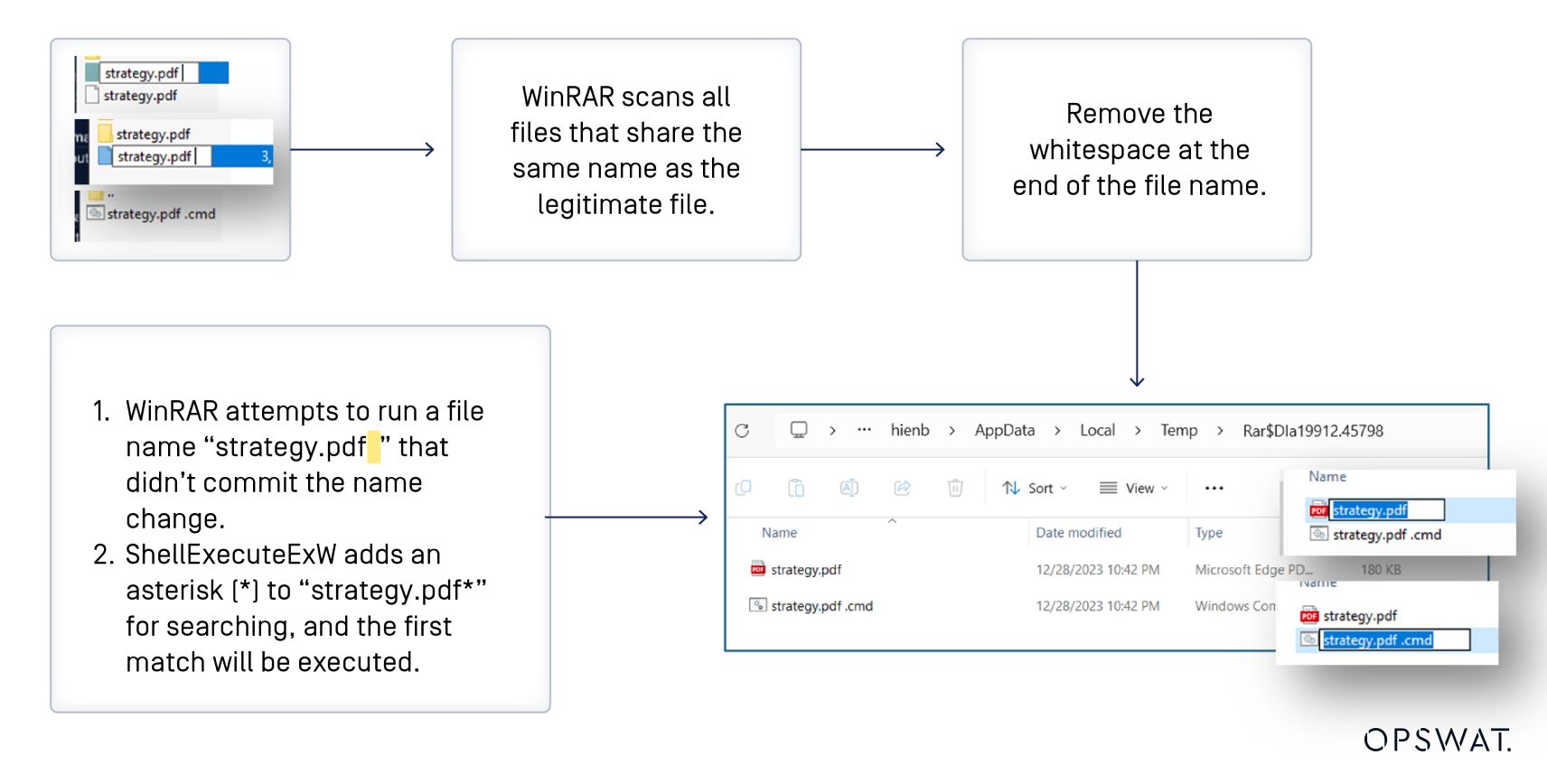
When users try to open the benign file “strategy.pdf ” using WinRAR, WinRAR proceeds to extract all files sharing the same name as the target file, depositing them into a temporary directory within the %TEMP% path.
