MetaDefender NAC™
Secure Your Network With MetaDefender NAC
The value of our MetaDefender NAC solution is simply this—by ensuring that every network connection and endpoint device is visible, allowed or blocked appropriately in real-time, the threat associated with security incidents can be reduced substantially. Don’t risk your organization’s data and reputation by exposing it – instead ensure that the security of your network, your constituents’ personal information, and your intellectual property remains intact.

What We’re Up Against
Many organizations are faced with the ever-increasing onslaught of unknown devices accessing their critical infrastructure.
Employees, customers, contractors, guests, suppliers and their devices are all potential threat vectors representing a challenge to implement network security policies without inhibiting business productivity. There is also the daunting task of providing user and device access/blocked access information to meet regulatory compliance and for security forensics.
Know What's On Your Network
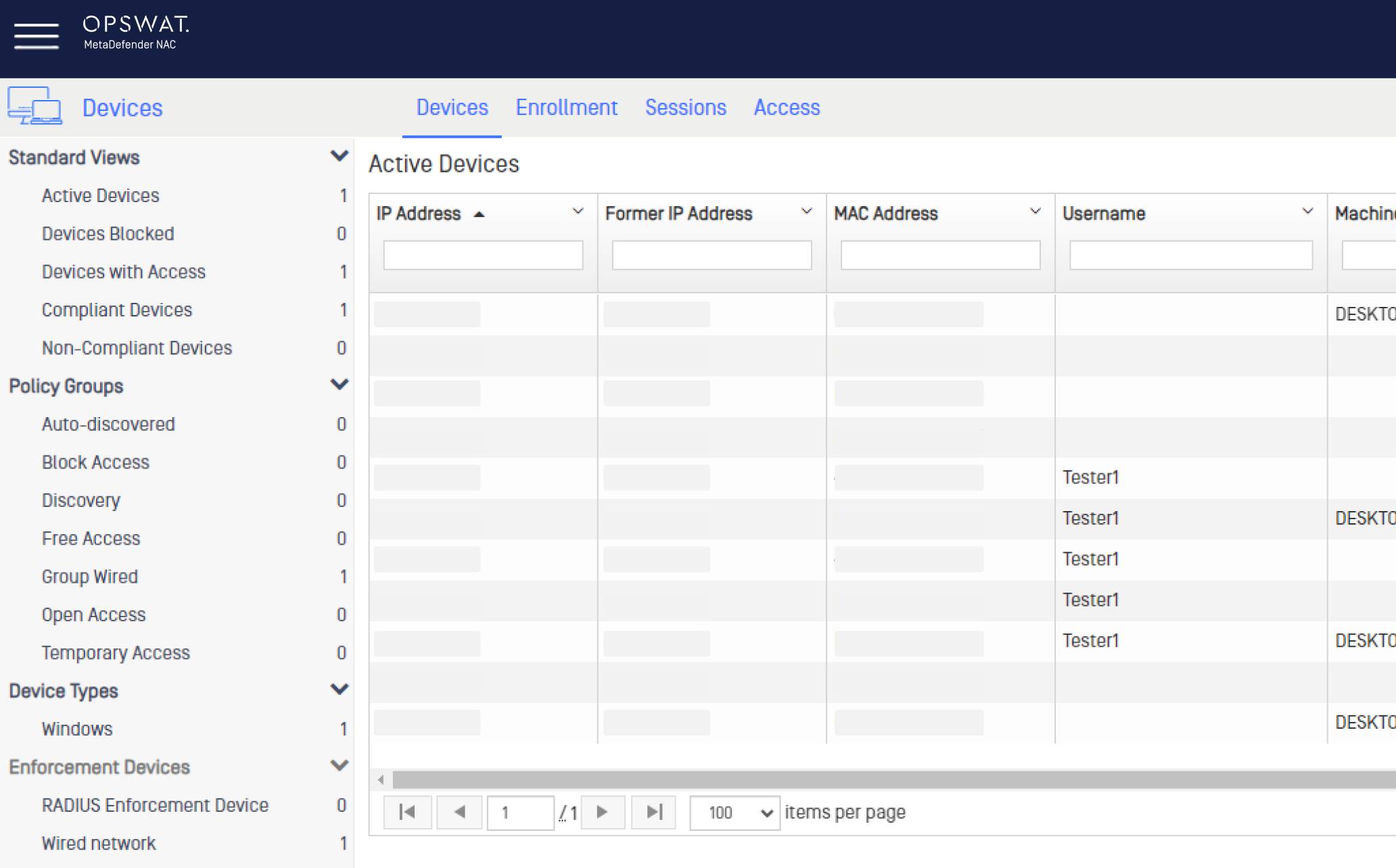
Agentless device identification and profiling provides visibility into detailed information for devices on your network: Username, IP address, MAC address, Role, Device Type, Location, Time and Ownership. MetaDefender NAC uses advanced heuristics and rich pattern analysis for strong device profiling.
