With the increasing importance of data privacy, security, and efficient resource allocation, file type detection is a critical yet often overlooked challenge for organizations. Artificial Intelligence (AI) is revolutionizing file type verification, a core component of the MetaDefender Platform, as it can detect spoofed files using machine learning. This enables increased detection accuracy while operating at much higher levels of efficiency than traditional static scanning solutions.
File Type Spoofing Techniques
While changing a file extension (e.g. .exe to .txt) was a common tactic in the past, security solutions have grown adept at recognizing such basic tricks. This has led attackers to more elaborate methods. Modern file type spoofing goes beyond simple extension manipulation. Attackers can manipulate the internal structure of a file to mimic a legitimate file type.
The true challenge for attackers lies not just in disguising the file, but also in tricking the user into executing it. Social engineering tactics often come into play here. Attackers might disguise the file with a familiar icon or name, luring the user into opening it. Alternatively, they might exploit vulnerabilities in software that allow automatic execution regardless of the perceived file type.
In some cases, spoofed files can even be part of elaborate, multi-stage attacks. A seemingly harmless file could download or install the real malicious payload on the target system.
File type spoofing poses a significant risk because it bypasses traditional signature-based detection methods that rely on pre-defined patterns of malicious code. This deceptive technique can be used to distribute various threats, including ransomware, Trojans, and worms.
Why Accurate File Type Detection Matters
Consider file filtering, a cornerstone of organizational security. By accurately identifying file types, organizations can effectively block malicious files. This protects from inbound threats like malware, while also enhancing privacy by preventing the outbound flow of sensitive information. Additionally, filtering out non-essential files like entertainment media optimizes resource utilization. This is especially important in healthcare, where HIPAA regulations mandate strong patient data protection to safeguard digital healthcare data from cyberattacks. Reliable file type detection forms the backbone of successful file filtering compliance.
The importance of file type detection extends beyond file filtering. Virus scanners often leverage it to prioritize scans. By efficiently identifying file types historically not associated with viruses, scanners can focus their resources on high-risk files, expediting the detection of malicious threats.
Accurate file type detection plays a vital, behind-the-scenes role in various security and data management practices including:

Traditional security software relies on signature-based detection, which identifies threats based on known patterns. However, this approach is ineffective against zero-day threats, which are novel attacks unknown to security software. Accurate file type detection offers a crucial advantage in such scenarios. By analyzing the internal structure of a file, it can identify suspicious files based on characteristics that deviate from expected patterns for a particular file type. This allows for the flagging of potentially malicious files, even if they haven't been encountered before.

Accurate file type detection enables security systems to prioritize threats more effectively. Instead of wasting resources on analyzing every single file, systems can focus their efforts on those identified as potentially risky based on their file type. This allows for a more streamlined approach to security, where legitimate files are processed quickly, and resources are directed towards analyzing suspicious files for further investigation. This ultimately improves the overall security posture of an organization by ensuring that threats are identified and addressed promptly.

Knowing the true nature of a file allows systems to handle it correctly. Different file types require different processing methods, parsing techniques, and storage allocations. Accurate file type detection ensures that files are handled appropriately, preventing malfunctions and vulnerabilities that could arise from misidentified files. For instance, attempting to execute a malicious script disguised as a harmless image file could lead to a security breach. Accurate file type detection helps prevent such scenarios by identifying the true nature of the file and preventing improper execution.

Many regulations, such as HIPAA and PCI DSS, mandate specific controls for data security. Accurate file type detection is a crucial element in complying with these regulations. It helps organizations identify and classify sensitive data, implement appropriate security measures for different file types, and ensure the secure storage and transmission of data. This reduces the risk of data breaches and regulatory non-compliance.