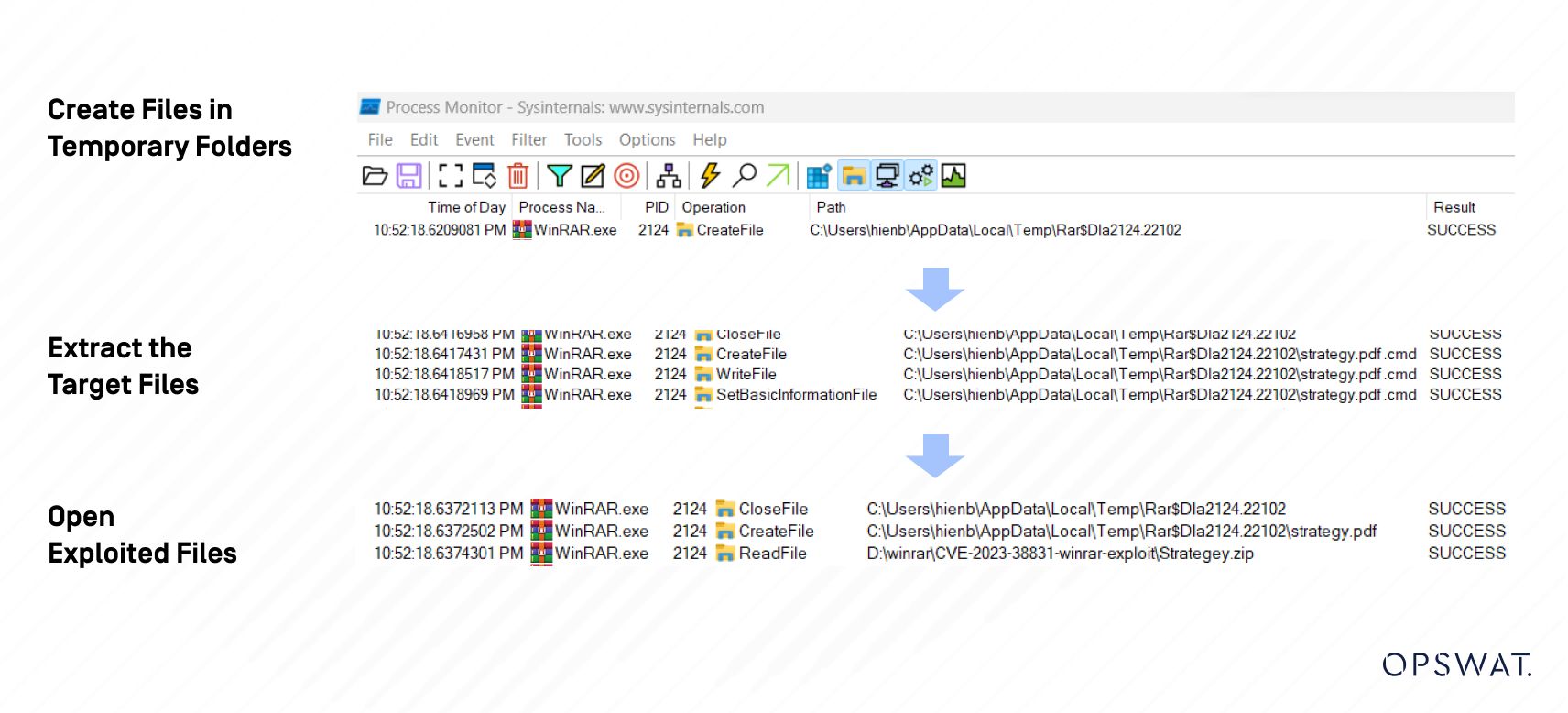
If a directory shares the same name as the selected file, extracting it will result in both the selected file and the files within that directory being extracted to the temporary folder.
The following pseudocode illustrates WinRAR's extraction logic and determines whether an archive entry should be extracted.
