Streamlined Management, Security, and Secure Access
A single-pane-of-glass solution that centrally manages OPSWAT MetaDefender products, inventory, and secure endpoint access.
Detailed Reports and Analytical Tools
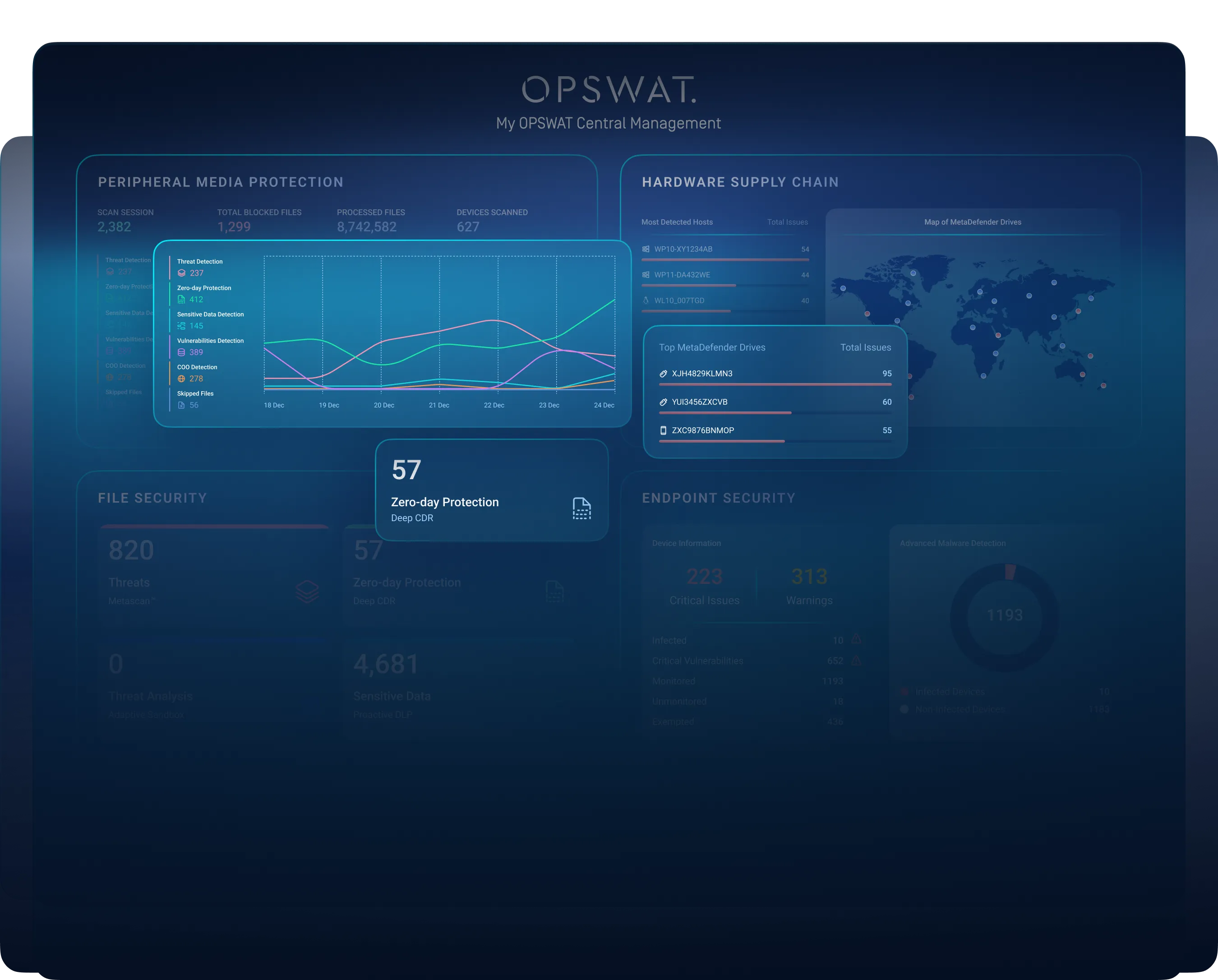
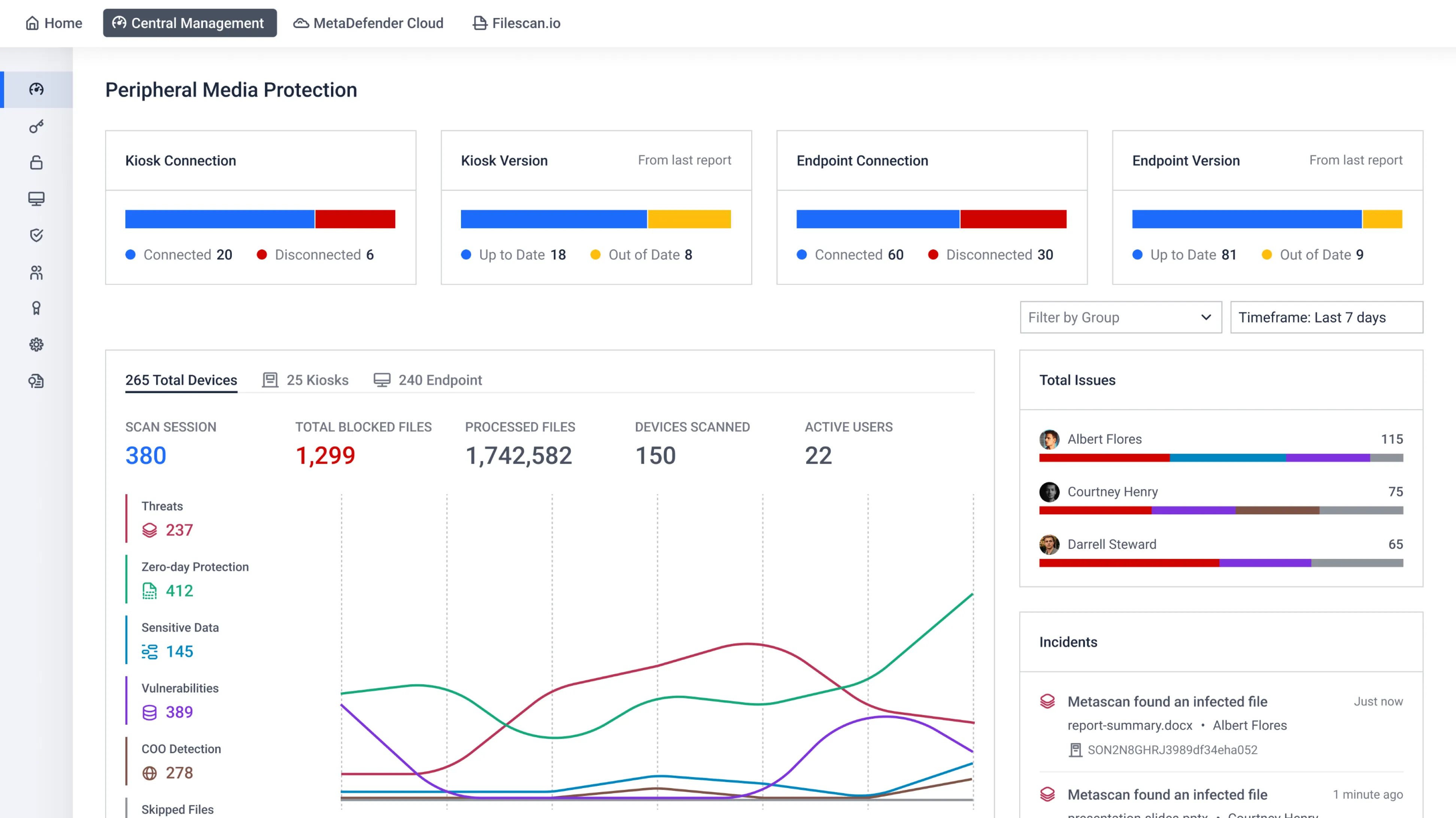
