Secure File Uploads
Organizations that offer customers and partners the ability to easily upload files realize the benefit of unrestricted file workflows. Fortified with multi-layered technologies and fine-tuned policy controls adapted to your file workflow needs, OPSWAT solutions stop threats before they are uploaded to your web applications and file systems.
File Upload Security Risks
Malware
File uploads can introduce malicious software into a system, potentially compromising data integrity and security.
Targeted Attacks
Cybercriminals may exploit file upload vulnerabilities to gain unauthorized access to a system or launch sophisticated attacks on specific targets.
Resource Exhaustion Attack
Large or numerous file uploads or archive bombs are designed to overwhelm a system’s resources by creating a denial-of-service condition with the potential to crash the system.
Personally Identifiable Information (PII)
Regulations like GDPR require organizations to protect user-uploaded PII from unauthorized access by implementing restrictions and deleting data upon request.
Compliance Regulations
Compliance standards like PCI and HIPAA mandate organizations to protect sensitive data, including credit card information and personal health information, to prevent unauthorized access and potential breaches.
The OPSWAT Solution
Stop Threats That Others Miss
- Supports 200+ file formats
- Recursively sanitize multi-level nested archives
- Regenerate safe and usable files
More Engines Are Better Than One
- Detect nearly 100% of malware
- Scan simultaneously with 30+ leading AV engines
Detect Evasive Malware with Advanced Emulation-Based Sandboxing
- Analyze files in a high-speed
- Anti-evasion sandbox engine extracts IOCs
- Identify zero-day threats
- Enable deep malware classification via API or local integration
Enhance Detection with Real-Time Threat Intelligence
- Correlate global IOCs, IPs, URLs, & file reputation across 50B+ artifacts
