As organizations move toward a hybrid storage model, both on-premises and in the cloud, the complexity and vulnerability of those file systems is also increasing. More complexity means more points of entry and a broader attack surface for threat actors, which is why organizations must apply the right security measures and avoid misinformation to ensure their assets are protected.
In this blog, we’ll debunk some common data storage security myths and shed light on the realities of safeguarding your valuable information.
Myth #1: Data Stored in the Cloud is Automatically Secure
Most data breaches affect assets stored in multiple environments, including cloud and on premises. Breaches of this type are more difficult to identify and take longer to contain, leading to higher costs and longer service interruptions.

Source: Cost of a Data breach Report 2023, IBM
In this 2023 report, the largest percentage of breaches, 39%, involved data stored across multiple environments, followed by breaches that involved data stored in the public cloud at 27%. The number of breaches occurring across multiple environments surpassed the combined 34% of breaches occurring only in private cloud or on-premises environments.
While cloud storage providers implement many security measures, users must also take steps to ensure safe uploading, downloading, and sharing of files, and security protocols for cloud assets must be implemented for on-premises assets as well because:

Cloud storage solutions are not inherently more secure and are, in fact, more likely to be targeted by threat actors.

Cloud service providers may not be held liable for security breaches due to uploaded files from your external storage systems that introduce hidden, undetected malware.

Offline/on-premises assets that are compromised and added to cloud file systems can then proliferate and compromise other aspects of file synchronization processes.
Myth #2: Antivirus Software is Enough
Antivirus (AV) software is a necessary line of defense, but it's just one piece of the puzzle. Social engineering and zero-day attacks often circumvent this defense strategy, with detection rates ranging from just 7% to 76% for a single AV engine.

To fortify your defenses, consider layering additional security measures like Multiscanning for advanced malware detection, Deep CDR (Content Disarm and Reconstruction) for file sanitization and sandboxing to isolate and detonate suspicious files in a protected environment. This strengthens your security posture by:

Detecting nearly 100% of known threats, as well as unknown threats based on heuristics and suspicious behavior patterns.

Removing all potentially malicious code and regenerating sanitized, safe-to-use files that can’t pose a threat.

Enabling your organization to take preventative measures with in-depth reports and analyses of even the most sophisticated, novel threats.
This multi-layered approach to storage security intercepts nearly 100% of all known and unknown threats, ensuring that no compromised file puts your storage systems at risk.
Myth #3: Cloud Security is Only the Provider’s Responsibility
Cloud providers invest heavily in security, but it’s important to remember that cloud security is a shared responsibility. While providers secure the cloud storage infrastructure, cloud customers are responsible for securing the data they store.
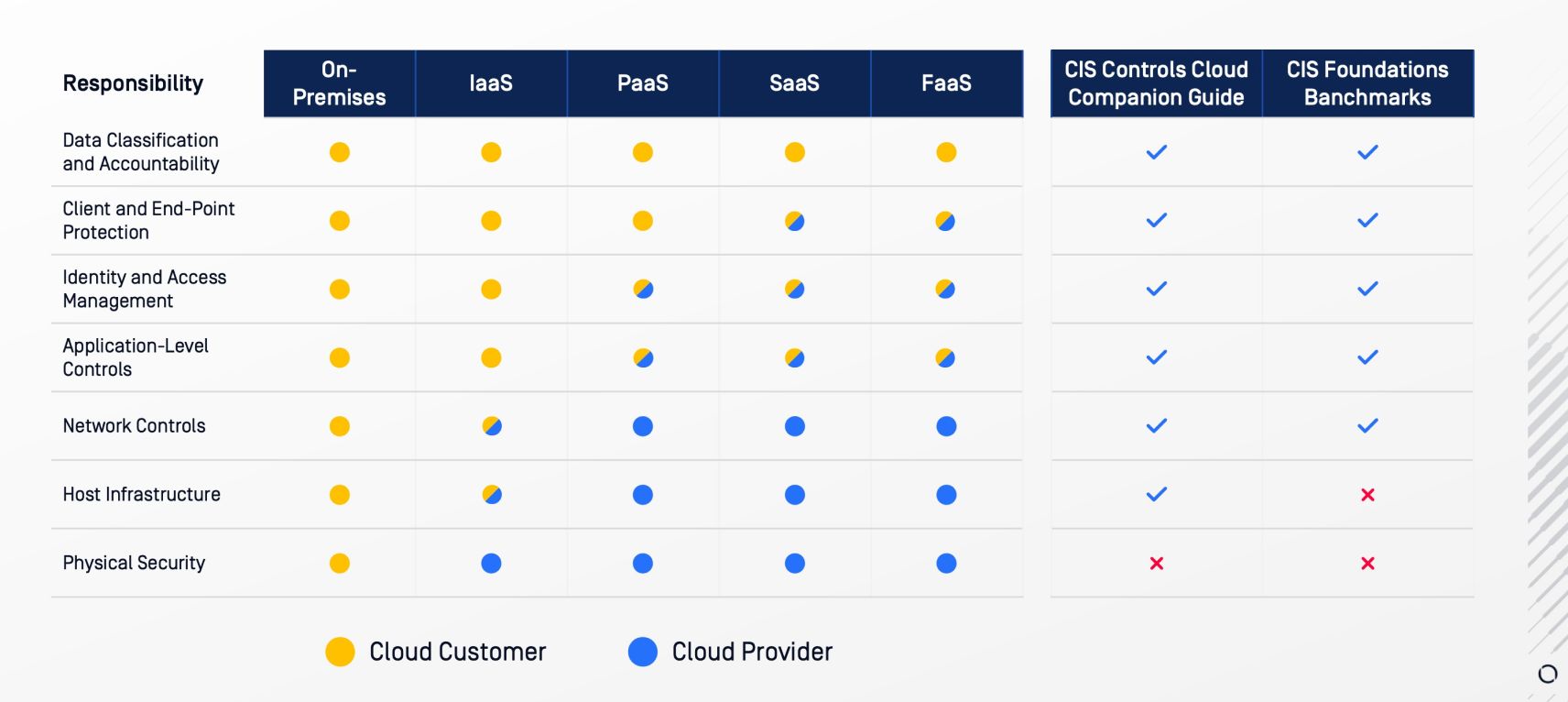
Source: Center for Internet Security
Implementing robust storage security measures, managing user access with the principle of least privilege, and complying with relevant data privacy regulations are crucial steps businesses must take to safeguard their information:

A multi-layered security strategy ensures no file enters your file system without rigorous scrutiny.

The principle of least privilege reduces the likelihood of employees intentionally or accidentally compromising your entire file system by only giving employees access to assets that are specific to their needs, which limits the impact of security breaches to the least privileged level of access possible.

Complying with data privacy regulations, in addition to helping secure your assets, shields your organization from hefty fines and costly audits.
Myth #4: On-premises Compliance is Easier than Cloud Compliance
While some believe using cloud services clashes with industry regulations, this isn't always true. Many cloud providers adhere to frameworks like HIPAA, GDPR, and PCI DSS. They implement robust security controls and offer features that aid customers in meeting compliance obligations.
However, it's critical for organizations to thoroughly assess a cloud provider's compliance capabilities in order to shield themselves from huge fines and costly audits in the event of a data breach. Ensuring alignment with these regulations is essential before migrating sensitive data.
Proactive DLP (Data Loss Prevention) technology can be a powerful supporting shield. This technology helps safeguard your data from regulatory or out-of-policy violations by setting up rules to govern how data is accessed, used, and shared within storage environments. Proactive DLP automatically intercepts and obscures this information to ensure no sensitive data is shared or accessed erroneously by unauthorized employees or stolen by threat actors for ransomware attacks.

Fortify Your Data Storage with MetaDefender Storage Security's Multi-Layered Protection
MetaDefender Storage Security offers a robust layer of protection for on-premises and cloud storage. It protects enterprise-stored data from data breaches and downtime, and aids in meeting compliance standards.
MetaDefender Storage Security leverages multiple OPSWAT technologies like Deep CDR, Multiscanning, and Proactive DLP to protect stored files, documents, and images from zero-day attacks, advanced threats, and sensitive data loss.

MetaDefender Storage Security offers enterprise-class features tailored for scalability and ease of integration into existing workflows. Its intuitive GUI and RESTful API interface enable seamless incorporation into diverse operational setups. Moreover, features like file tagging and automated remediation aid in rapid content classification and identification of malicious files for further analysis or forensic examination.
Conclusion
By debunking data storage security myths and implementing MetaDefender Storage Security, you can safeguard your valuable information with confidence.
Contact us today to learn more about how OPSWAT can help you achieve comprehensive data security and protect your business from ever-evolving threats