Aggregate data from all connected MetaDefender products, generate in-depth device usage and access reports, and leverage analytics to identify trends and enhance security strategies.
See how My OPSWAT Central Management streamlines your operations while enhancing visibility and control to safeguard your critical infrastructure.
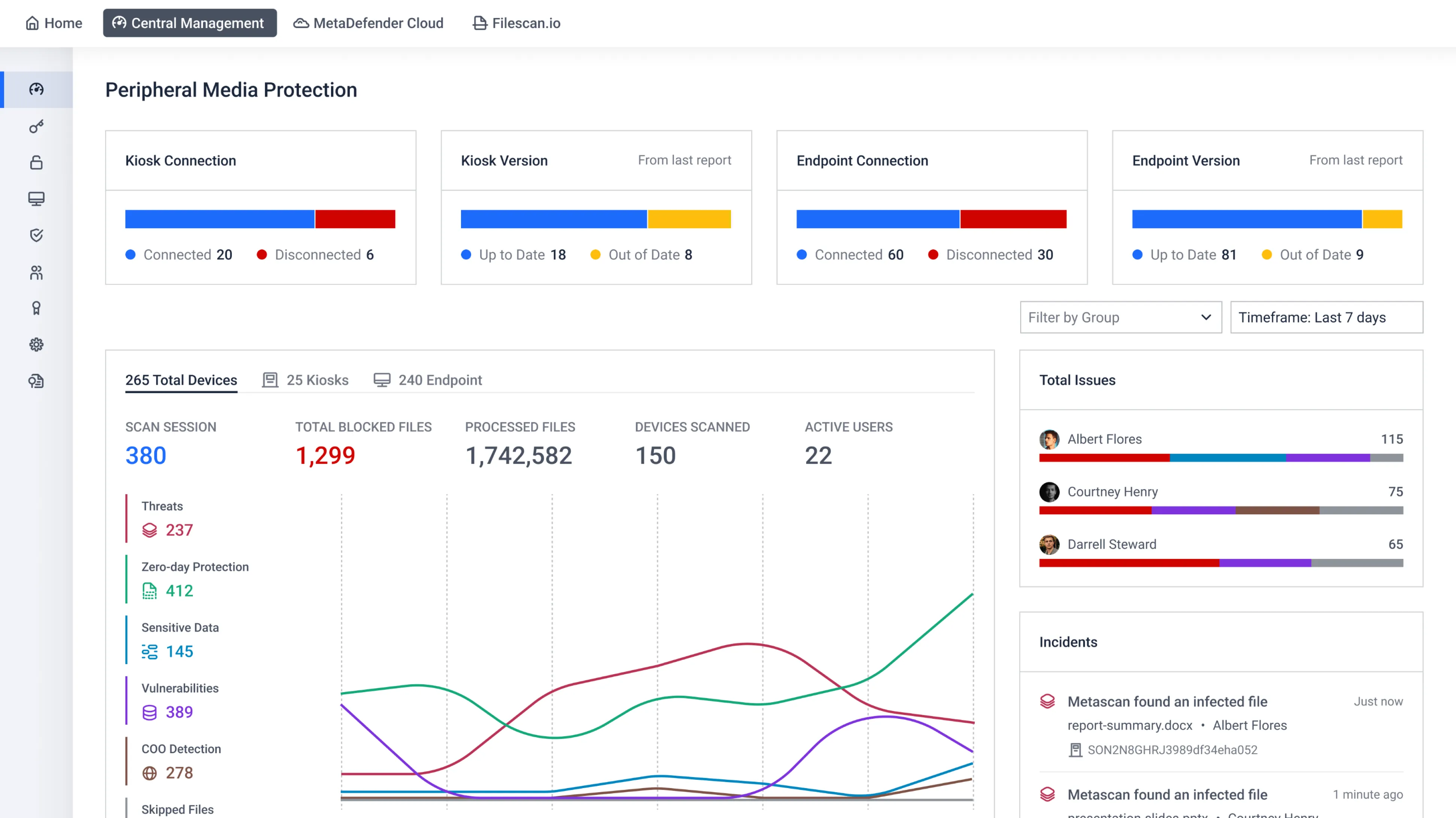
Get real-time data and critical information at a glance in a global dashboard.
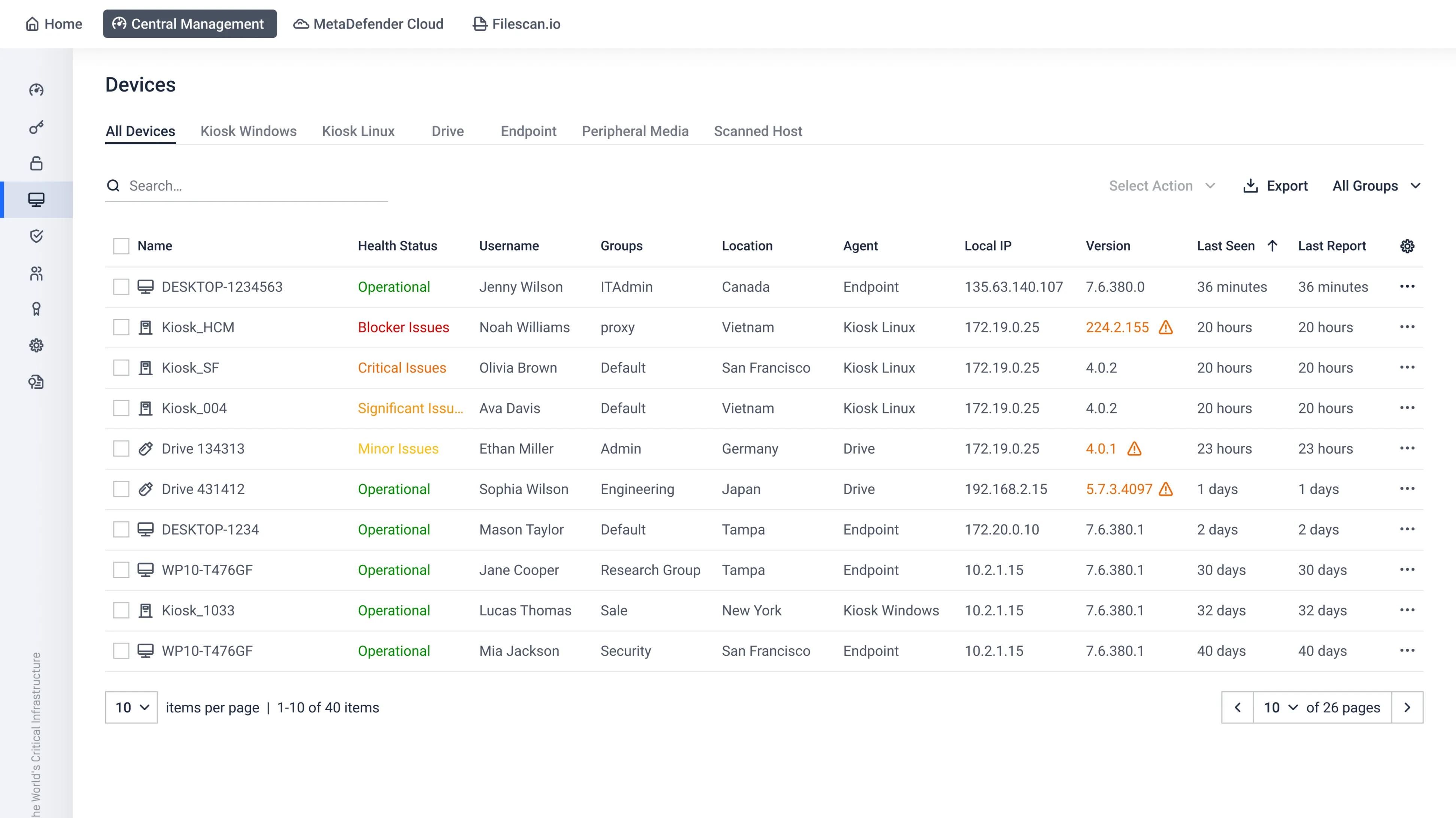
Browse, monitor, and easily manage your network of interconnected Kiosks, Drives, and other endpoints.