- Stop emerging threats faster
- Enrich downstream analysis
Seamless Deployments
Deploy via an extensible REST API and a native connector-enabled platform that seamlessly integrates with your existing file upload web application and security infrastructure.
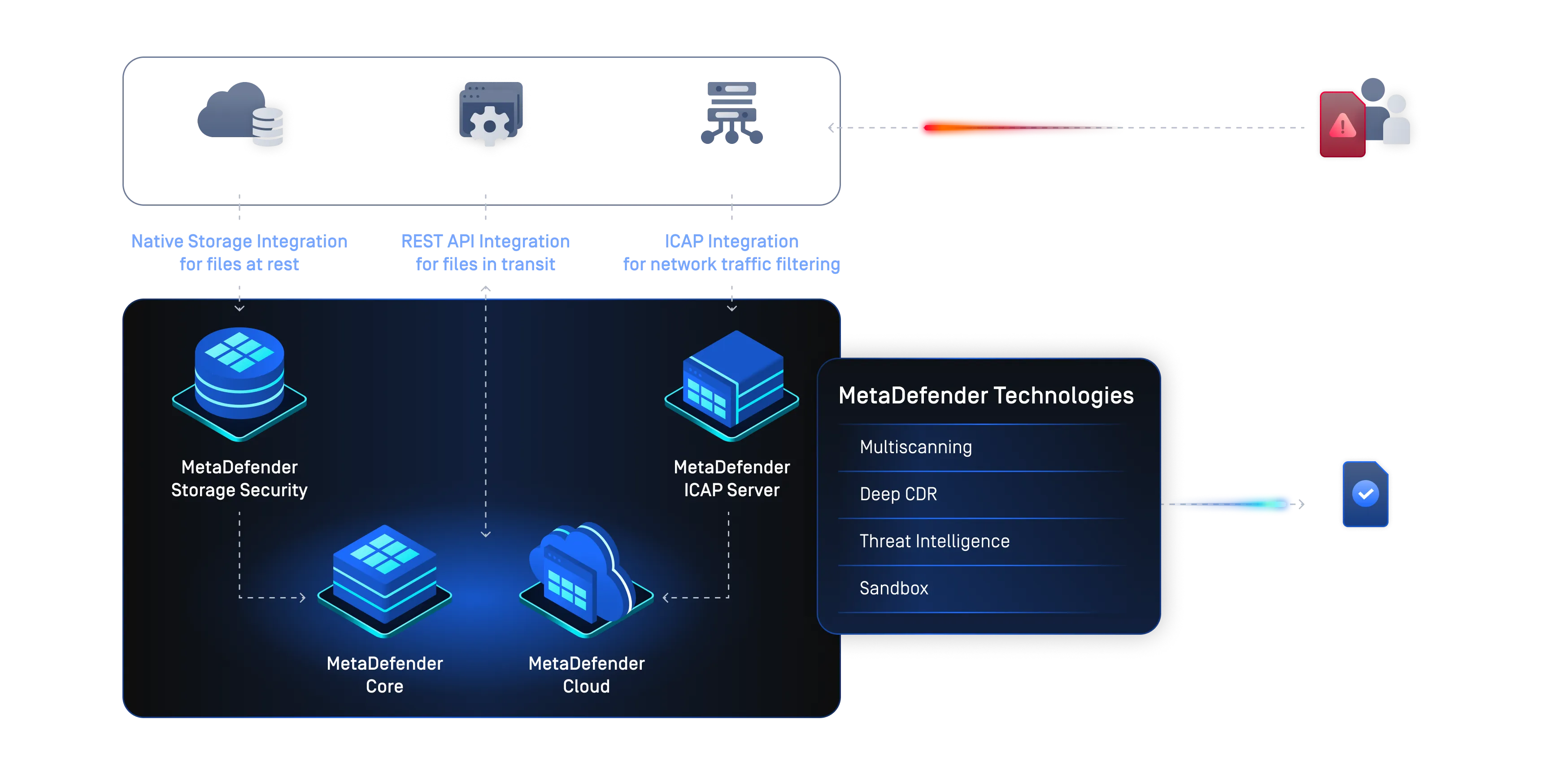








Configuring MetaDefender for File Uploads
MetaDefender Workflow gives security professionals the flexibility to customize security policies, file processing, and administrative options to meet specific security requirements and service level performance commitments.
Below is a is a typical MetaDefender workflow for File Uploads
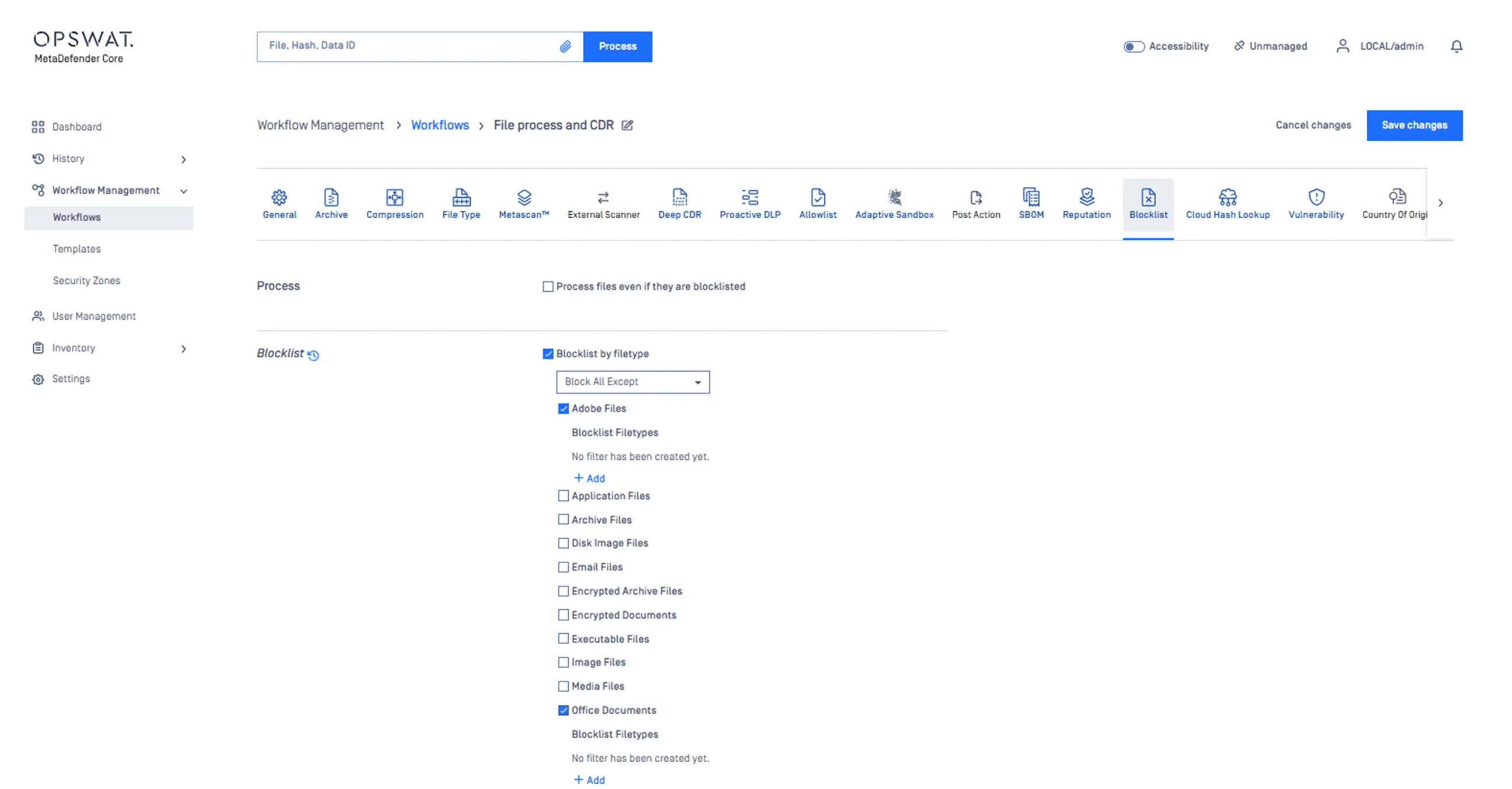
Restrict productivity file types to PDF, CSV, DOC, and XLS, typically with an average file size of 5 MB, consistent with the types of files expected to be uploaded.
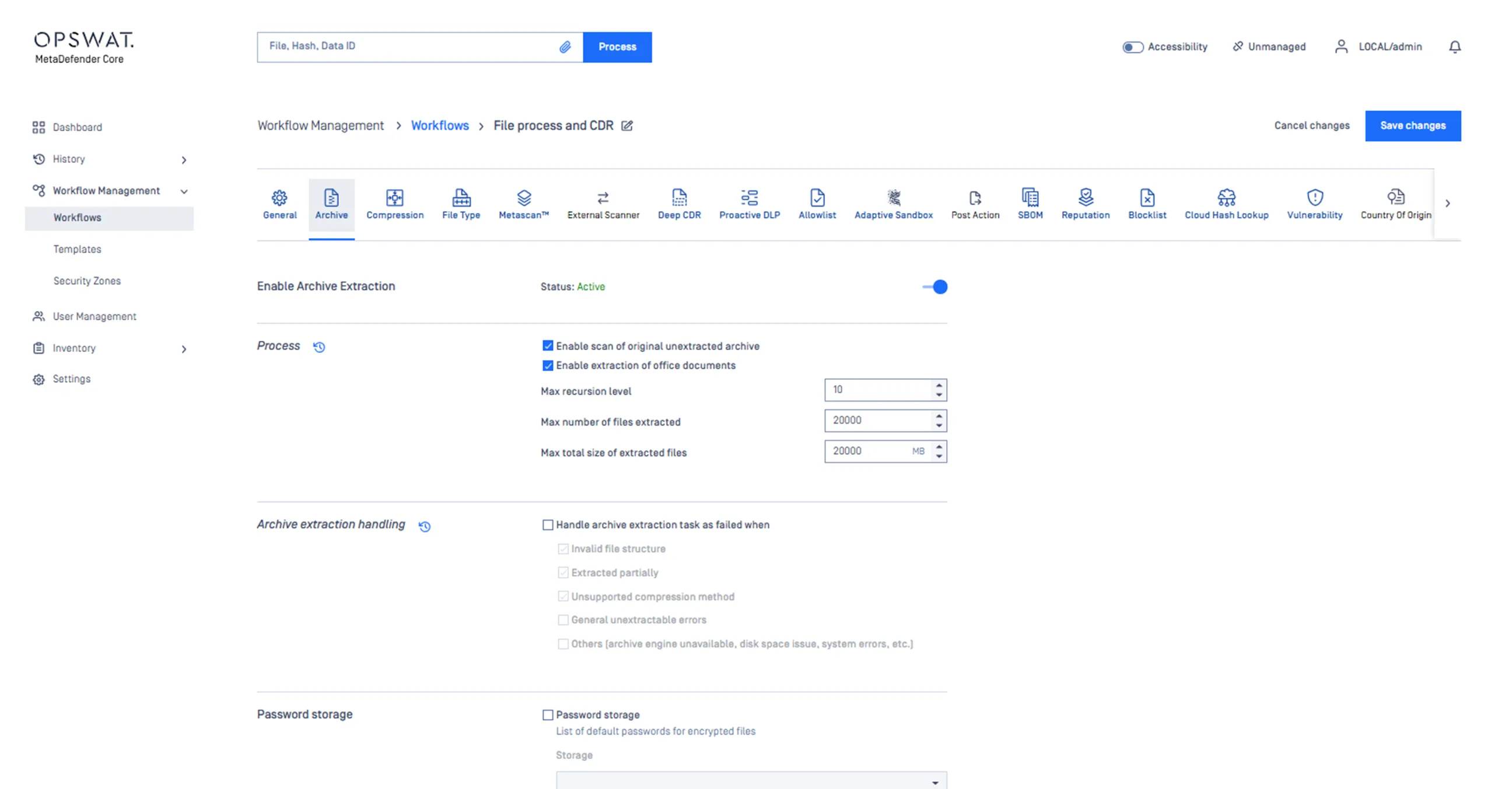
Accept archive files, but typically less than ten files per archive to limit complexity.
