Cloud-Native Cybersecurity Platform
All-encompassing cybersecurity platform designed to detect, prevent, and neutralize file-born threats in the Cloud.
- Comprehensive File Security
- Seamless Cloud Integration
- Simplified Compliance Automation
OPSWAT is Trusted by
A Unified Approach for Enterprise File Security
MetaDefender Cloud unifies prevention, visibility, compliance, and automation to address the biggest risks facing CISOs and SOC teams.
Product Overview
Learn how MetaDefender Cloud scans, sanitizes, and analyzes files across SaaS, cloud storage, and hybrid workflows
to prevent malware, zero-day attacks, and data leaks at scale.
MetaDefender Cloud Technologies
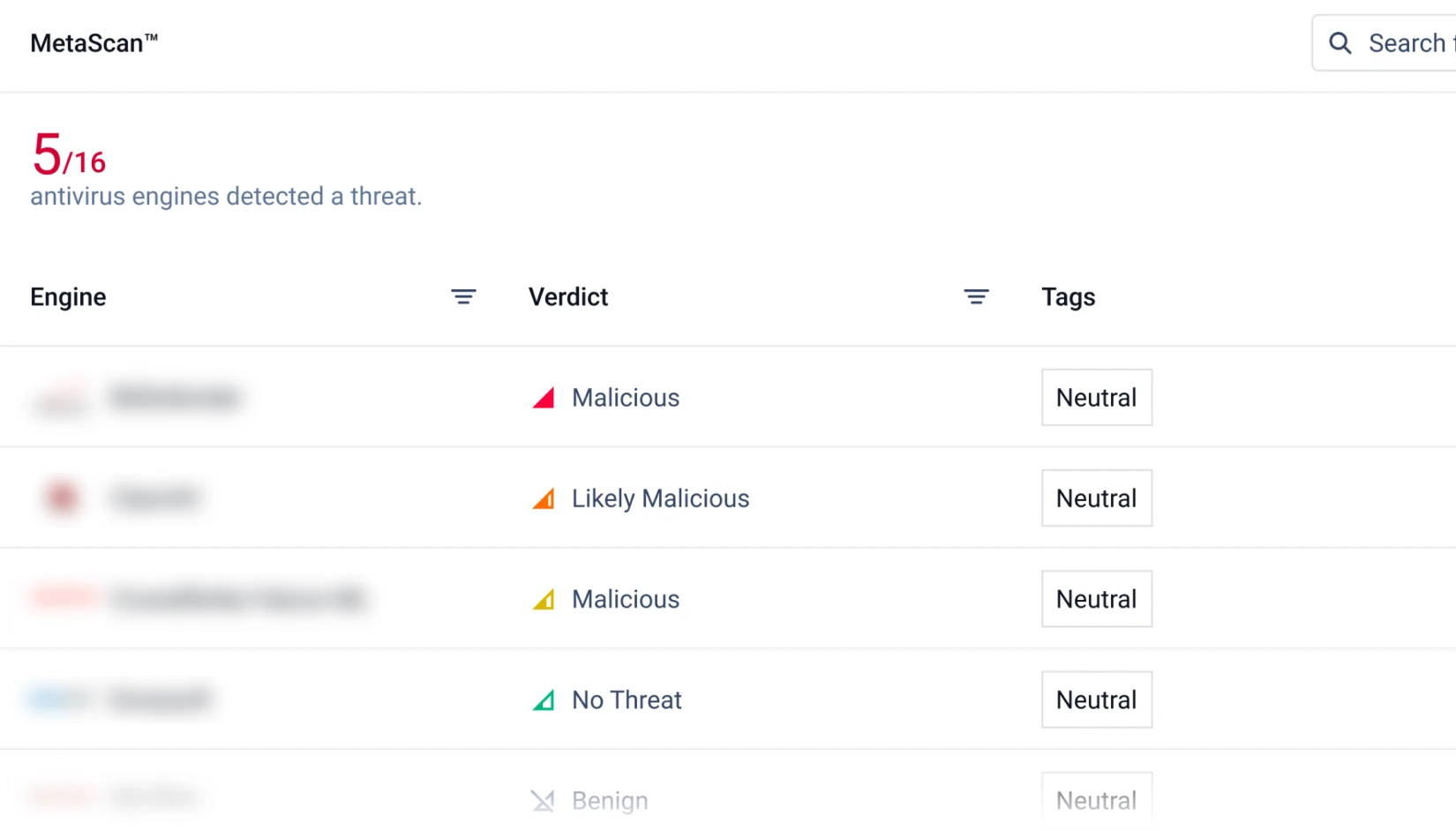
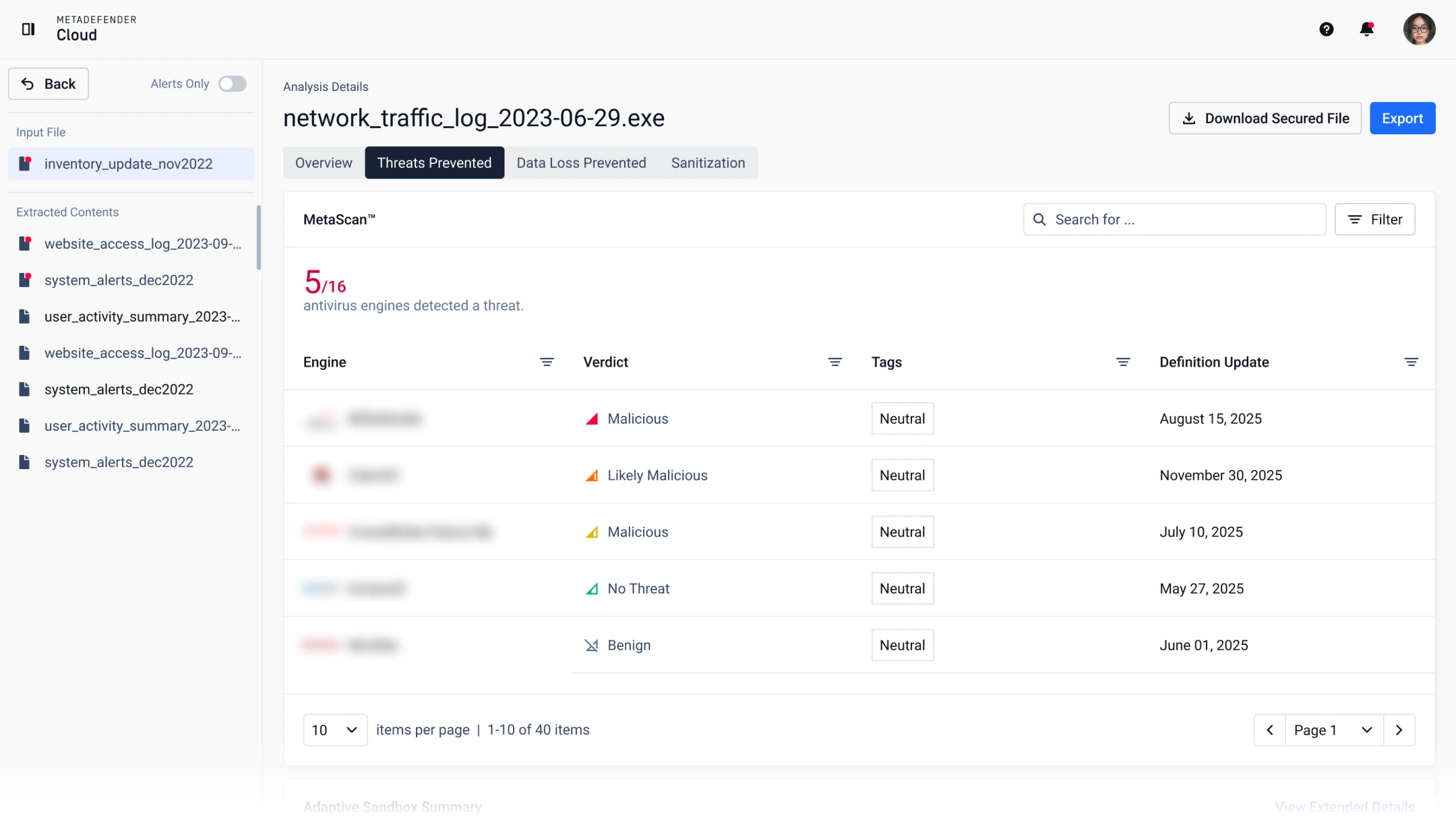
Metascan™ Multiscanning
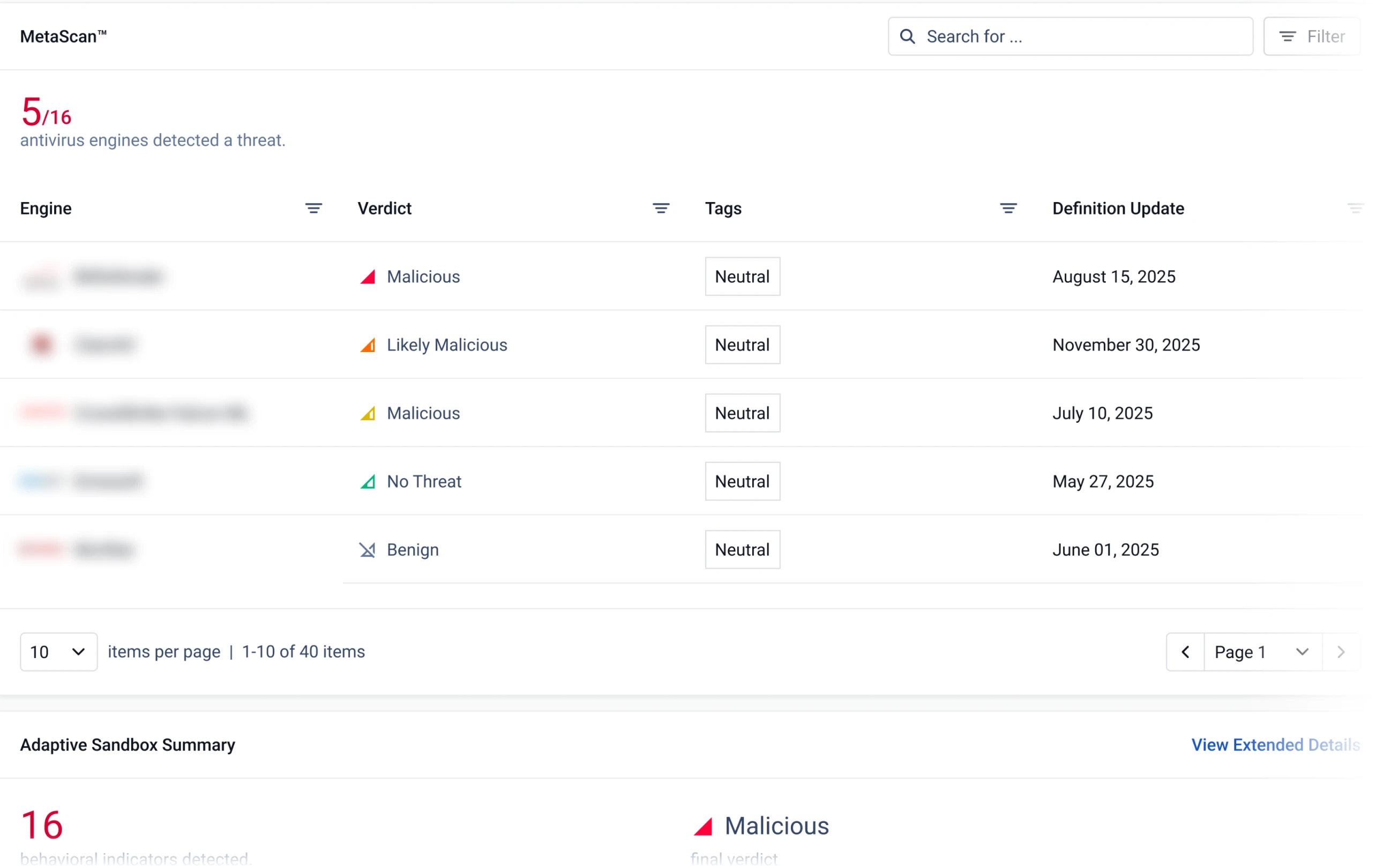
Scan files with 20+ industry-leading anti-malware engines and achieve over 99% detection rates.
