A new ransomware called PowerWare was recently identified by researchers at Carbon Black. This threat is spreading through phishing emails containing Microsoft Word documents embedded with malicious macros. We have seen a few examples of this threat uploaded to our public MetaDefender.com site, where users can scan files, hashes and IP addresses for threats.
Documents with these types of macros, which are written in PowerShell scripting language, are examples of unknown threats. OPSWAT's MetaDefender Core is designed to prevent this type of attack by using data sanitization. The philosophy behind data sanitization is to proactively remove any components from files that have the potential to be malicious, even if a threat has not been detected. For more details on how this works, you can check out several posts from our data sanitization series:
- Part 1 - The Case for Data Sanitization
- Part 2 - File Structure Alterations
- Part 3 - Active Content Curing
When combined with OPSWAT's MetaDefender Email product, data sanitization can be used to prevent these types of phishing attacks from compromising an organization's security. MetaDefender Email allows any incoming email attachments to be scanned for threats and can sanitize document files that may contain embedded threats. Once sanitized, the new version of the file is delivered to the recipient for safe use.
For some examples demonstrating how data sanitization can remove threats from office documents, here are three examples of scan results from MetaDefender.com, showing both the threats found in the original documents as well as the threat free sanitized documents.
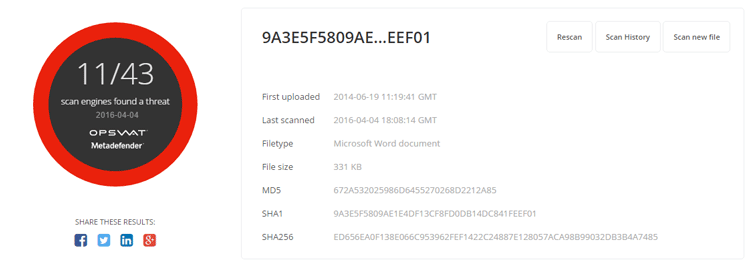
Word Doc Example #1
- Original file scan result from MetaDefender.com
- Threat Name - W97M.Marker
- Threat type - Virus
- File Type: Microsoft Word Document
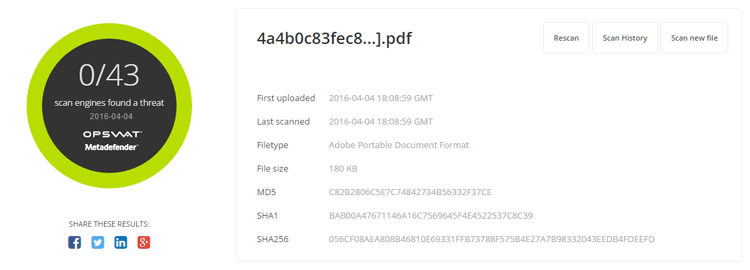
- Sanitized file scan result from MetaDefender.com
- File Type: Adobe Portable Document Format
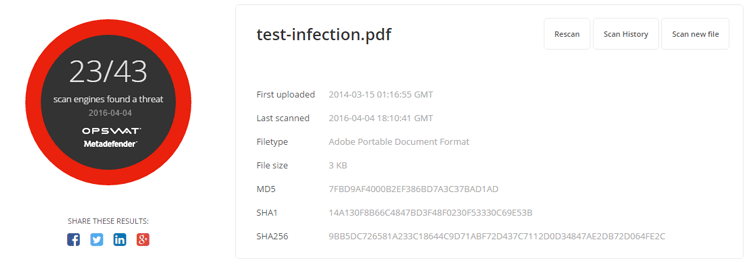
PDF Example
- Original file scan result from MetaDefender.com
- Threat Name: Bloodhound.Exploit.213
- Threat Type: Trojan/Virus
- File Type: Adobe Portable Document Format
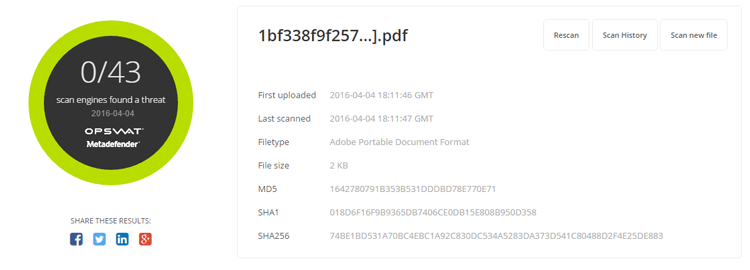
- Sanitized file scan result from MetaDefender.com
- File Type: Adobe Portable Document Format
Word Doc Example #2
- Original File scan result from MetaDefender.com
- Threat Name: W32/Renamer
- Threat Type: Virus/Trojan
- File Type: Microsoft Word document
- Sanitized file scan result from MetaDefender.com
- File Type: Adobe Portable Document Format

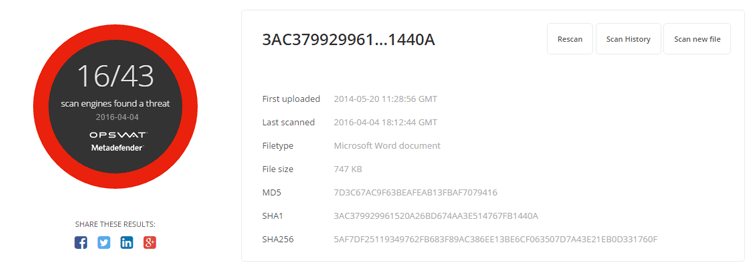
Word Doc Example #3
- Original file scan result from MetaDefender.com
- Threat Name: Trojan-Dropper
- Threat Type: Trojan
- File Type: Word Microsoft Office Open XML Format document
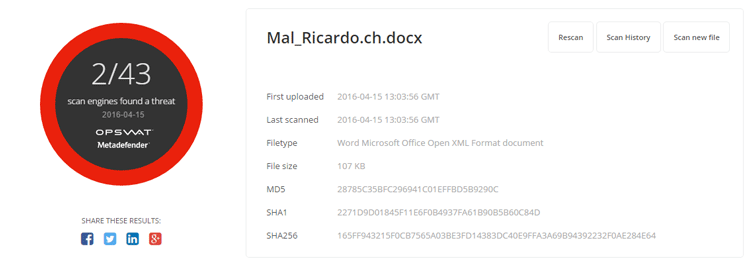
- Sanitized file scan result from MetaDefender.com
- File Type: Word Microsoft Office Open XML Format document
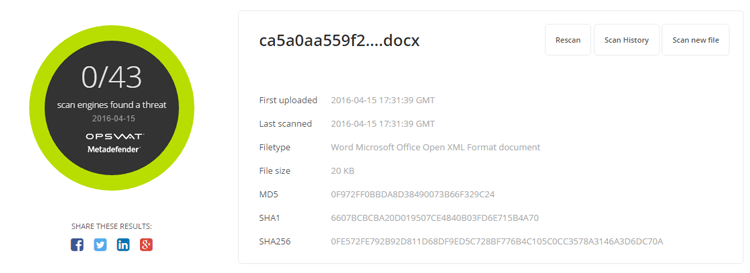
Data sanitization allows organizations to safely receive documents while preserving the usability files. By using data sanitization, the hospitals recently hit by ransomware attacks, could have prevented the attack from ever entering their organization. If you are interested in learning more about this technology, check back on our blog soon for the 4th part of our data sanitization series.