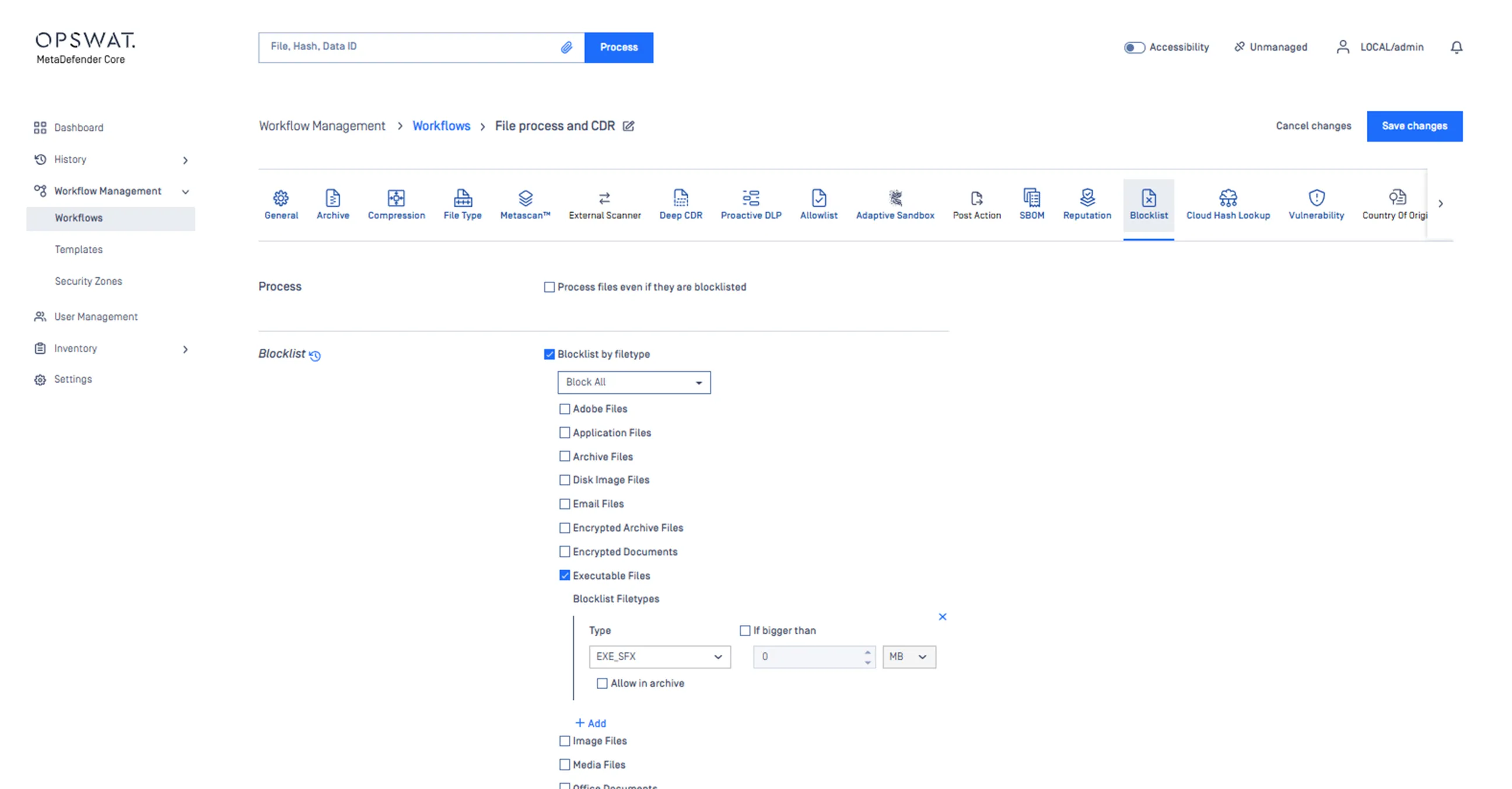
Reject executable files, as most file upload use cases don’t involve software.