See how detection rates compare depending on the number of AV engines involved in Multiscanning in the Package Efficacy Report.
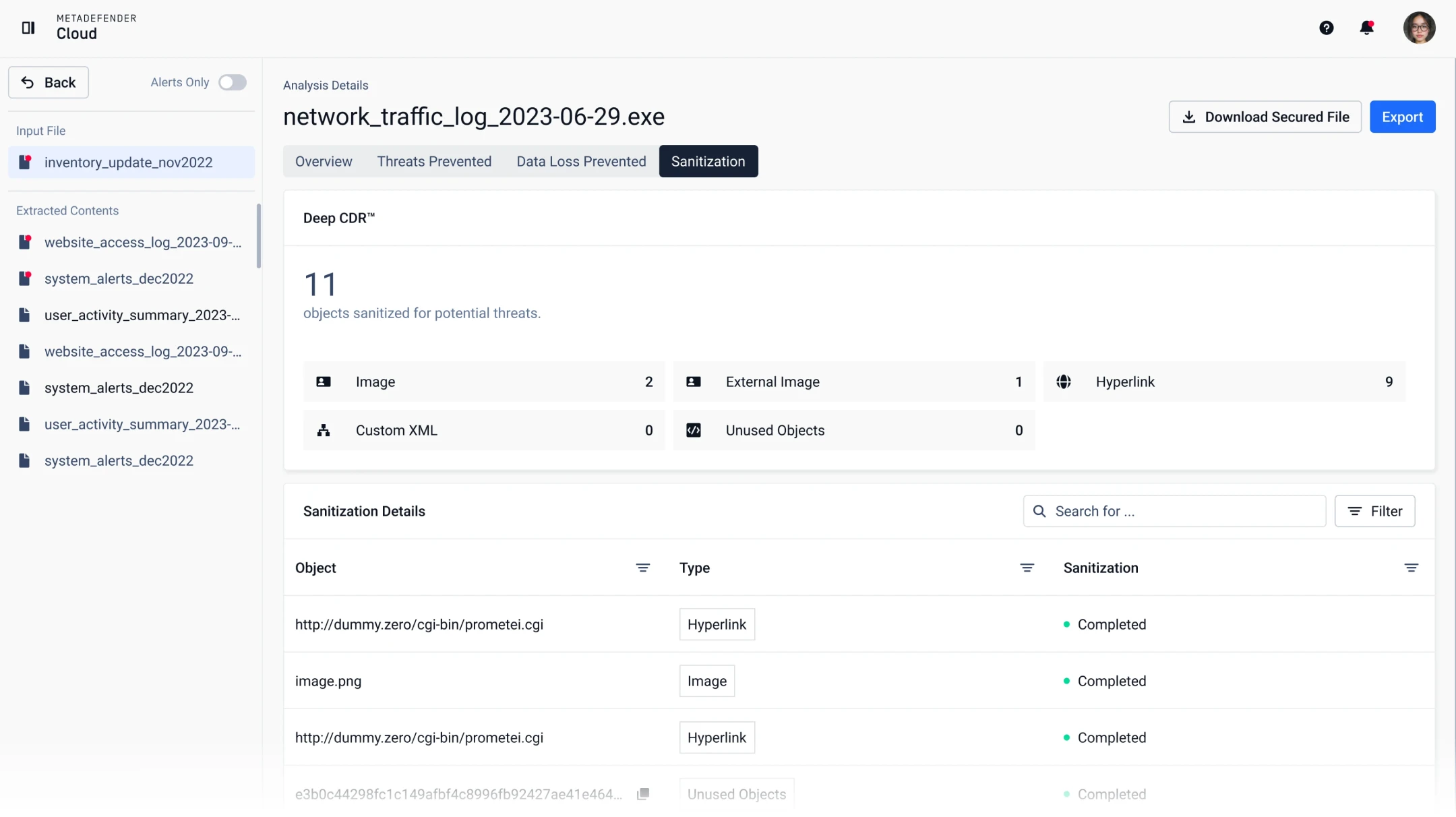
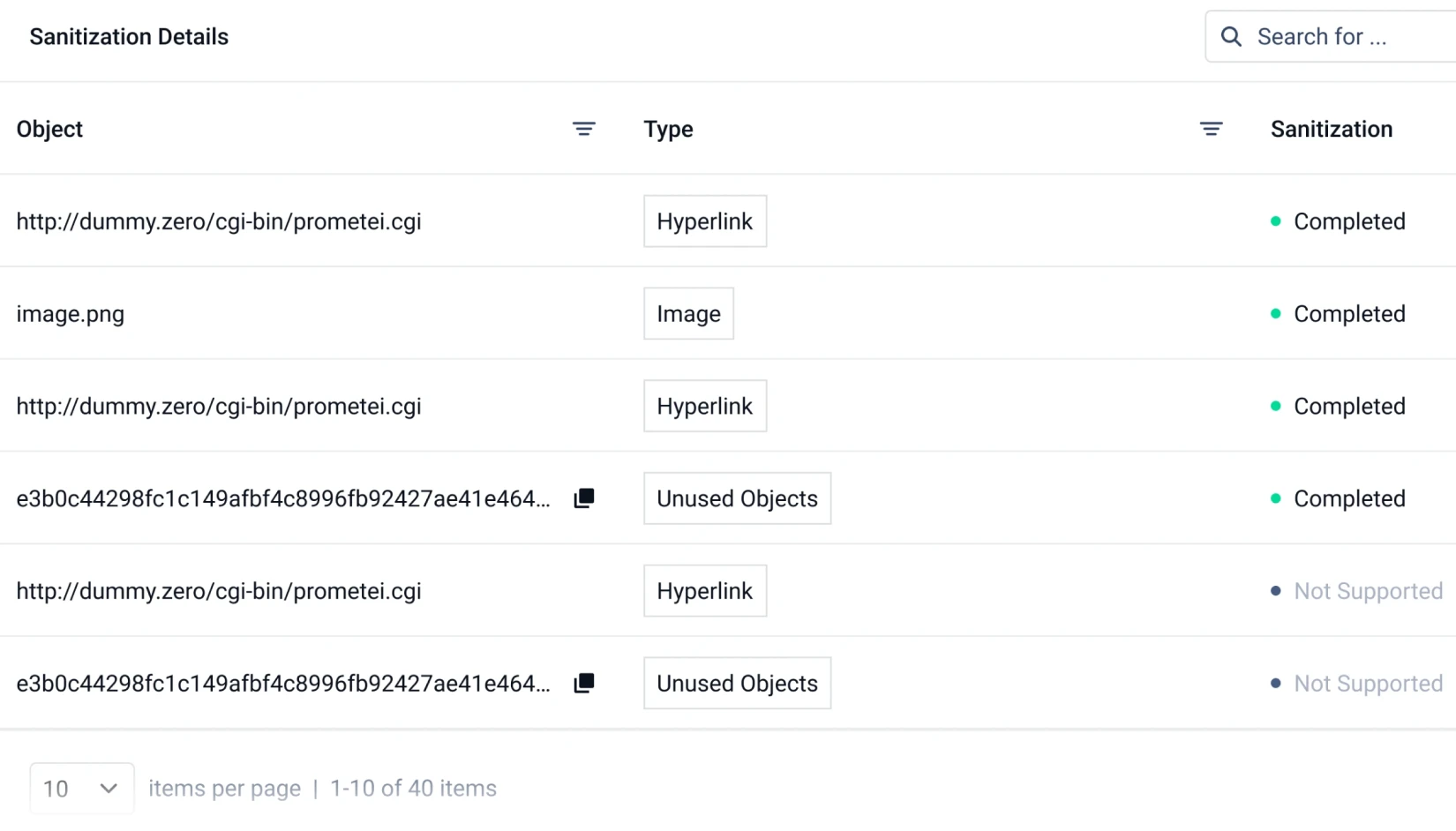
Deep CDR™
Prevent Zero-Day and targeted attacks using Deep CDR technology, ranked # 1 in the industry. Assuming all files are malicious, Deep CDR deconstructs each file and rebuilds it to remove potentially harmful and out-of-policy components. Safe files are returned to users with zero impact on workflow efficiency and file usability.
