Securing File Transfers in Isolated Operational Environments
The utility sector continues to face persistent cyberthreats, including targeted malware, ransomware, and zero-day exploits, particularly where OT (operational technology) systems must ingest data from external sources. According to IBM’s X-Force Threat Intelligence Index, energy utilities were the fourth most targeted industry in 2024.
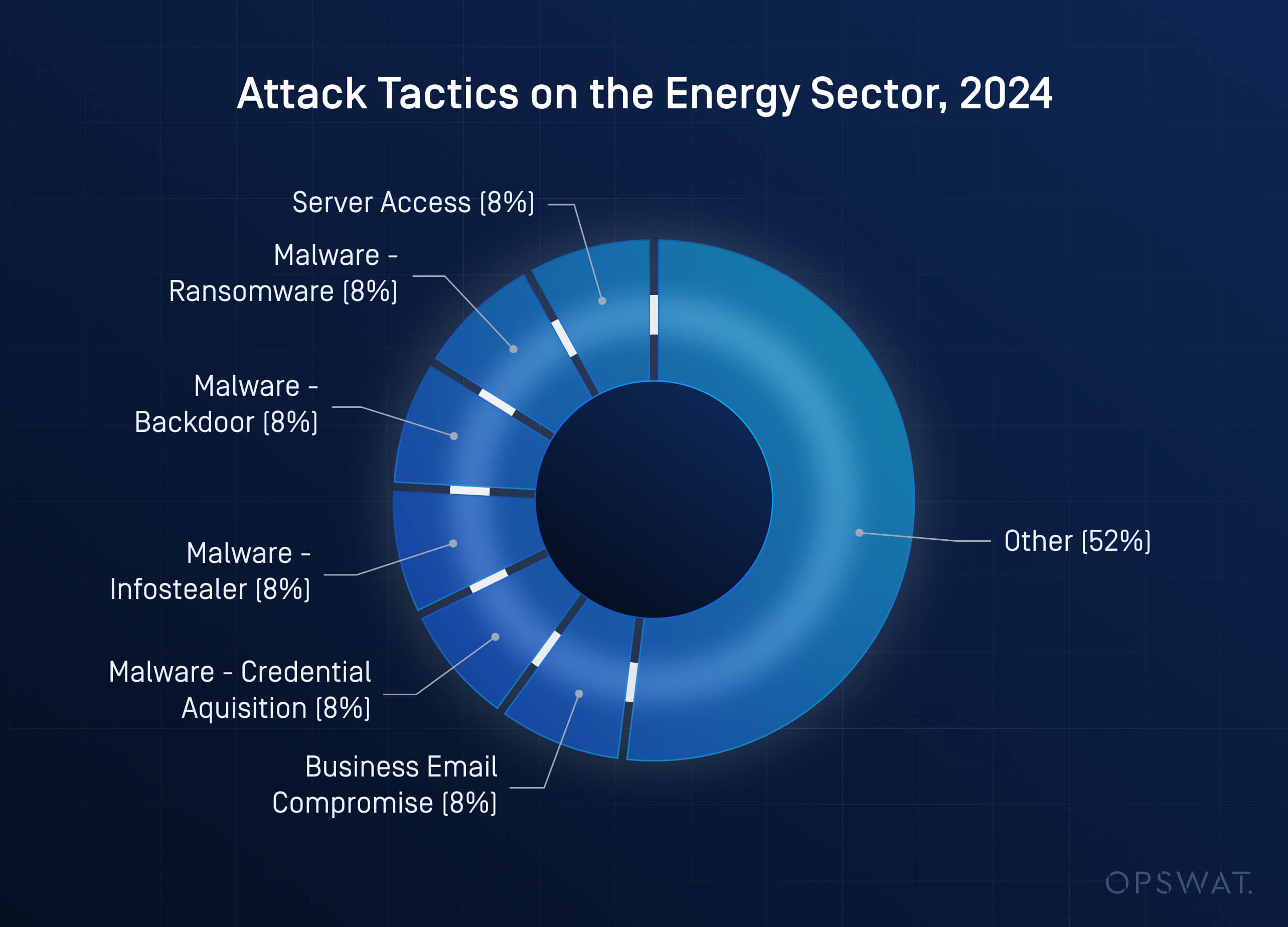
As utility operations become increasingly digitized, the need to process external files—such as diagnostic reports, patch files, and system updates, without exposing internal assets, has become a core requirement. These transfers often involve third-party vendors and portable media, such as USB drives, which carry a high risk of malware infiltration and compliance violations if not properly controlled.