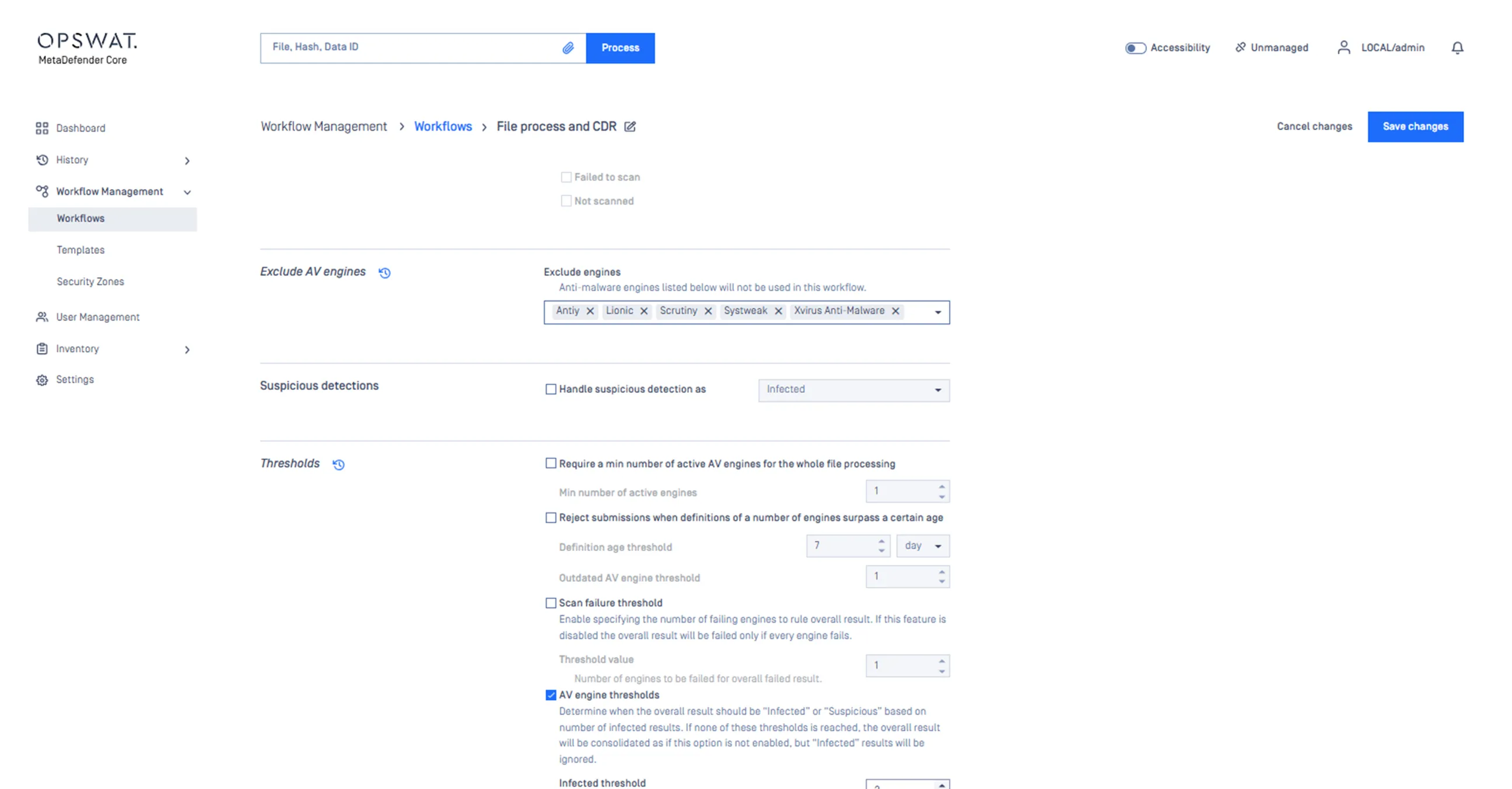
Establish a low multiscanning detection threshold of 1 or 2 engines before a file is flagged and returned to the customer or partner for remediation.