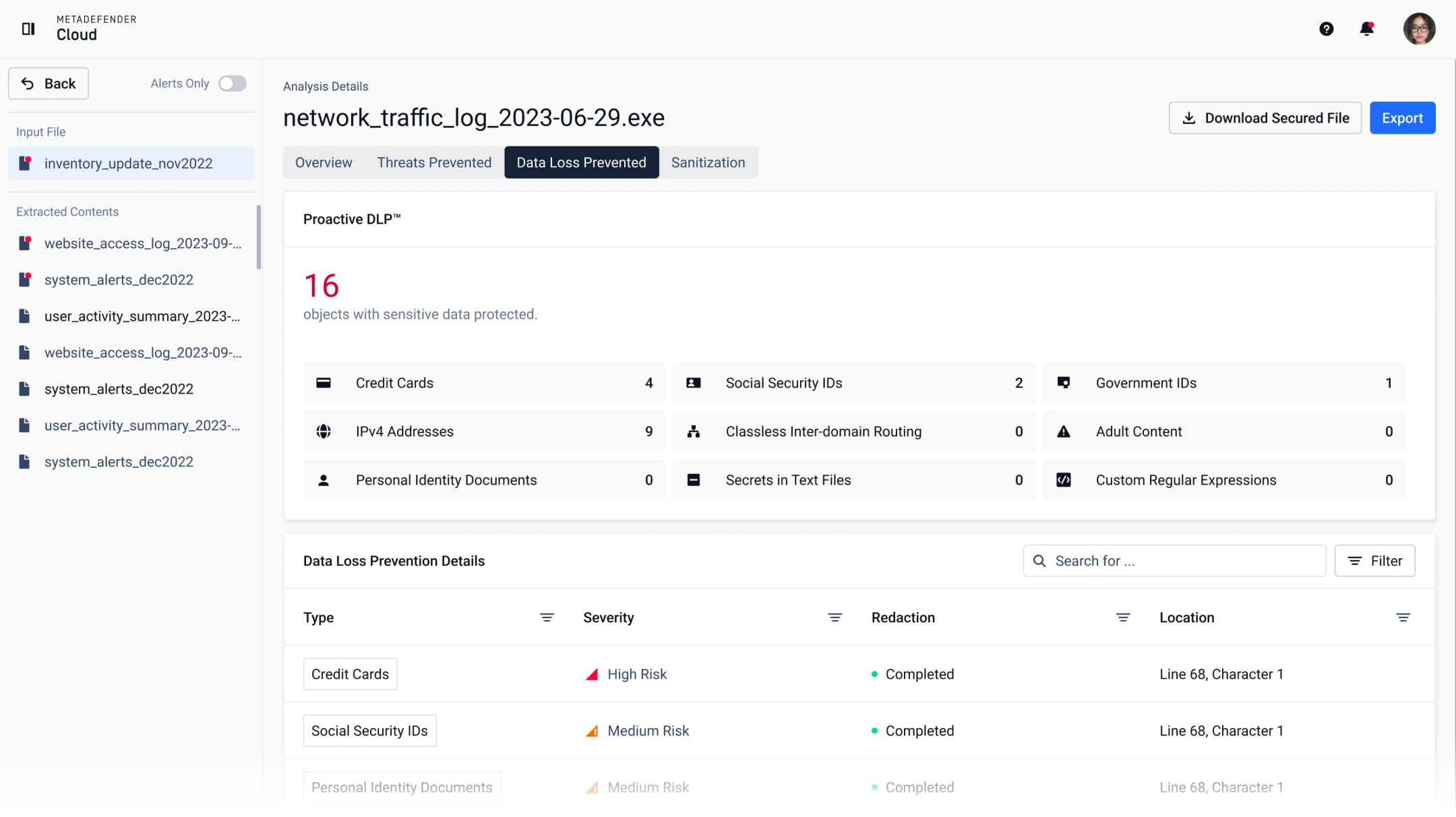
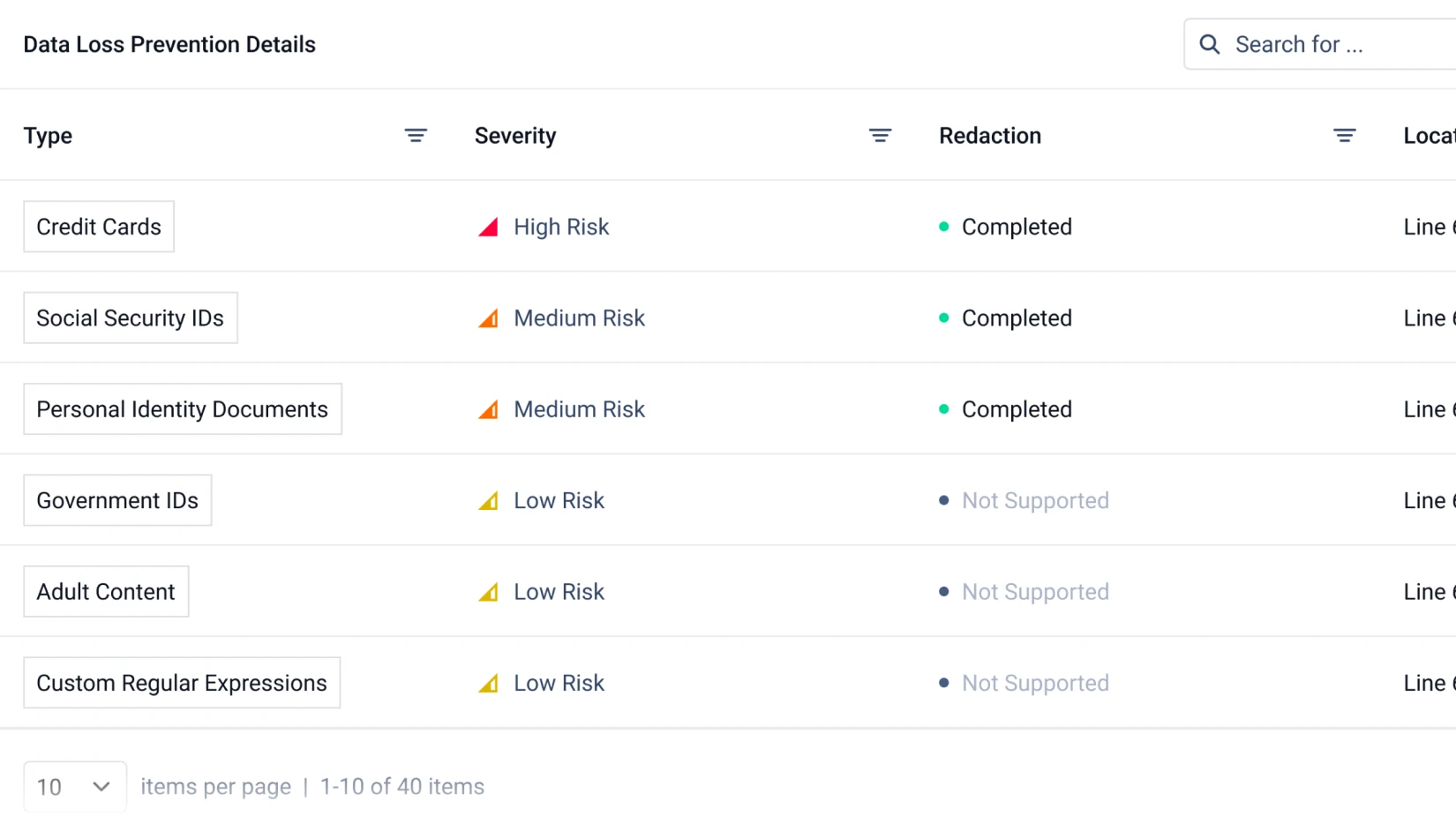
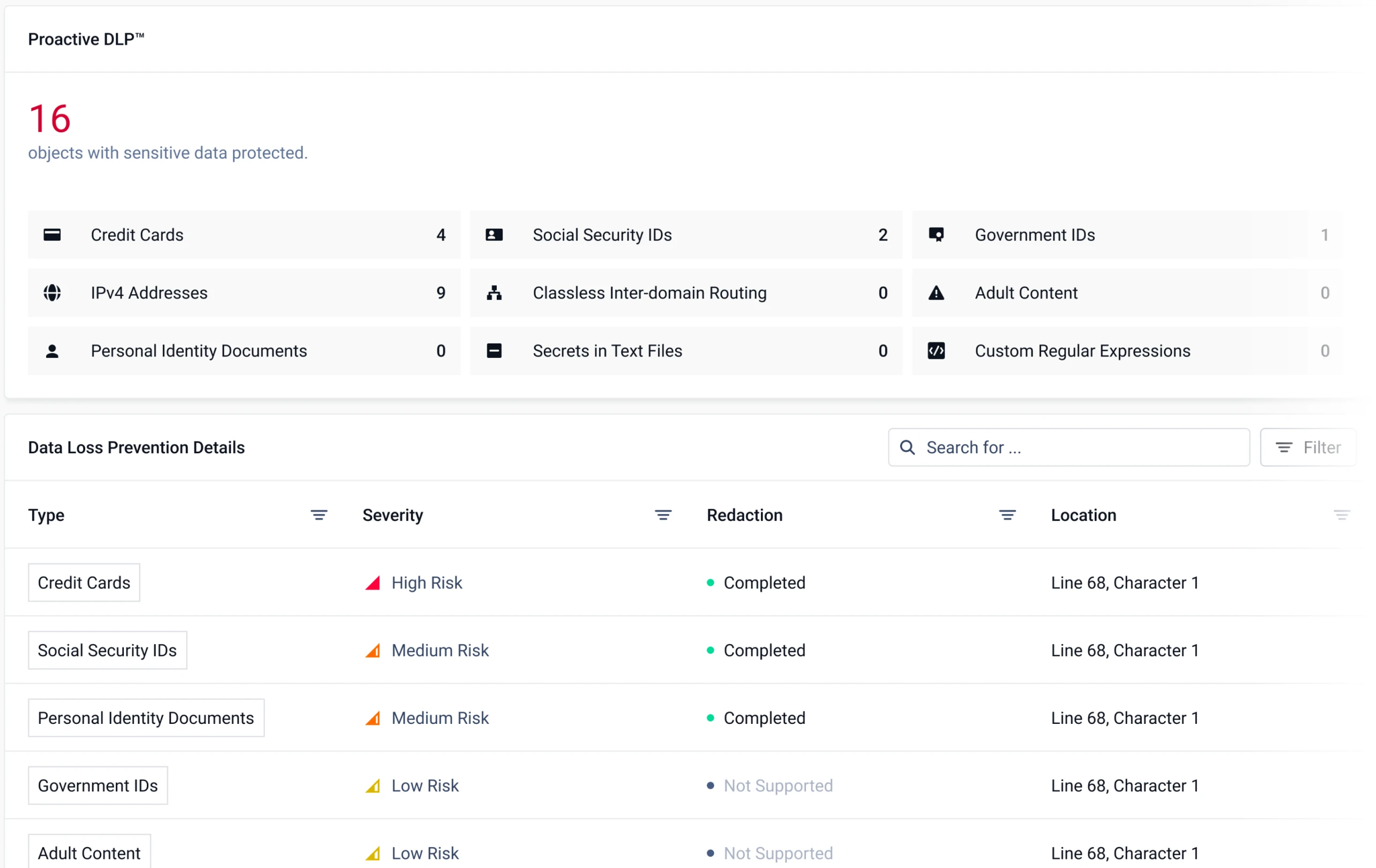
Proactive DLP
Proactive Data Loss Prevention (Proactive DLP) helps prevent potential data breaches and regulatory compliance violations by detecting and blocking sensitive data in files.