Device Discovery And Profiling
MetaDefender NAC discovers new IoT and User Devices that attempt network access. This solution can either Profile (determine device type) in a passive manner or quarantine the device until device type is explicitly known. We use the following techniques to determine device types:
Deep Device Fingerprinting
- DHCP
- Web Browser User Agent Identification
- URL Fingerprinting
- MAC Address OID Fingerprinting
Input From External Sources Such As
- In-line Network Devices (Wireless Access Points, Firewalls)
- Database Resources
Flexible Deployment Options
- Cloud (SaaS)
- On-prem
- Hybrid
Control IoT Or Browser-less Device Access
Whether it’s printers and VOIP phones, smart devices like thermostats and lights, or OT devices specific to your industry, controlling and monitoring these devices can be a real challenge. These devices can represent much of the risk in your environment, and many organizations are addressing this issue through network segmentation. Our NAC solution provides a consolidated view of traditional systems, mobile and IoT devices, and now, operational technology (OT) systems; giving you the ability to segment IoT devices either using ACLs or assignment to a specific VLAN from a single dashboard.
The NAC solution allows multiple options designed to meet your varying requirements for these types of devices:

Passive Onboarding
You have an option for MetaDefender NAC to recognize certain device types and passively allow them access.
Bulk Upload
You have an option to allowlist a group of devices with the MAC address, ensuring only these specific MAC addresses will get on the network.
Self-Registration
If you are in an environment where you have specific IoT Devices that need identity tied to it, these can be self-registered through the captive portal.
Deep Compliance Device Check
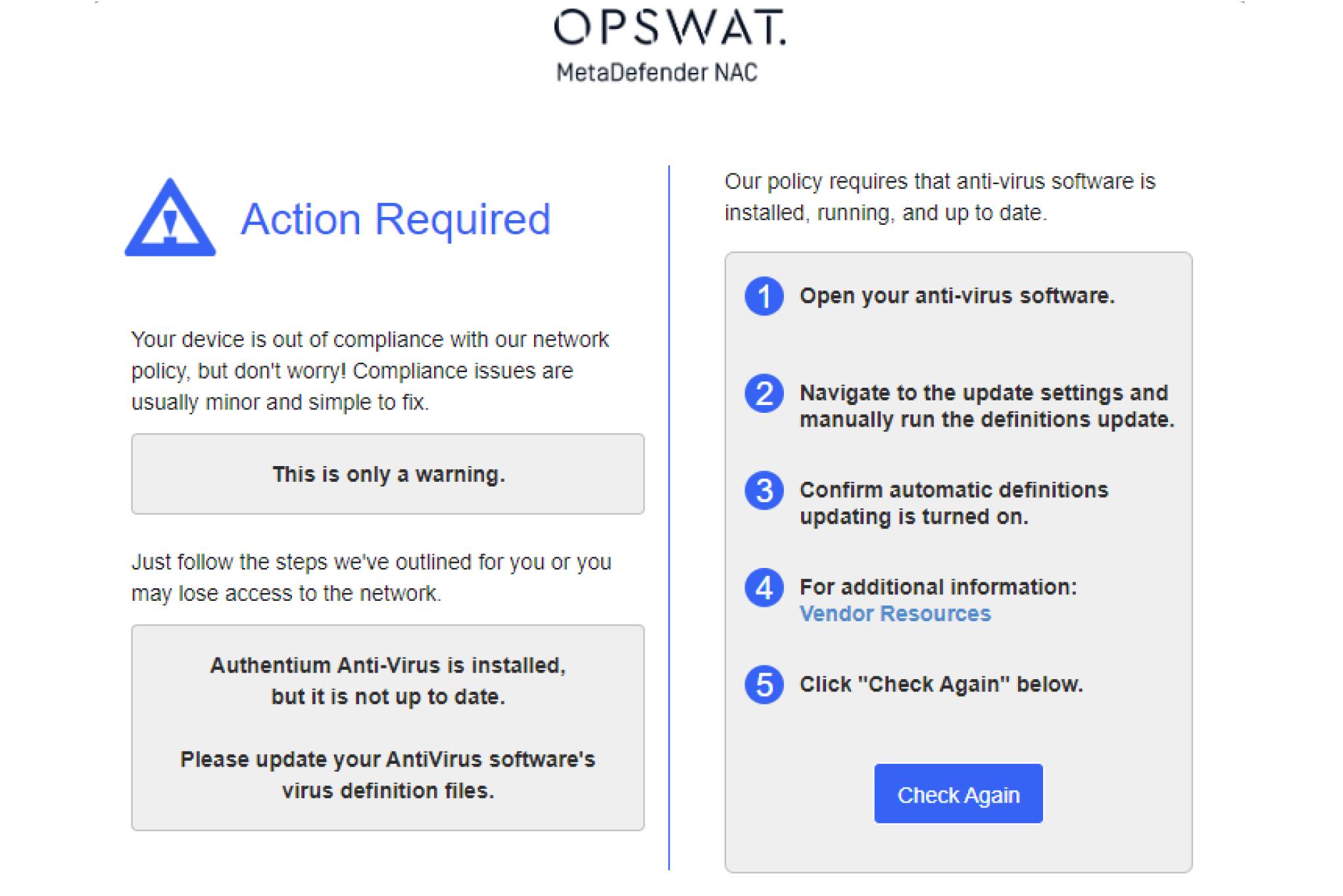
Whether it's your organization's Acceptable Use Policies (AUP) or regulatory requirements, MetaDefender NAC ensures devices on your network adhere and comply accordingly.
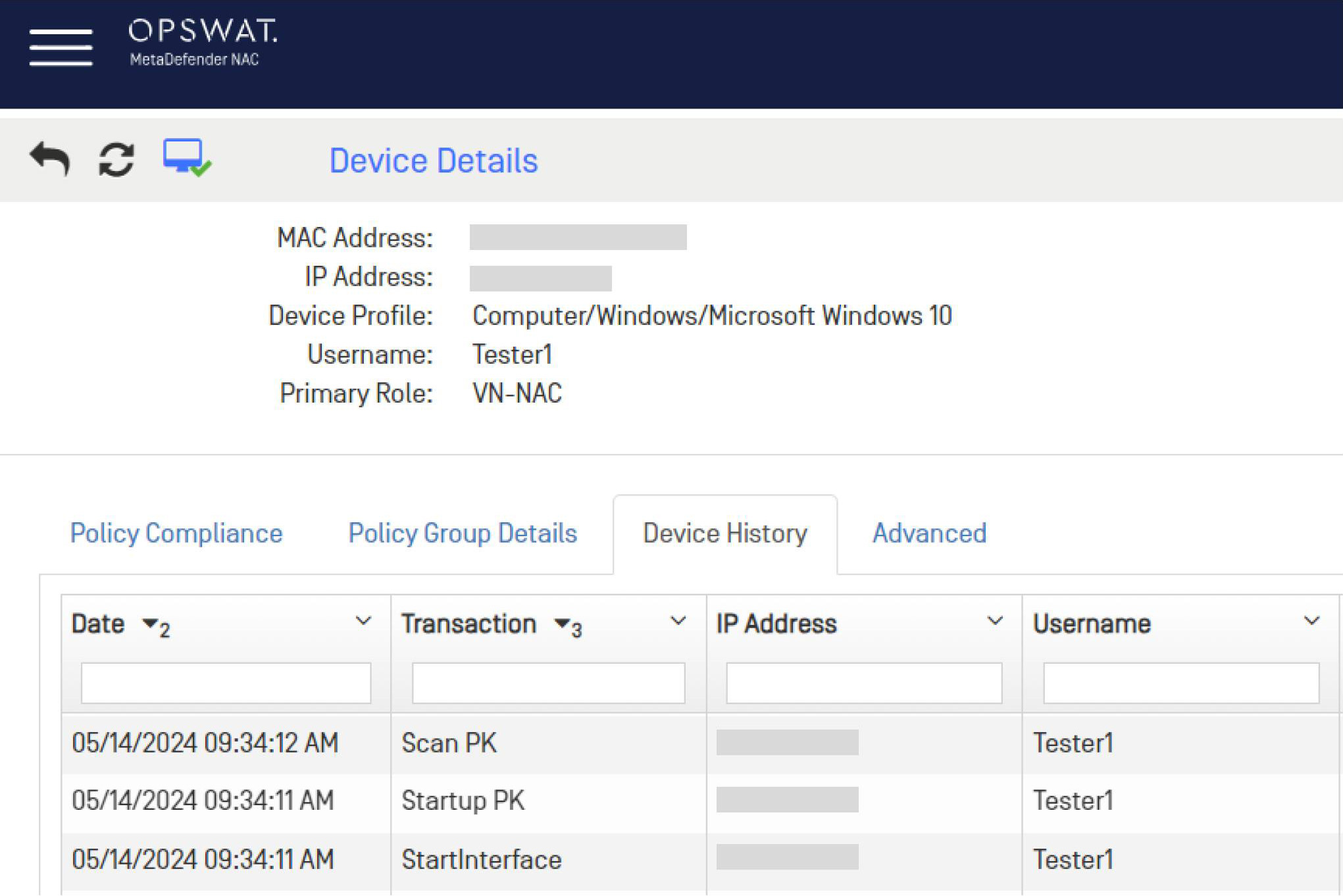
Windows, macOS, and mobile devices are checked with deep Endpoint Assessments prior to granting network access to ensure that the device adheres to your AUPs and are also checked in real-time as they move across your network.
Meeting regulatory compliance requirements such as GDPR, HIPAA, PCI DSS, SOX, or GLBA revolve around knowing “who, what, when and where” for devices and users on your network and controlling access to the data your company needs to keep secure. MetaDefender NAC helps you achieve that visibility, security, and control - and automates policies that validate accountability, mitigate vulnerabilities and block evolving threats – ensuring your compliance with recurring audits.

Authenticate Your Users