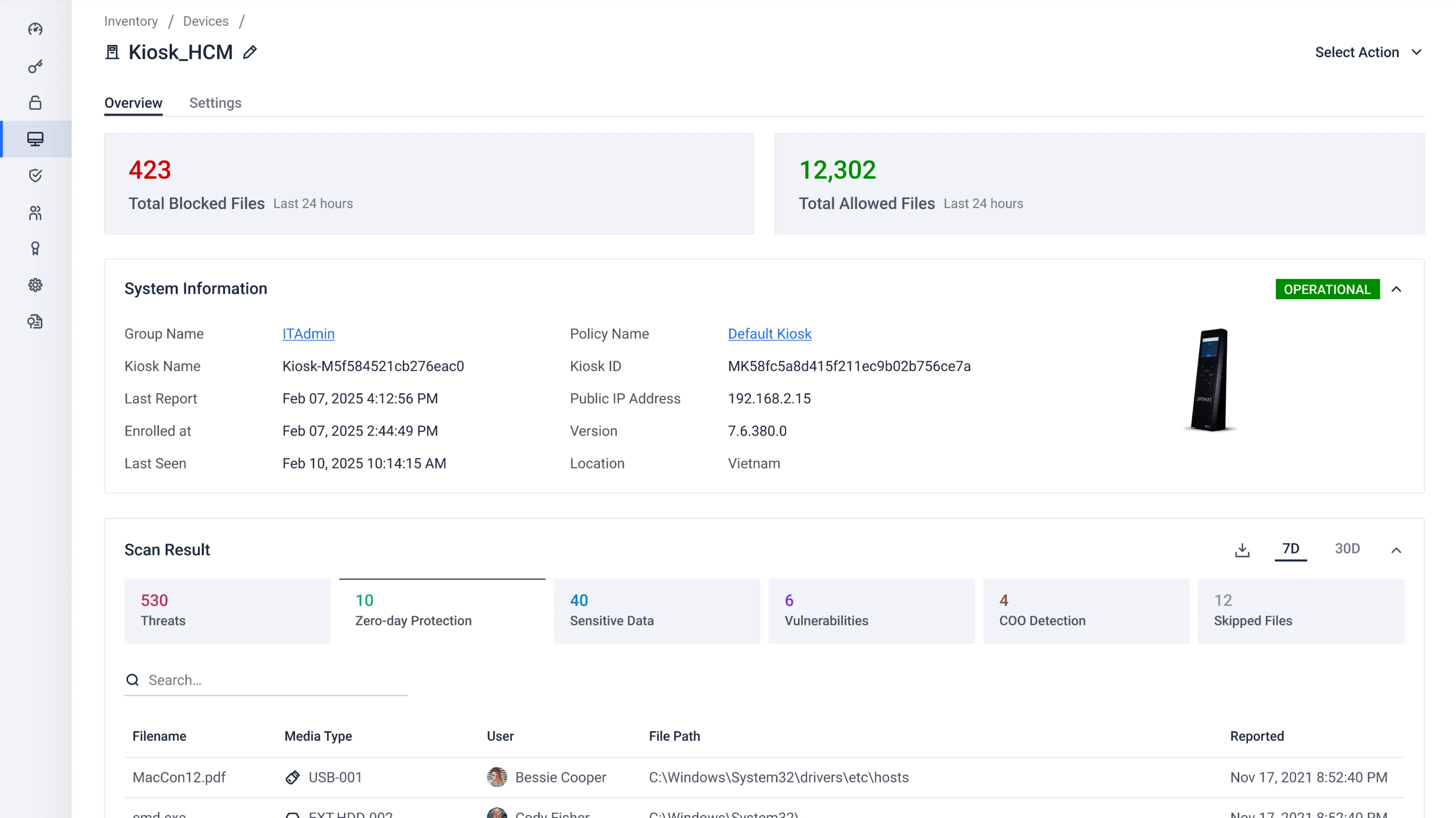
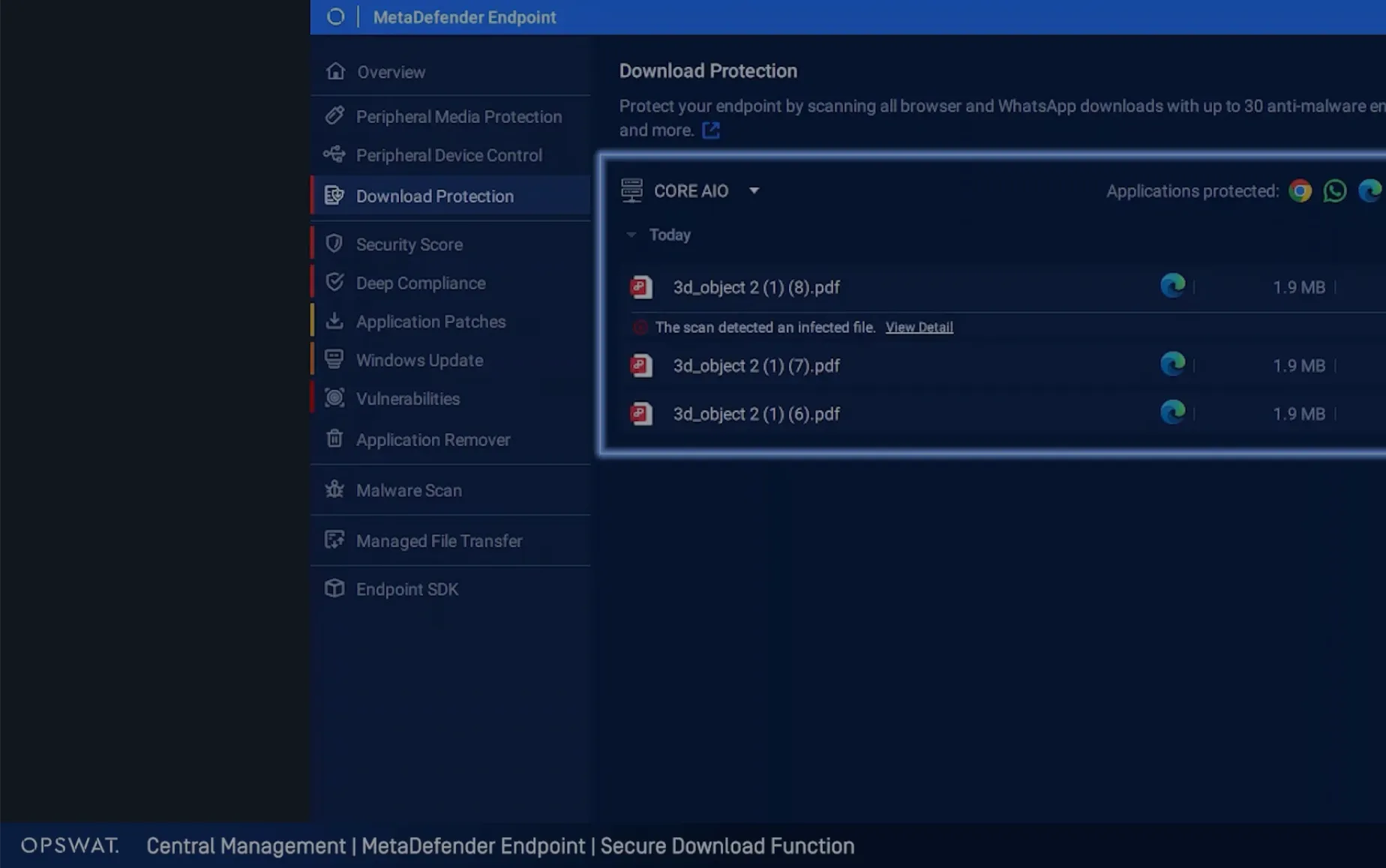
Get detailed information about detected threats