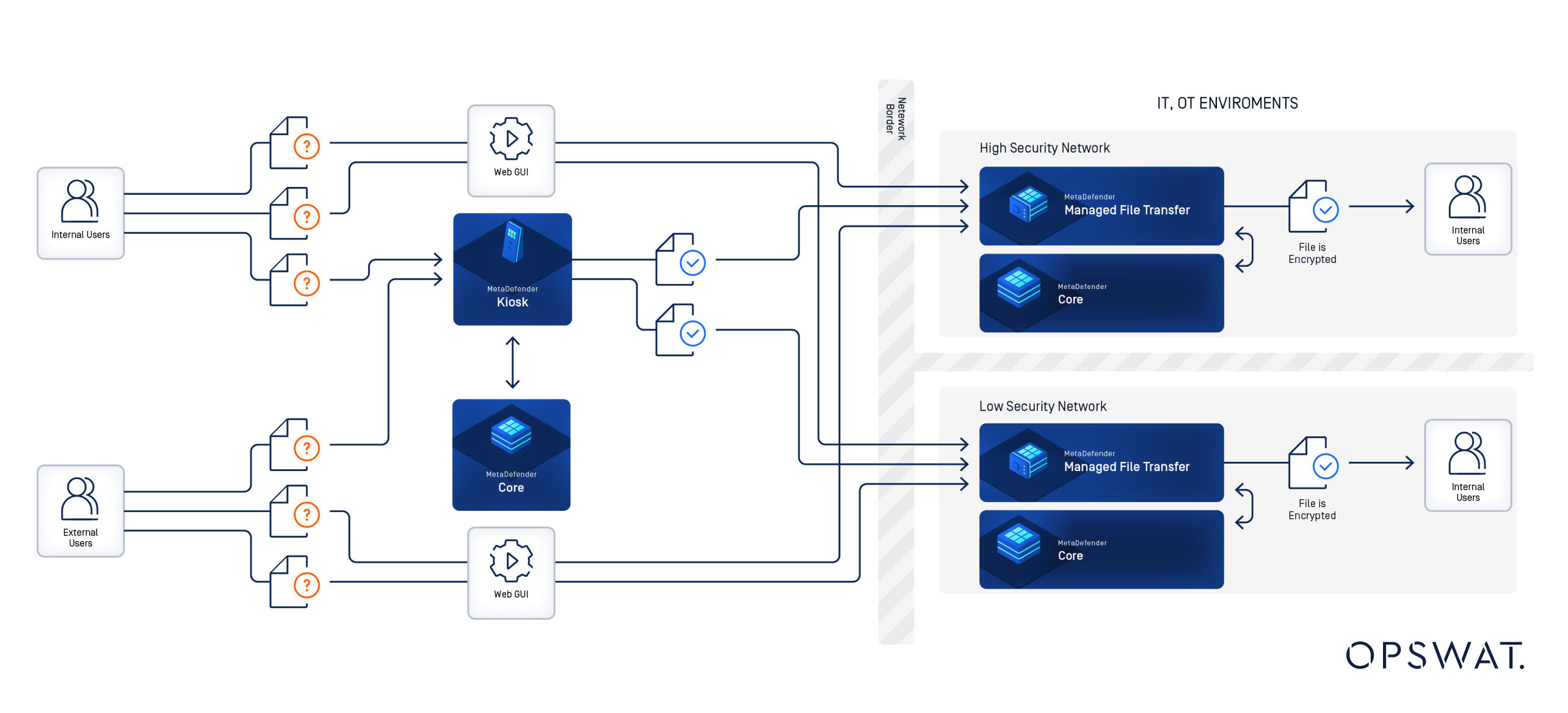
To mitigate these risks, the company adopted a segmented architecture that keeps file transfer processes entirely contained within their respective trust zones. MetaDefender Managed File Transfer (MFT) (MFT) and MetaDefender Core were deployed in both low-security (external-facing) and high-security (internal) environments. Each environment operates independently, with no direct connectivity between zones. Files are now scanned and processed according to zone-specific security policies, ensuring that external submissions do not bypass internal safeguards.
Enforcing Policy-Based File Uploads from Internal and External Sources
The company’s operational processes require a secure intake of files from both internal engineering teams and external contractors. These files can include system diagnostics, patch packages, or update payloads that must be introduced into protected OT environments without compromising internal systems.