It supports 110+ file types, including Microsoft Office, PDF, CSV, HTML and image files. AI-powered Document Classification detects adult content in images and offensive language in text.
- MetaDefender Cloud
- MetaDefender Cloud
- MetaDefender Cloud
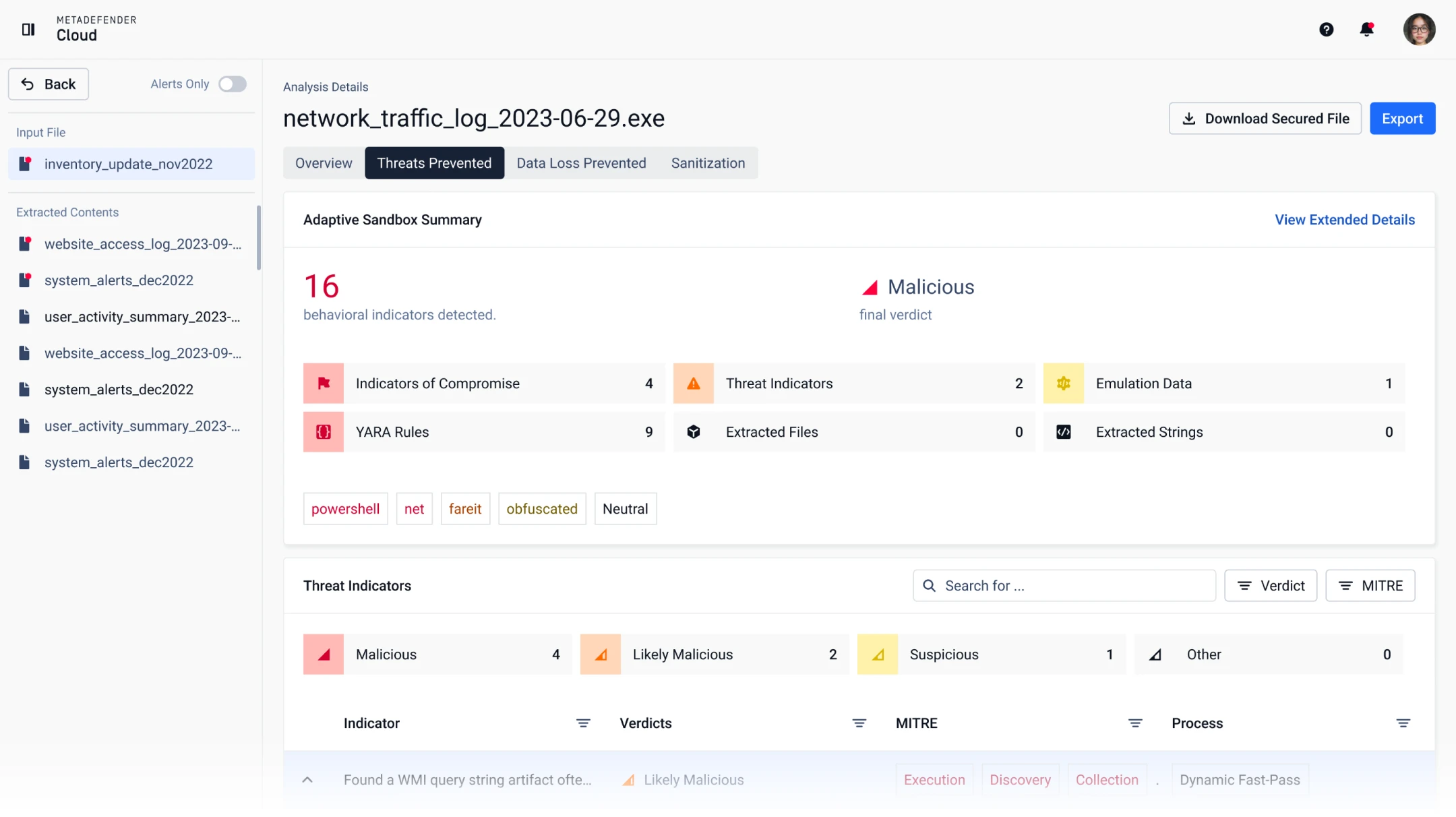
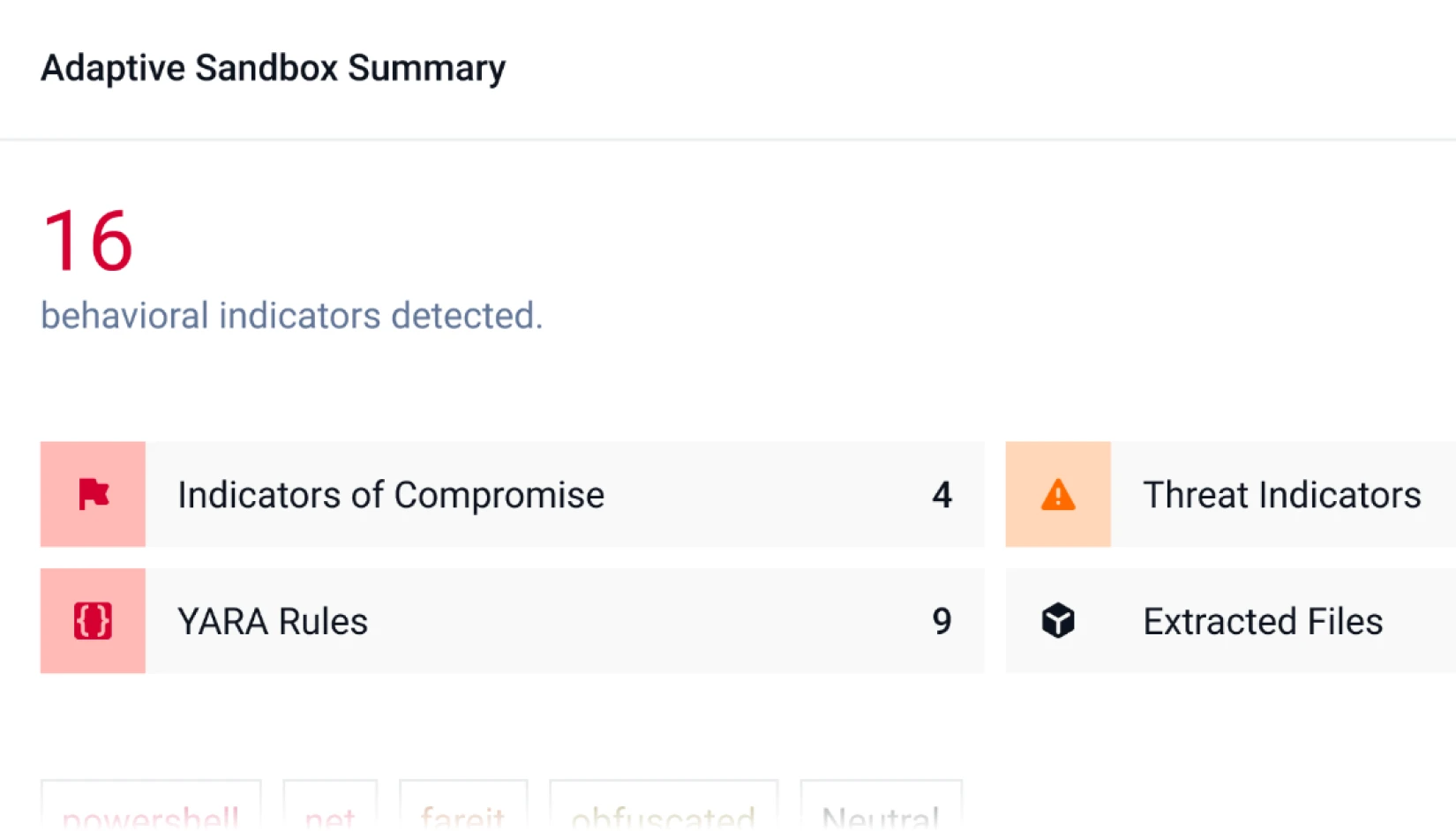
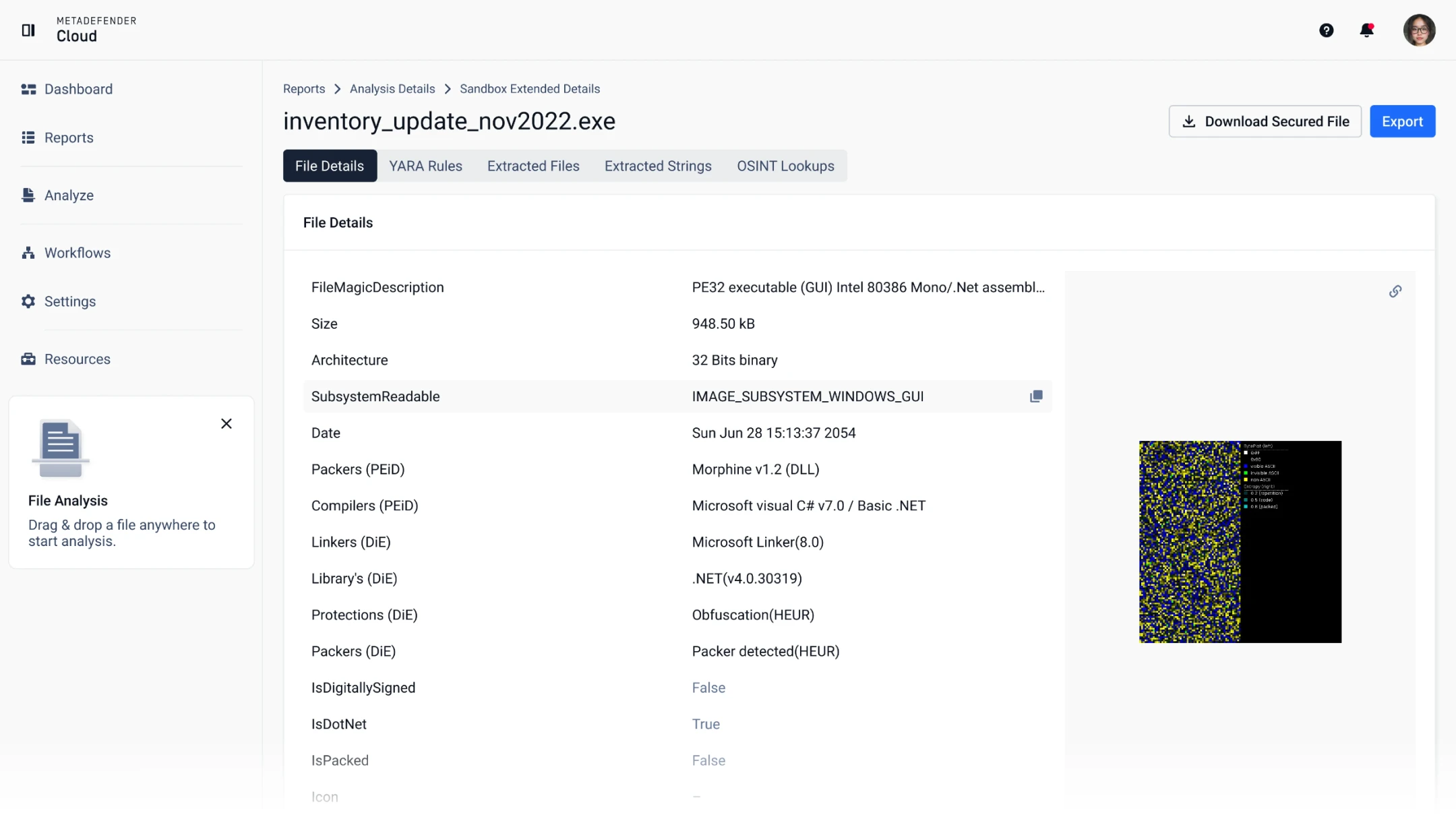
Next-Gen MetaDefender Sandbox
Detonate malware in a controlled environment to expose malicious behavior by recording and classifying file behavior. MetaDefender Sandbox expands the malware detection capabilities of MetaDefender Cloud, giving organizations a complete toolset of security technologies.