and blocked files.
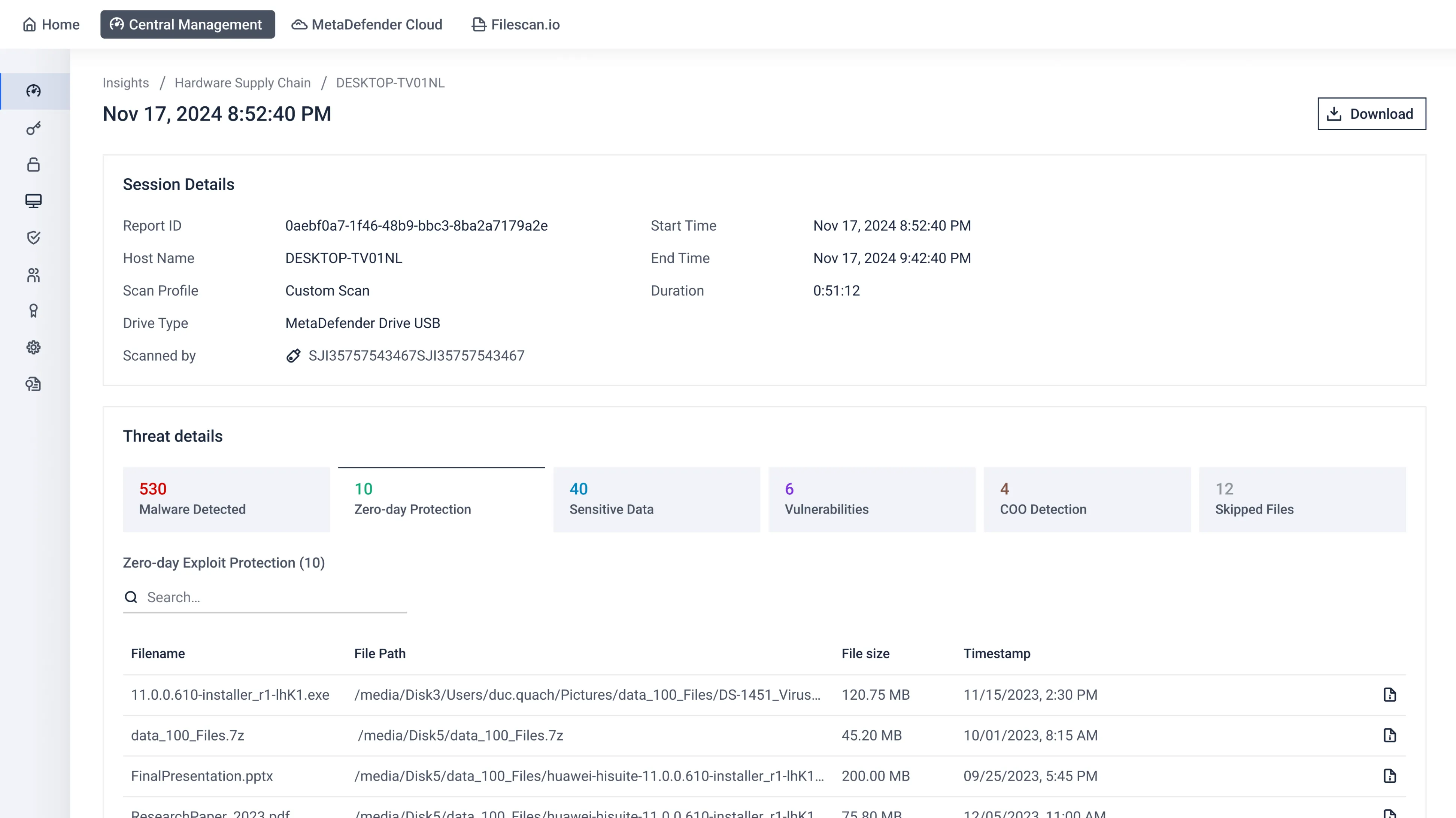
Get comprehensive data and forensic analysis of cyberthreats detected