Prior to adopting MetaDefender solutions, these transfers often relied on manual procedures and ad hoc tools, including shared drives, unsecured file transfers, and physical media handoffs. USB-based deliveries in particular lacked standardized scanning procedures, creating the risk of malware introduction and inconsistent policy enforcement.
To address this, the organization deployed MetaDefender Managed File Transfer (MFT) and MetaDefender Core scanning engines in both low- and high-security environments. File submissions – whether from USB devices via MetaDefender Kiosk or MetaDefender Managed File Transfer (MFT) authenticated web interfaces (WebGUI) – are handled independently within each zone with policy-enforced uploads for USB and network-originating files.
MetaDefender Kiosk provides an upload station for scanning removable media before it enters the network, while web-based uploads are restricted to authenticated users through locally managed accounts. All files are scanned according to zone-specific rules, including content tagging and deep threat inspection using MetaDefender Core. This ensures that submissions are processed securely, without exposure to shared infrastructure across zones.
This structure enables the company to maintain complete operational separation between low- and high-security networks, while still allowing file uploads where needed. It also ensures full audit logging and traceability for all uploads, user actions, and policy decisions, enabling consistent enforcement of internal policy and helping meet audit and compliance requirements.
OPSWAT’s Solution: MetaDefender Managed File Transfer (MFT) in Segmented Environments
The company selected OPSWAT’s MetaDefender Managed File Transfer (MFT) after identifying the need for file transfer technology capable of operating securely in segmented network environments. A basic requirement was to enable secure file uploads within each environment, whether from internal users or external suppliers, while maintaining strict separation between low-security and high-security zones.
The solution was deployed as two fully independent environments. One instance of MetaDefender Managed File Transfer (MFT) and MetaDefender Core was installed in the low-security zone, and a separate instance in the high-security zone. Each instance operates autonomously, applying its own security policies and scanning workflows to all incoming files.
MetaDefender Kiosks were installed at key upload points to enable secure transfer of USB media. These Kiosks act as controlled upload stations, allowing users to scan and submit files without direct access to internal networks. Web-based uploads are also supported, with users authenticated through locally managed accounts. This ensures secure submission without exposing internal directory services.
By enforcing segmented, policy-controlled file workflows and layered threat detection in each environment, the company established a secure and auditable process for handling external and internal files. Files are never transferred between zones, and thus trust boundaries are never crossed while still enabling operational file delivery wherever needed.
3 Key Capabilities Delivered by OPSWAT Technologies

File Scanning
All submitted files through MetaDefender Kiosk or the MetaDefender Managed File Transfer (MFT) WebGUI are subject to multiple layers of threat detection. Files are scanned within the receiving environment using MetaDefender Core, which applies both signature- and behavior-based analysis to identify and block known and unknown threats. Scanning policies can also identify sensitive file types, such as national-interest (SNI) content, to ensure appropriate handling under regulatory frameworks.

Zone-Specific Authentication
External users submit files through the MetaDefender Managed File Transfer (MFT) WebGUI using local accounts managed independently within each environment. This provides zero-trust access control through local user authentication without Active Directory integration. All user actions are audit-logged with full attribution to specific identities, supporting accountability and traceability.

Automated File Routing
Approved files are automatically routed to predefined storage locations within each zone (such as designated SMB shares) according to policy, reducing manual handling risks and ensuring controlled delivery paths. This reduces manual effort, eliminates the risk of human error, and ensures that only vetted files are delivered into operational environments. All transfers are logged, and any exceptions trigger policy-defined responses.
Together, these controls allow the company to maintain strict isolation between security zones while still enabling operational file uploads and processing under consistent governance.
Building Resilience Through Segmented, Policy-Driven File Uploads
By adopting a layered, policy-controlled approach to file transfers, the company has significantly reduced its exposure to file-borne threats while maintaining strict operational boundaries between trust zones. MetaDefender Core enforces deep content inspection, whether files originate from USB devices scanned at a Kiosk or are submitted through the MetaDefender Managed File Transfer (MFT) WebGUI.
Each zone processes files independently, ensuring that no file movement occurs across security boundaries. This segmentation strategy, combined with automated workflows and detailed audit logging, allows the organization to meet internal security policies and regulatory expectations without compromising operational flexibility.
As the threat landscape evolves and OT environments remain high-value targets, this architecture provides a future-proof foundation for secure, traceable file handling, regardless of where the files originate.
To explore how MetaDefender Managed File Transfer (MFT) can help your organization enforce secure, auditable file uploads and transfers within segmented environments, talk to an expert today.