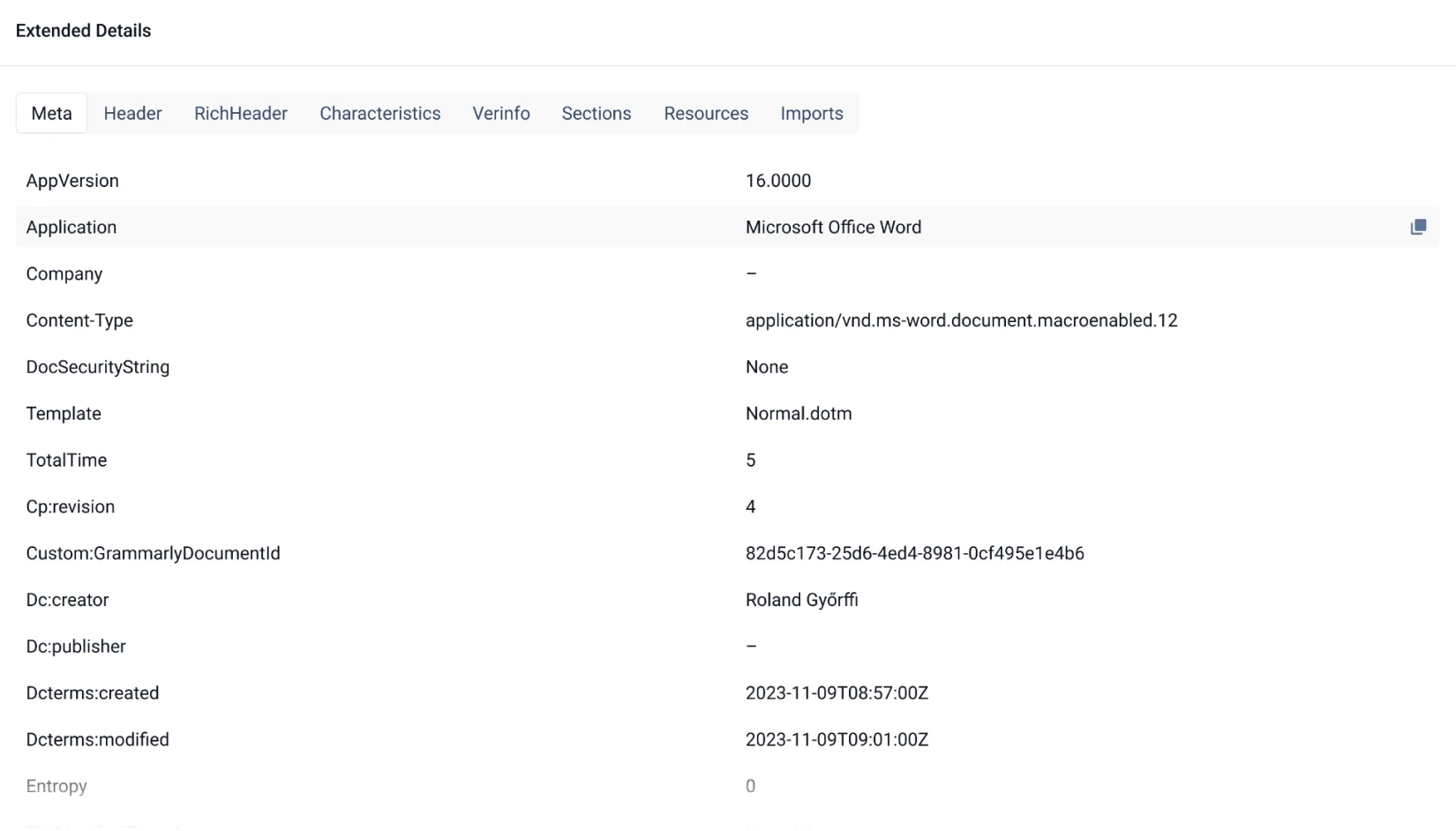
Rich Metadata
MetaDefender Cloud analyzes and extracts rich file metadata, giving security professionals access to information that exposes potential file irregularities or malicious capabilities. This data includes portable executable information, EXIF data, Android manifests, and others.
- MetaDefender Cloud
- MetaDefender Cloud