by OPSWAT solutions.
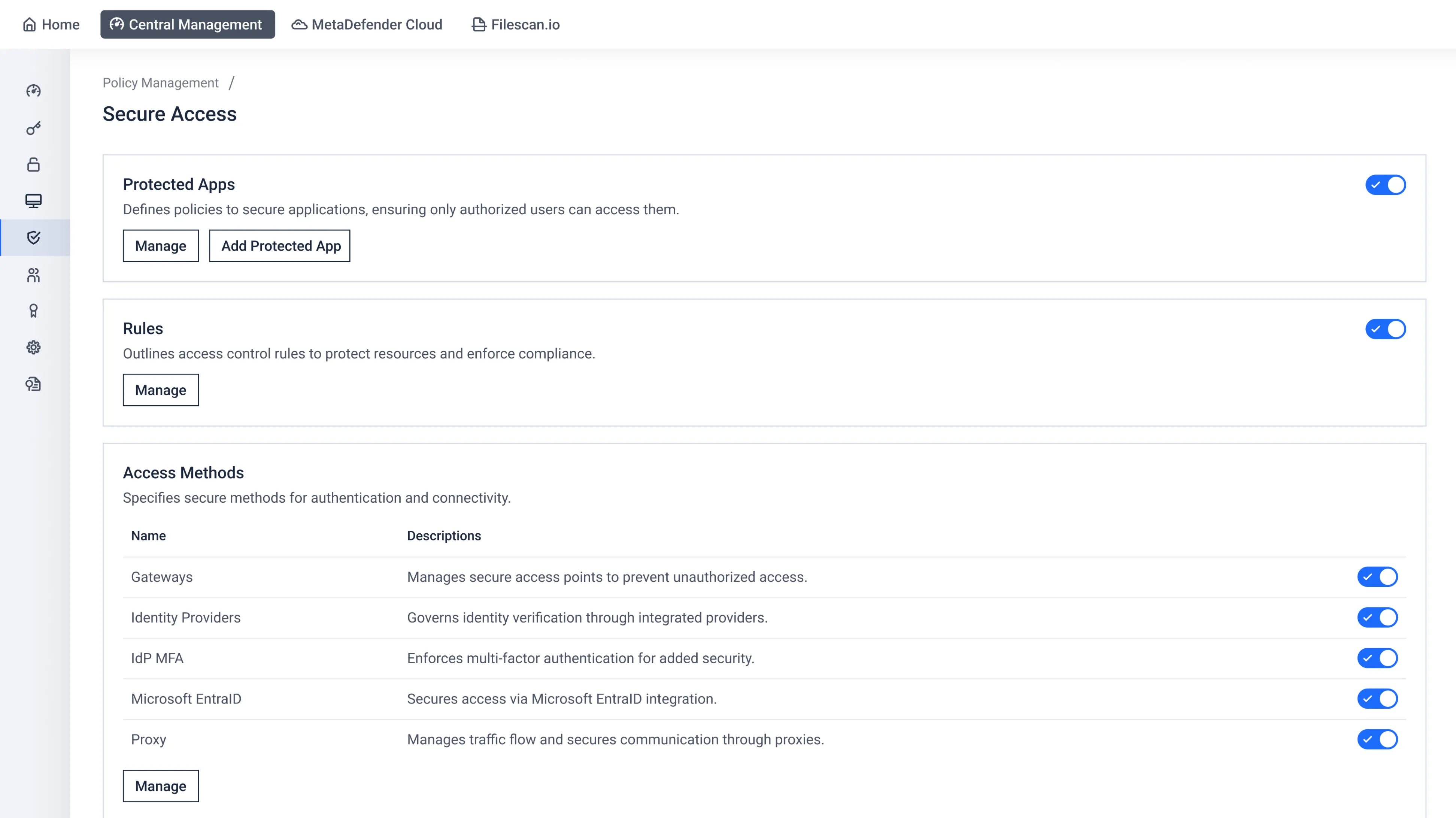
Manage policies, access, permissions, protected apps, and more.