Depending upon your environment, you can authenticate your users with multiple methods/protocols. End User AD/LDAP/SAML Authentication prevents unauthorized users from accessing network resources.
MetaDefender NAC supports the following authentication types: EAP-PEAP (credential based), EAP-PEAP (machine based), EAP-TLS (certificate based), as well as domain and 802.1X Single Sign-On (SSO).
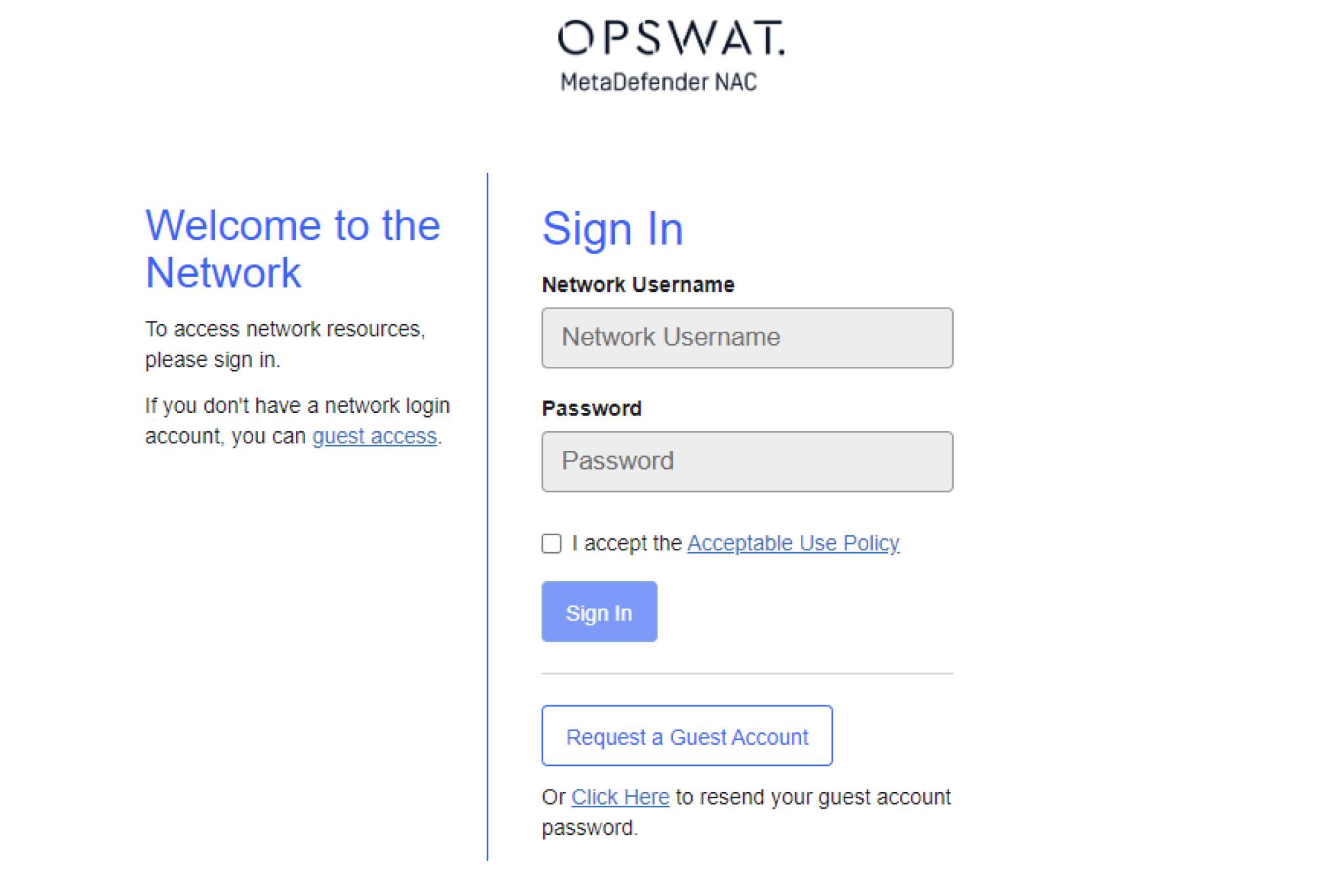
Secure Access for Guests, Vendors and 3rd Parties
End User Captive Portal for authentication of BYOD devices with extensive branding / customization capabilities.
Guest Self-Registration automates the process of provisioning temporary network access for your guests. Set up different access levels and approval processes for guests, vendors or other 3rd parties needing access to your network. MetaDefender NAC comes standard with a fully configured SMS gateway that provides international SMS support right out of the box.
Device Enrollment with Bulk Upload MAC Address capability enables proper authentication for browser-less devices such as printers, VOIP phones, IP Cameras or any other IOT enabled device including optional network access assignment (VLAN, ACL, Role, Profile, etc.).
View Real-time Or Historical Management Reporting
MetaDefender NAC gathers a wealth of real-time and historical context-aware device information called Contextual Intelligence, such as Username, IP Address, MAC Address, Role, Location, Time, Ownership and even Compliance Status. This information allows for more timely and informed security decisions.
Use the Real-time Reporting Dashboard for visibility into who and what is on your network along with a built-in reporting interface for 30 days of detailed device information and 6 months of historical information. These reports can be run on a schedule, on demand, or exported to other tools.
Additionally, a built-in reporting interface provides 30 days of detailed client information and 6 months of historical session information through an easy-to-use interface that can either be run on demand or scheduled to e-mail reports on a daily, weekly, or monthly basis. This data can also be exported to an external source like a SIEM for longer periods of data retention.
MetaDefender NAC Integration To Enhance Current Security Investments
MetaDefender NAC can shares the contextual intelligence information it gathers with other security solutions such as identity-based firewalls, web content filters, SIEM, and bandwidth management solutions to enhance their capabilities well beyond the scope of traditional domain devices.
This capability is bi-directional and can receive alerts from Advanced Threat Detection systems to enforce a real-time quarantine for severe alerts. There will be no incidents of missing a middle-of-the-night critical alert spreading through your company, as it will be blocked immediately.