Product Walkthrough
Connect with MetaDefender Cloud to start processing & analysis.
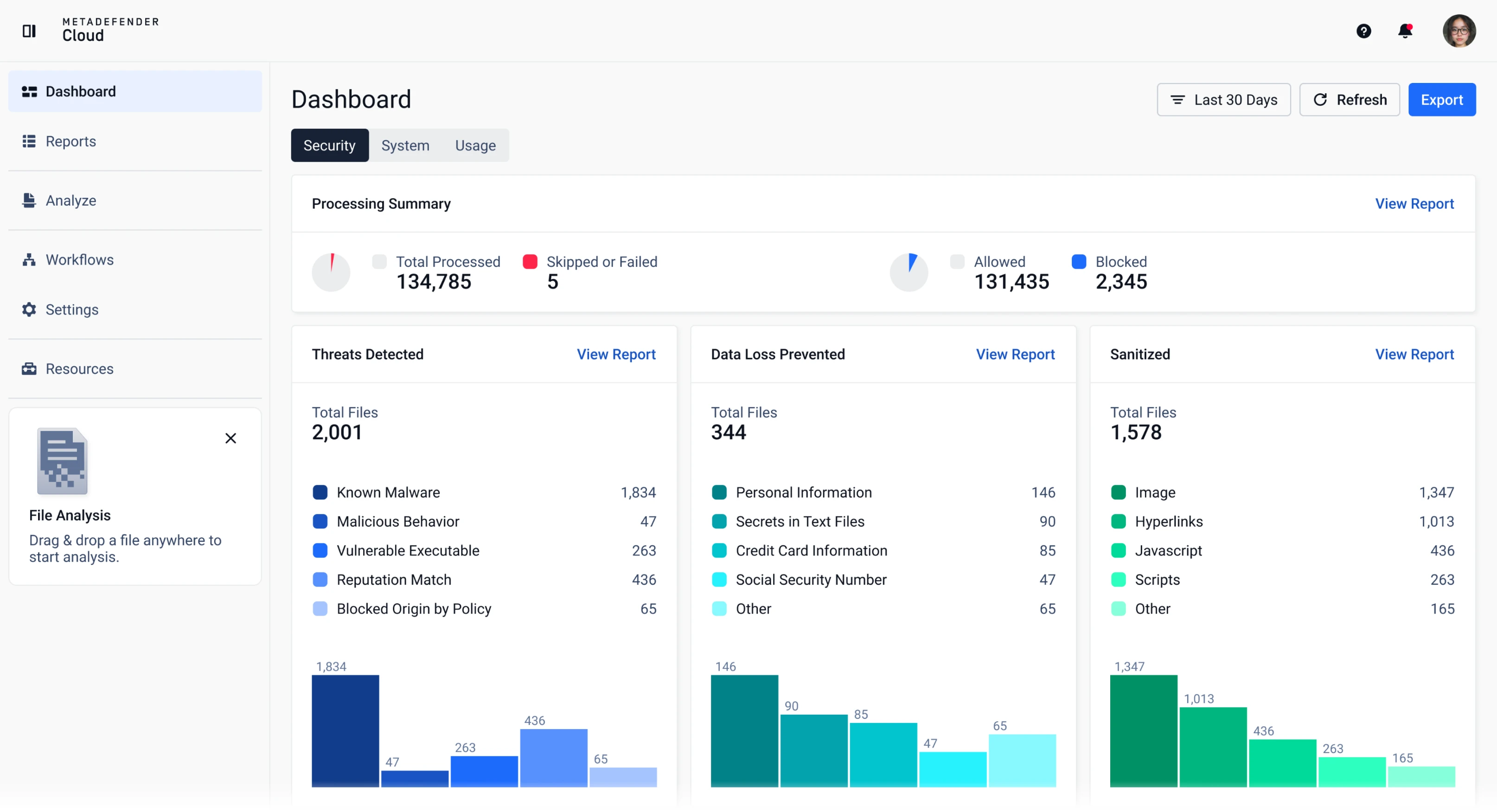
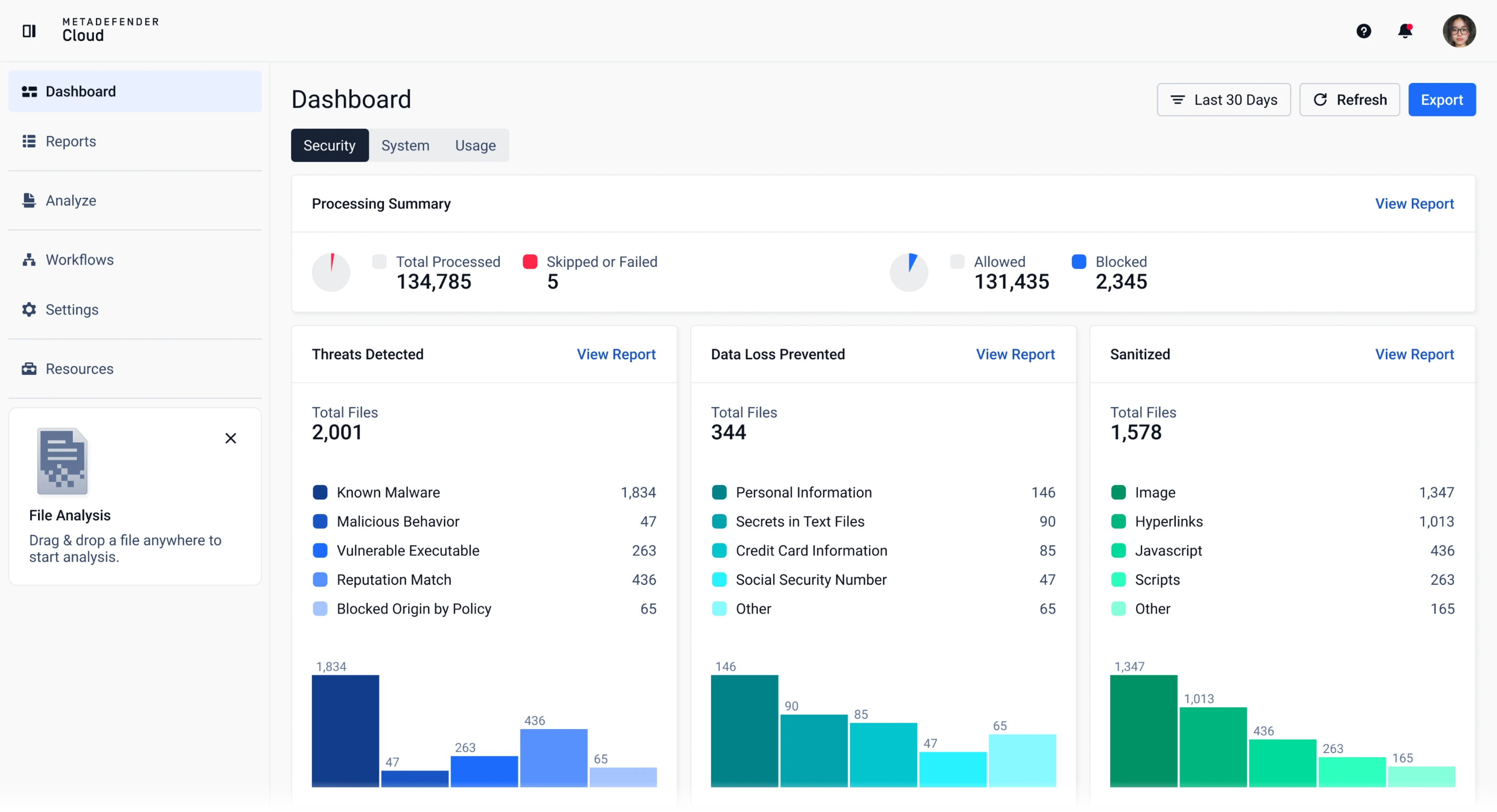
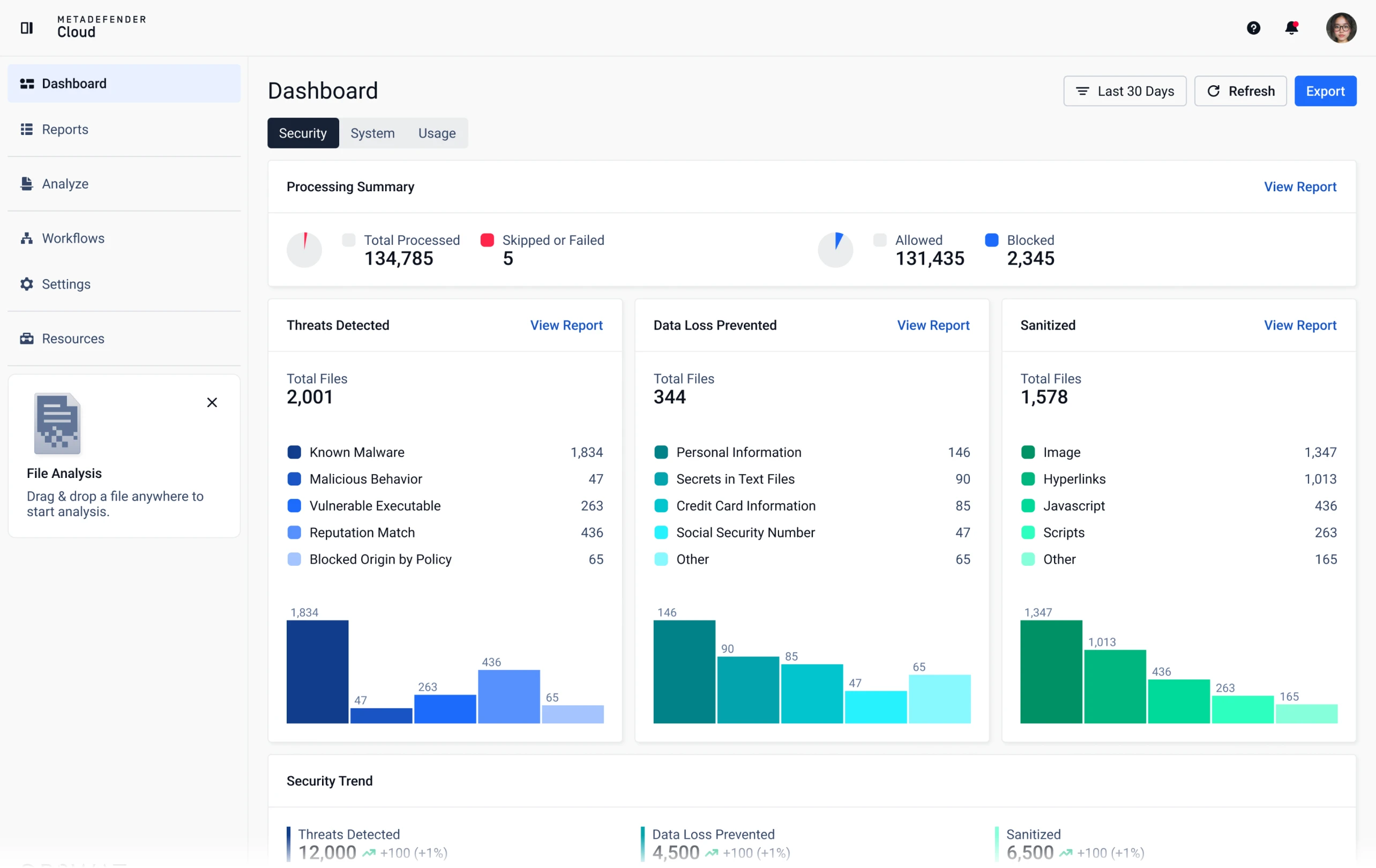
See scan results with real-time metrics and usage analytics.
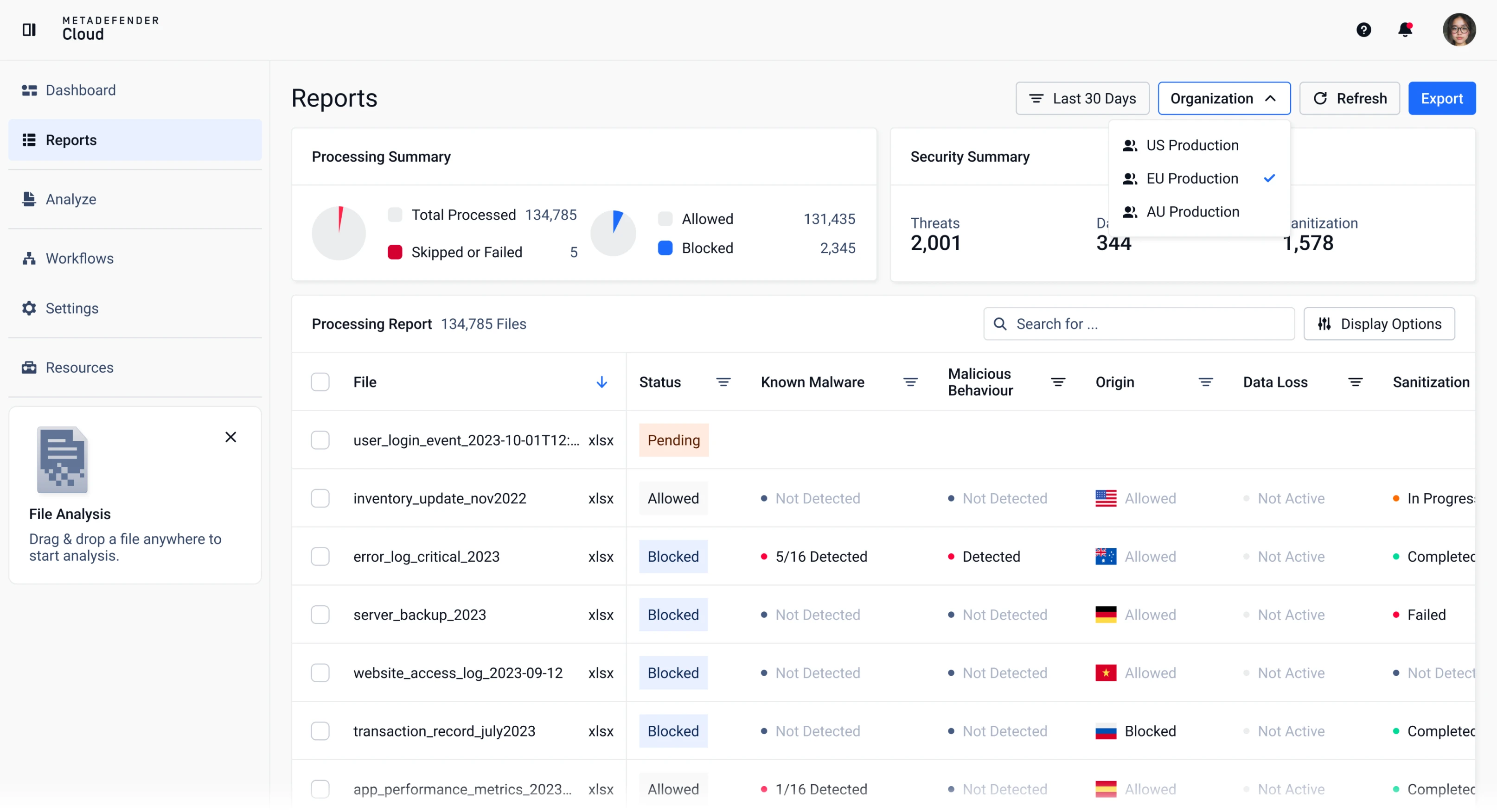
Access and filter scan reports. Monitor specific clients, departments, or partners.