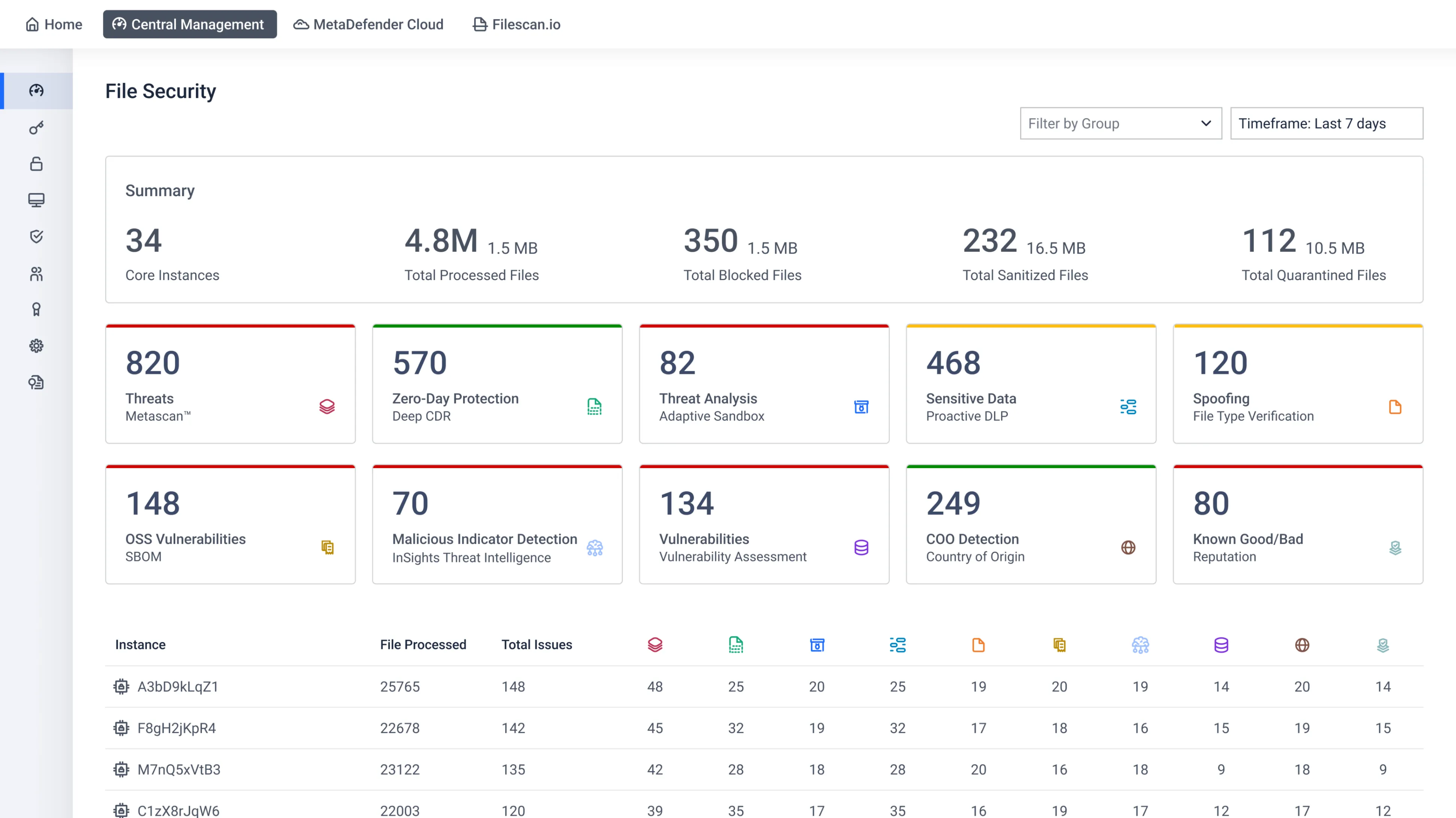
Detect and eliminate file-borne threats with Deep CDR™ and Metascan™ Multiscanning.
Integrating OPSWAT Central Management
Watch these quick demos to see how Central Management integrates with Kiosk, Endpoint, Core, and Cloud solutions. Understand how to simplify policy enforcement, automate updates, and gain centralized oversight from one console.
Unified Management
Manage all enrolled devices on a single platform and enforce endpoint security policies, with a global executive view of data processing, and detailed device usage and access patterns.
Improved Security Posture
React to threats, patch vulnerabilities, and prevent data leaks in real time with comprehensive reports, visibility, and control over peripheral and removable devices.
Efficient Risk Monitoring
Quickly identify security risks and send critical notifications to administrators automatically with centralized monitoring and alerts.
Scalable and Flexible
My OPSWAT Central Management is lightweight and built for seamless integration, suitable for small organizations as well as large businesses with complex webs of company-owned and BYOD endpoints, and secure or compliance-restricted environments.
Tailored Support
Get instant support from our technical experts around the globe, available 24 hours a day, seven days a week. Our professional consultants ensure integrations and product configurations are tailored and customized for your specific environment.