Three Main Methods of File Verification
| Method | Pros | Cons |
| File Extension | Fast and Easy: Checks the file extension for quick identification. Universally applicable on most operating systems. | Easily Deceived: Attackers can simply rename malicious files with harmless extensions. Limited for non-standard extensions and unreliable for Linux/Unix where extensions are optional. |
| Magic Bytes | More Reliable: Relies on specific byte patterns (magic bytes) for identification, offering better accuracy than extensions. Can identify binary files that lack extensions. | Limited Coverage: Only works for file types with defined magic bytes. Not all file types have them. Vulnerable to attackers altering magic bytes for spoofing. Inconsistent information from different sources can cause confusion. |
| Character Distribution Analysis | Uncovers Deception: Analyzes the actual content to reveal the true file type, potentially exposing hidden malware disguised with a harmless extension. Provides valuable insights into the type of text file (e.g., plain text vs. code). | Computationally Costly: Requires reading and analyzing the file content, making it slower than other methods. False alarms are possible for unique or irregular file content. Limited effectiveness for binary files lacking a distinct character distribution. |
How OPSWAT Leverages AI to Accurately Detect File Types
For enhanced accuracy and security, OPSWAT File Type Verification technology goes beyond these traditional methods by leveraging MetaDefender Core’s workflow, which combines them into a uniquely powerful and efficient filtering process. It reduces processing time while achieving the highest possible accuracy.
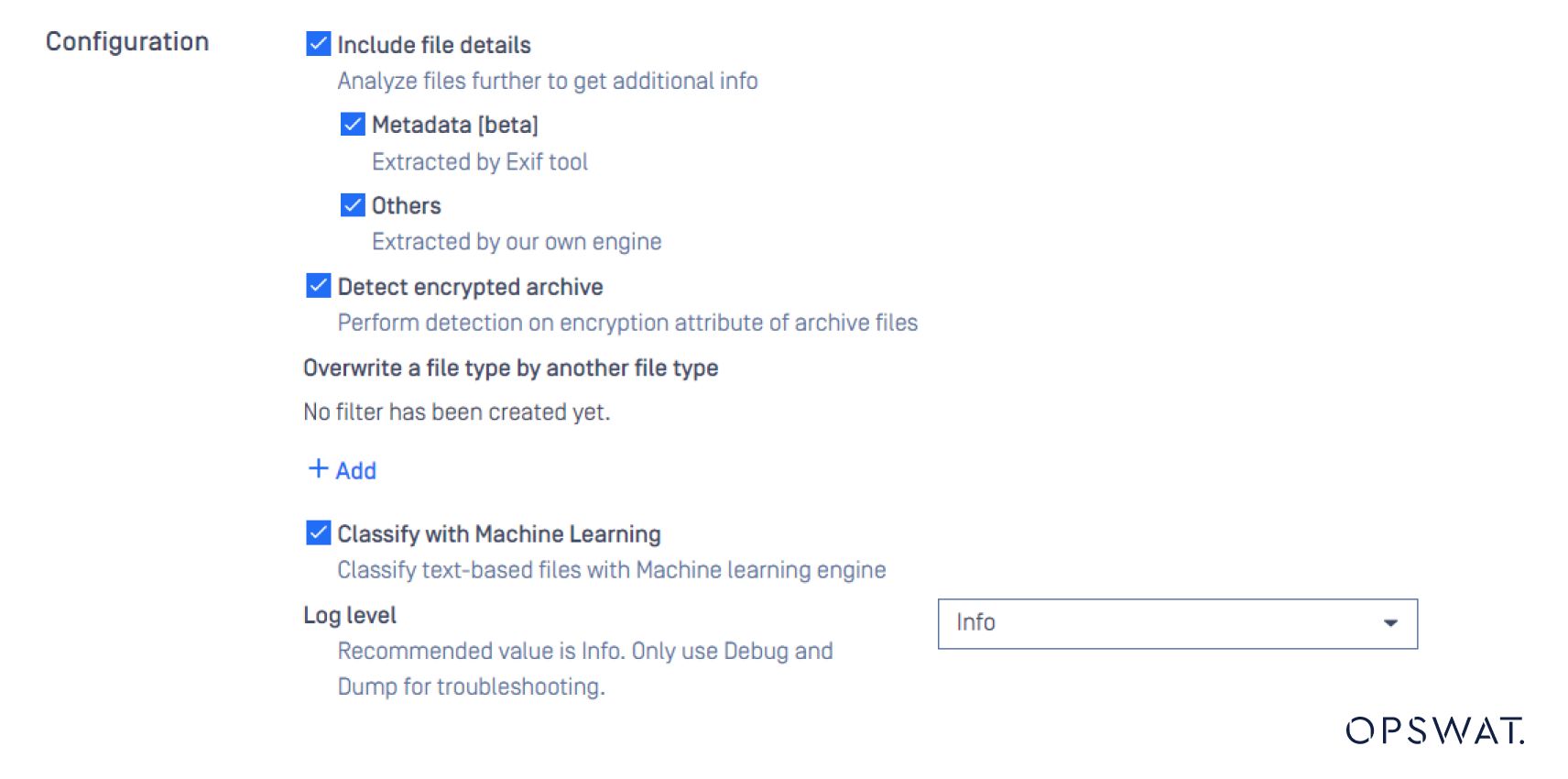
We've also recently added machine learning detection specifically to address the challenge of text-based files. These files, such as log files, script files, and readme files, are all simply "text" and lack distinct characteristics revealed by other methods. Analyzing the contents is crucial for accurate classification. Misclassifying a text-based file can be dangerous, as a malicious script file could be allowed to run undetected.