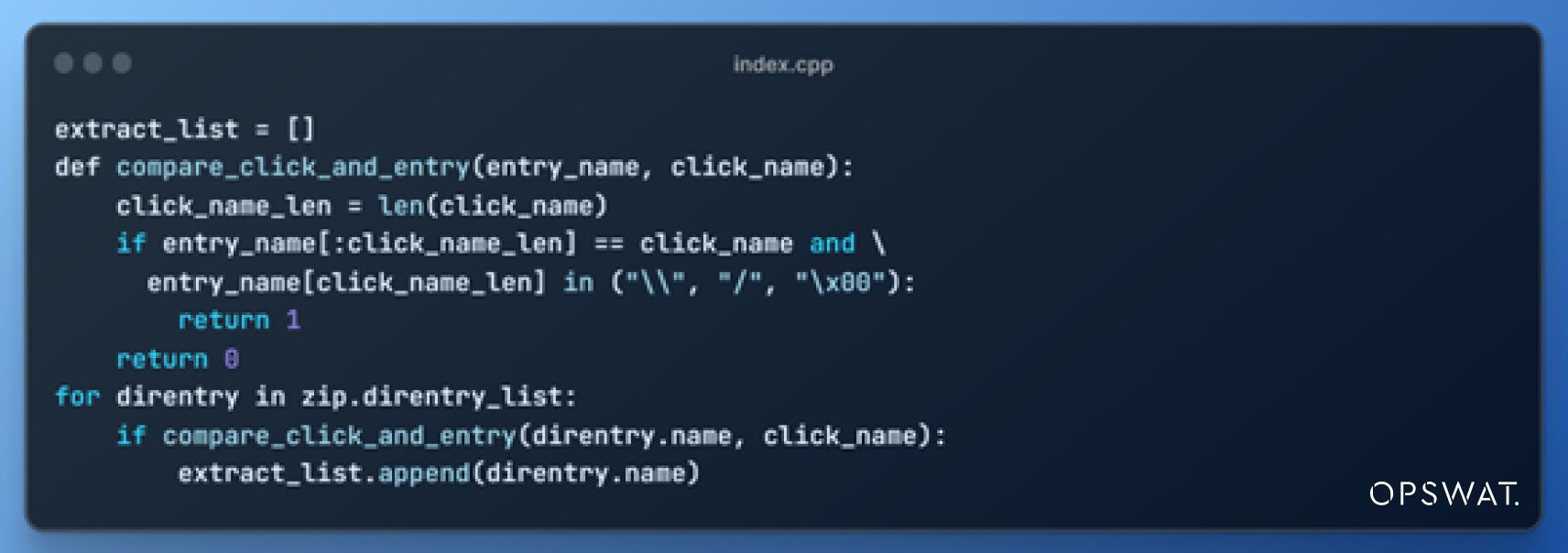
During the file content writing process, WinRAR adjusts file paths by eliminating any added spaces through a procedure known as path normalization.
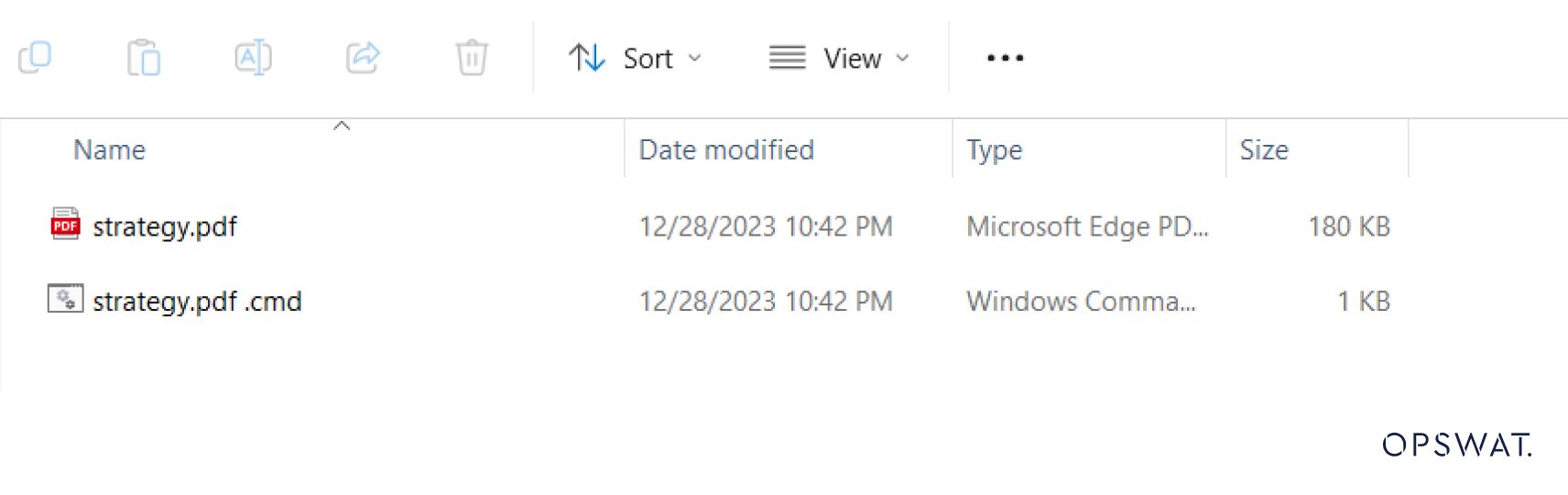
After extraction, WinRAR triggers file execution via ShellExecuteExW. However, the function uses a non-normalized path as input. The last space character is misinterpreted as an asterisk, leading to the execution of the “strategy.pdf ”.cmd file instead of the originally selected file.