Secure Access
Ensure that access from devices to your cloud and legacy applications are secure whether connecting from the office, home, or other remote locations. Available as Secure Cloud Access with SAML IdP Integration and Software Defined Perimeter (SDP).
Manage Powerful Security Solutions from OPSWAT

Endpoint Security
Protect endpoints from advanced threats with multi-layered security and compliance enforcement. Ensure zero-trust access and prevent malware infiltration across all devices.

File Security
Detect and eliminate file-borne threats with Deep CDR™ and Metascan™ Multiscanning. Secure files at rest and in motion without slowing down workflows.

Hardware Supply Chain Security
Safeguard critical infrastructure by verifying the integrity of hardware components. Detect unauthorized modifications and prevent supply chain attacks before deployment.

Peripheral Media Protection
Control and secure removable media with advanced scanning and policy enforcement. Prevent malware infections from USBs, external drives, and other peripheral devices.
Feature Comparison and Roadmap
| Features | Central Management v8 | Central Management v10 |
|---|---|---|
| Solution Overview Dashboard | ||
| Peripheral Media Protection | — | |
| Endpoint Security | — | |
| Hardware Supply Chain | — | |
| File Security | — | |
| Secure Access | — | |
| Peripheral Media Protection Solution | ||
| MetaDefender Kiosk | — | |
| Removable Media Protection | — | |
| Endpoint Security Solution | ||
| Endpoint Compliance | — | |
| Regulation & Standard | — | |
| Vulnerability & Patch Management | — | |
| Endpoint Scanning | — | |
| Secure Access Solution | ||
| SDP method: a next-generation VPN | — | |
| IdP Method / IdP MFA: Secure access with Identity Provider integration | — | |
| Network Access Control from Cloud | — | |
| Secure access to Microsoft Entra ID / Office 365 | — | |
| Hardware Supply Chain | ||
| MetaDefender Drive | — | |
| File Security | ||
| MetaDefender Core | — | |
| MetaDefender ICAP | — | |
| Malware Analysis | ||
| MetaDefender Sandbox | — | |
| Managed File Transfer Solution | ||
| MetaDefender Managed File Transfer (MFT) | — | |
| Products & Features | Central Management v8 | Central Management v10 |
|---|---|---|
| MetaDefender Kiosk Windows (K-Series) | ||
| Visualized Data Report | MetaDefender Kiosk | MetaDefender Kiosk & Endpoints |
| Health & Connection Status | ||
| Centralized Configuration | Group, Individual | Group, Individual & Policy management |
| License Management | ||
| Certificate Management | — | |
| MetaDefender Kiosk Linux (L-Series) | ||
| Visualized Data Report | MetaDefender Kiosk | MetaDefender Kiosk & Endpoints |
| Health & Connection Status | ||
| Centralized Configuration | Group, Individual | Group, Individual & Policy management |
| License Management | Single volume license | Multiple volume licenses |
| MetaDefender Core | ||
| Visualized Data Report | ||
| Health & Connection Status | ||
| Centralized Configuration | Group, Individual | Group, Individual & Policy management |
| Processing History & Details | ||
| License Management | ||
| Certificate Management | — | |
| MetaDefender Endpoint | ||
| Visualized Device Health Report | — | |
| Device Monitoring & Protection | — | |
| Centralized Configuration (Group & Policy Management) | — | |
| Customizable Summary Report | — | |
| MetaDefender Drive | ||
| Visualized Data Report | — | |
| Health & Connection Status | ||
| Centralized Configuration (Group, Individual & Policy Management) | — | |
| Customizable Summary Report | — | |
| MetaDefender Managed File Transfer | ||
| Visualized Data Report | ||
| Health & Connection Status | ||
| MetaDefender ICAP Server | ||
| Visualized Data Report | ||
| Health & Connection Status | ||
| Processing History & Details | ||
| Features | Central Management v8 | Central Management v10 |
|---|---|---|
| Access | ||
| User Management | Admin & Co-admin | Admin & Co-admin & EndUser for SDP |
| Access Control | Role-Based Access Control | Granularity Role-Based Access Control |
| 3rd Party Identity Provider (SSO - SAML) | — | |
| Customizable Reports | ||
| Account Summary | — | |
| Peripheral Media Protection | — | |
| Hardware Supply Chain | — | |
| Infected Devices | — | |
| Unknown Device Discovery | — | |
| Secure Access | — | |
| Notifications & Logs | ||
| Customizable Account, Endpoint & Product Notifications | — | |
| Account & Product Event Logs | ||
| Features | Central Management v8 | Central Management v10 |
|---|---|---|
| SIEM Integration | ||
| Webhook | — | |
| Syslog | — | |
| AWS S3 Storage Log | — | |
| Syslog Integration | — | |
| Splunk Add-on | — | |
| Bring Your Own Cloud | ||
| AWS Marketplace | ||
| Azure Marketplace | ||
| Certification | ||
| SOC2 Compliance | — | |
| ISO/IEC 27001 | — | |
Technical Documentation
Getting Started
Deployment & Usage
Support
Getting Started
Deployment & Usage
Support
Getting Started
Deployment & Usage
Support
Unlock the Full Potential of Our Products

Recommended Resources
Streamlined Operations with My OPSWAT Central Management