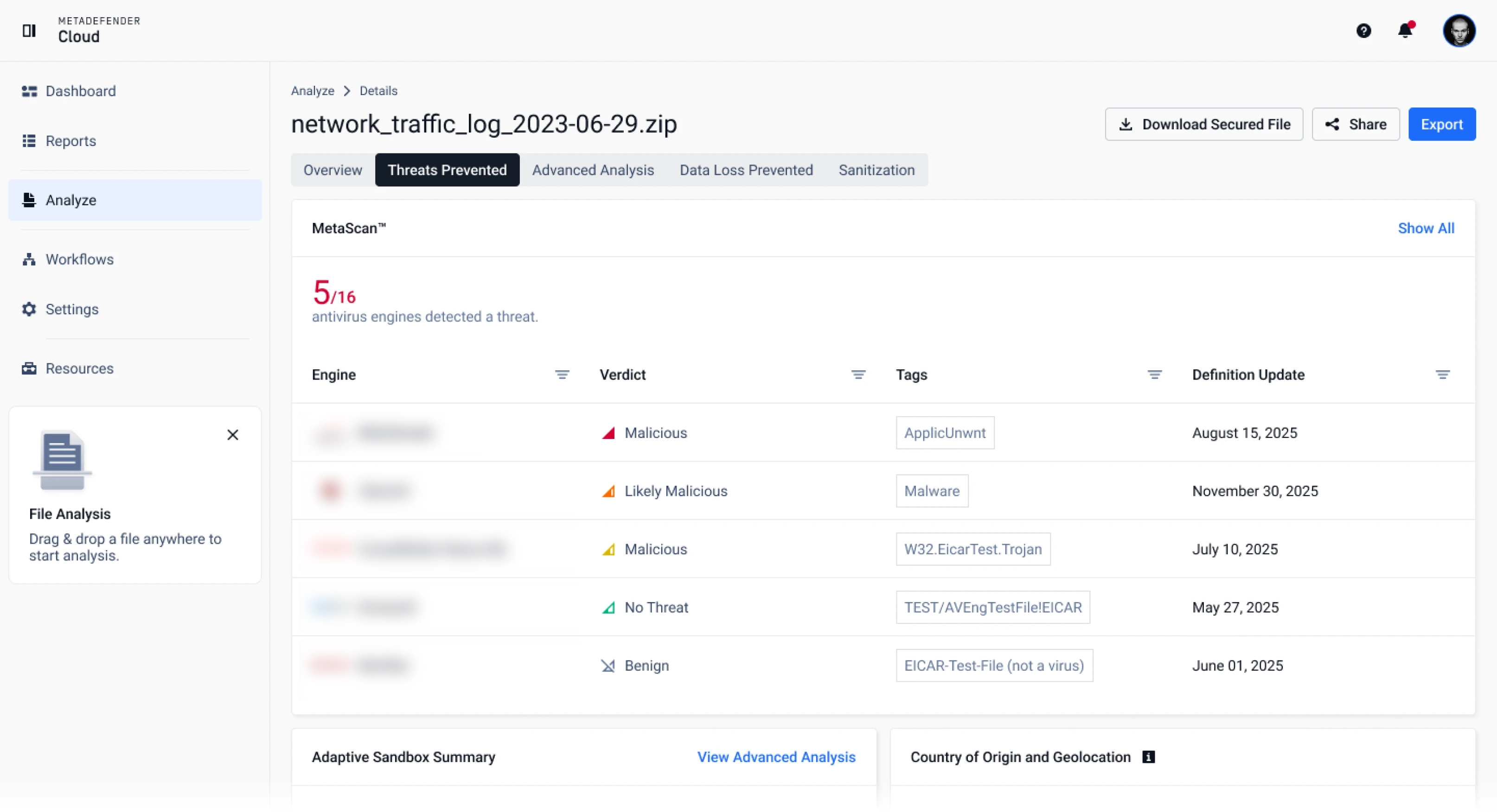
Dive deeper into specific file reports. See detailed metadata, results, and potential issue breakdowns.
Protect Every Critical Workflow
MetaDefender Cloud delivers advanced file security capabilities that stop malware, prevent data leaks, and strengthen your threat intelligence.
Prevent Malicious File Uploads
Prevent malicious files uploaded through web applications that bypass sandboxing and single anti-malware detection solutions. Deep CDR removes potentially malicious content from files and supports 200 common file types.
Perform Malware Analysis Quickly and Effectively
Malware analysts can take advantage of more than 20 anti-malware engines. The MetaDefender Cloud platform is easy to license and keeps data private with commercial options that do not store your files in the cloud. MetaDefender Cloud privately processes files in temporary storage and removes files immediately after analysis.
Prevent Data Breaches and Regulatory Compliance Violations
MetaDefender Proactive DLP helps companies prevent sensitive and confidential information in files from leaving or entering the company’s systems by content-checking files before they are transferred.
This helps enterprises meet regulatory requirements like HIPAA, PCI-DSS and GDPR. AI-powered Document Classification detects adult content in images and offensive language in text.
Inform Your Threat Intelligence Framework
OPSWAT's threat intelligence feed enables organizations to leverage real-time malware data collected by the MetaDefender Cloud platform from all around the world. Organizations integrate our up-to-date threat intelligence into their existing tools or solutions to protect their infrastructure against threats.
Deploy Anywhere, Integrate Everywhere
MetaDefender Cloud works seamlessly across SaaS, storage, and hybrid environments. The native integrations support file download, upload, and sharing workflows, enabling fearless collaboration in private and government organizations.
Native Integrations
MetaDefender Cloud works seamlessly across SaaS, storage, and hybrid environments. The native integrations support file download, upload, and sharing workflows, enabling fearless collaboration in private and government organizations.
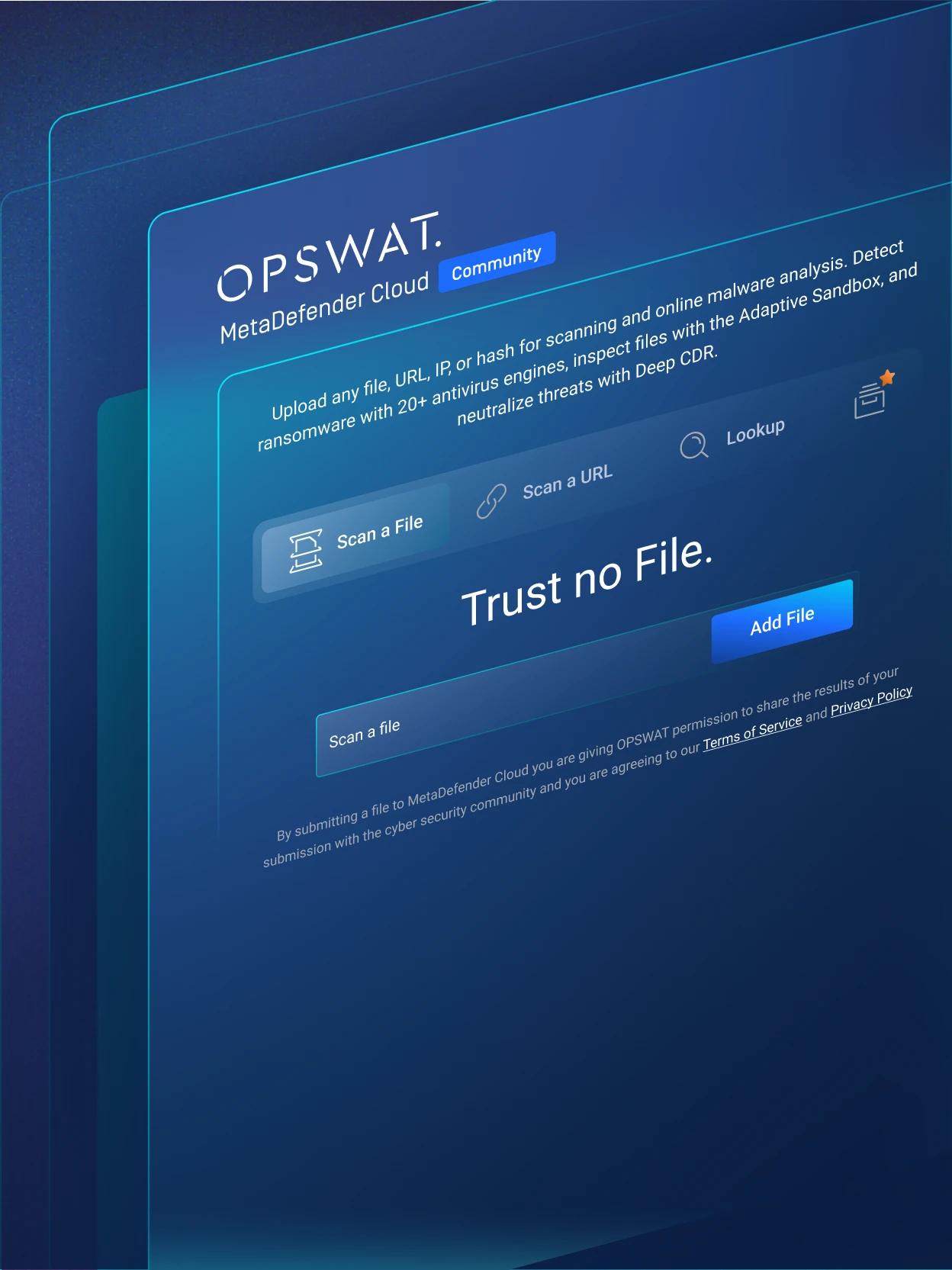
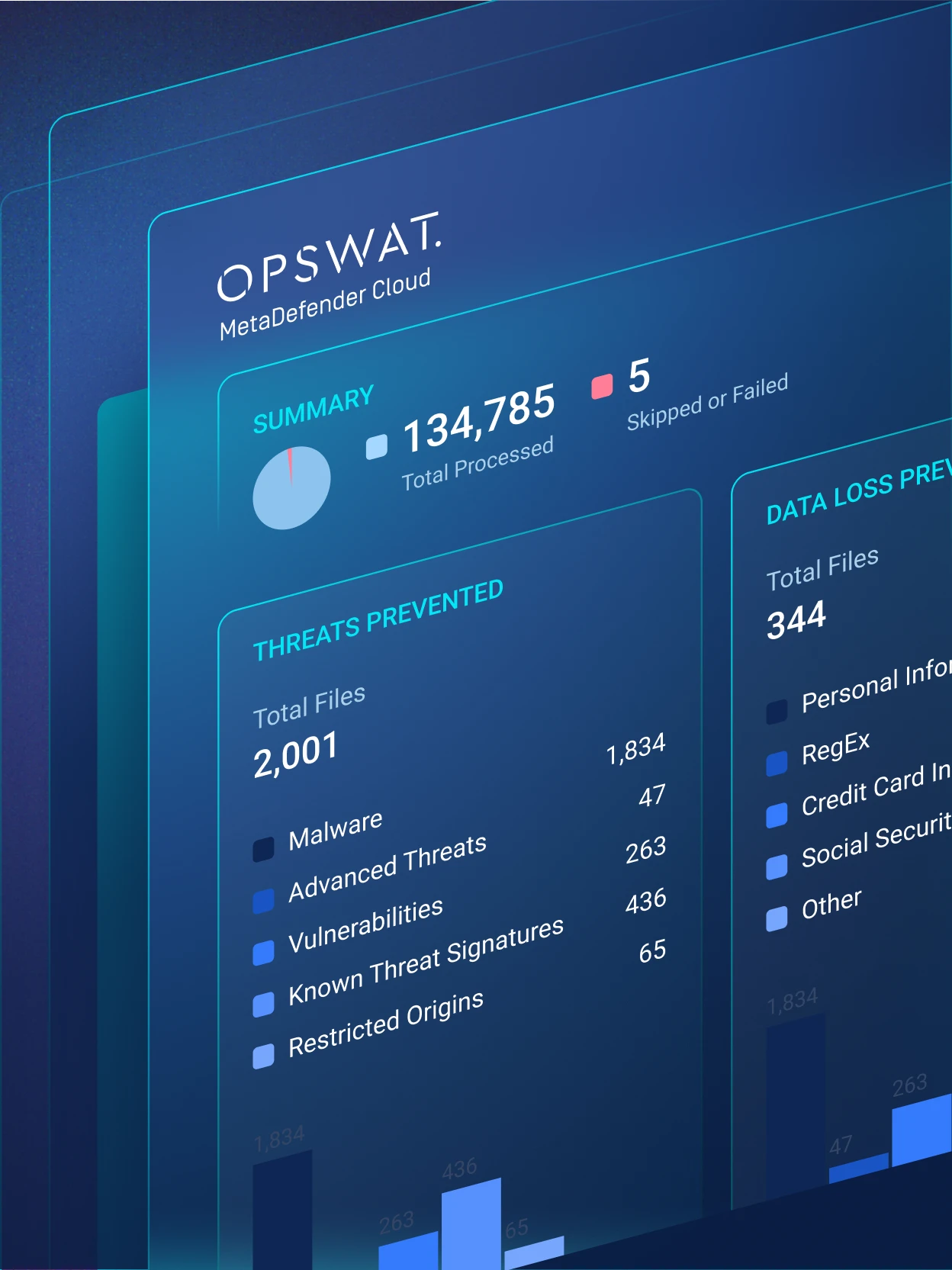
Web UI
The UI offers users full access to all the features offered by MetaDefender Cloud. For manual malware analysis or individual file and IP-Domain verification, the Web UI is a great tool to use from Desktop or Mobile.