Configuring text-based file type verification in MetaDefender Core.
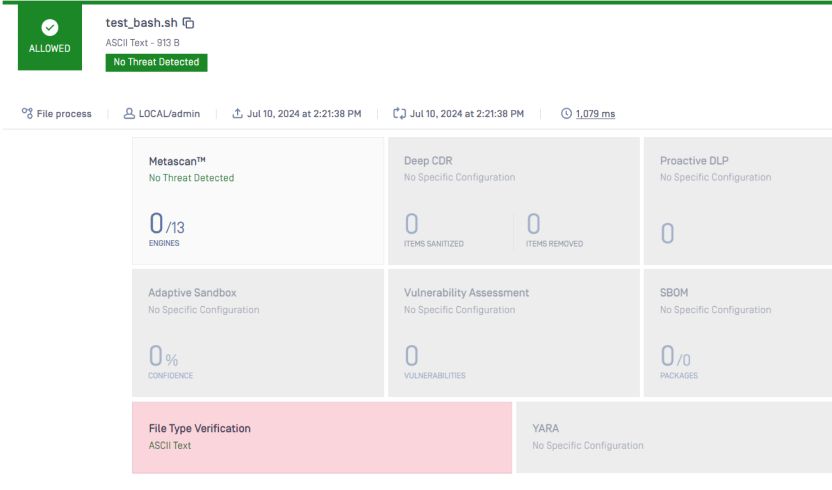
Let’s look at this example to see how it works.
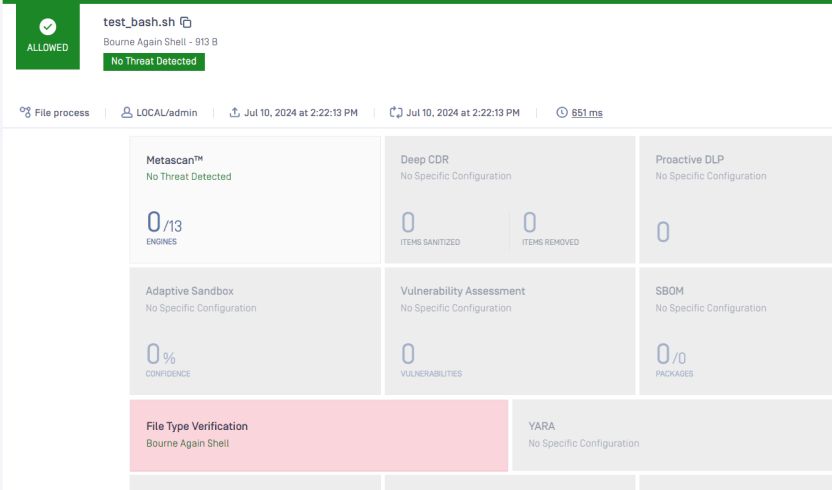
See the comparison with and without AI in detecting file types.
Interestingly, we can modify the shell file to have a short description on the top as shown in the sample below.