Simulation and Detection with OPSWAT MetaDefender
The proof of concept (POC) for CVE-2023-38831 has been available for some time now, and threat actors are actively exploiting it in current campaigns. To simulate the CVE-2023-38831 vulnerability, OSPWAT Graduate Fellows utilized the MetaDefender Platform, providing real-world insights into threat detection.
Exploitation Mechanics
Everyday users face a significant risk from cyber threats, especially as information-sharing channels continue to expand. Malicious actors often take advantage of this vulnerability by disguising harmful elements within downloadable files, like ZIPs, which carry embedded malicious links. Another common tactic involves email phishing, where users receive harmful attachments sent to their email addresses.
Exploitation Flow
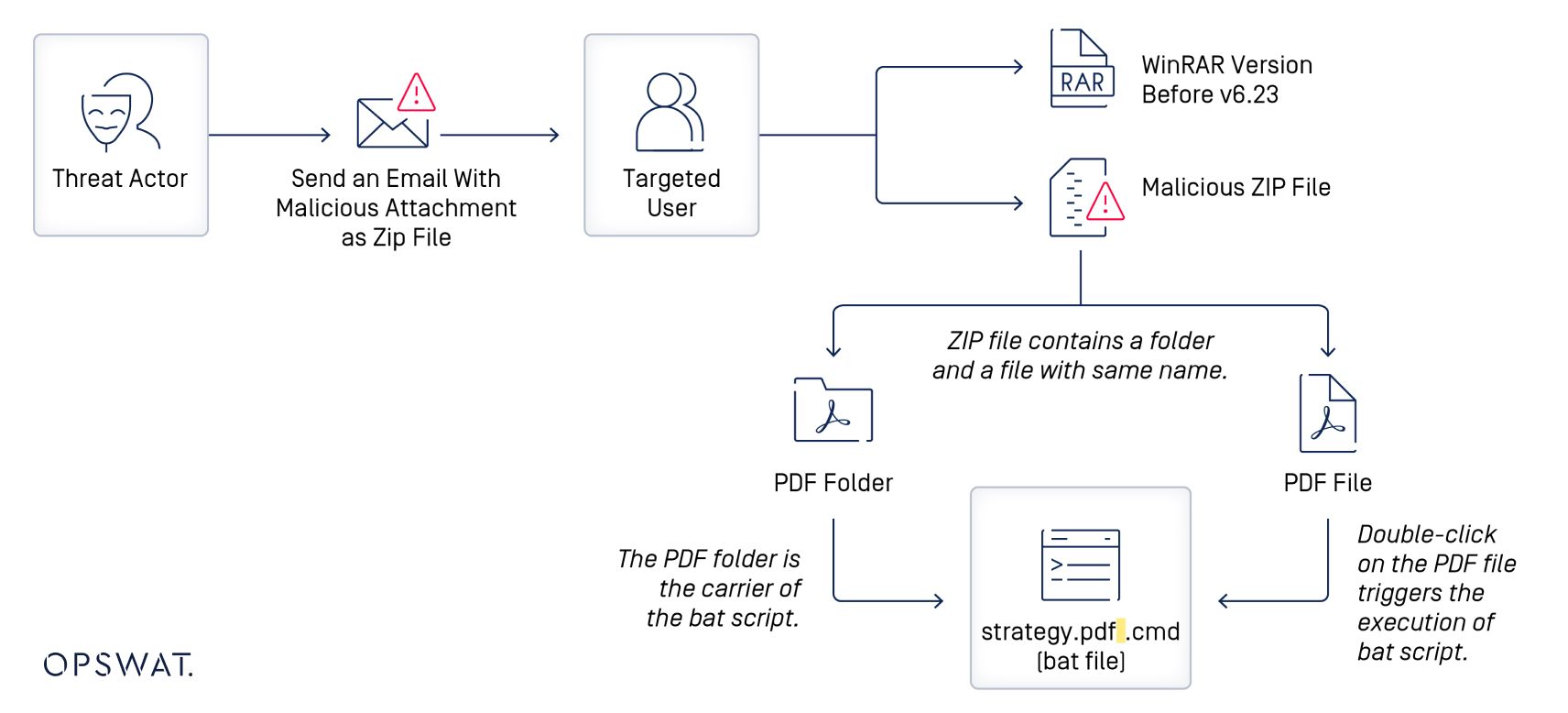
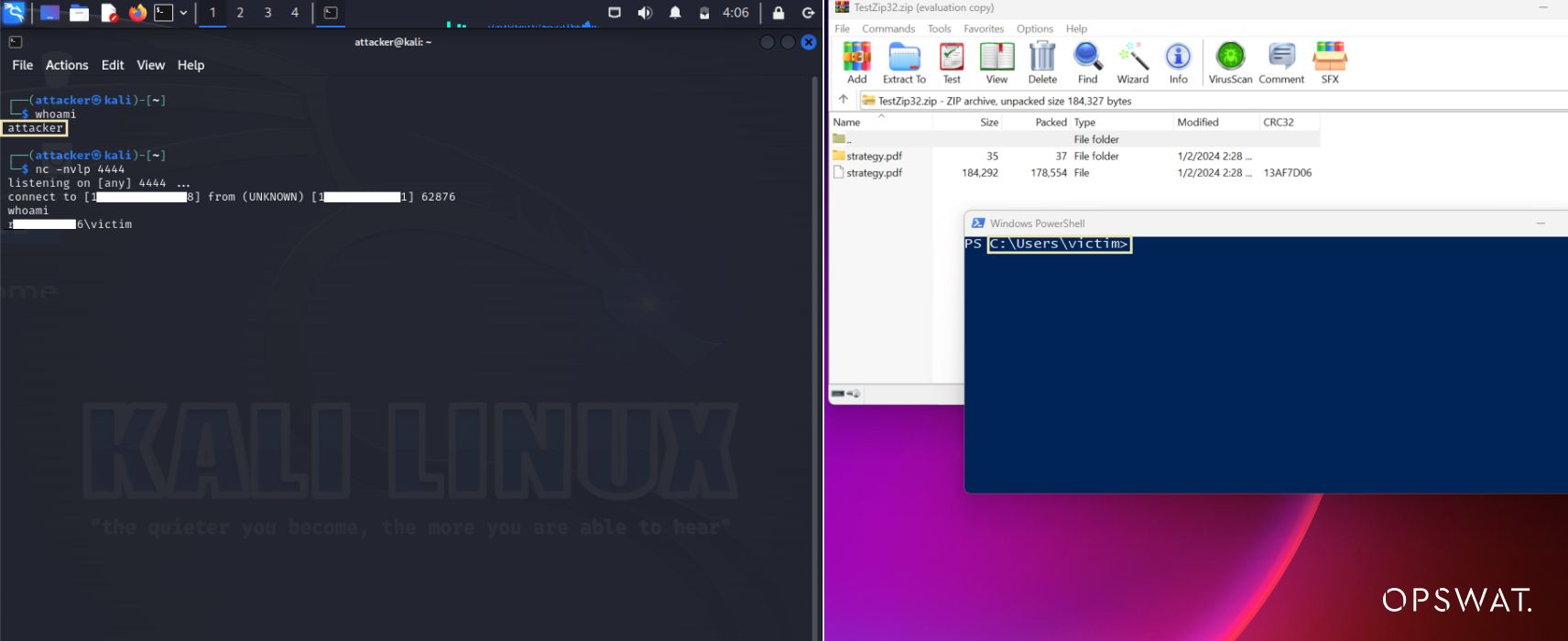
When users double-click to open the file, it activates malicious code, leading to the creation of a reverse shell that connects back to the threat actor. Once a connection is successfully established, the attacker can then exploit execution commands to fully compromise the victim's device.