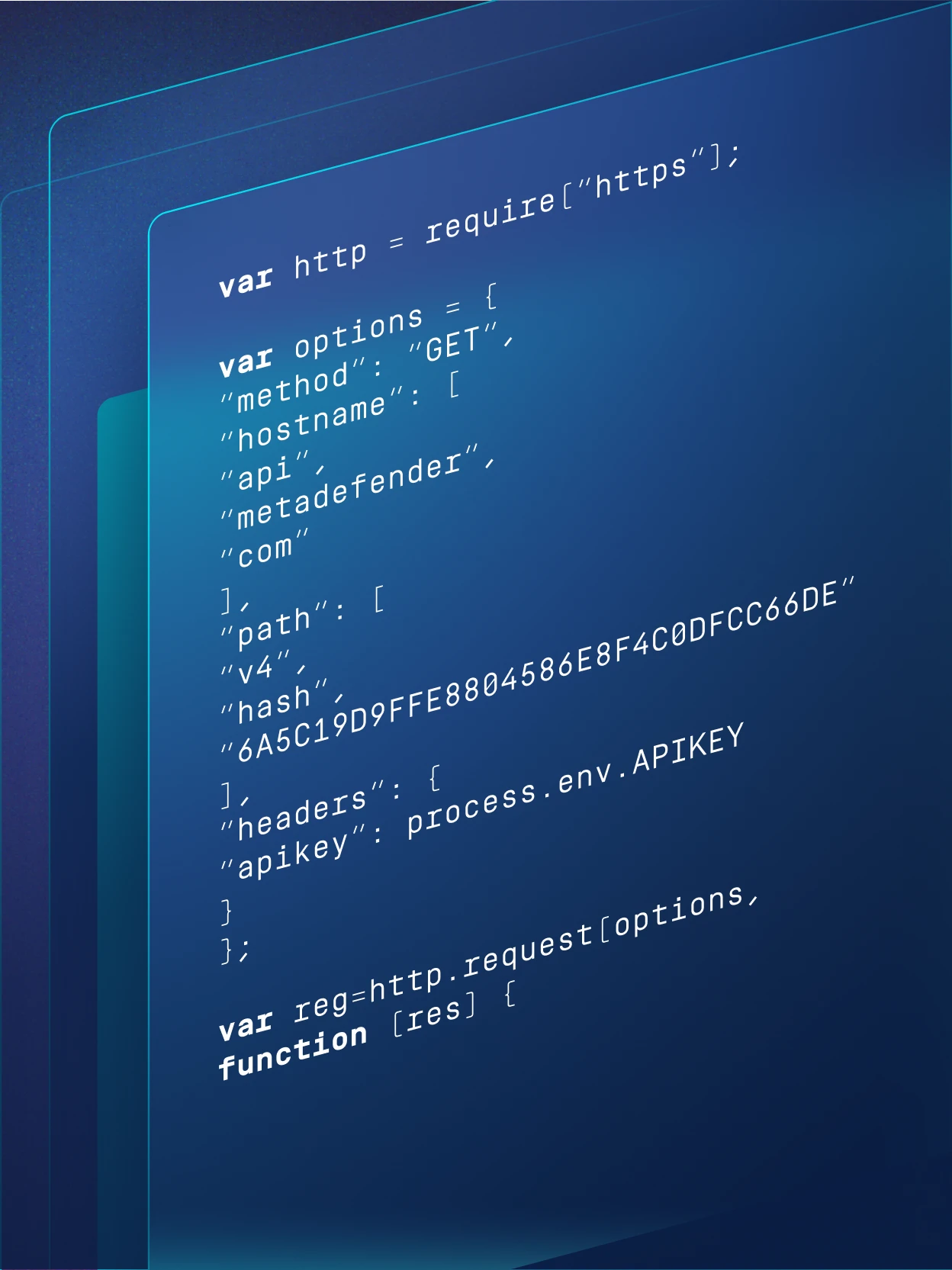
Rest API
All the functionality is also exposed as a REST API. With straightforward api key authentication, MetaDefender cloud easily integrates into any application or SIEM. The API is perfect for automating file, IP, and domain analysis.
A Single Platform Protects
Your Entire Cloud Stack
Seamless integrations, meant to secure files across the entire workflow; from upload to download, sharing, collaboration, and storage.
Trusted by Market-Leading Companies Worldwide
Support Compliance with
Regulatory Requirements
MetaDefender Cloud Licensing Models
Threat Prevention API
Flexible file processing and with multiple threat detection, lookup and prevention technologies available in three different tiers to meet your service and volume requirements.
| Features | Standard | Professional | Enterprise |
|---|---|---|---|
| Key Features | |||
| Metascan™ Multiscanning | |||
| Deep CDR™ File Sanitization | |||
| Proactive DLP™ Sensitive Data Detection and Redaction | |||
| Archive Extraction | |||
| File Type Verification | |||
| Volume | |||
| API Call Starting at | 1,000 / Daily | 1,000 / Daily | 1,000 / Daily or 30,000 Monthly |
| File Size Limit | 140 MB | 256 MB | 1 GB+ |
| Throttling (req/min) | 75 | 150 | 500 |
| Max files in archive | 500 | 10,000 | 50,000 |
| Archive recursion level | 5 | 25 | 50 |
| Antivirus Engines | |||
| Number of Engine(s) | 10 | 15 | 23 |
| Service & Support | |||
| Service & Support | Low | Medium | High |
| Availability SLA | 99.5% | 99.5% | 99.9% |
| Response time SLA |
8 seconds p50 500ms API calls p50 |
8 seconds p75 500ms API calls p75 |
8 seconds p90 500ms API calls p90 |
| RTO | 24 hour | 12 hour | 4 hour |
| Support | 24 hour | 12 hour | 4 hour |
| Added Security | |||
| Private Scanning | |||
| Private Processing | |||
| End to End Encryption | |||
| IP Range Restrictions | — | — | |
| mTLS | — | ||
| Customer Provided IDP | — | — | |
| Billing & Organization | |||
| Buffer Limit | — | 20% Over Without Fee | 50% Over Without Fee |
| Organizations | — | ||
| Reporting | — | ||
| Notifications/Alerts | — | ||
| Custom Domain | — | — | |
Additional API Tools
| Features | Cloud Sandbox API Expand the malware detection and analysis capabilities with adaptive threat analysis. | Reputation API Leverage real-time malware data collected by from all around the world. | Threat Intelligence API Perform threat hunting and detect unknown threats. |
|---|---|---|---|
| Key Features | |||
| Execute files on multiple operating systems | — | — | |
| Automated interpretation of malware behavior | — | — | |
| Extract Indicators of Compromise (IOCs) from a wide range of executables, documents, scripts, and URLs | — | — | |
| Emulates 90%+ of highly obfuscated state-of-the-art macro malware (VBA), VBS, PowerShell, Jscript, MSHTA, XSL, WSF | — | — | |
| Integrates with YARA, MITRE ATT&CK framework and more | — | — | |
| Retrieve scan reports using a file hash | — | — | |
| Scan IP addresses, URLs, and domains | — | — | |
| File metadata lookup | — | — | |
| Pattern search (expression search) intelligence data that focuses on exact matches of predefined conditions | — | — | |
| Similarity search techniques aim to identify patterns or indicators resemble known threats or Indicators of Compromise (IOCs) | — | — | |
| Volume | |||
| API Call Starting at | 1,000 / Daily | 25,000 / Daily | 1,000 / Daily |
Want To Know More About
Our Licensing Models?
How It Works in 3 Simple Steps
Technical Documentation
Getting Started
Deployment & Usage
Support
Unlock the Full Potential of Our Products

Recommended Resources
Predictive Alin AI
Detect and prevent malicious behavior before execution with OPSWAT’s next-generation static AI engine—optimized for accuracy and seamless integration across the MetaDefender Platform.