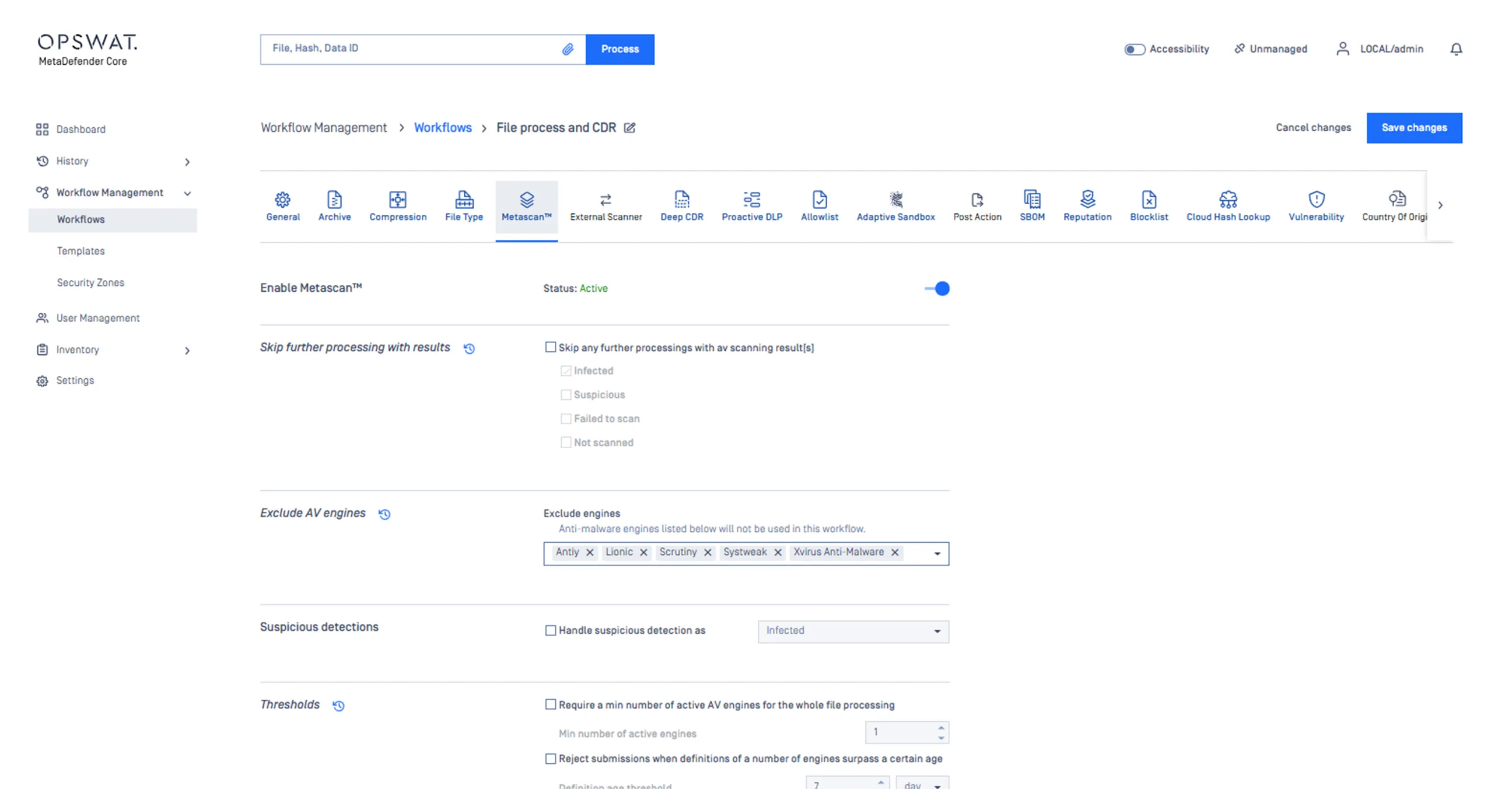
Define detection and protection workflows across Metascan Multiscanning, Deep CDR, Proactive DLP, and Adaptive Sandbox depending on the source of file uploads.
How to Block Malicious
File Uploads
Are you ready to put MetaDefender on the front lines of your
cybersecurity strategy?
Secure File Uploads in Action
Securing local government file uploads with Deep CDR and Multiscanning