Vulnerability Simulation Process
Vulnerability Remediation
There are a few key strategies to remediate this vulnerability.
- Upgrade WinRAR to version 6.23 or later, which properly sanitizes ZIP filenames before extraction to block attacks.
- Configure ZIP filename filters through Group Policy or registry settings as a temporary mitigation before upgrading.
- Scan downloaded ZIP files from unknown sources with antivirus tools before extraction.
- Avoid extracting ZIPs received through unsolicited means like suspicious emails.
OPSWAT Coverage
WinRAR CVE-2023-38831 can be identified and detected with the following solutions:
OPSWAT MetaDefender Core
MetaDefender Core provides comprehensive file upload security to protect against malware and data breaches. OPSWAT designed MetaDefender to secure the world’s critical infrastructure from the most sophisticated file-based threats: advanced evasive malware, zero-day attacks, and APTs (advanced persistent threats).
MetaDefender Core scans and analyzes WinRAR installers using File-based Vulnerability Assessment engine to detect known vulnerabilities before execution on endpoints. To counter spoofed file attacks like CVE-2023-38831, processing ZIP files through File Type Verification is highly recommended. This technology verifies file types based on content, not unreliable extensions. MetaDefender Core also leverages Multiscanning, scanning ZIP files with 30+ anti-malware engines using signatures, heuristics, and machine learning to proactively identify over 99% of malware. This multilayered approach helps swiftly detect malware associated with CVEs.
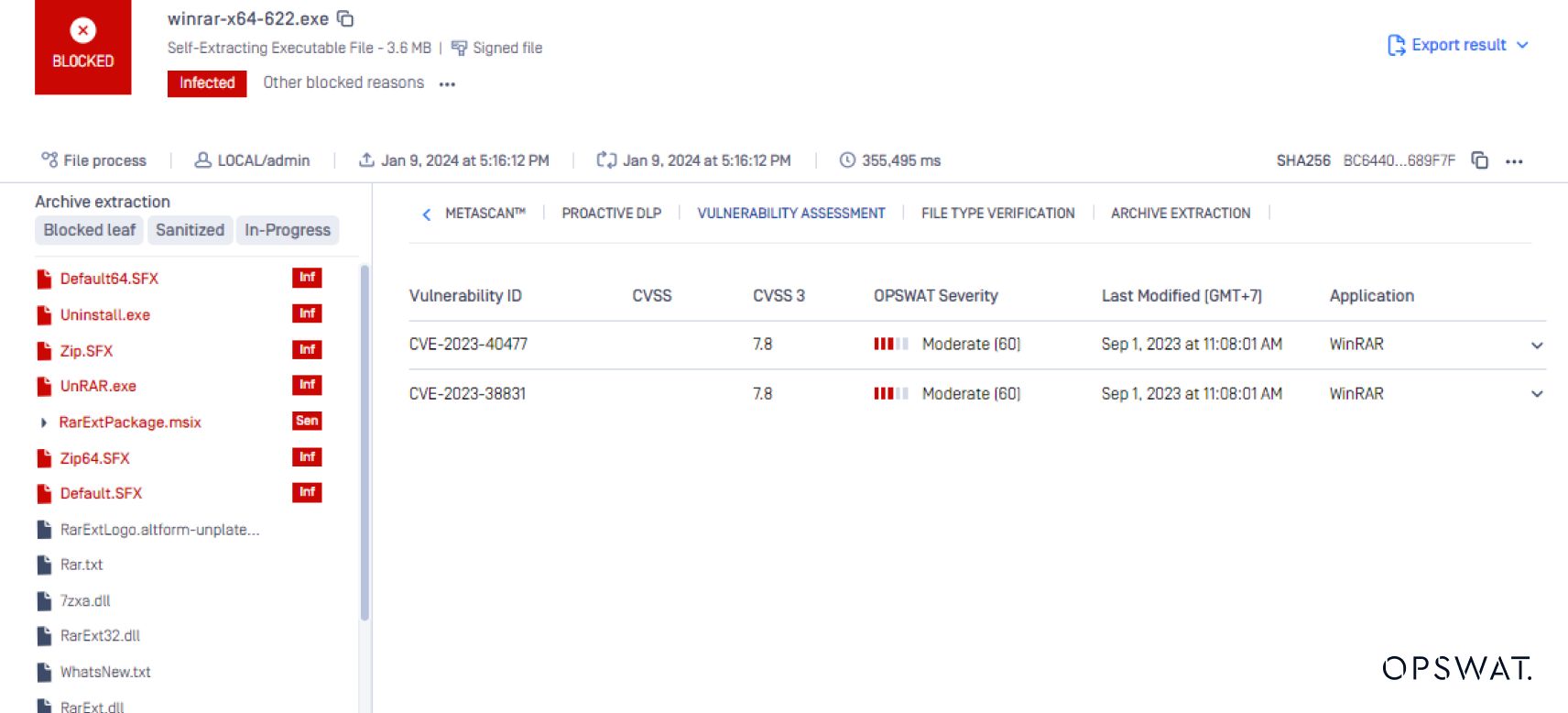
OPSWAT MetaDefender Endpoint
MetaDefender Endpoint detects risky applications and provides remediation options to resolve potential security issues. Ensuring the robust security of your organization requires dedicating ample time to patching. Vigilantly seeking indicators of attacks and promptly identifying signs of exploitation attempts or intrusion is pivotal. The OPSWAT MetaDefender Endpoint stands as an asset in your toolkit, facilitating the patching and updating of vulnerabilities, such as WinRAR, to the latest version.
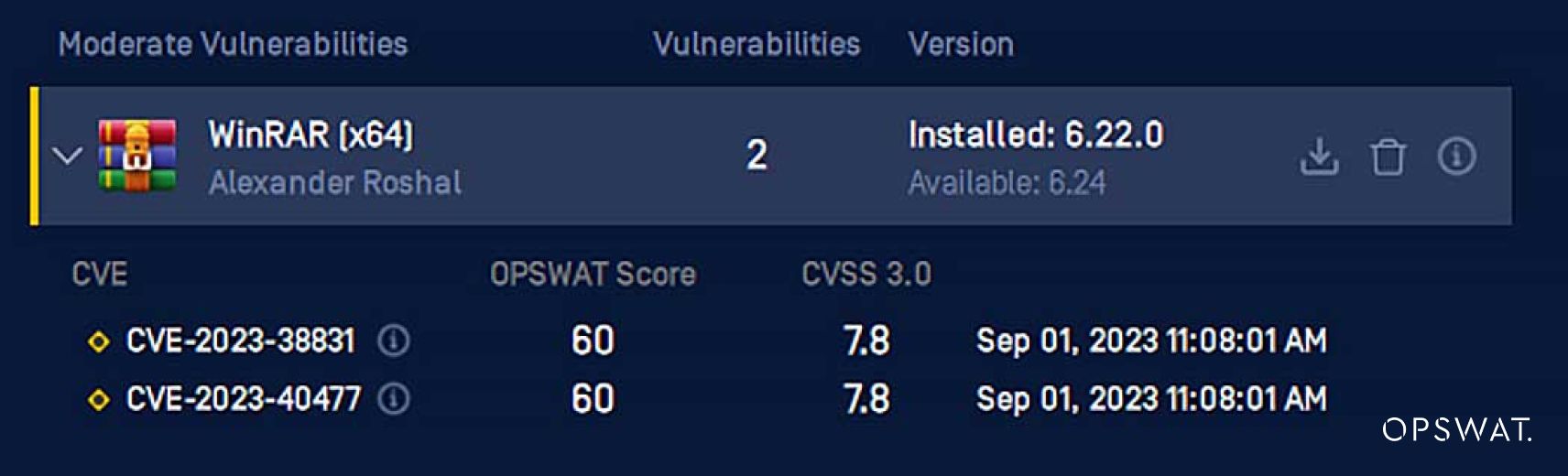
Final Thoughts
The CVE-2023-38831 vulnerability demands immediate attention due to WinRAR's widespread use and ease of exploitation. Early detection is crucial and OPSWAT MetaDefender offers advanced threat detection and mitigation capabilities. As cybersecurity professionals, staying updated, implementing robust security measures, and fostering a culture of cybersecurity awareness are paramount.
For more CVE simulation projects from OPSWAT Graduate Fellowship Program, subscribe and explore our latest blog covers.