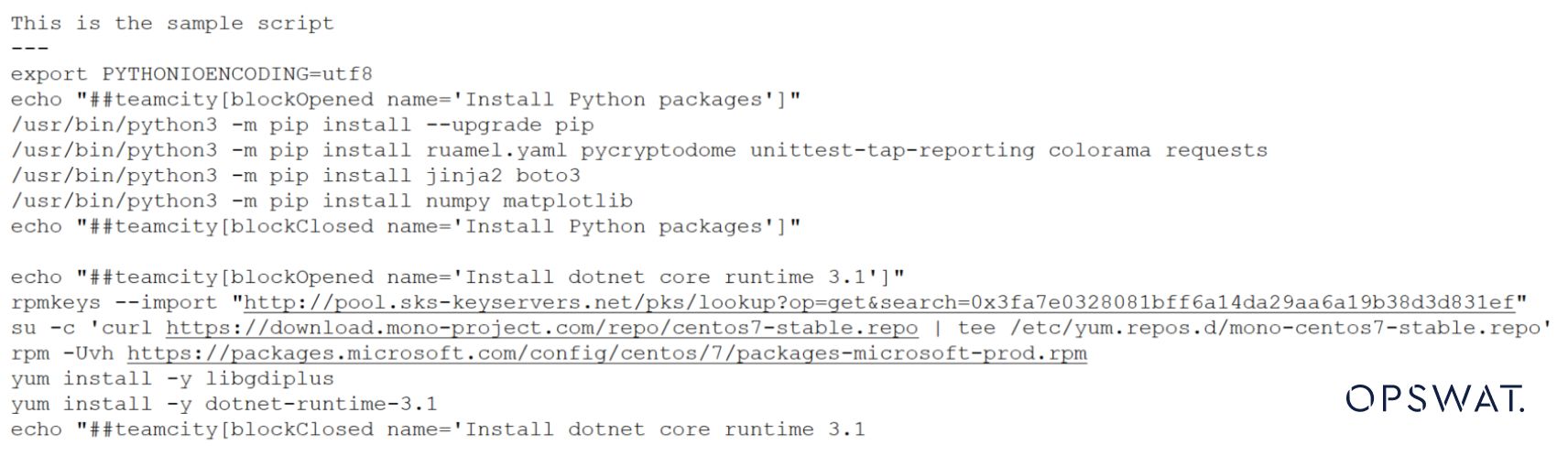
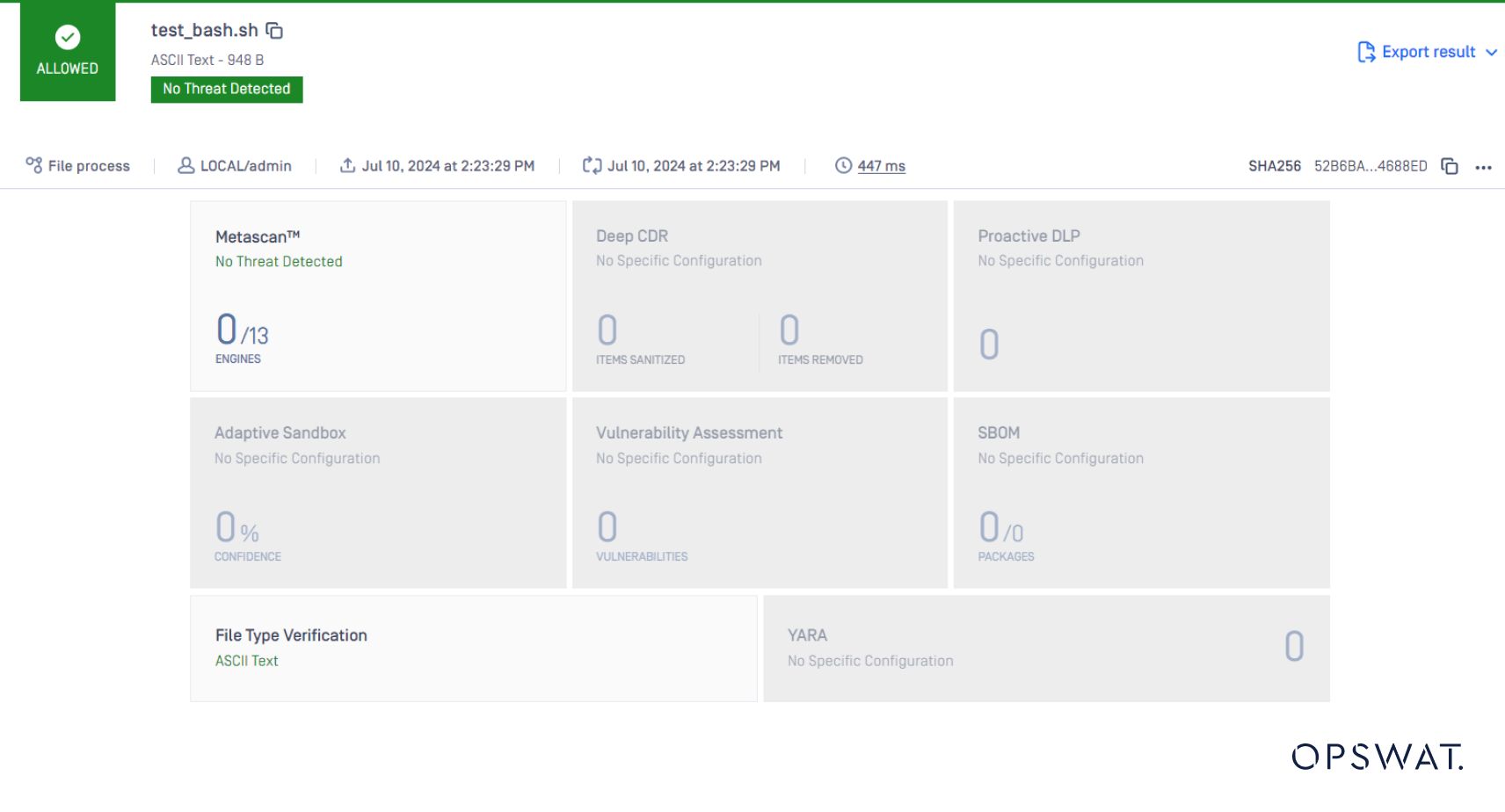
The file type will detect it again as text, which is true. It is no longer a script.
If we comment out those two lines but still keep it there as shown in the below image.
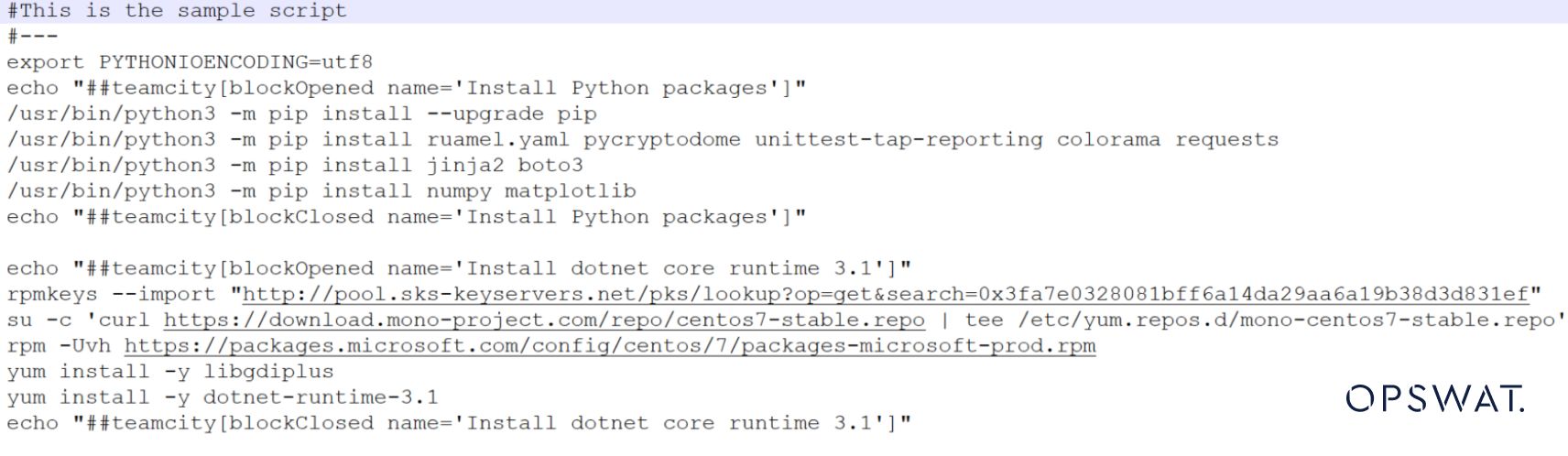
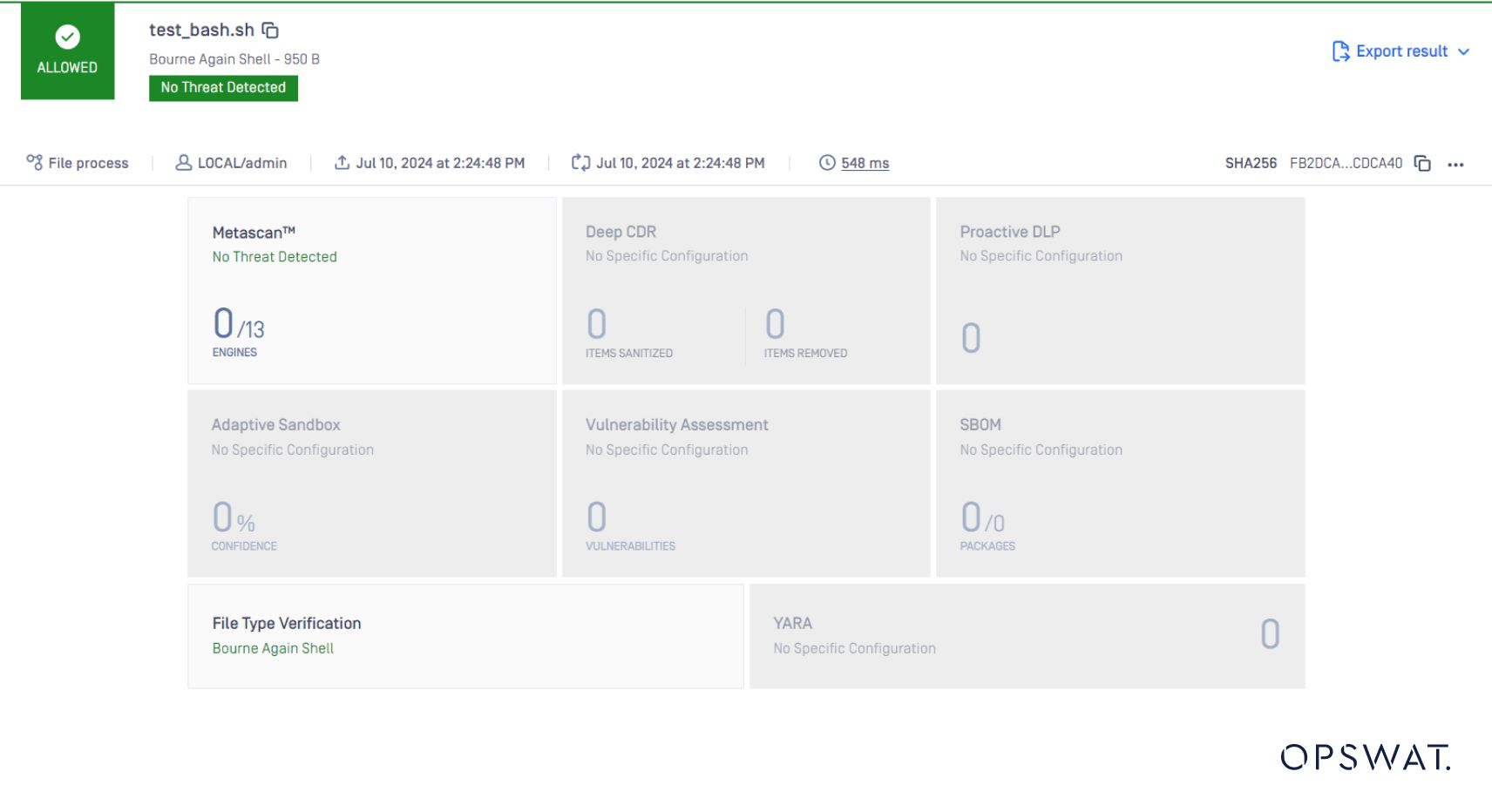
The file type should be:
By leveraging deep learning for text-based file analysis, OPSWAT File Type Verification achieves:
- Enhanced accuracy - AI models can identify even the most sophisticated file type spoofing attempts, especially within text-based files.
- Future-proof security - The ability to adapt to new threats ensures continuous protection.
- Improved efficiency - Accurate detection reduces the need for manual analysis, saving time and resources.
Closing Thoughts
While accurate file type detection forms a critical first line of defense, OPSWAT File Type Verification with AI enhancement empowers businesses to further strengthen their security posture. By leveraging this advanced solution alongside other security measures like file-borne malware prevention and sensitive data protection, companies can achieve a multi-layered defense that safeguards their organizations from file-type spoofing threats and data breaches.
For more information, talk to our cybersecurity experts.