MetaDefender NAC Integration Partners
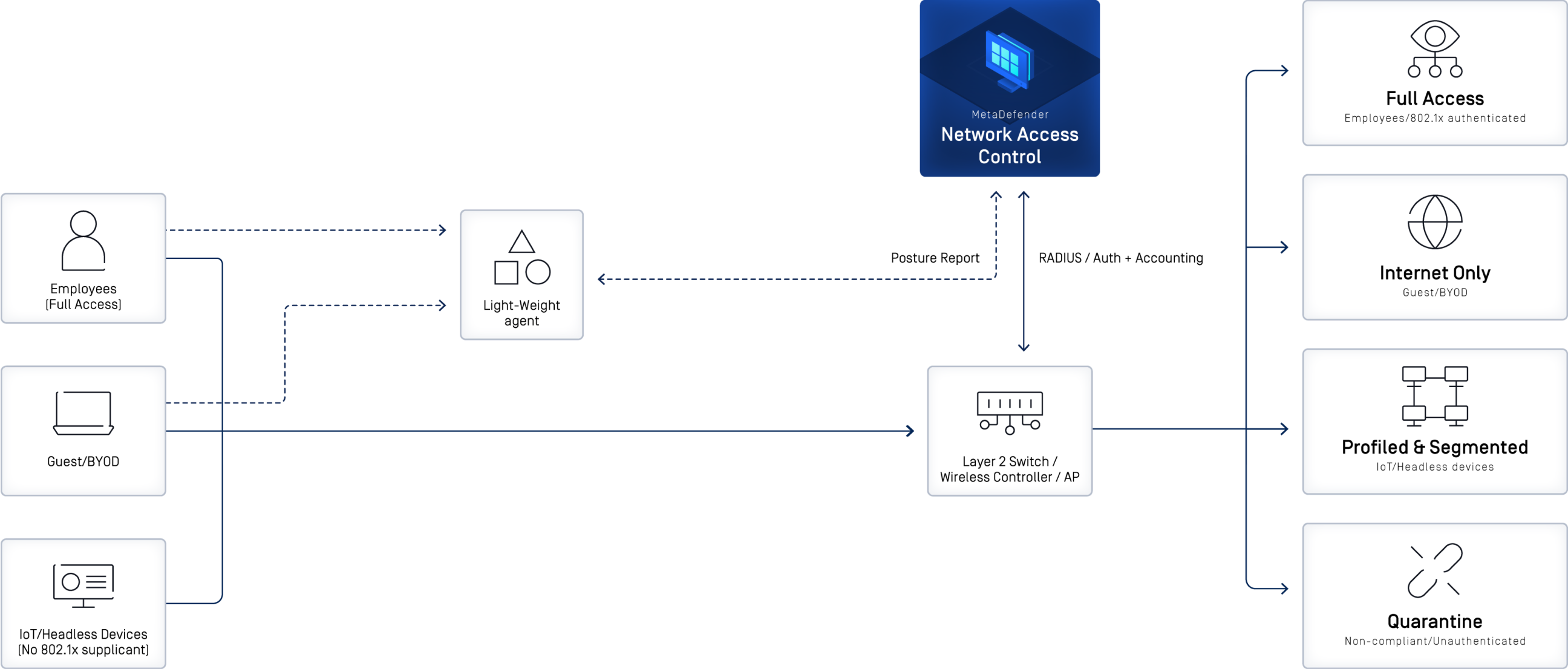
Use Your Existing Network
With MetaDefender NAC, you have flexible network integration options, which means that in most cases, you’ll be able to implement NAC without changing your current network infrastructure.
Included is a RADIUS server with Layer 2 Network Integration that allows you to authenticate users and devices, control network access using 802.1X and/or by MAC address and assign network privileges for authenticated users and devices. Bulk NAS importing and NAS CIDR notification options are available along with custom RADIUS attribute creation. Network Access Control and Assignment provides wired port level and wireless SSID control. This can be done with Dynamic VLAN Assignment, Downloadable ACLs (dACL), and/or Role Based Access such as Roles, Profiles and Filter-Id.
Optionally, Layer 3 integration bypasses the requirement for RADIUS with Policy Based Routing. This can also be used in addition to basic RADIUS server and MAC address allowlisting for the initial network assignment.
A helpful feature is that controls can be implemented to restrict access to a specific network VLAN based on allowed host types and/or MAC addresses, a feature particularly useful for assigning IoT devices such as printers, VOIP phones and IP Cameras to a segmented VLAN.
Scale NAC Capacity and Availability As You Grow
Leverage VM hardware fault tolerance or purchase the High Availability (HA) option for active/passive nodes. Additionally, multi-node supported clusters are an option for environments of over 25,000 devices.

NAC Installation and Management Without Complicated, Lengthy Consulting Services
Remotely deploy with a time proven 5-step install process with access to engineering support throughout. Once implemented, ongoing support includes: 24x7 proactive monitoring & support, nightly configuration backups and automated updates of new device fingerprints, OS & Antivirus signature updates, and either scheduled or automated version upgrades.
Discover What Our Esteemed Users Say
Technical Documentation
Getting Started
Deployment & Usage
Support
Unlock the Full Potential of Our Products

Recommended Resources

MetaDefender NAC Cloud Datasheet




